StreamIO-htb-writeup
0x00 靶场技能介绍
章节技能:MSSQL数据库SQL注入攻击、二级目录扫描、hydra登录表单爆破、PHP过滤器使用、配置文件敏感信息泄露、chisel工具端口转发、mssqlclient工具使用、crackmapexec密码验证枚举、sqlcmd命令查询数据库、Firefox密码文件搜集和密码解密、pyLAPS可用于检索LAPS密码、使用 PowerView 工具添加某用户到某组中、crackmapexec获取ntds密码、使用ldapsearch来枚举ms-MCS-AdmPwd
参考链接:https://0xdf.gitlab.io/2022/09/17/htb-streamio.html
参考链接:https://b0ysie7e.gitbook.io/articulos/write-up/hackthebox/2024-03-20-streamio
0x01 用户权限获取
1、获取下靶机IP地址:10.10.11.158
2、获取下开放端口情况
1 | |
3、根据端口开放情况,目标靶机是一个域控,那就简单的ldap协议枚举下信息吧
1 | |
4、接下来还是先绑定下本地hosts信息吧
1 | |
5、剩下的就是查看下WEB端口服务的内容了
http://10.10.11.158/
https://10.10.11.158/
https://streamio.htb/
https://watch.streamio.htb/
6、其实枚举到这个WEB端口的情况,我就知道这个靶机不是好打的,毕竟开放的端口多,WEB服务也多,说明兔子洞也多,先查看下网站是什么语言,再决定如何扫描靶机
7、扫描下目录文件情况吧
1 | |
https://watch.streamio.htb/search.php
https://watch.streamio.htb/blocked.php
8、继续扫主域名的目录
1 | |
https://streamio.htb/Register.php

shiyanshiyan
https://streamio.htb/admin/master.php

