UpDown-htb-writeup
0x00 靶场技能介绍
章节技能:目录扫描、二级目录扫描、虚拟主机子域名扫描、.git源码泄露、git_dumper.py、.htaccess 配置文件、文件上传绕过、上传扩展名为 png 的 zip 文件、phar://path、二进制文件字符串分析、Python内置命令执行代码、ssh秘钥获取并登录、sudo提权、easy_install提权
参考链接:https://htbwp.readthedocs.io/en/latest/linux/UpDown.html
参考链接:https://0xdf.gitlab.io/2023/01/21/htb-updown.html
0x01 用户权限获取
1、获取下靶机IP地址:10.10.11.177
2、获取下开放端口情况:
1 | |
3、绑定下域名地址,再查看下默认的80端口信息
1 | |
http://10.10.11.177/

4、扫描下目录情况
1 | |
5、发现了2个文件,一个是dev目录一个是server-status,分别查看下
http://siteisup.htb/server-status
1 | |
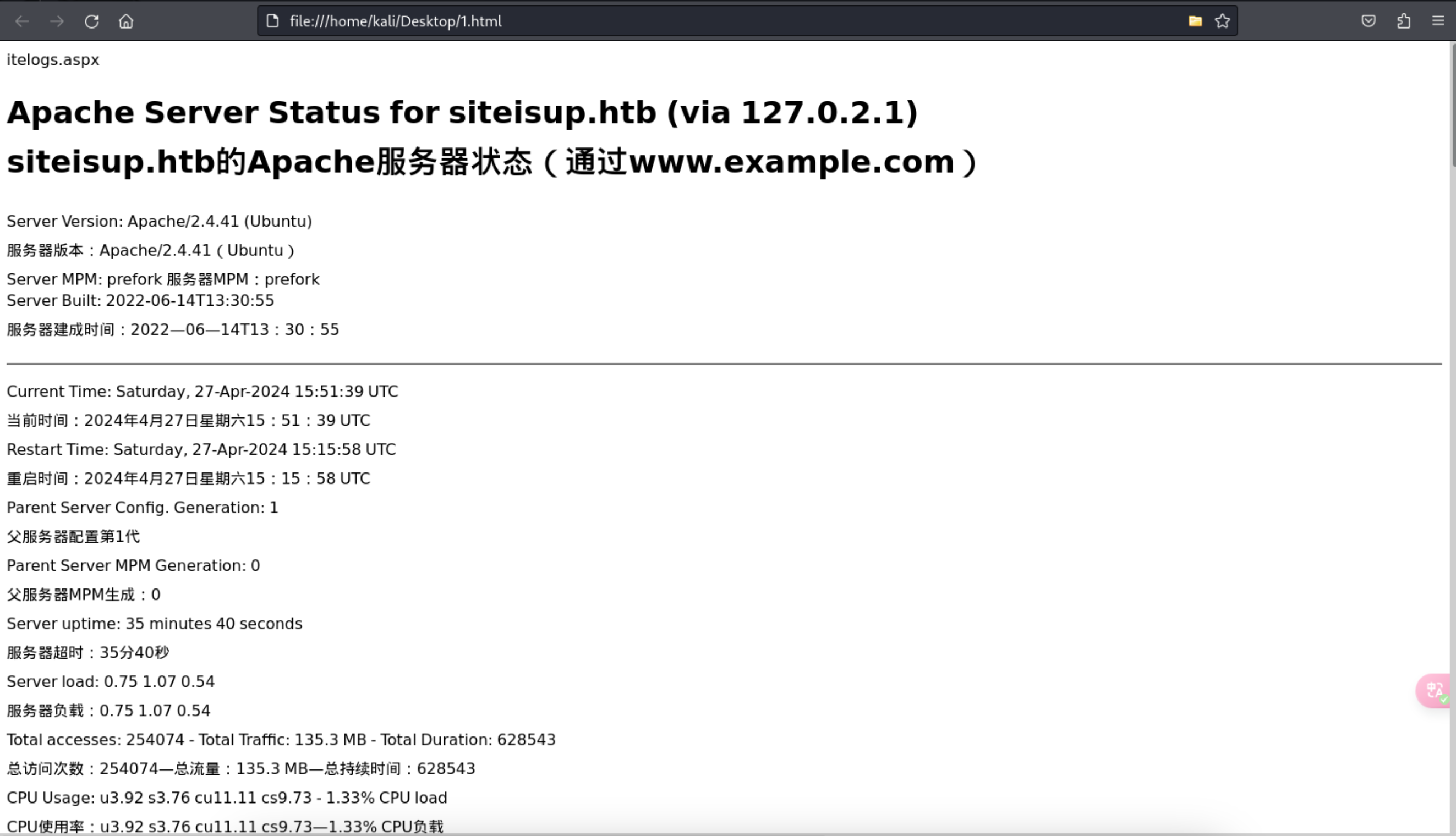
1 | |
http://10.10.11.177/dev/
http://10.10.11.177/dev/.git/
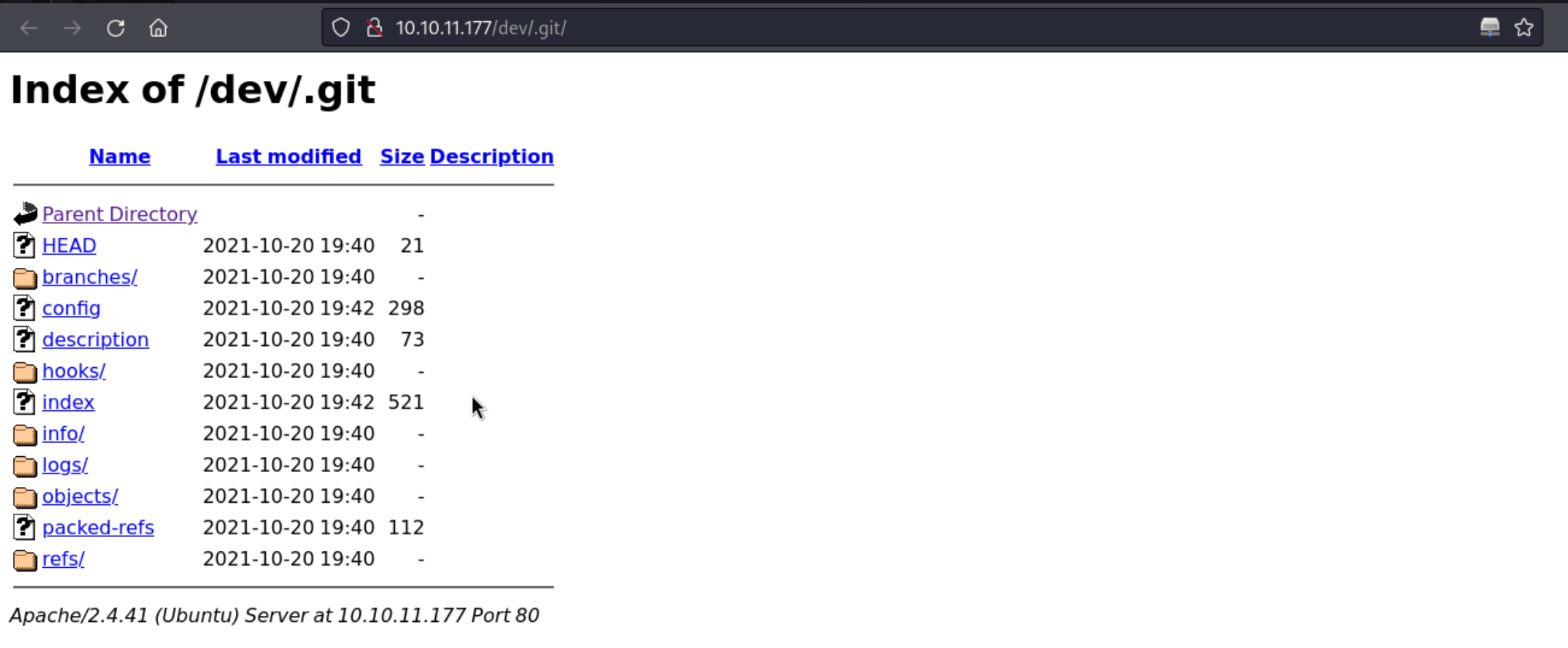
