Shoppy-htb-writeup
0x00 靶场技能介绍
章节技能:目录扫描、子域名扫描、SQL注入、万能密码、sudo、二进制反编译、硬编码、docker特权组
参考链接:https://blog.heapbytes.tech/rooms/hackthebox/easy/shoppy
参考链接:https://0xdf.gitlab.io/2023/01/14/htb-shoppy.html
0x01 用户权限获取
1、靶机介绍
关于ShoppyShoppy 是一款简单的 Linux 机器,其特点是带有登录面板和用户搜索功能的网站,但容易受到 NoSQL 注入攻击。攻击者可以利用该漏洞获取所有用户的密码哈希值。破解其中一位用户的密码哈希值后,我们可以验证服务器上运行的 Mattermost 聊天,从而获取用户“jaeger”的 SSH 凭据。通过逆向工程密码管理器二进制文件,可以横向移动到用户“deploy”,从而获取用户的密码。我们发现用户“deploy”是组“docker”的成员。可以利用其权限读取根标志。
2、首先测试下靶机连通率
1 | |
3、扫描下开放端口情况
1 | |
4、这里绑定下端口扫描发现的域名信息
1 | |
5、然后查看下该域名下的网站内容信息
http://shoppy.htb/
6、这里我们使用ffuf扫描下网站目录情况