9、截止到目前的信息,最先的突破口,估计就是那个电影的搜索目录了,最容易出现SQL注入漏洞,简单尝试下吧
https://watch.streamio.htb/search.php
1' AND 1=1 -- //
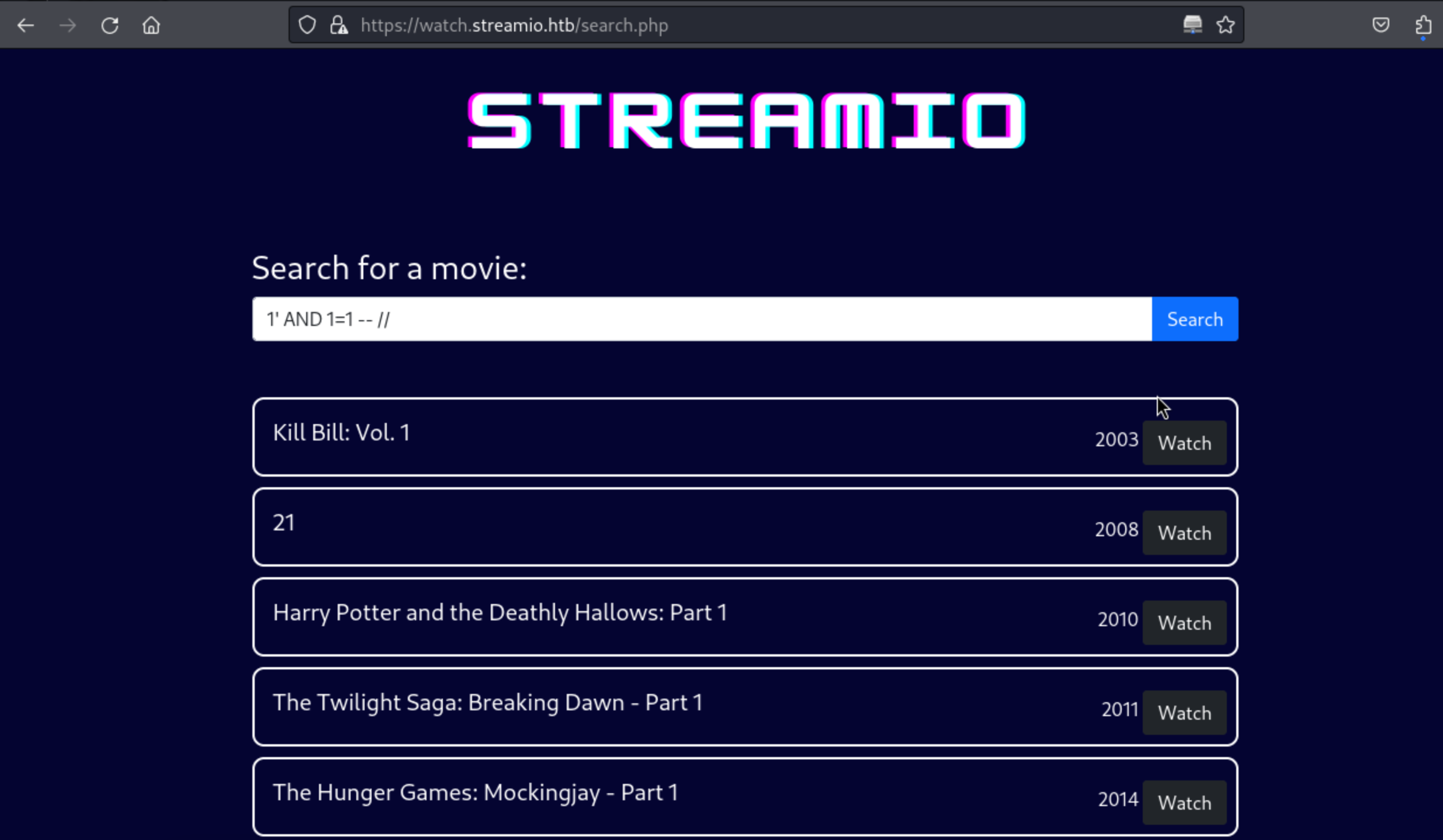
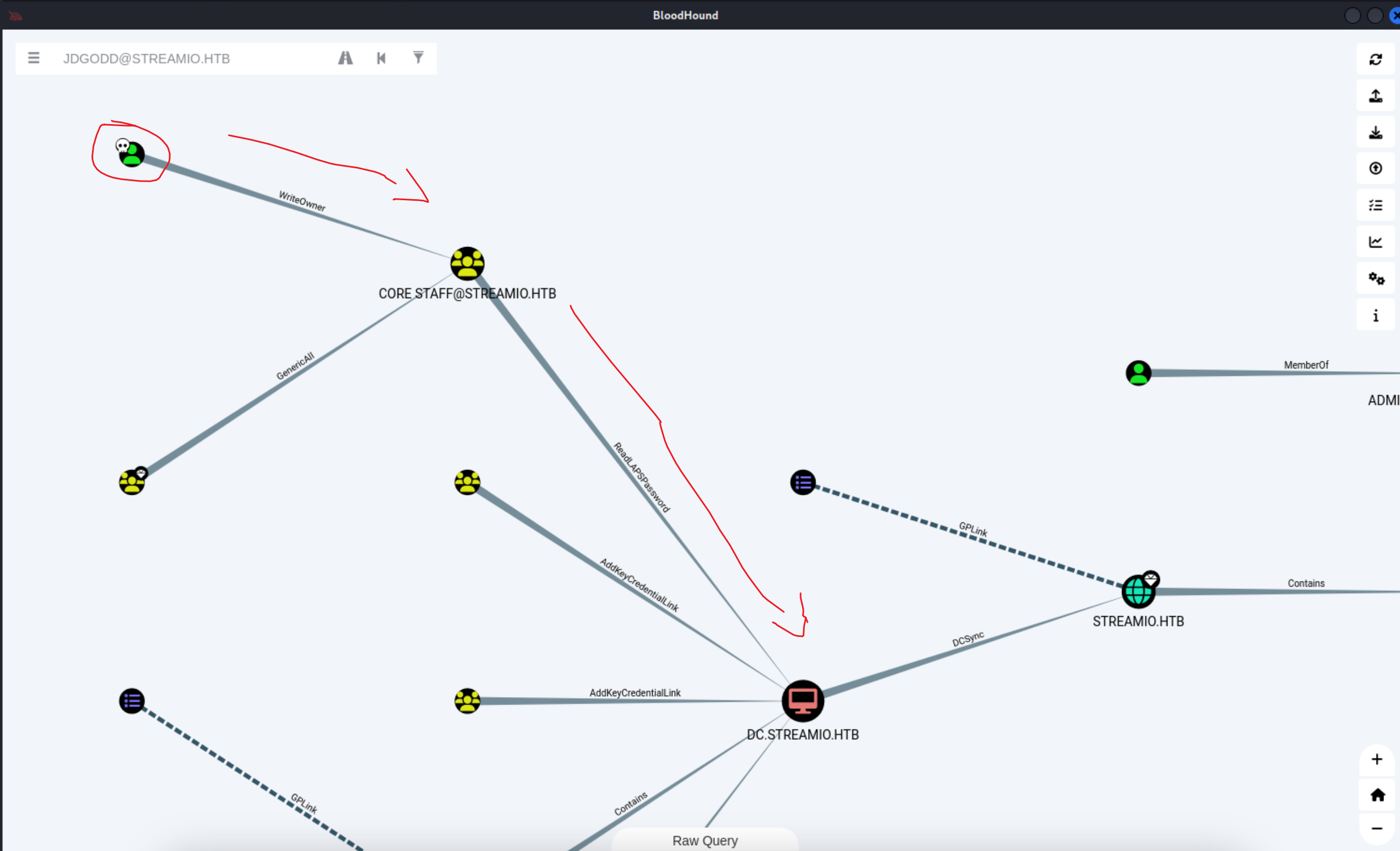
1' AND 1=2 -- //
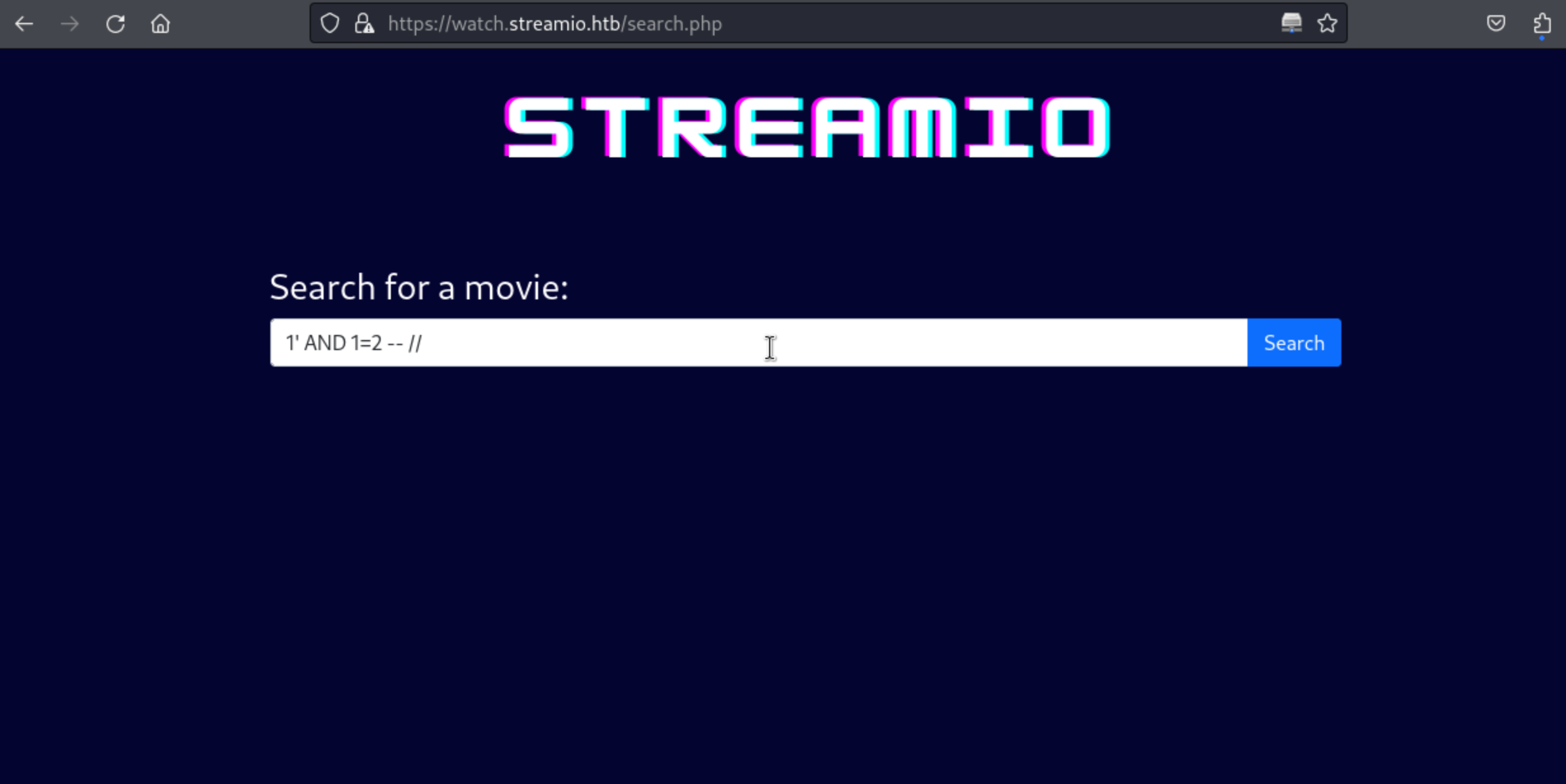
10、到这里基本上就是存在SQL注入漏洞了,下面开始枚举出来一些数据
q=-1' union select 1,2,3,4 ,5,6 -- //
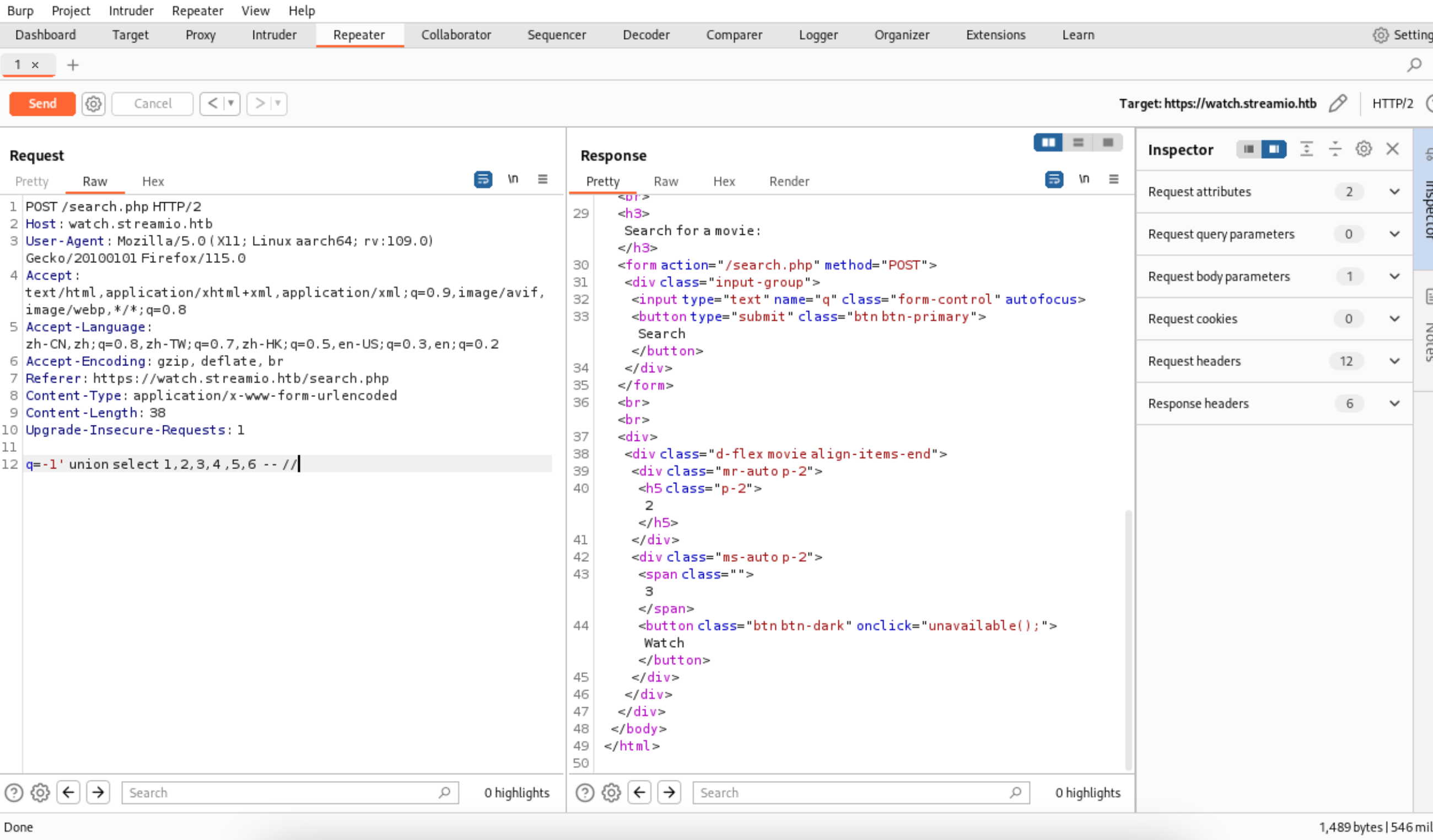
1 | |
11、到这里就发现了一些账号密码,那就使用在线的破解网站进行密码破解把,这样快些

1 | |
12、既然账号密码都是那个网站的上的 https://streamio.htb/ , 呢就是开始尝试枚举登录吧
