0x00 靶场技能介绍 章节技能:目录扫描、jar文件反编译读源码、sudo -i 切换root用户
参考链接:官方引导
0x01 用户权限获取 1、这是一个简单的靶机,却也是我觉得最符合oscp的靶机,有兔子洞,但是又存在多种可能
2、常规获取下靶机IP地址:10.10.10.37
3、扫描下开放端口信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 ┌─[us-vip-22]─[10.10.14.4]─[htb-shiyan@htb-tlqbfgzof4]─[~/Desktop]for 10.10.10.37
4、这里发现个域名,本地加入下hosts
1 2 3 ┌─[us-vip-22]─[10.10.14.4]─[htb-shiyan@htb-tlqbfgzof4]─[~/Desktop]echo "10.10.10.37 blocky.htb" | sudo tee -a /etc/hosts
5、由于存在21端口,我这里尝试了ftp匿名登录,但是无果,我又ftp软件版本漏洞测试无果、ssh版本漏洞无果、Apache版本漏洞无果。
6、这里80端口首页是wordpress,我尝试了wpscan扫描,又尝试了wp版本漏洞等均无果、后台弱口令无果。。。
7、至此,我陷入了迷茫,感觉做的靶机越多,越觉得哪里都是漏洞,只要出现版本号。
8、由于觉得这个是wp框架,我就懒了目录扫描了,这里继续目录扫描下,结果发现了奇点
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 ┌─[us-vip-22]─[10.10.14.4]─[htb-shiyan@htb-tlqbfgzof4]─[~/Desktop]dir -u http://blocky.htb --wordlist=/usr/share/dirbuster/wordlists/directory-list-1.0.txtin directory enumeration mode