1 | |
7、这里发现了登录地址
http://shoppy.htb/login
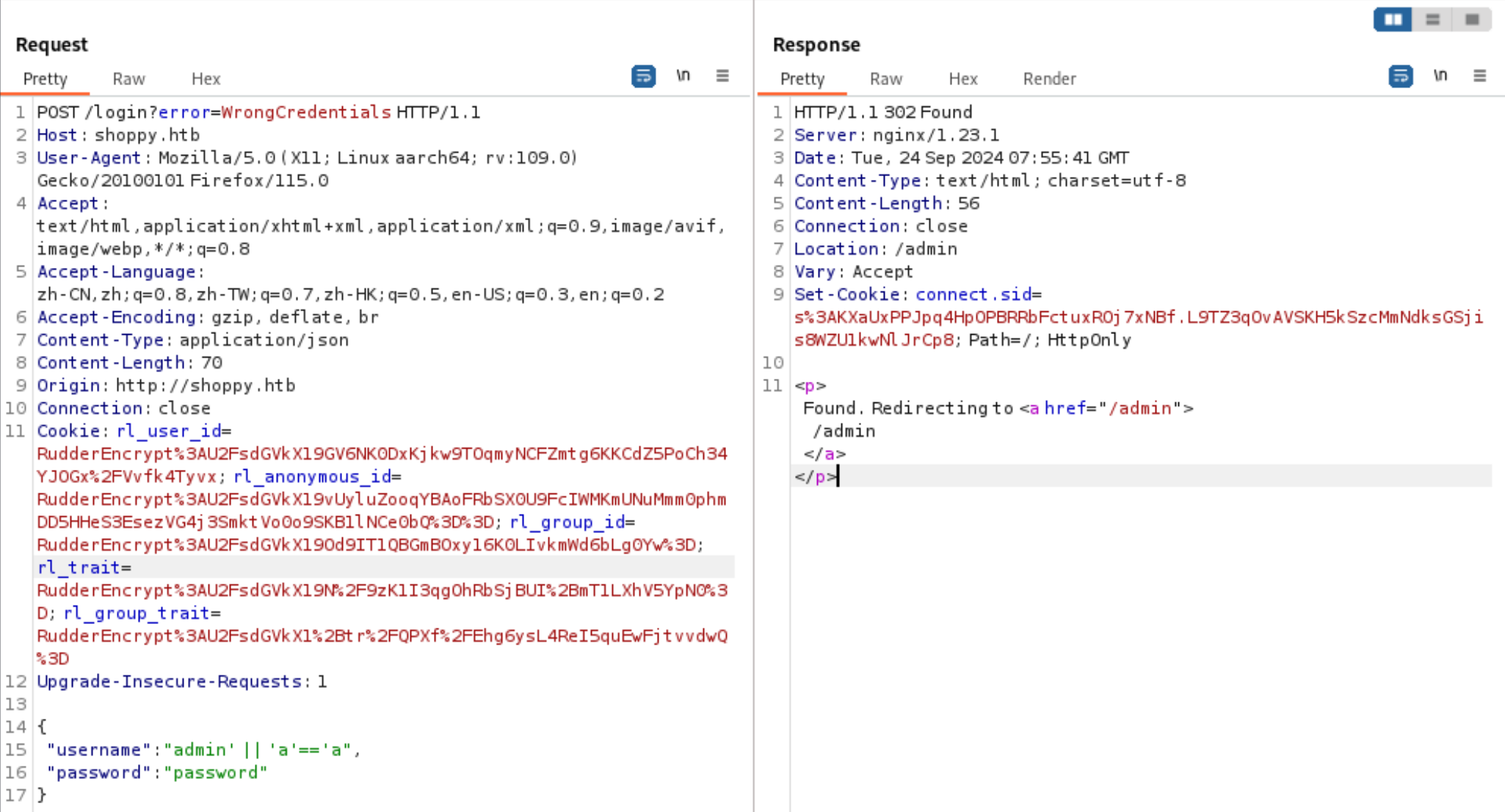
8、这里其实存在 nosql 注入的地方的,但是我太菜了,用sqlmap也没跑出来
1 | |
9、然后就绕过登录了,来到了后台界面了
http://shoppy.htb/admin

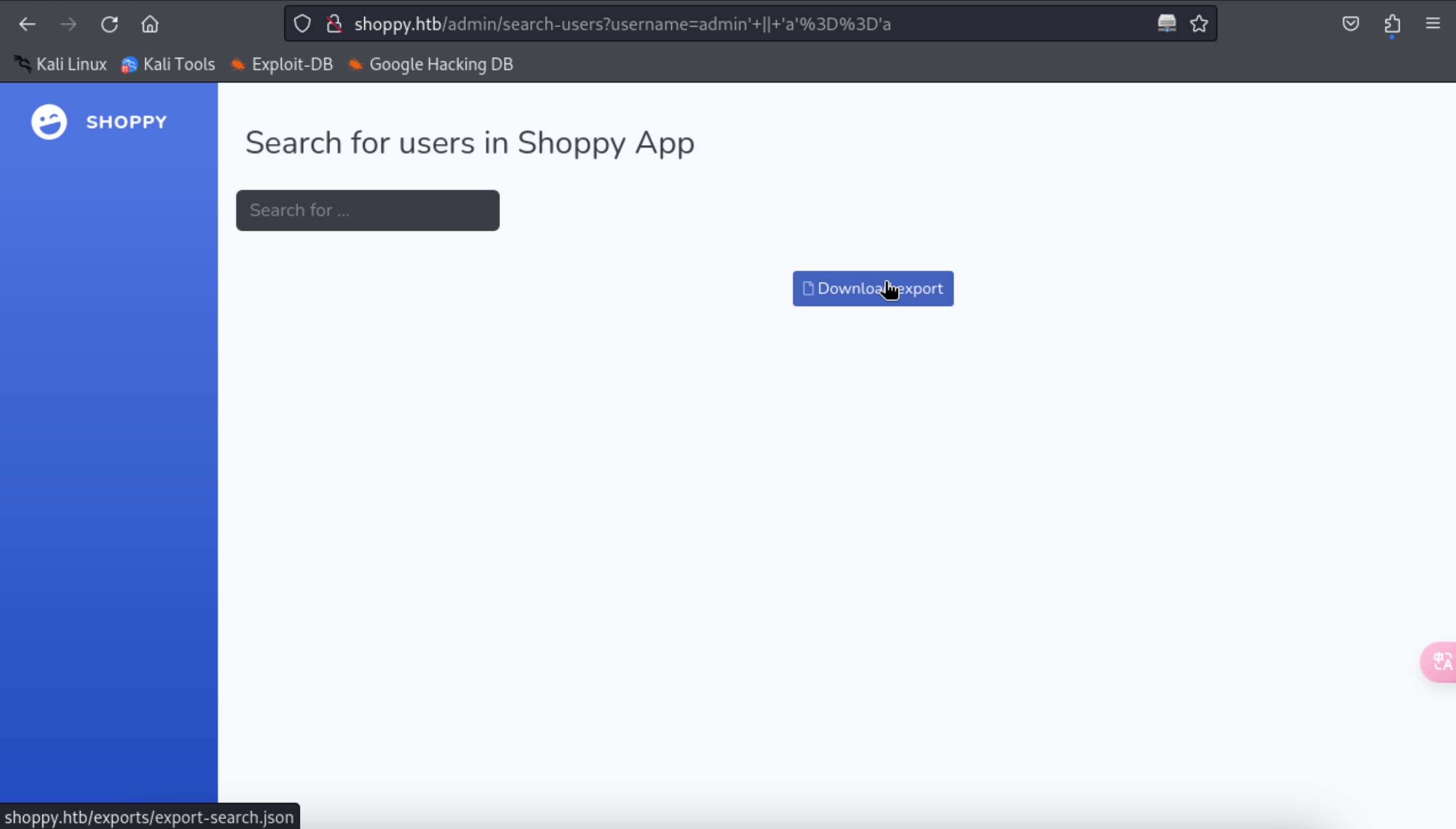
10、在搜索界面上随意输入绕过代码,发现可以下载文件
http://shoppy.htb/admin/search-users?username=admin%27+%7C%7C+%27a%27%3D%3D%27a