13、把上面的用户名和密码分别放到字典列表里,开始进行尝试
1 | |
14、下面使用上面破解的账号密码进行登录
https://streamio.htb/admin/

15、通过访问页面,没有发现什么页数的东西,但是可以使用ffuf进行目录枚举下,参数是名称形式的
1 | |
16、访问debug功能,此选项仅适用于开发人员这里进行模糊枚举,发现可以进行包含前期的发现的地址
https://streamio.htb/admin/?debug=

1 | |
17、尝试使用过滤器去访问

1 | |
18、进行解码查看下,核心代码点,发现eval

1 | |
19、file_get_contents():这是PHP的一个内置函数,用于读取文件并将内容作为字符串返回。当它接收到$_POST[‘include’]作为参数时,会尝试读取该字符串指定的文件路径,并将文件内容读取出来。
20、这不一个命令执行就有了啊,开始尝试,感觉像那个啥,就是返回的太多了,看不到最后的结果了,这里尝试下反弹shell吧
1 | |

1 | |
1 | |
1 | |
21、这里我们就获取到了一个初始的shell环境,由于这个是中级靶机,所以到这里还需要枚举信息,来横向移动到另一个用户下,才能获取到第一个flag信息
1 | |
22、这里的枚举中,发现了个数据库的账号密码,我这里想的是做一个简单的端口转发,然后我使用本地的工具,去登录数据库
1 | |
1 | |
23、端口是转发出来了,然后我们使用mssqlclient工具进行连接和枚举
1 | |
24、下面简单的列一下发现的密码信息
1 | |
25、这里获取的用户和主机上存在的用户很相似,这里使用crackmapexec 工具或者 evil-winrm 工具尝试验活下
1 | |
26、然后使用可以登录的账号密码进行登录,并获取到第一个flag信息
1 | |
补充:这里放置个演练报告里的方法,他是通过本地查看的
1 | |
0x02 系统权限获取
27、提升了到了用户级别的权限,就开始继续枚举信息了
1 | |