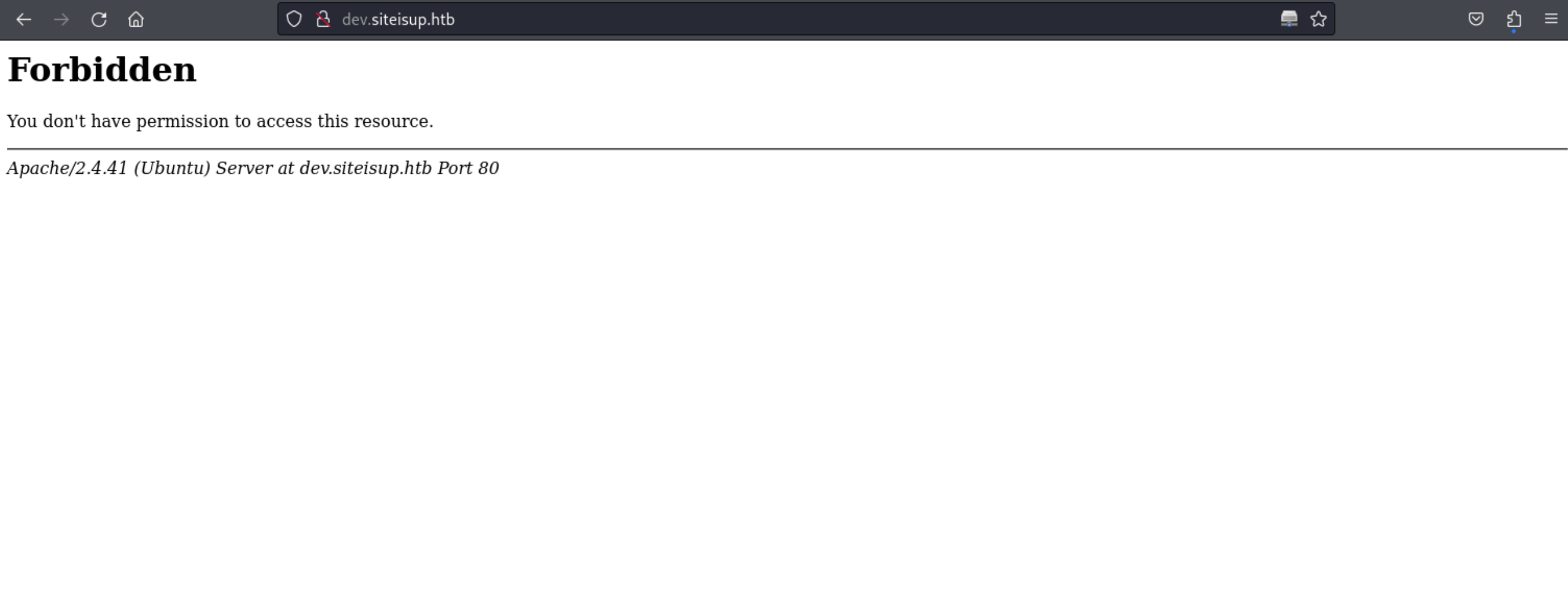
6、再此之前,再枚举下子域名信息
1 | |
http://dev.siteisup.htb/
7、前期使用了gitdumper.sh 工具进行下载,结果该工具下载的文件不全,导致我一直卡着了,这里整个目录都翻遍了,也没发现自己想发现的内容,故查看writeup,发现是 .git 这里下载的文件不全,故换了个工具重新开始下载
1 | |
8、查看分析文件
1 | |
9、这里显示,添加上这个文件头,就可以访问地址,结合上面发现的Dev子域名,可以尝试下
http://dev.siteisup.htb/

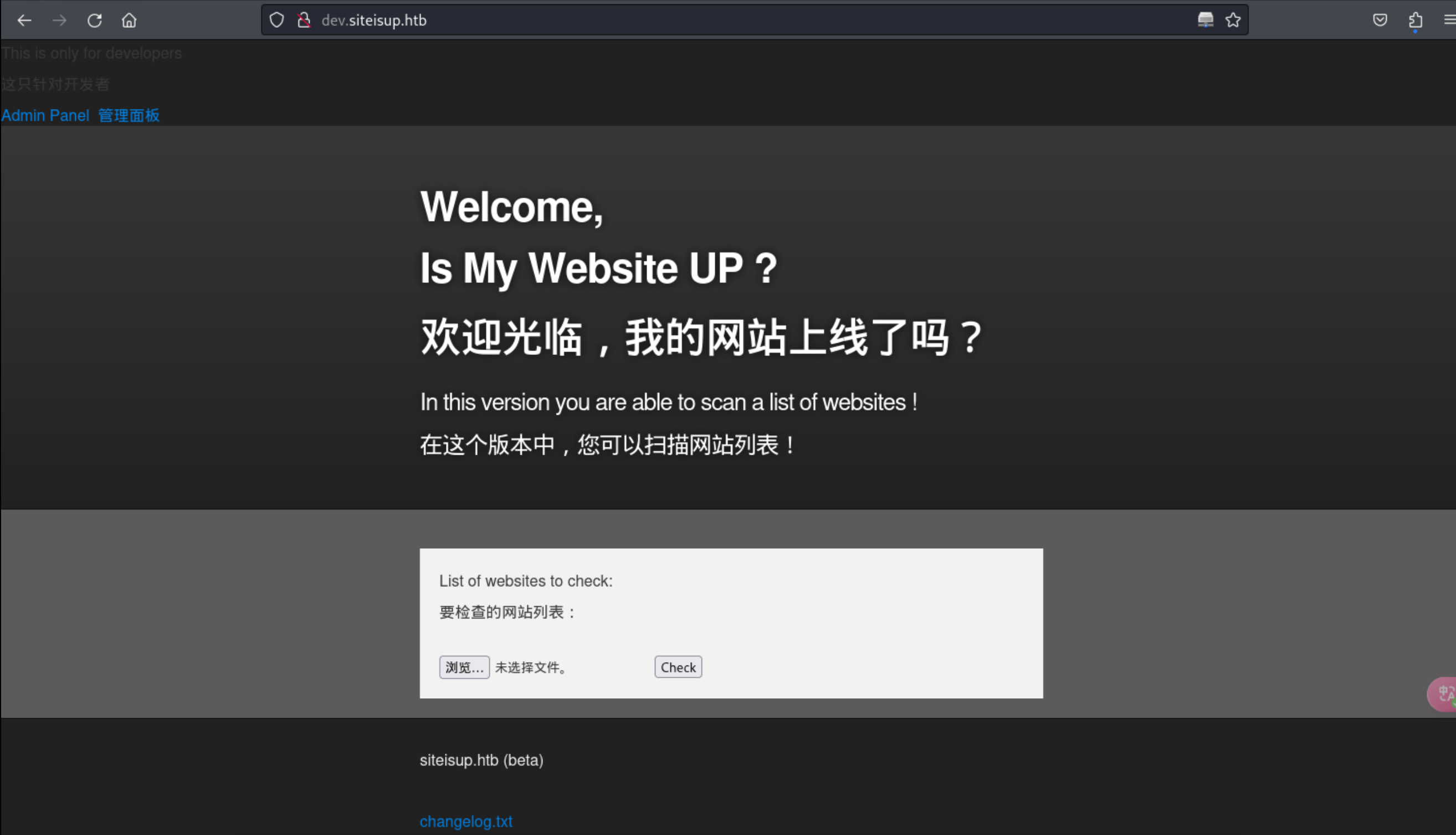