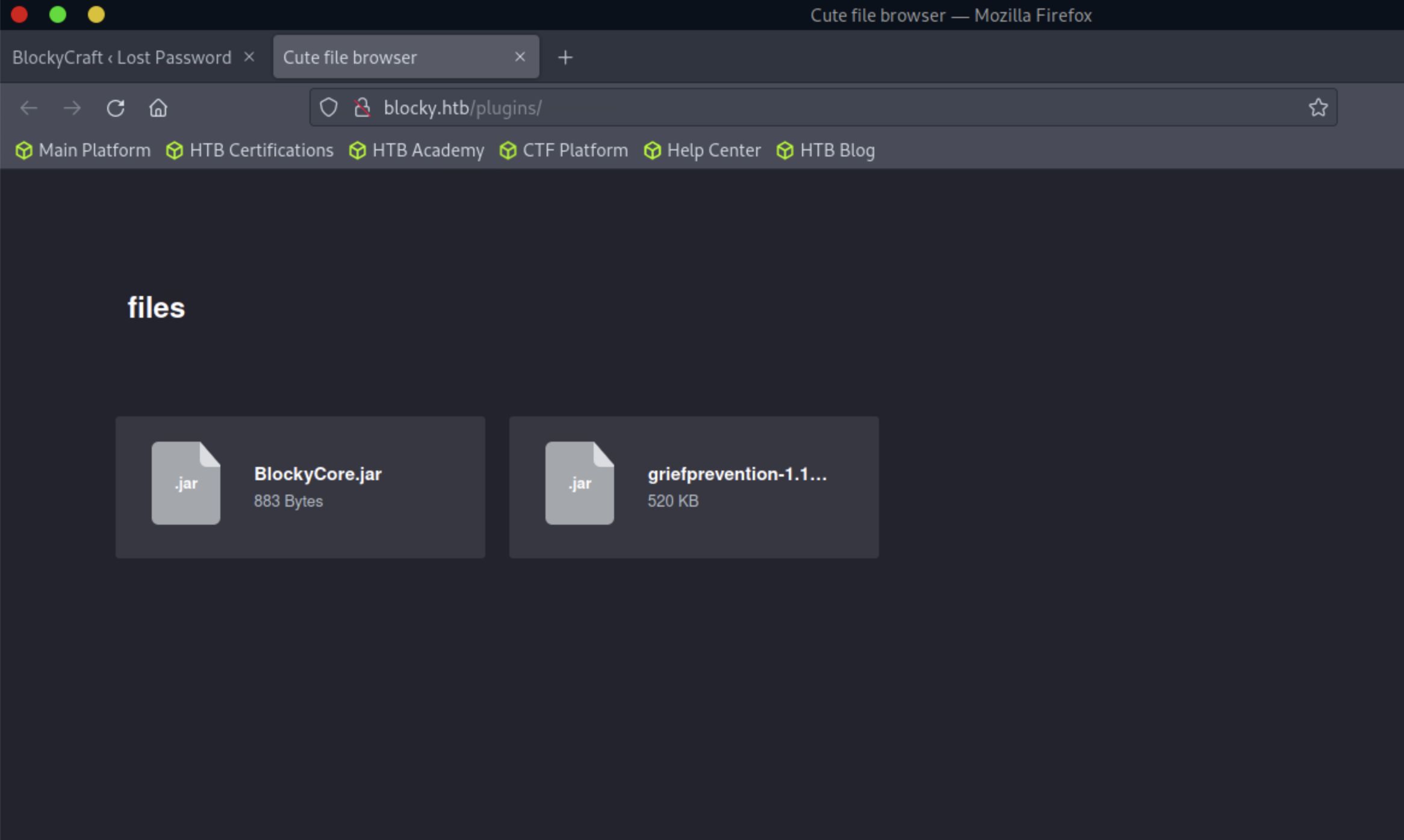
9、这里发现了2个压缩包文件,下载下来,使用jd-gui进行反编译下看看内容
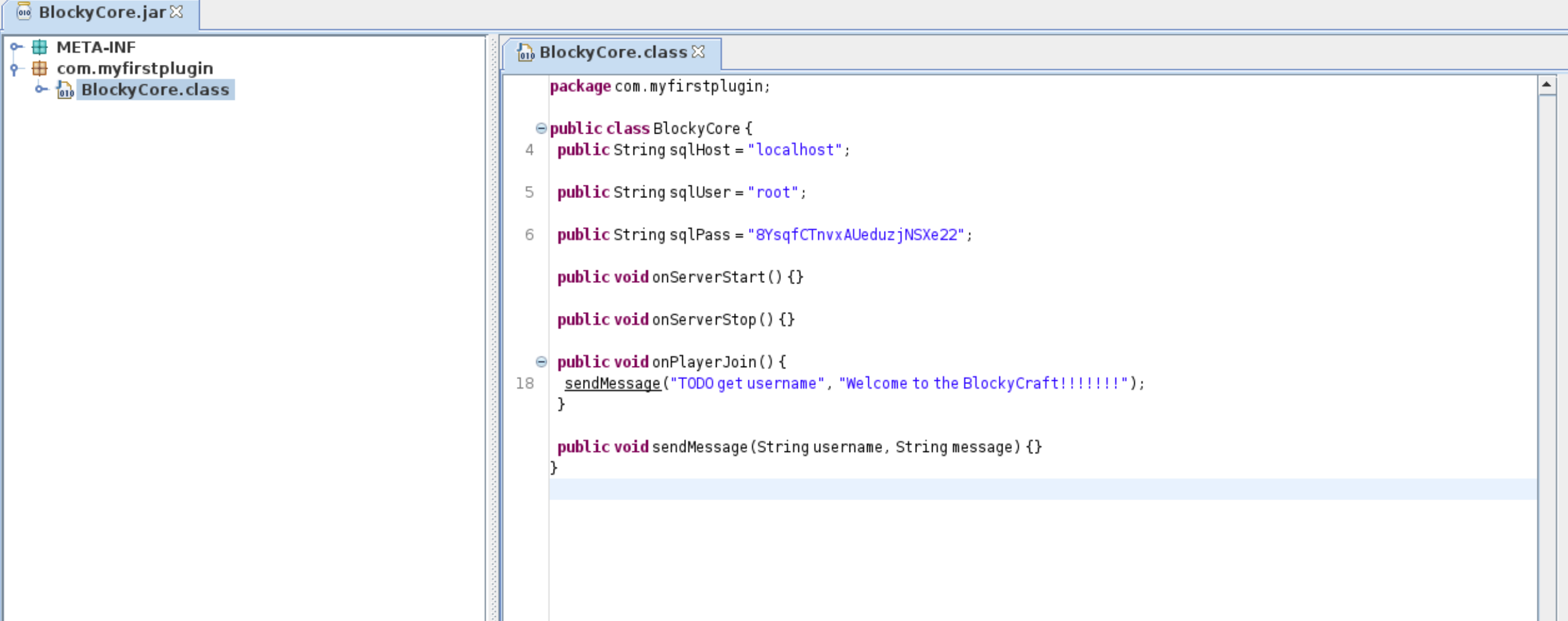
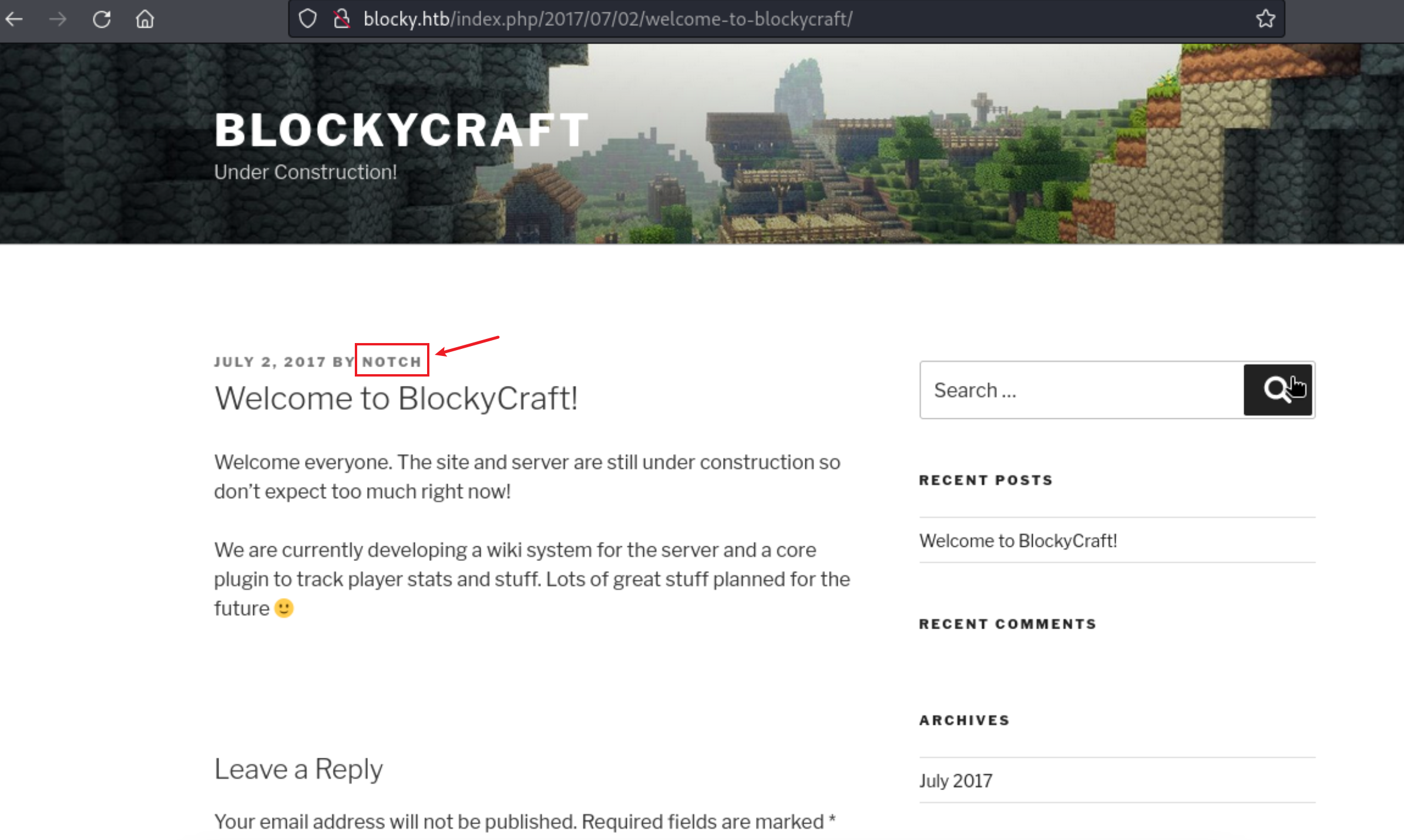
10、在这里发现了数据库的账号密码,这里我想起了以前的htb的靶场套路,使用root直接ssh登录,登录失败,但是在网站首页有个用户名信息的
11、到这里使用该账号名,成功登录系统,并获取到第一个flag信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 ┌──(kali㉿kali)-[~/桌面]'s password: Welcome to Ubuntu 16.04.2 LTS (GNU/Linux 4.4.0-62-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage 7 packages can be updated. 7 updates are security updates. Last login: Fri Jul 8 07:16:08 2022 from 10.10.14.29 To run a command as administrator (user "root"), use "sudo <command>". See "man sudo_root" for details. notch@Blocky:~$ pwd /home/notch notch@Blocky:~$ ls -la total 40 drwxr-xr-x 5 notch notch 4096 Jul 8 2022 . drwxr-xr-x 3 root root 4096 Jul 2 2017 .. -rw------- 1 notch notch 1 Dec 24 2017 .bash_history -rw-r--r-- 1 notch notch 220 Jul 2 2017 .bash_logout -rw-r--r-- 1 notch notch 3771 Jul 2 2017 .bashrc drwx------ 2 notch notch 4096 Jul 2 2017 .cache drwxrwxr-x 7 notch notch 4096 Jul 2 2017 minecraft drwxrwxr-x 2 notch notch 4096 Jul 2 2017 .nano -rw-r--r-- 1 notch notch 655 Jul 2 2017 .profile -r-------- 1 notch notch 33 Dec 12 00:23 user.txt notch@Blocky:~$ cat user.txt 5ca90bc0edb9f99b3b0a33f9ddc79f88 notch@Blocky:~$
0x02 系统权限获取 12、这里通过 sudo -l ,发现可以直接切换到root用户。
1 2 3 4 5 6 7 8 9 10 11 12 13 notch@Blocky:~$ sudo -lfor notch: for notch on Blocky:
0x03 通关凭证展示 https://www.hackthebox.com/achievement/machine/1705469/48
http:\sh1yan.top\photo\