11、下面是下载的文件内容
http://shoppy.htb/exports/export-search.json
1 | |

1 | |
12、在这里我们获取了一些账号密码信息,然后就没进度了,其实到这里就是使劲的扫描子域名了
1 | |
13、这一个步骤的子域名枚举,太坑了,我用了好几个字典都没有枚举出来想要的子域名,深度差评。
14、本地绑定下hosts信息
1 | |
15、查看该子域名下的信息
http://mattermost.shoppy.htb/login
http://mattermost.shoppy.htb/reset_password
16、这里使用上面破解出来的账号密码,登录了这个系统
http://mattermost.shoppy.htb/shoppy/channels/town-square
17、发现老板的账号
1 | |
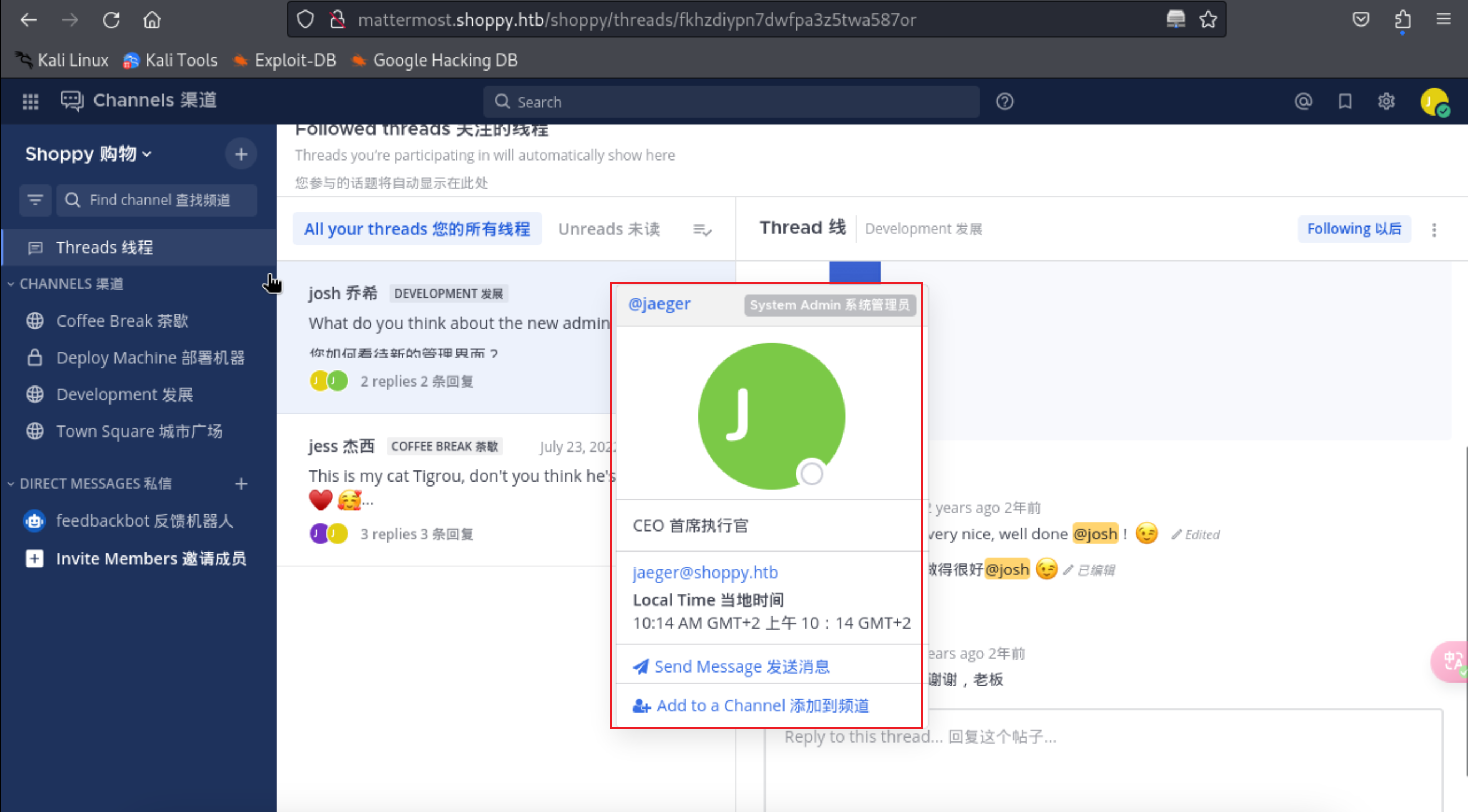
18、发现账号密码信息
http://mattermost.shoppy.htb/shoppy/channels/deploy-machine
1 | |
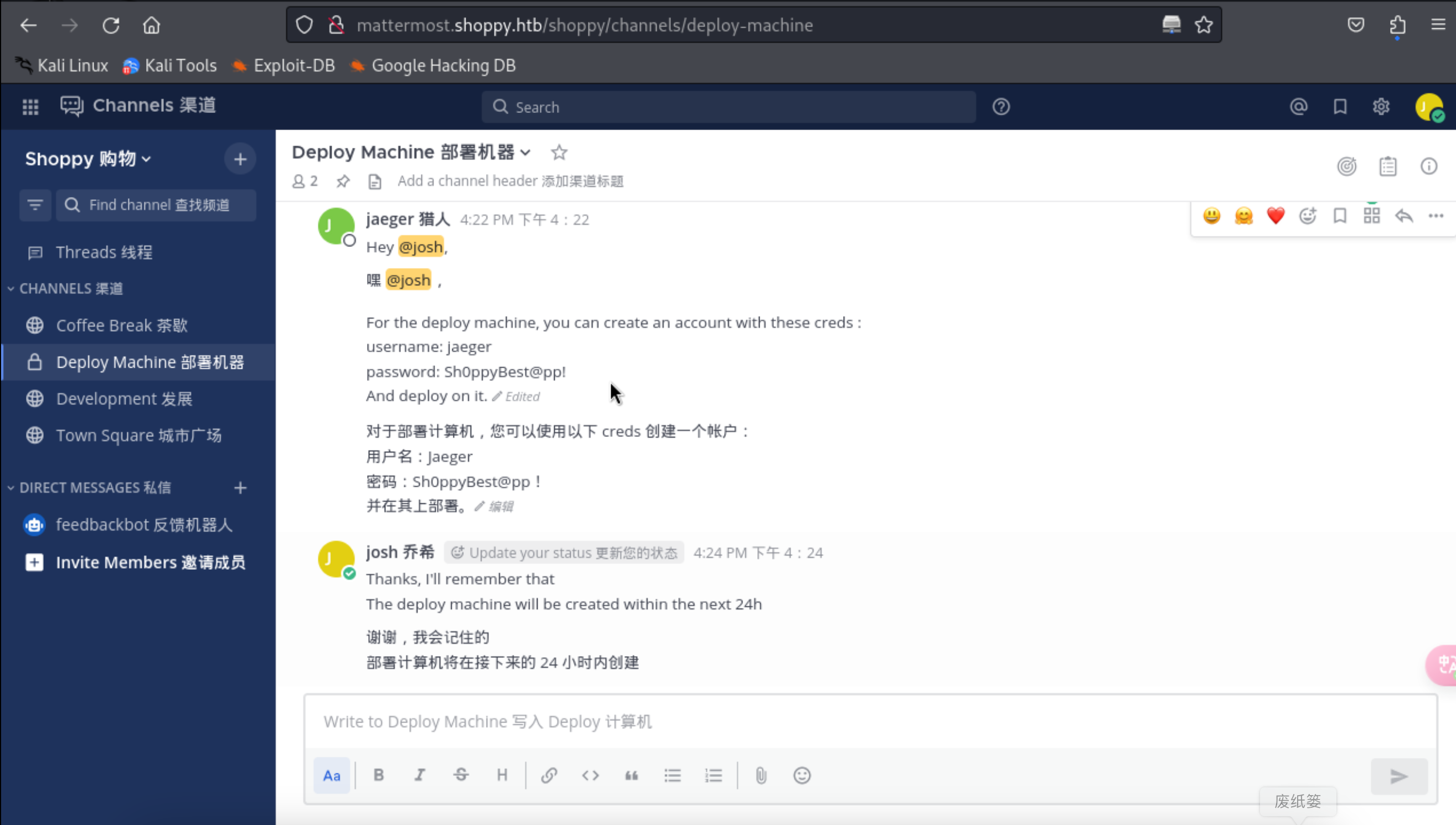