10、发现了可以上传文件的页面,结合 .git 源码里发现的情况,可以上传扩展名为 png 的 zip 文件,进行绕过
1 | |
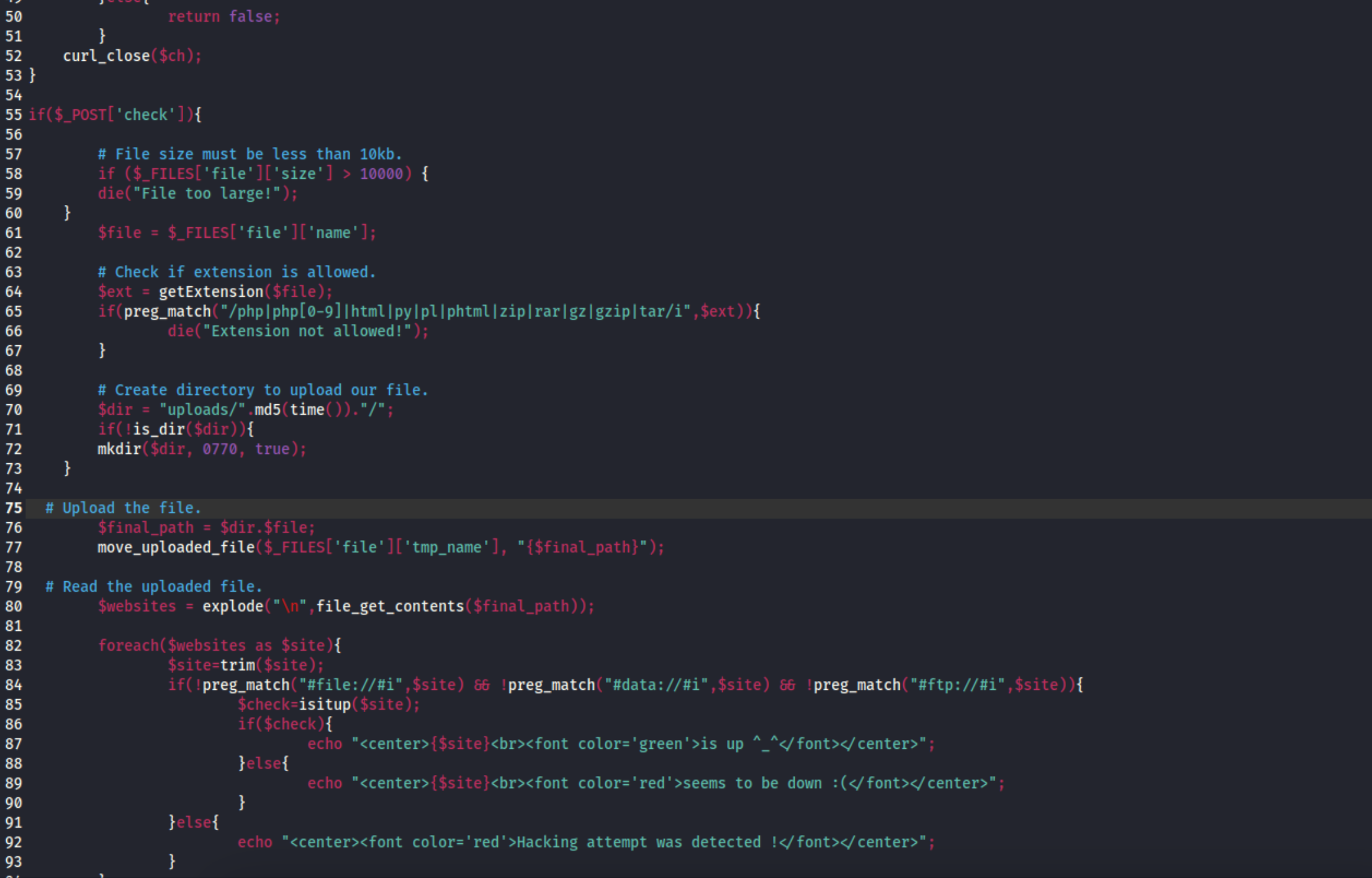
11、构造压缩包文件,并开始上传
1 | |
http://dev.siteisup.htb/uploads/9df78c6c215ea04b53719ab74e46d47a/pipinfo.png
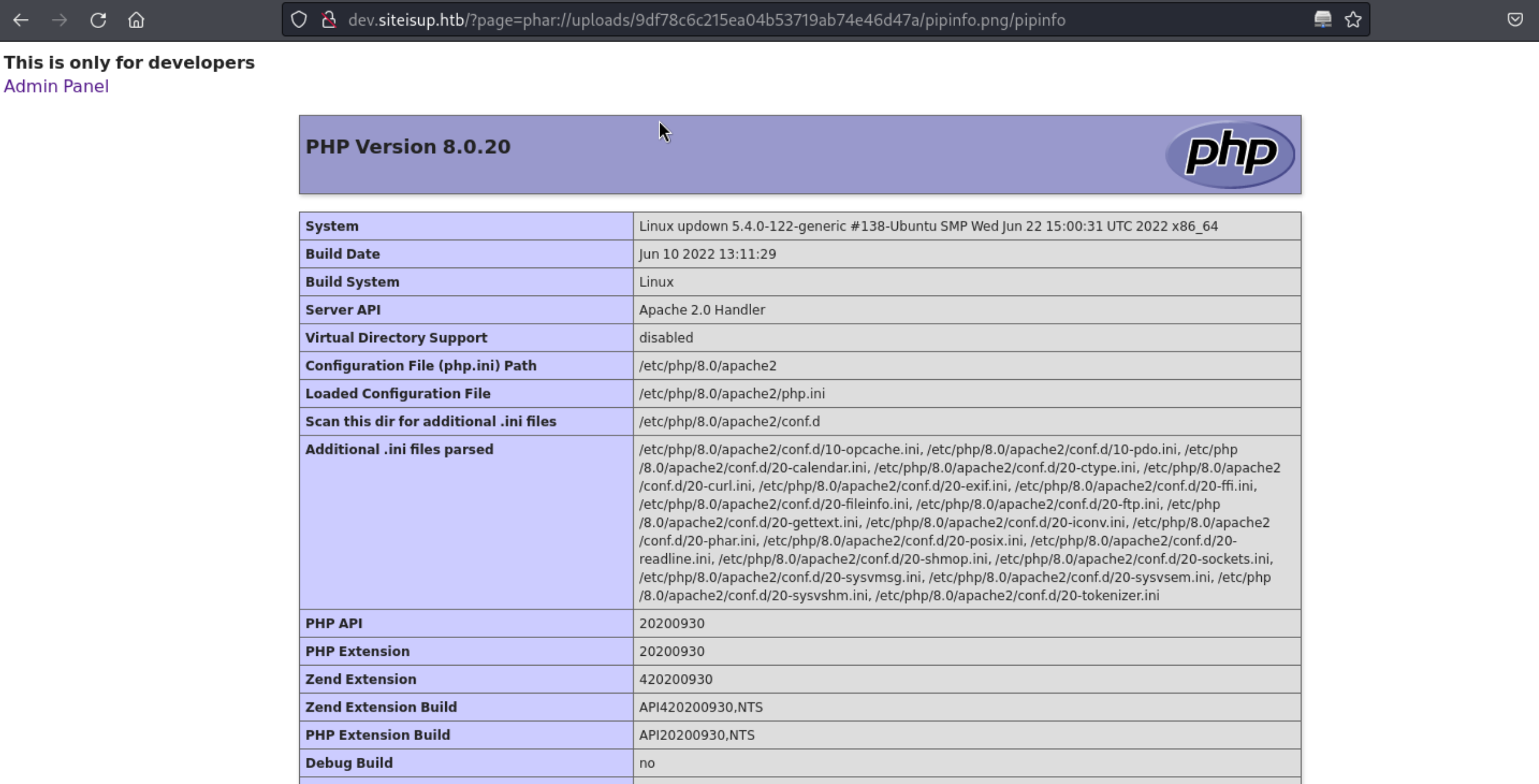
12、在上传的 zip 中执行 phpinfo,phar://path