28、这里解密的时候,涉及到Python的3方库存在过期的问题,导致一直提示缺少某个库,修改了下以下代码后,成功解密出来火狐的密码
1 | |
29、这里得到一些密码后,继续进行密码喷洒下
1 | |
30、但是上面获取的账号,在手工枚举阶段没有发现了什么有效的信息,那就直接域枚举吧
1 | |
31、登录bloodhund 工具,清理历史数据后,再上传最新的数据发现了存在一个可利用的漏洞
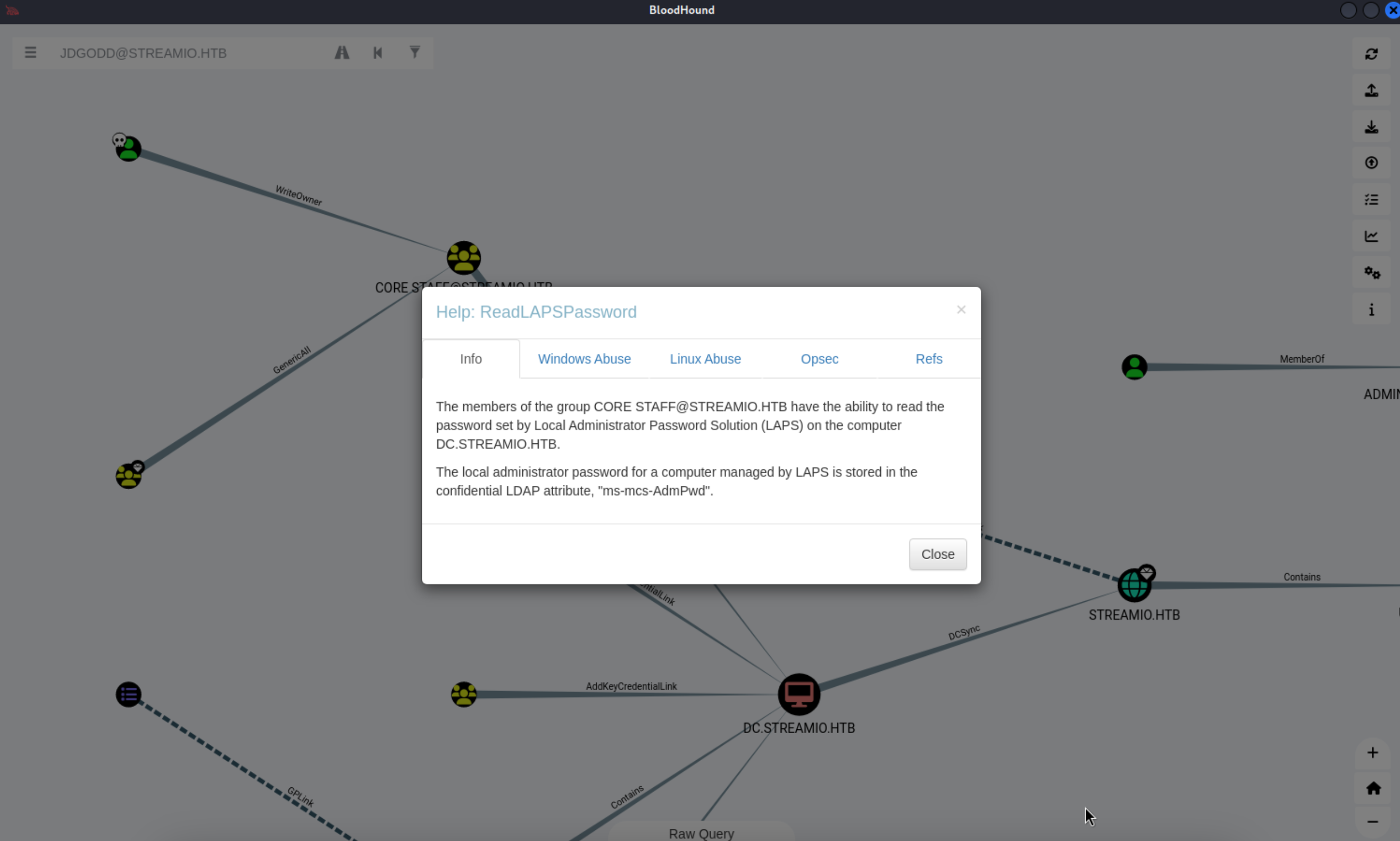

1 | |
32、那就按照提示开始枚举吧
1 | |
33、但是,可能是权限的问题吧,就是获取不到任何一个密码结果,突然想到,是不是我漏了一个环节,我对该组拥有写入权限,但是我当前的账号并不在组里,我需要添加一下。
1 | |
34、弄好权限后,那就继续开始使用工具进行获取密码
1 | |
35、读取最终flag信息
1 | |
36、其他读取方法:
1 | |
0x03 通关凭证展示
https://www.hackthebox.com/achievement/machine/1705469/474