19、然后我们就开始使用发现的账号进行登录了。这里需要注意的是用户名的大小写,在linux机器中,对大小写很明显,所以这里一般都是需要小写的用户名的。
1 | |
20、然后获取到第一个用户的flag信息
1 | |
0x02 系统权限获取
21、通过枚举,发现当前用户拥有其他用户的sudo权限
1 | |
22、尝试利用,发现并没有权限
1 | |
23、这里,我们把这个文件复制到本地机器上
1 | |
24、简单查看下类型
1 | |
25、这里有点技能超纲了,经过仔细判断分析,还是能看出来点门道的
26、下载反编译工具
1 | |
27、对该文件进行反编译的查看
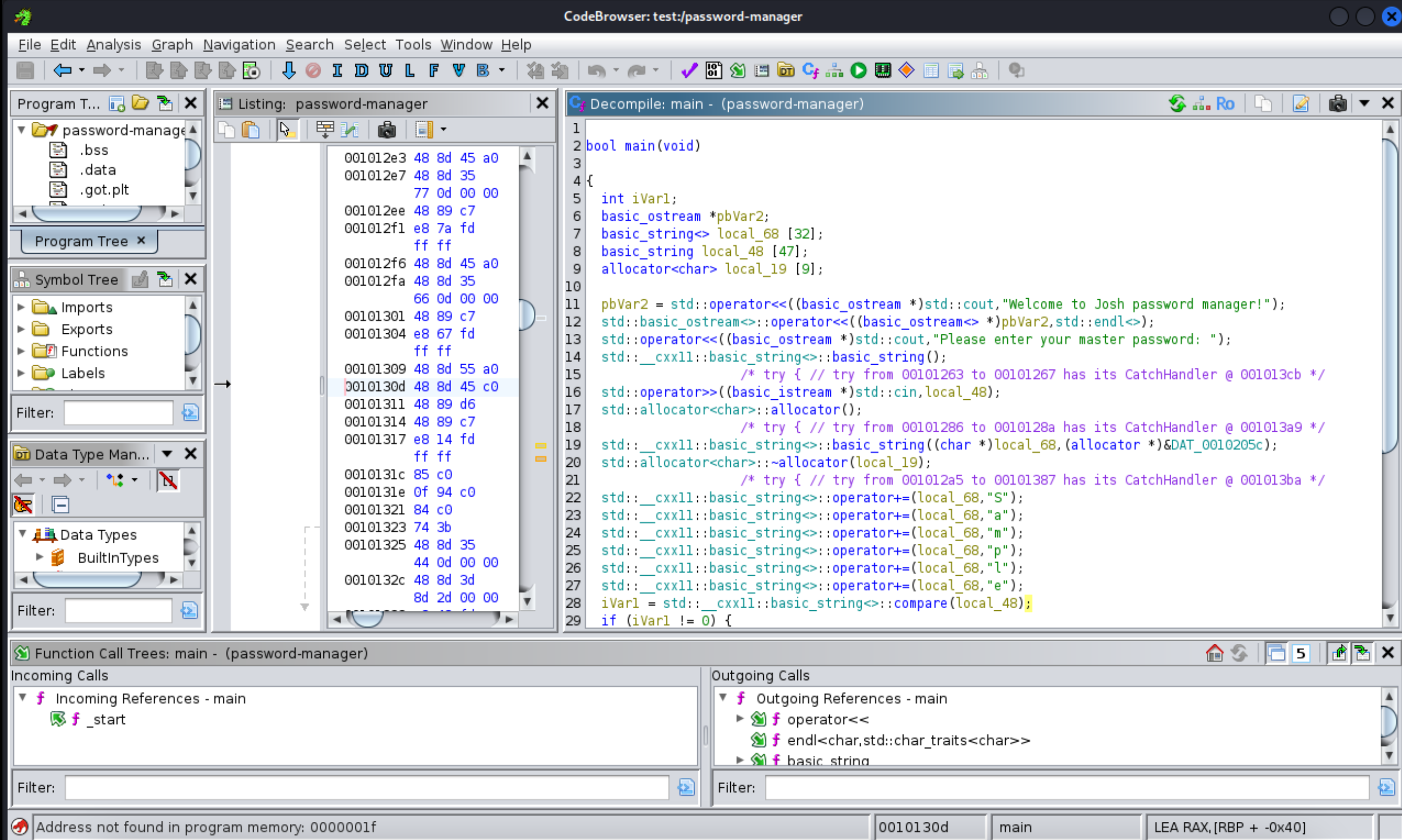
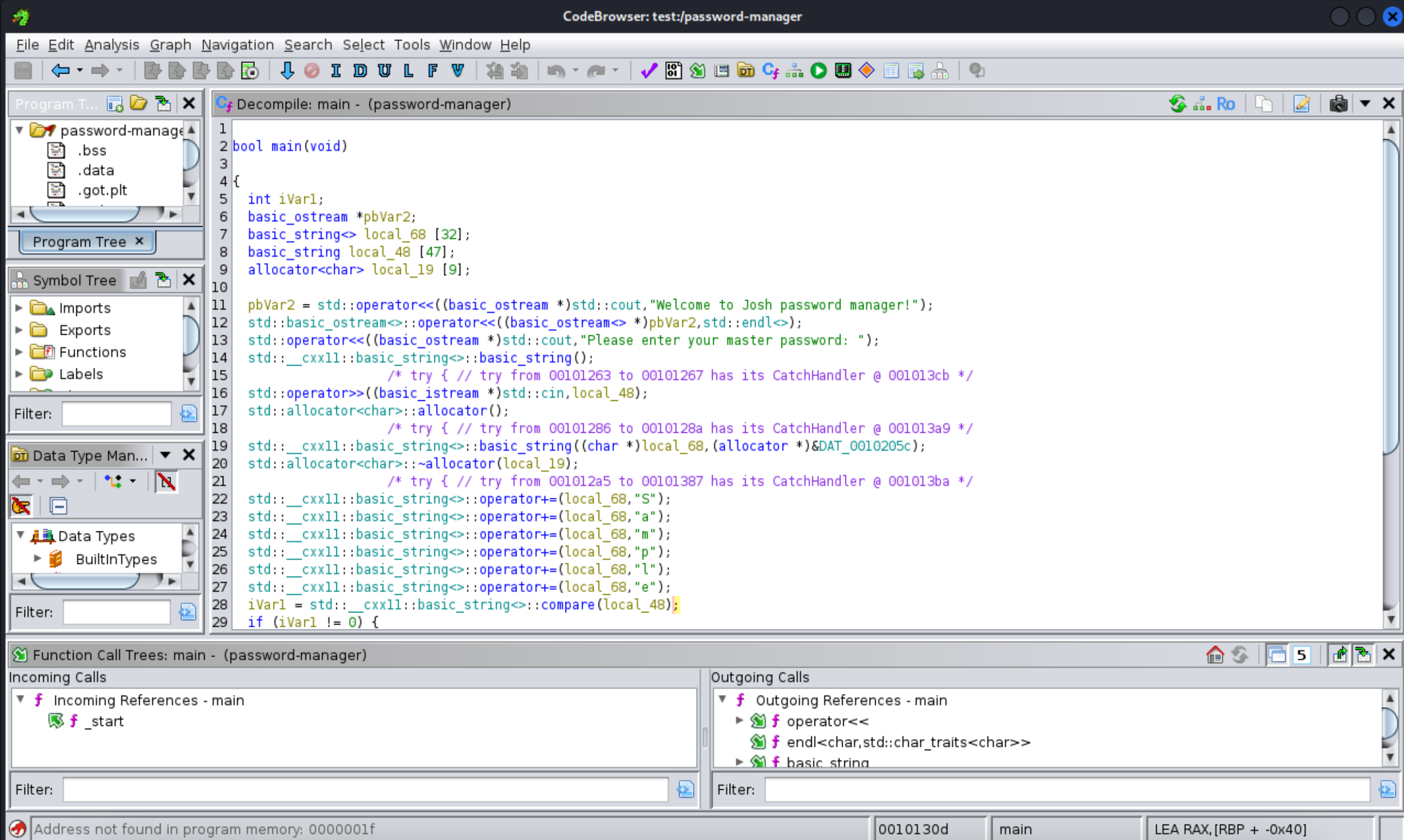
1 | |
28、这里的门道就是发现了 Sample 这个硬编码的内容,开始利用
1 | |
29、获取到deploy用户的密码凭证信息
30、开始切换用户,并枚举
1 | |
31、这里用户拥有 docker 组的权限,直接利用HTB学院里的特权组利用章节,一套带走
1 | |
0x03 通关凭证展示
https://www.hackthebox.com/achievement/machine/1705469/496