http://dev.siteisup.htb/?page=phar://uploads/9df78c6c215ea04b53719ab74e46d47a/pipinfo.png/pipinfo
13、接下来就是构造反弹shell进行上传了
1 | |
http://dev.siteisup.htb/uploads/7c6eba507d508a9a10bf42e63a81cef8/shell.png
http://dev.siteisup.htb/?page=phar://uploads/7c6eba507d508a9a10bf42e63a81cef8/shell.png/shell
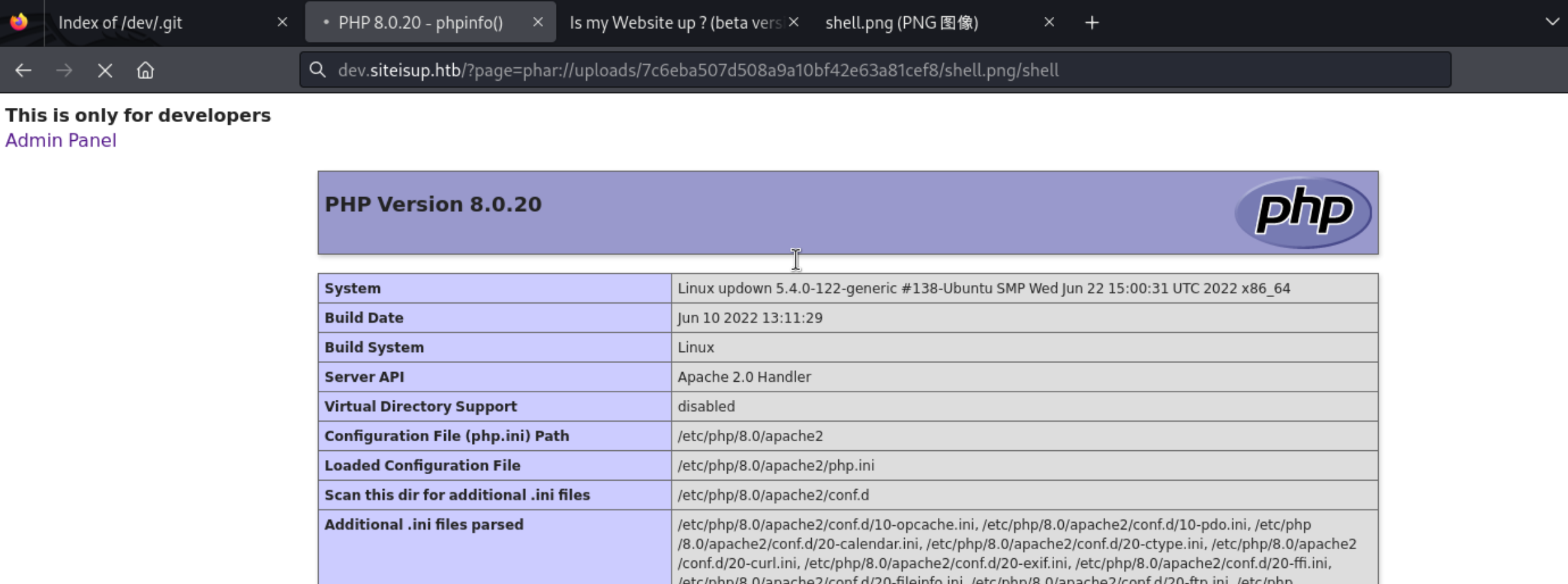
14、成功获取到初始的shell了
1 | |
15、经过分析发现了目标用户下有个文件,可执行文件,通过nc进行下载
1 | |
16、开始分析下载的文件
1 | |
17、这里发现,疑似这个程序会运行这个Python脚本
__import__('os').system('id')
__import__('os').system('bash')
18、在shell环境中运行一下看看
1 | |
19、看来可以利用
1 | |
20、到这里就获取到了另一个用户的shell了,为了提高shell的可枚举性,我们把ssh的秘钥给弄了下来,并成功登录上了用户
1 | |
21、获取下第一个flag信息吧
1 | |
0x02 系统权限获取
22、开始继续枚举
1 | |
23、easy_install 是一种在Python中安装软件包的方法,现在已被弃用。它的核心是运行一个 setup.py 脚本,该脚本承诺采取某些操作来安装软件包。由于 easy_install 有效地运行了一个Python脚本,因此从它获得执行是微不足道的。有一个GTFObins页面,其中包含一些复制粘贴以获取shell,但我将自己完成它以更好地理解它。
https://gtfobins.github.io/gtfobins/easy_install/
1 | |
24、那就直接利用提权吧,并读取下flag信息
1 | |
0x03 通关凭证展示
https://www.hackthebox.com/achievement/machine/1705469/493